Risky Biz News: Fastly to block domain fronting in 2024
In other news: Windows Hello authentication bypassed; Pegasus spyware found in Serbia; and 21 Chinese anti-censorship tools disappeared overnight.
This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Internet infrastructure company Fastly will block domain fronting on its cloud platform from February 27, 2024.
Fastly now joins a growing list of major cloud companies that have banned domain fronting. The list includes Amazon (banned in 2018), Google (2018), Microsoft (2022), and Cloudflare (2015).
Domain fronting is a technique to use different domain names on the same HTTPS connection.
The technique became popular in the early 2010s in the mobile app development ecosystem, where developers would configure their apps to connect to a "front" domain that would then forward the connections to the developer's backend. This way, the developer could expand their backend to deal with growing traffic and new features without constantly having to release app updates.
Since then, the technique has expanded and has been adopted by online services like Tor, Telegram, and Signal to bypass internet censorship attempts in oppressive countries. The Tor Project maintains a list of CDN providers and their support for domain fronting, a core feature that allows its users to find and connect to new relays.
Because of its ability to hide backend infrastructure, domain fronting has also become popular with malware operations, being adopted by both financially and espionage-motivated groups.
Fastly began notifying customers about its intention to stop supporting domain fronting at the end of October.
Two weeks later, Microsoft notified Azure customers that it was tightening the screws on its domain fronting 2018 block. Customers who were grandfathered in with the 2018 block will have to make additional changes to their server infrastructure by January 8, 2024.
Back in 2018, when both Amazon and Google blocked domain fronting on their platforms, everyone suspected the Russian government was putting pressure on the two companies. At the time, the Russian government blocked 1.8 million AWS and Google Cloud IP addresses in an attempt to block access to Telegram's instant messenger.
Lower in today's edition of this newsletter, you'll find an entry on how 21 anti-censorship tools maintained by Chinese developers and meant to bypass China's Great Firewalls were removed at the same time from GitHub—all on November 2 and 3.
Prior to that, the Chinese government also ordered that any online account with more than 500,000 followers must share their real name. The government pressured seven of the major Chinese social media platforms to abide by this rule in an attempt to prevent the subversion of its power and influence in cyberspace.
With the proximity of all these announcements, one might wonder if the Chinese government might have applied some pressure. Sadly, we cannot answer this, although things are not as dire as they look.
An academic study published in October this year found that 22 out of 30 tested CDN providers still support/allow domain fronting in some form or another, including major providers like Akamai, CDN77, and Lumen.
Breaches, hacks, and security incidents
Pegasus in Serbia: Traces of the Pegasus spyware have been found on the smartphones of two members of the Serbian civil society. The victims learned of the infection at the end of October after receiving a notification from Apple. The SHARE Foundation says it will not name the victims to protect their identities, but it will work with Access Now and Amnesty International to investigate the hacks.
Fidelity National Financial: Insurance company Fidelity National Financial has shut down some of its IT systems in the aftermath of a major cyberattack. The Florida-based company disclosed the incident a day before the Thanksgiving US holiday, shortly after the intrusion took place. As soon as it was made public, the AlphV ransomware operation took credit for the intrusion. Fidelity National Financial is the largest title insurance company in the US, and the incident is preventing the closure of some real estate transactions. [Additional coverage in RealEstateNews]
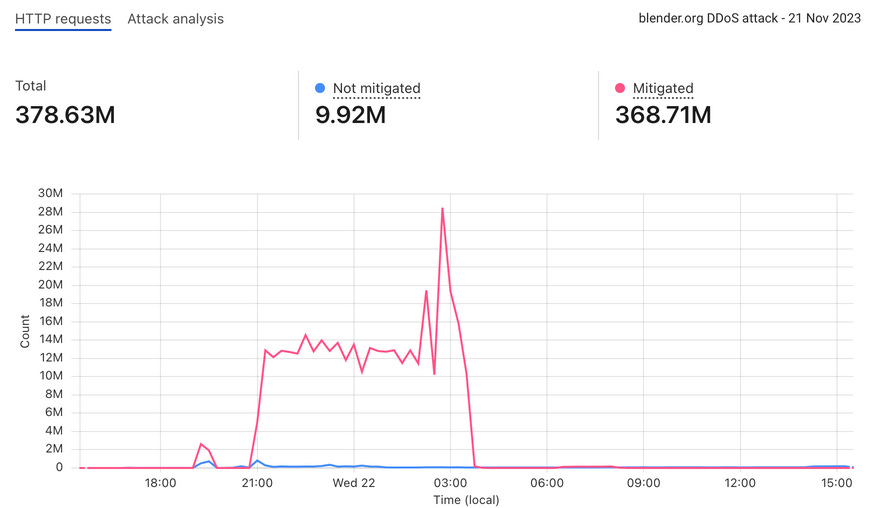
Blender DDoS attacks: Some psychopath is DDoSing the website of Blender, an open-source 3D design application. Blender says the attack peaked at over 28Mrps, which is quite the number. I've seen some weird DDoS attacks, but... Blender!?! Really!?!
General tech and privacy
GFW anti-censorship tools are disappearing: At least 21 tools meant to bypass China's Great Firewall and other state censorship tools have been removed from GitHub. All the tools were maintained by Chinese developers and were removed on November 2 and 3, showing some level of coordination either from the developers or from authorities. Western privacy experts believe the Chinese government managed to deanonymize and pressure the developers into removing the tools. The move comes after China is cracking down on internet anonymity. Earlier this month, the Chinese government ordered that any online account with more than 500,000 followers must share their real name. [Additional coverage in TechCrunch]
Twitter misinformation: NewsGuard has published a report detailing how ads from 86 major advertisers appeared next to tweets promoting "some of the most egregious false or misleading claims about the [Israel-Hamas] war."
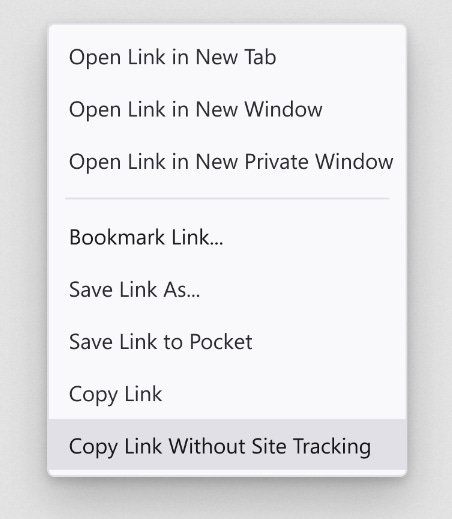
Firefox 120: Mozilla has released Firefox 120. New features and security fixes are included. The biggest changes in this release are the ability to copy URLs without site tracking parameters and a limited test (in Germany) to automatically block those annoying cookie banners.
Government, politics, and policy
Australian Cyber Security Strategy: The Australian government has published its Cyber Security Strategy for the 2023-2030 period. The plan describes a government-wide effort to improve the country's cybersecurity posture. Major points include the introduction of a no-fault, no-liability ransomware reporting requirement and a possible ban on some ransom payments. It also plans to set up "cyber rapid assistance" teams to help Pacific island nations respond to cyber attacks. The government has allocated AUS$586 million for the strategy's implementation. [Additional coverage in ABC]
New US Navy cyber strategy: On the same topic, but on a much smaller scale, the US Navy has also released its cyber strategy. This is the first time the Navy has put together and released such a document. [Additional coverage in DefenseScoop]

Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Derek Hanson, Yubico VP of Solutions Architecture and Alliances, about the state of authentication and what Passkeys are all about.
Cybercrime and threat intel
Killnet leader dox: In a surprising turn of events, a regime-controlled news outlet has doxed and revealed the real-world identity of Killmilk, the leader of the infamous pro-Kremlin hacktivist group Killnet. According to Russian news outlet Gazeta, Killmilk is a 30-year-old named Nikolai Nikolaevich Serafimov. The news outlet says it learned of Killmilk's identity from two Russian hacktivist groups, and they later confirmed the dox with a source in Russian law enforcement. This is quite an interesting turn of events!
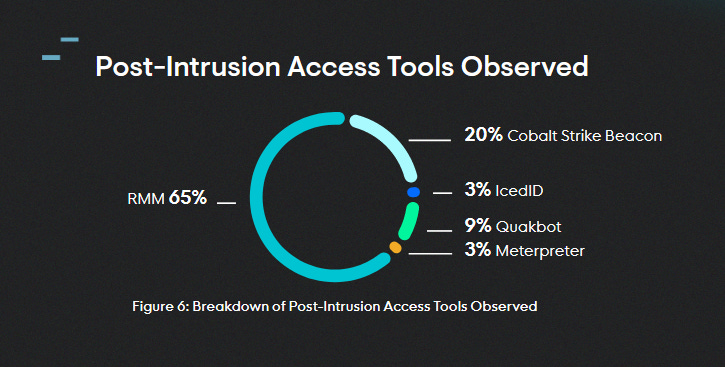
RMM abuse: Huntress Labs' Q3 threat report is out, and the company highlights the rise in abuse of legitimate remote monitoring and management (RMM) software by threat actors in post-intrusion activity.
Malware technical reports
ParaSiteSnatcher: Trend Micro looks at ParaSiteSnatcher, a framework used by threat actors to create malicious Chrome extensions to monitor and steal data from user browsers. Trend Micro says the framework has been used in the wild to create Chrome extensions that target Brazilian users.
InfectedSlurs botnet: A new Mirai-based botnet is exploiting two unpatched zero-days to take over smart IoT devices and carry out DDoS attacks. Named InfectedSlurs, the botnet began operating in late 2022, but its activity ramped up in October this year after the addition of the two zero-days. The two zero-days impact router and network video recorder (NVR) models. Security firm Akamai says it won't reveal the vendor and model names until patches are available—in order to prevent additional exploitation.
WSO-NG: Akamai has published a technical write-up of WSO-NG, a pretty common web shell family that's been around for almost 14 years.
Lu0bot: Trend Micro looks at a recent infection with the Lu0bot malware.
IPStorm: Security researcher Ian French has published an analysis of the IPStorm proxy malware, whose botnet was taken down by US officials this year.
DarkGate: Trellix has published a report on the evolution of the DarkGate loader, a malware strain that appears set to replace QakBot in the hearts of most malware operators. A similar report on DarkGate is also available from Sekoia.
WailingCrab: IBM X-Force has published an analysis of WailingCrab, a malware loader strain also known as WikiLoader. The report covers recent malware updates relating to its C2 communication mechanisms, which include support for MQTT connections.
Vidar servers: A Censys scan of the internet has discovered the IP addresses of 22 command and control servers used by the Vidar infostealer.
Atomic Stealer: Malwarebytes is seeing malvertising campaigns push fake browser updates infected with the AMOS, aka Atomic Stealer, a macOS-centric infostealer.
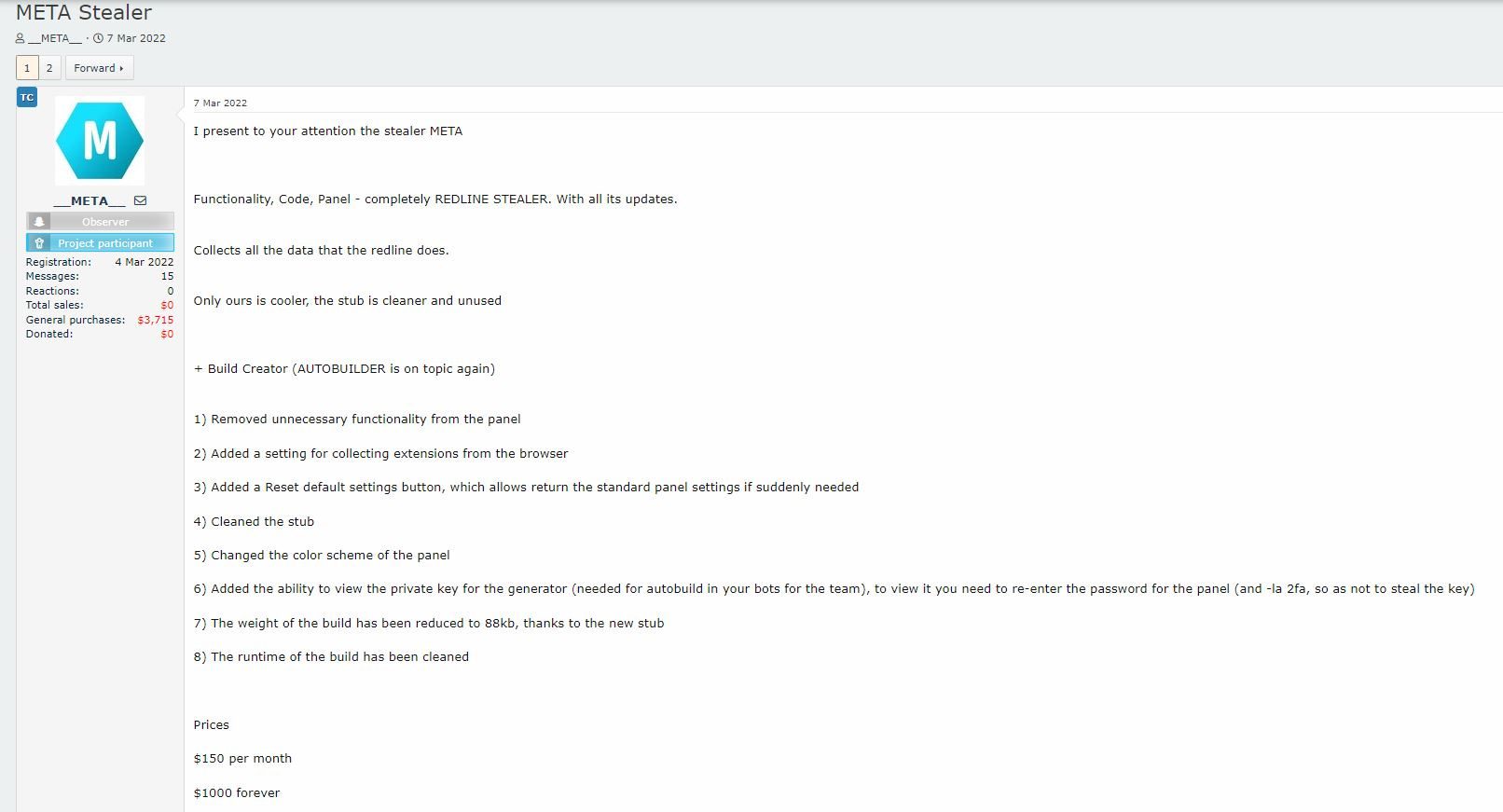
MetaStealer: eSentire researcher RussianPanda has published an analysis of MetaStealer. The infostealer launched in March 2022 and incorporates a lot of code from Redline Stealer, as its creator candidly admitted back then. The malware is different from the MetaStealer that SentinelOne discovered earlier this year, which is written in Go and targets macOS exclusively.
Sponsor Section
Brought to you by Yubico, the inventor of the YubiKey, a security key that provides the gold standard for multi-factor authentication (MFA) and stops account takeovers in their tracks. Find them at yubico.com
APTs, cyber-espionage, and info-ops
HrServ: Kaspersky researchers have discovered a new web shell named HrServ that has been secretly installed on hacked Microsoft Exchange servers across the world. The malware can hide and execute in a server's memory and appears to have been in use since 2021. Kaspersky says the only victim they managed to identify based on its telemetry is a government organization in Afghanistan. The security firm described the malware as sophisticated and believes to be the work of an APT group.
Another DPRK supply chain attack: A North Korean hacking group has carried out a supply chain attack using the infrastructure of CyberLink, a Taiwanese company that develops multimedia software products. Tracked as Diamond Sleet (Zinc, Temp.Hermit, Labyrinth Chollima), the group hid the LambLoad malware in the company's legitimate applications. The incident took place at the end of October and had limited impact. Microsoft says the malicious activity only impacted around 100 devices across the world, with most victims in Japan, Taiwan, Canada, and the US.
Kimsuky alert: The South Korean National Police Agency (KNPA) has published a security alert warning of a Kimsuky spear-phishing campaign impersonating government and news media organizations. More than 1,400 users have received emails so far, according to officials.
Russian disinfo: Israeli news site Haaretz has found a cluster of Kremlin-run accounts pushing disinformation about the Israel-Hamas war. The campaign included antisemitic graffiti painted by foreign actors in Paris and fake news stories in various languages.
Vulnerabilities, security research, and bug bounty
Windows Hello bypass: Security researchers from Blackwing Intelligence have bypassed Windows Hello fingerprint authentication on Dell Inspiron, Lenovo ThinkPad, and Microsoft Surface Pro laptops. The researchers targeted the Secure Device Connection Protocol (SDCP) and how device manufacturers implemented the protocol. Blackwing says that while Microsoft did a "good job" at designing some parts of the SDCP, two of the vendors they tested didn't even enable it. The research was sponsored by Microsoft's MORSE security team and aimed to test the security of the top three fingerprint sensors used for Windows Hello authentication.
InfStones vulnerability: Blockchain security firm dWallet Labs has disclosed a vulnerability in blockchain infrastructure provided by InfStones. According to dWallet Labs, an attacker who exploits the vulnerability can take over servers and extract the private keys of validators hosted on InfStones infrastructure. Researchers say the vulnerability impacts transaction validators for different blockchains, such as ETH, BNB, SUI, APT, and others.
WordPress admin password reset bug: Wordfence has discovered a vulnerability in the UserPro WordPress plugin that can let attackers reset an admin account's password.
ActiveMQ vulnerability: PRIOn security researchers have published an analysis of CVE-2023-46604, an actively exploited vulnerability in Apache ActiveMQ servers.
OpenCMS vulnerabilities: watchTowr Labs has published a write-up on four vulnerabilities in the OpenCMS platform that got patched at the end of October.
Kubernetes security updates: The Kubernetes project has released a security update to fix a privilege escalation on Container-Optimized OS and Ubuntu nodes.
Atlassian security updates: Atlassian has released 22 security updates.
NCSC challenge coins: The UK NCSC plans to provide special challenge coins (pictured below) to the top security researchers who reported vulnerabilities in UK government sites via the NCSC's bug bounty program.

Infosec industry
SAINTCON 2023 videos: Talks from the BlueHat 2023 security conference, which took place in October, are available on YouTube.
Buggy Fortinet alerts: Fortinet alerts for its monthly security updates are not DMARC-signed and are getting sent to spam folders. Someone at Fortinet might wanna look into that.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how being more open about cybersecurity threats is great for marketing and has also forced cybersecurity companies to pick sides and make value judgements.




