Risky Biz News: DOJ and FTC tell companies to stop deleting chats
In other news: NSA confirms buying netflow data; spyware scandal unfolds in Brazil; and fewer ransomware victims are paying.

This newsletter is brought to you by enterprise browser maker Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Federal investigators are warning companies not to delete chats and preserve conversations that have taken place via business collaboration and ephemeral messaging platforms.
In press releases on Friday, the US Department of Justice and the US Federal Trade Commission announced that they updated the language in their preservation letters and specifications—documents they send to companies under federal investigations.
The new language updates evidence preservation procedures to cover modern tech stacks such as Slack, Microsoft Teams, and Signal.
Companies that receive subpoenas or other legal notifications will have to take steps to preserve chat logs and disappearing IM messages.
Companies that fail to comply will be charged with obstruction of justice.
"These updates to our legal process will ensure that neither opposing counsel nor their clients can feign ignorance when their clients or companies choose to conduct business through ephemeral messages," said Deputy Assistant Attorney General Manish Kumar of the Justice Department’s Antitrust Division.
The new guidance comes as the DOJ faced difficulties in its Google and Amazon antitrust lawsuits.
In February 2023, the DOJ accused Google of lying when it claimed it auto-suspended its chat auto-deletion feature. In addition, the DOJ claimed that for a period of four years, Google trained employees to delete internal chats and move conversations to off-the-record platforms because it anticipated facing antitrust litigation in the near future.
In November 2023, the FTC similarly accused Amazon of deleting more than two years worth of internal Signal employee chats after the agency started a multi-state antitrust lawsuit.
Breaches, hacks, and security incidents
Mercedes-Benz leak: German automaker Mercedes-Benz accidentally exposed all of its source code after it left a GitHub access token exposed online. Security researchers from RedHunt Labs discovered the leak. Researchers say the token granted access to the company's GitHub Enterprise Server, where they found API keys to pivot inside the company's Azure and AWS cloud infrastructure. [Additional coverage in TechCrunch]
SolarWinds files to dismiss SEC lawsuit: Software maker SolarWinds has filed a motion to dismiss its SEC lawsuit in a New York court. The SEC sued SolarWinds and its CISO in October of last year arguing that the company lied about its cybersecurity posture to investors for years before it was hacked in 2020. SolarWinds says it disclosed all risks surrounding its business and informed investors when the hack took place. In a statement to Bloomberg Law, the company argues that the SEC is trying to "move the goalposts" and create new reporting requirements about a company's internal cybersecurity programs.
General tech and privacy
Windows Server 2025 & Insiders: Microsoft has launched an Insiders distribution channel for the Windows Server operating system. The channel will be used to test Windows Server features before they are shipped. The new channel will be available for Windows Server 2025, the next version of the Windows Server OS, announced on the same day. Windows Server 2025 will ship with universal hotpatching support, new versions for the AD and SMB protocols, Hyper-V and AI support.
Notepad update: Microsoft's engineers are working on sandboxing the Notepad editor's process.
Meta's data scraping case: A US judge ruled that Israeli company Bright Data did not violate Meta's terms of service when it scraped data from Facebook and Instagram. Meta sued the company in February 2023. The judge ruled that Bright Data didn't violate Meta's terms of service because it wasn't logged into a Meta account when it did the scraping—hence, the information was public anyway. As part of its defense, Bright Data revealed that Meta was one of its past customers and had paid past to scrape other websites. [Additional coverage in CourthouseNews]
Twitter propaganda: Ahead of elections all over the world, Twitter is currently flooded with the most abhorrent political disinformation and misinformation. Some examples flooding the site these days. [Additional coverage in DerSpiegel, NYT, and Vice]
iOS notification abuse: Multiple popular iOS apps are abusing the short time interval they receive a notification to send analytics back to their servers. The hidden behavior was discovered by German security researcher Tommy Mysk. The researcher says the apps are abusing a feature introduced in iOS 10 that allows apps to be woken up for a short period of time to process a notification before being put back to sleep. Mysk says that apps such as Facebook, TikTok, Twitter, LinkedIn, and Bing are abusing this small time window to collect and track users on their phones.
Government, politics, and policy
Brazil spyware scandal: Brazilian authorities have started an investigation against the country's former intelligence chief for organizing a mass surveillance campaign against the political rivals of former president Jair Bolsonaro. Brazilian Federal Police say they raided several homes owned by Alexandre Ramagen, the former head of ABIN, the country's intelligence agency. Officials say Ramagen created a "parallel structure" inside ABIN that targeted state governors, lawmakers, judges, and journalists. The ABIN unit allegedly used a spying tool named FirstMile, developed by Israeli company Cognyte. [Additional coverage in El Pais]
Ukraine cyber defense fund: The Danish government plans to send $13.25 million to boost Ukraine's cyber defense capabilities against cyber attacks.
USSS cyber board: The US Secret Service is reestablishing its Cyber Investigations Advisory Board. The Board was initially established in 2020 to help the agency overhaul its cyber investigations practices. The reestablished Board will include members from the public sector, academia, and non-profit organizations, who will advise the Secret Service on its cyber investigations. [Additional coverage in CyberScoop]
NSA confirms buying internet metadata: The US National Security Agency is buying internet traffic metadata known as netflow from commercial data brokers. The agency has confirmed the purchases in a letter to US Senator Ron Wyden. The NSA says it uses the data for mission-related activities, such as national security, cybersecurity, and foreign intelligence collection. NSA Director Paul Nakasone says the agency has taken steps to minimize cases where it buys data on Americans, such as not acquiring data from US smart cars. The agency also doesn't buy netflow data exchanged between US internet providers, but it buys netflow data between US and foreign providers.

Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Bradon Rogers, Chief Customer Officer at enterprise browser Island, on how a modern enterprise browser solution like Island can be used to replace, complement, or enhance some enterprise security tools or technology stacks.
Cybercrime and threat intel
Ransomware operator sentenced: A Canadian judge has sentenced an Ottawa man to two years in prison for launching ransomware attacks. Officials say Matthew Philbert infected more than 1,100 victims with ransomware using malicious emails. The 33-year-old is believed to have made $50,000 from his attacks, and some of his victims included police departments and children's charities. [Additional coverage in CBC]
Russian hacker detained: Ukraine's Security Service SBU has detained a member of pro-Kremlin hacking group Russia's Cyber Army. The suspect was identified as an IT specialist from Kharkiv who was recruited by the FSB through a specialized Telegram channel. Officials say the suspect prepared DDoS attacks against Ukrainian government sites and also adjusted Russian strikes against civilian targets in Kharkiv.
Serial swatter arrested in California: The FBI has arrested a 17-year-old from California on charges of orchestrating hundreds of swatting attacks across the US. Officials have described the teenager as one of the most prolific swatters in American history. He is suspected of orchestrating swatting events targeting schools, politicians' homes, courthouses, and religious institutions. The unnamed teen is also suspected to have operated Torswats, a Swatting-as-a-Service operation hosted on a Telegram channel. [Additional coverage in Wired]
Ermakov profile: Threat intel firm Intel471 has published a profile on REvil member Aleksandr Gennadievich Ermakov, the Russian behind the Medibank attack, recently sanctioned by Australian, UK, and US officials. In the meantime, there's a discussion that the ASD might have identified the wrong REvil member behind the Medibank attack.
Knight interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operators of the Knight ransomware, a revamped version of the older Cyclops RaaS.
Malvertising in China: Malwarebytes looks at some malvertising campaigns targeting Chinese consumers with boobytrapped instant messaging apps.
Treewolf: Chinese security firm Duba Security has published a report on Treewolf, a threat actor infecting Chinese users with malware using classic state tax administration lures.
Dark Mosquito: Chinese security firm Antiy has published a report on Dark Mosquito, a threat actor targeting Chinese users with Windows, Linux, and macOS malware. Most of the group's operations rely on pirated software and malicious ads to deliver their payloads.
YouTube AI scam ads: It took an investigation and public shaming from a news outlet for Google to delete thousands of AI-generated ads that promoted Medicare scams for months. [Additional coverage in 404 Media]
New npm malware: 767 (yes, 767) malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
2023 cybercrime trends: Security firm RedSense published a report with the most common trends spotted across the cybercrime ecosystem last year. Examples include "ghost" cybercrime groups, actor profile diversification, black hat SEO, and attempts to weaponize AI.
2023 mobile threats: Mobile security firm Lookout has published its year-in-review report for 2023. Just as before, Android threats dominated the threat landscape.
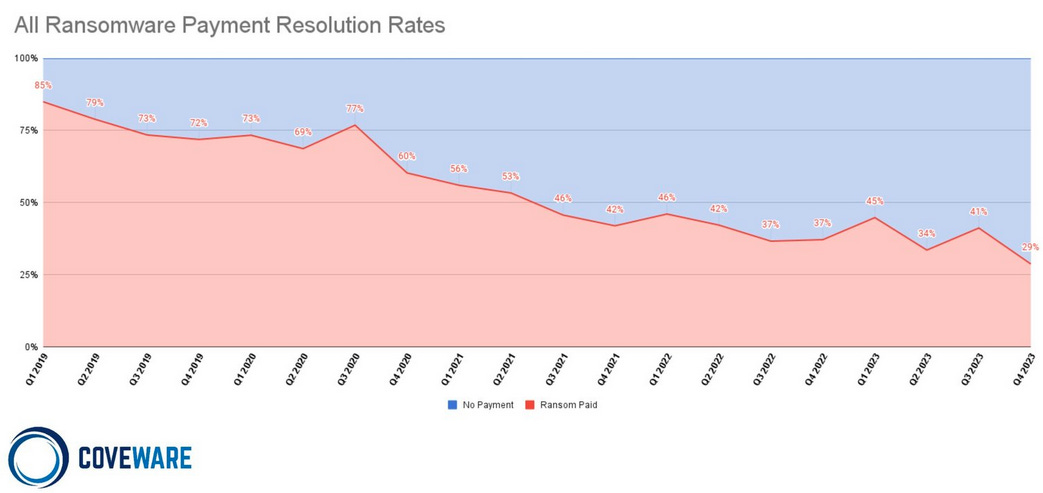
Fewer ransomware victims are paying: The number of ransomware victims who opted to pay ransoms fell to an all-time low at the end of last year. Cybersecurity firm Coveware estimates that 29% of victims paid ransoms in Q4 2023, down from the 85% registered in Q1 2019 when the company began tracking the stat. Coveware attributes the fall to improved data backup and recovery strategies in corporate environments and companies getting smarter about not trusting empty promises made by ransomware groups.
Malware technical reports
PixPirate: IBM's Trusteer security division has discovered a new Android RAT that is currently used in the wild in attacks targeting the customers of Brazilian banks. Named PixPirate, the malware heavily utilizes anti-research techniques and goes after payment details used by Pix, a popular Brazilian payment system.
"PixPirate is not only an automated attack tool, but it also has the capability of becoming a manually operated remote control attack tool. This capability is probably implemented to manually execute fraud if the automatic fraud execution flows fail because the user interface of the banking app changes or if a new lucrative target presents itself."
Rage Stealer: CyFirma researchers have discovered a new infostealer used in the wild. The stealer was created by a threat actor named "nsper" and is currently advertised on Telegram channels under names such as Rage Stealer, xStealer, and Priv8 Stealer.
RADX RAT: Russian security firm FACCT has discovered a new remote access trojan named RADX that is currently being used in attacks targeting Russian companies. Just like most of these things, the RAT is being advertised on underground forums.
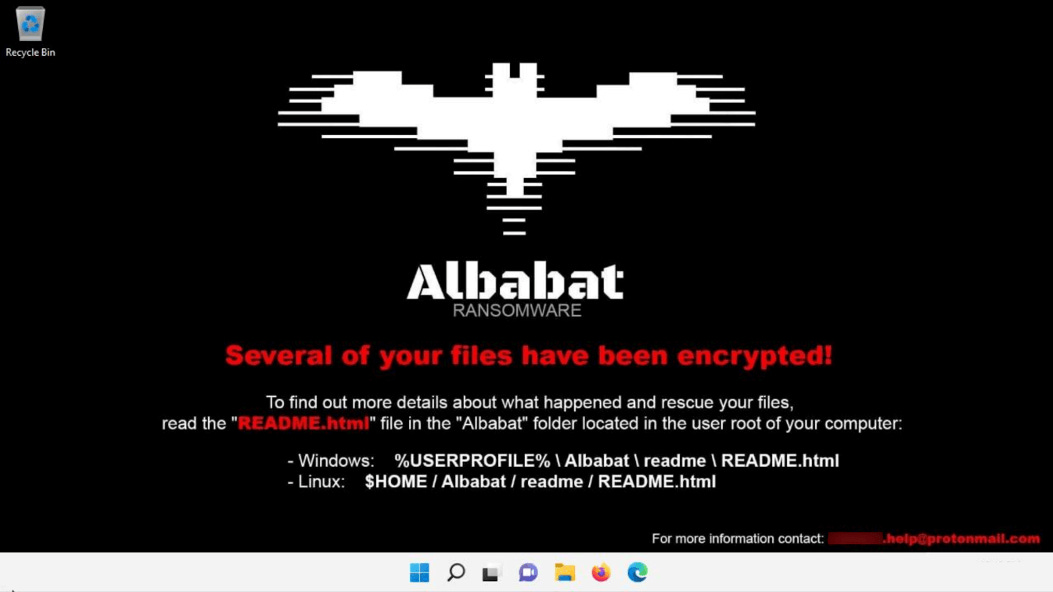
Albabat ransomware: Fortinet researchers have published a report on Albabat, or White Bat, a new ransomware strain they've spotted in the wild. Albabat is written in Rust, was first seen in the wild in November 2023, and appears to target home users, per Broadcom.
Sponsor Section
Island is an enterprise browser that embeds access policies, data protection, and security controls to create a safe environment that works on unmanaged as well as managed endpoints. Take a look at Island's essential features below [PDF].

APTs, cyber-espionage, and info-ops
Midnight Blizzard: Microsoft has published a technical report describing how Russian APT group Midnight Blizzard gained access to its corporate email servers after password-spraying a test tenant account last November. According to Microsoft, the hackers pivoted from the test tenant to its corporate environment via a legacy OAuth app that had access to both environments and with elevated privileges on the corporate environment. Former Yahoo and Facebook CSO Alex Stamos published a deep dive into Microsoft's report and rips the company a well-deserved new one for its weasely legalese.
Stately Taurus: A Chinese APT group known as Stately Taurus (Bronze President, Camaro Dragon, Earth Preta, Mustang Panda, Red Delta, Luminous Moth) is conducting cyber-espionage campaigns targeting Myanmar's Ministry of Defence and Foreign Affairs. The campaign is taking place as a coalition of three rebel groups have taken control of the northern Shan state from the Myanmar military junta. Chinese officials previously expressed concern regarding the war's effect on trade routes and security around the China-Myanmar border.
UNC5221's WIREFIRE: QuoIntelligence has discovered a new version of WIREFIRE, one of the web shells used by Chinese APT group UNC5221/UTA0178 in its exploitation of the recent Ivanti Connect Secure zero-days (CVE-2023-21887 and CVE-2023-46805).
Vulnerabilities, security research, and bug bounty
GitLab security update: GitLab has published security updates to address five vulnerabilities in its self-hosted solution.
Panda vulnerabilities: Cybersecurity firm Sophos has discovered three vulnerabilities in the driver of fellow antivirus maker Panda Security. The vulnerabilities can allow remote code execution attacks in some scenarios. Sophos says it discovered the bugs after a customer conducted an APT simulation test.
Jenkins RCE PoC: Public proof-of-concept code has been published for the recent and pretty bad RCE vulnerability in the Jenkins CLI component.
Infosec industry
New tool—SOAPHound: Cybersecurity firm FalconForce has open-sourced a tool named SOAPHound that can be used to enumerate Active Directory environments via the Active Directory Web Services (ADWS) protocol.
New tool—TeamsBreaker: Security group ASOT has released TeamsBreaker, a tool designed for automating the sending of phishing messages to Microsoft Teams users.
New tool—PurpleLab: Security researcher Krook9d has open-sourced PurpleLabs, a web-based lab setup for cybersecurity professionals to test detection rules, simulate logs, and undertake various security tasks.
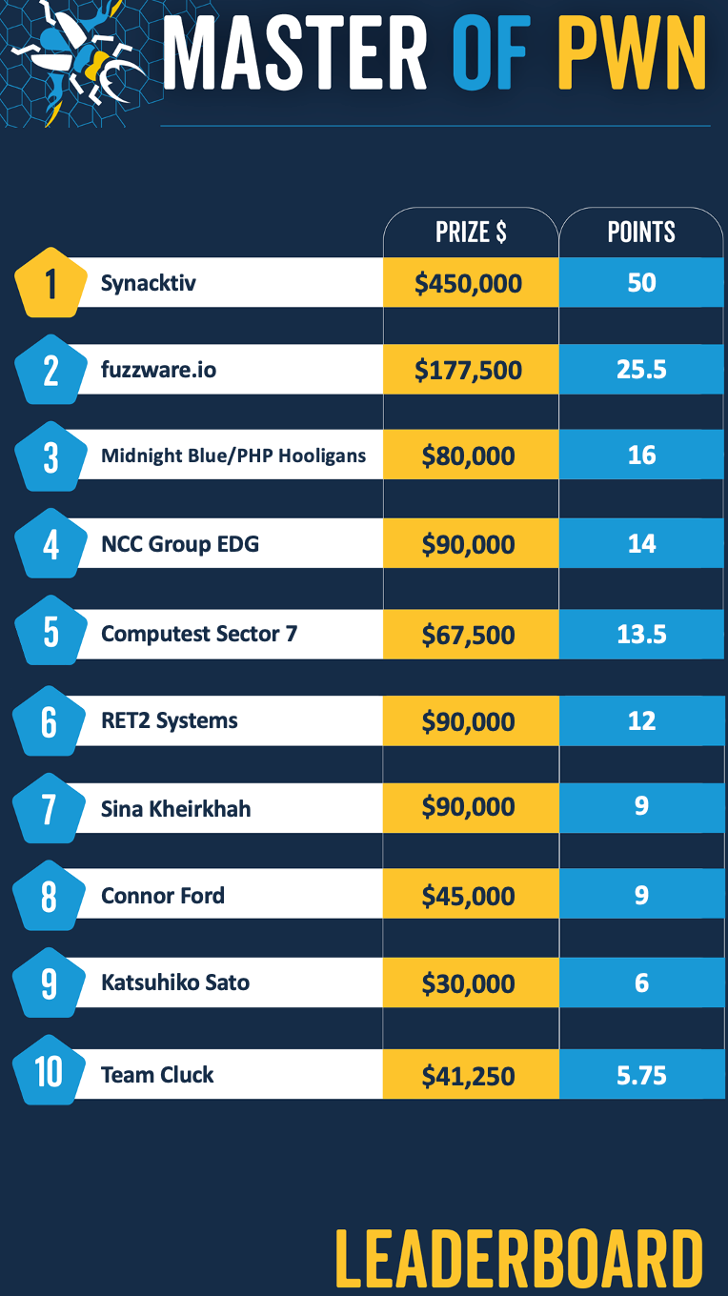
Pwn2Own Automotive: French security firm Synacktiv has won the first-ever edition of the Pwn2Own Automotive hacking contest, which was held last week in Tokyo, Japan. Contests used 49 different zero-days during the contest, earning more than $1.3 million in prizes for their efforts. Synacktiv alone took home $450,000, a third of the earnings. During the contest, researchers hacked Tesla cars, EV charging stations, and the Automotive Grade Linux operating system.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how having so much data available about Americans feels creepy, yet there is little visible harm to individuals. But there are still reasons to be worried.




