Risky Biz News: FBI takes down and mass-uninstalls Qakbot botnet
In other news: Cisco VPNs targeted by Akira ransomware; Barracuda hacking spree hit 5% of all ESG appliances; and major BGP software vulnerability disclosed.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The FBI has seized server infrastructure that hosted the Qakbot botnet and mass-uninstalled the malware from infected systems.
Also known as Qbot and Pinkslipbot, the botnet has been active since 2008. It initially launched as a banking trojan but changed to operating as a "loader" in the mid-2010s, infecting systems via malspam campaigns and then selling access to infected systems to other cybercrime groups.
Over the past three years, Qakbot has served as an initial entry point for many ransomware attacks. Groups that have worked with Qakbot include the likes of Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta.
The FBI says that with help from law enforcement in Europe (France, Germany, the Netherlands, the UK, Romania, and Latvia) it seized tens of servers operated by the Qakbot gang and redirected traffic to FBI systems.
From here, the FBI says it mapped all infected Qakbot systems and then delivered a module that told infected hosts to remove the Qakbot malware from their systems.
Officials say they found that Qakbot had infected more than 700,000 systems across the globe, with more than 200,000 located in the US.
The US Justice Department also seized $8.6 million from the Qakbot gang, representing illicit profits, while Dutch police secured 7.6 billion credentials from the seized servers. The Qakbot server seizures took place last Saturday, August 26, per the UK NCA.
The FBI says Zscaler provided technical assistance for the takedown, and CISA, Microsoft, the Shadowserver Foundation, and Have I Been Pwned are helping notify affected victims.
No arrests or formal charges have been announced so far, but that does not exclude that they've taken place.
Officials named the Qakbot takedown as Operation Duck Hunt. It marks the third major malware loader botnet they have taken down over the past few years, after similarly hitting Emotet and Trickbot in 2020 and 2021.
Since no arrests were announced in those takedowns either, both botnets made a comeback, but at a much-diminished capacity and as a shadow of their former selves.
Breaches, hacks, and security incidents
Magnate Finance rug pull: The developer of the Magnate Finance crypto-token has stolen $6.4 million of its users crypto-assets in a type of scam known as a "rug pull." The project has shut down its website and Telegram channel shortly after the thefts. Blockchain security experts say they found evidence to link the developer to similar rug pulls at the Solfire and Kokomo Finance projects.
UM cyber incident: The University of Michigan has taken its IT network offline to deal with a cybersecurity incident. The incident took place on Sunday, a day before the new school year was scheduled to start. Classes have taken place as scheduled but without an internet connection. The university expects to recover this week.
Dutch Land Registry leak: The Dutch Data Protection Agency has ordered the Land Registry authority to shore up its website after journalists discovered they could get access to any citizen's personal data and land ownership information. In a report this week, RTL Nieuws says that anyone can register and get automatically approved for a professional account on the Land Registry website. These are accounts available for lawyers, notaries, and real estate agents that provide full, uncensored access to land ownership data. Reporters say such access could be used to track and harass citizens, such as politicians, military and police personnel, and former life partners.
UK Met Police leak: The data of 47,000 UK Metropolitan Police officers has been stolen from the systems of one of its suppliers. The hackers gained access to data such as names, ranks, photos, vetting levels, and pay numbers for officers and staff, the Met said in a statement. Data such as home addresses and phone numbers was not included, but the Met has told officers to be on alert. [Additional coverage in Sky News]
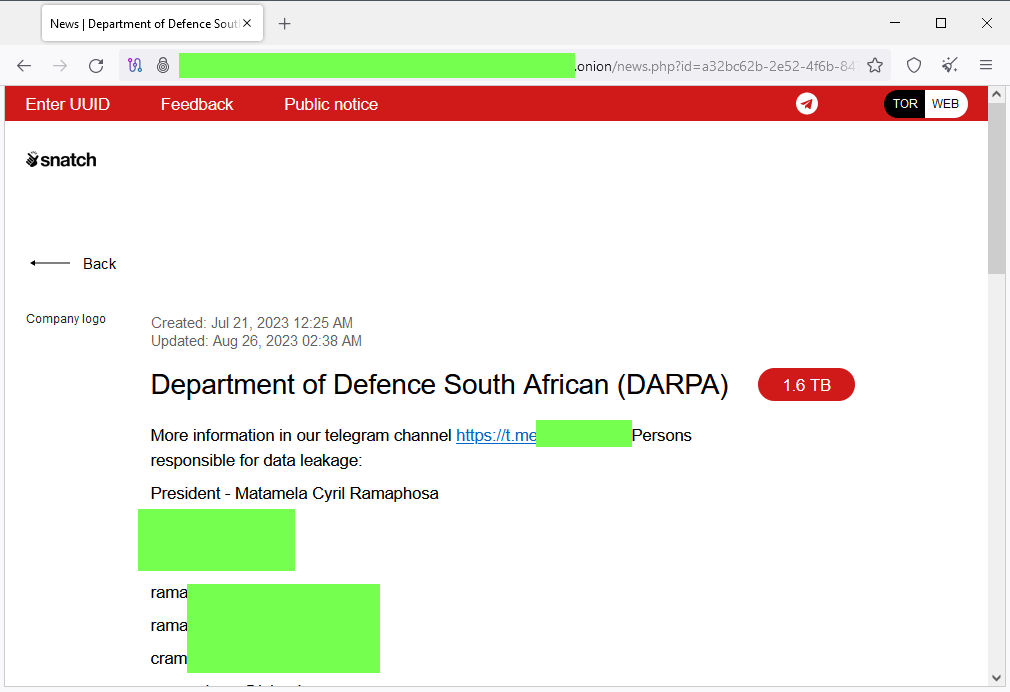
South Africa DOD ransomware attack: The Snatch ransomware gang claims it breached and stole more than 200TB of files from the South African Department of Defense. The group released 1.6TB of data to prove their claims, including the personal contact details of South African President Cyril Ramaphosa. The Department initially claimed the hack was fake news before walking back their claim. [Additional coverage in MyBroadband]
General tech and privacy
Exchange Extended Protection: Microsoft will enable by default a security feature named Extended Protection for all Exchange 2019 email servers later this fall. The feature is meant to protect Exchange servers from Adversary-in-the-Middle (AitM) and other authentication relay attacks. It has been available to Exchange admins since August of last year, but Microsoft is now turning it on by default for every customer. Admins can still opt out of this upgrade or disable it afterward. Exchange servers also got HSTS support—via a separate announcement.
Google Pixel security updates: Google plans to offer security updates for its upcoming Pixel 8 smartphone as long as Apple does for its iPhones, insider sources have told 9to5Google. The company's current Pixel 7 phones only receive four years of security updates. This is smaller than its direct competitor in the Android market, with Samsung offering five years of guaranteed security updates for all its newest devices.
Kaveh Hack: The developers of the Genshin Impact game have rolled out a patch to fix an exploit that was permanently removing crucial objects from the game. Known as the Kaveh Hack, the exploit appeared on the Chinese version of the game before spreading internationally. It works by deleting world exploration points, preventing users from starting quests and completing challenges. Hoyoverse says the patch fixed the exploit and restored deleted items, allowing bricked accounts to regain access to the game. The company says it plans to sue the developers of the hack and users who abuse it.
Linux 6.5: Version 6.5 of the Linux kernel is officially out.
Go gets reproducible builds: The Go programming language now supports reproducible builds, a security feature that can protect against supply chain attacks. The feature allows security teams to spot when a threat actor leaves a project's source code intact but swaps its binaries with malicious ones. Reproducible builds let anyone compile the source code and verify that the binary is bit-for-bit identical to what's available for download. Reproducible builds were added to the Go programming language earlier this month with the release of version 1.21.
Firefox 117: Mozilla has released Firefox 117. New features and security fixes are included. The biggest change is that Firefox Relay is now broadly available and easier to use by most of the Firefox userbase.
Government, politics, and policy
Russia's propaganda machine: VSquare researchers have a report out on the various EU organizations parroting Russian propaganda across Europe. The list includes a Berlin-based company, a Slovak biker gang, and multiple far-right groups all over Central Europe.
Meta's largest info-ops takedown linked to Chinese law enforcement: Meta has taken down the largest covert influence operation the company has seen to date, an operation that involved thousands of accounts on more than 50 platforms. The campaign pushed pro-Chinese narratives and was connected to a cluster previously tracked as Spamouflage. Meta says clues link the campaign to individuals working in Chinese law enforcement. Meta's report is the second time an online influence operation is linked to a Chinese government entity. The DHS linked a similar influence operation to the municipal government of Chongqing, China's fourth largest city.
"Our investigation found that the Spamouflage network is run by geographically dispersed operators across China who appear to be centrally provisioned with internet access and content directions.
We identified multiple distinct clusters of fake accounts that were run from many different parts of China. Their behavior suggested that they were operated by groups who may have worked from a shared location, such as an office. Each cluster worked to a clear shift pattern, with bursts of activity in the mid-morning and early afternoon, Beijing time, with breaks for lunch and supper, and then a final burst of activity in the evening."
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Chris St. Myers, Threat Intelligence Lead at Stairwell, on how the company Inception platform can be used for finding old or new threats that sometimes may go unnoticed.

Cybercrime and threat intel
SE Asia's online scam ecosystem: The UN's Human Rights Commission estimates that roughly 220,000 people across Cambodia and Myanmar are being forced to work in call centers as part of online scam operations. Similar call centers also operate in Laos, Thailand, and the Philippines. The Commission says the scam centers generate revenue in the realm of billions of US dollars each year.
STAC4663: Sophos says that a threat actor it is tracking as STAC4663 has been using a recently patched vulnerability (CVE-2023-3519) in Citrix NetScaler devices to gain access to corporate networks and deploy ransomware.
New "Maldoc-in-PDF" technique: JPCERT/CC has discovered threat actors using a new technique in the wild. The technique involves embedding malicious Office documents inside PDF files in order to avoid detection.
Lockbit warning: Spain's national police issued a warning last week about a rise in phishing emails leading to LockBit ransomware infections.
SMS bombing: Indian security firm CloudSEK says that it discovered several underground tools for performing SMS bombing/flooding attacks that abuse SMS and OTP APIs at telcos around the globe.
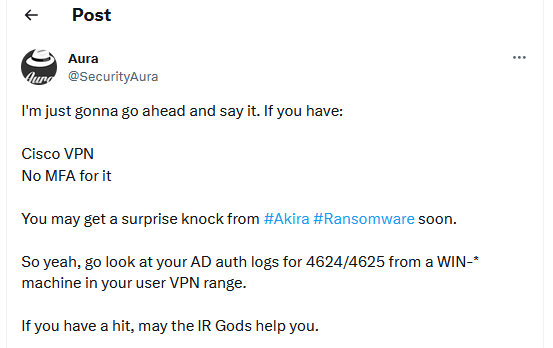
Akira attacks on Cisco VPNs: Cisco says it is aware of reports that the Akira cybercrime group is targeting Cisco ASA VPN devices in order to pivot to internal networks and deploy its ransomware. The attacks have targeted Cisco VPNs where multi-factor authentication has not been enabled. Cisco says threat actors are either conducting brute-force attacks or just buying compromised Cisco VPN credentials from dark web markets. Rapid7 researchers say the attacks are most likely brute-forcing of common Cisco ASA usernames such as admin, developer, test, and others (full list included in their blog post).
Malware technical reports
MMRat: Trend Micro has a report on a new Android malware strain named MMRat, currently distributed via third-party app stores. The malware is being used in your run-of-the-mill banking trojan and financial fraud operations. The malware has been used in campaigns targeting mobile users in Southeast Asia since late June 2023.
RemcosRAT: McAfee has an analysis of the RemcosRAT.
Nokoyawa infection chain: The DFIR Report has a write-up of a recent Nokoyawa ransomware infection that started from a good old phishing email exploiting the HTML smuggling technique.
Kinsing update: The Kinsing cryptomining botnet has incorporated a recent Openfire authentication bypass (CVE-2023-32315) in its exploitation arsenal. Cloud security AquaSec says that of the 5,000 Openfire servers it has discovered online, roughly 1,000 were still vulnerable. Taking into account that the vulnerability is three months old, an 80% patch rate is quite an accomplishment.
DreamBus botnet: On the same note, Juniper says it is seeing the DreamBus botnet now exploit a vulnerability (CVE-2023-33246) affecting RocketMQ servers. Just like in the Kinsing report above, this botnet focuses on cryptomining, and the vulnerability dates from May this year.
AttackCrypter: OALABS has an analysis of AttackCrypter, an open-source crypter used in recent VenomRAT campaigns.
Sponsor Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
UAC-0173: CERT-UA has a report on an AsyncRAT campaign carried out by the UAC-0173 group and targeting judicial authorities and notaries.
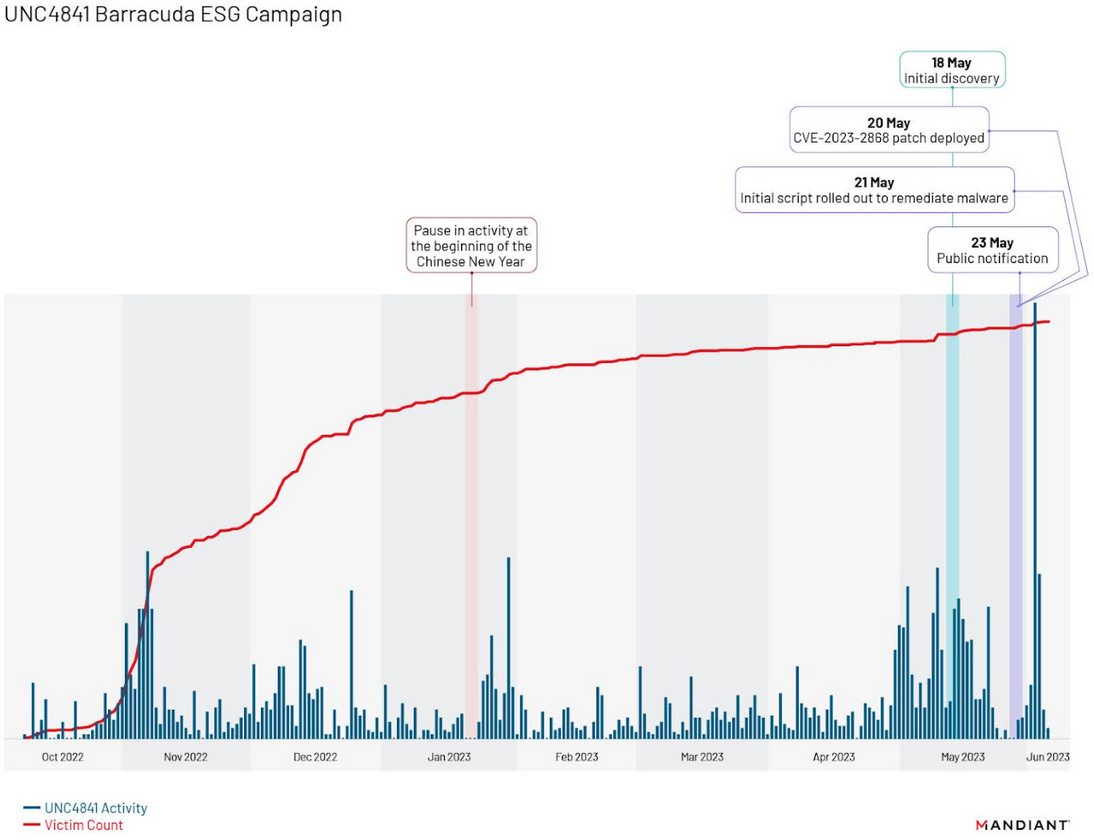
UNC4841 Barracuda hacks: Mandiant says the hacking campaign that targeted Barracuda email gateways compromised roughly 5% of the company's ESG appliances. The hacks took place between October 2022 and May this year, when Mandiant detected the intrusions and Barracuda released patches. Mandiant says that once patches were out, the attackers orchestrated a second campaign that used three new malware strains meant to bypass the patch and remain on infected devices. This second effort was focused on maintaining access to specific high-value targets in the government, military, telco, and aerospace industries. Barracuda told these customers to physically replace their ESG appliances. Mandiant linked the hacks to a suspected Chinese espionage group named UNC4841.
Vulnerabilities, security research, and bug bounty
BGP software flaws: A major vulnerability has been discovered in multiple BGP routing software products that can be exploited to create BGP worms and crash entire networks. The vulnerability resides in how routing software handles corrupt BGP route attributes. Vulnerable software includes the router operating systems of Juniper, Nokia, and Extreme Networks and network devices that use the FRR and OpenBGPd open-source packages. BGP.tools founder Ben Cartwright-Cox says he contacted vendors about the vulnerability, but patches are not yet available.
D-Link vulnerabilities: D-Link has patched 52 vulnerabilities discovered this summer by ZDI researchers. The bugs range from hardcoded credentials to firmware issues, and they impact the company's DAP-2622 router and access point products.
Techview vulnerabilities: Exploit Security has published details about three vulnerabilities impacting Techview routers.
BusyBox vulnerability: Pentagrid researchers have published details on CVE-2023-39810, a BusyBox directory traversal vulnerability.
Qlik Sense RCE: Security firm Praetorian has discovered an RCE in Qlik Sense, a business data analytics platform used for data visualization and analysis.
Java code exec PoC: Indian security researcher Bipin Jitiya has published a PoC for CVE-2023-21939, a code execution vulnerability in Java SE.
"Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Java SE, Oracle GraalVM Enterprise Edition accessible data."
AMSI bypass: Russian security researcher Michael Zhmaylo has published details on a new AMSI bypass method that uses the Windows process debugger mechanism.
New Battery Sleuth technology: A student from the University of Michigan has developed a hardware device that can be installed on modern cars and prevent hacks of the car's keyless entry system. The device is installed separately from all other car systems and works by limiting electric current from the battery to the car's starter until it detects a specific voltage fluctuation. This fluctuation can come from a fingerprint scan or a PIN code entered on the device's numerical pad. Named the Battery Sleuth, the device has been found effective against all car hacking kits.
Infosec industry
New book: "Philosophy of Cybersecurity," a book from Polish researcher Lukasz Olejnik, is now available to pre-order (discount codes available). The book tackles topics like user security, healthcare, critical infrastructure, policy, politics, international law, and cyberwarfare and how they mix together, complete with examples.
Acquisition news: Malwarebytes has acquired Cyrus, a provider of online privacy solutions.
Acquisition rumors: Private equity firm Veritas Capital is exploring buying BlackBerry, a provider of IoT and cybersecurity software.
New tool—SysReptor: Pen-testing company Sysfilters has open-sourced SysReptor, an offensive security solution for generating pen-test reports.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how asset inventory tools aren't a substitute for knowing what a business values.




