Risky Biz News: Disclosure snafu delays critical Exim patch more than a year
In other news: New major bug hits Progress (MOVEit) customers; Greek government sabotages spyware investigation; and IronNet ceases all operations.
This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A critical vulnerability impacting more than 3.5 million Exim email servers has remained unpatched for more than 15 months in one of the most egregious instances of vulnerability disclosure snafus in recent history.
Tracked as CVE-2023-42115, the vulnerability is a no-authentication remote code execution with a severity rating of 9.8/10.
It is one of six vulnerabilities that were disclosed by Trend Micro's Zero-Day Initiative (ZDI) to the Exim project in June 2022.
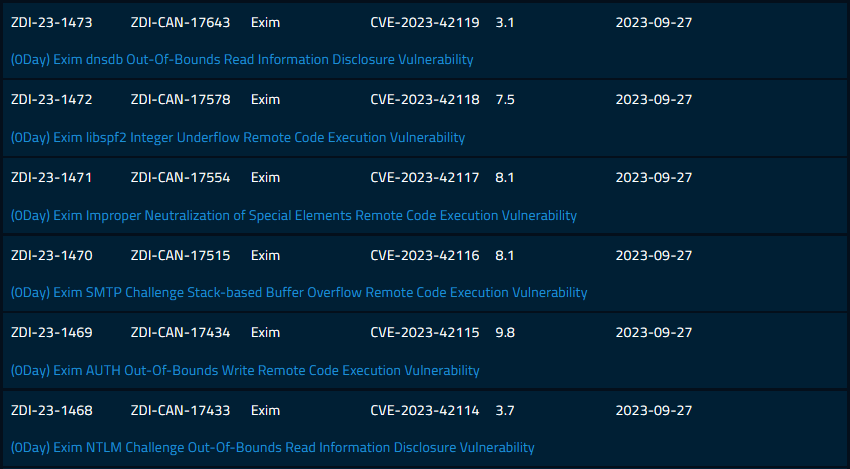
While you'd think a bug like this would get the Exim team's immediate attention, things didn't pan out as expected.
After the six vulnerabilities were publicly disclosed last week, the Exim team blamed ZDI for the lack of a timely patch. In a mailing list discussion, the Exim team says they received the bug report in June 2022, but the report lacked the necessary details to identify the root cause of the bug and release a patch. When they asked for additional information, ZDI took 11 months to provide a reply, only in May 2023.
Exim project member Heiko Schlittermann says they have patches for three of the six ZDI bugs, but they are currently only available via a private repository.
In a different mailing list discussion, Exim member Florian Zumbiehl says they have "no idea whether [the patch] actually addresses what ZDI has reported," suggesting ZDI has yet to provide an accurate description for the bugs they reported 15 months ago.
It's hard to blame any of the parties here, but this doesn't make any less of a clusterf**k.
For starters, ZDI intermediates bug reports between anonymous researchers and software vendors, meaning it can only relay what information the researcher makes available to its staff. If the researcher—credited as "Anonymous" in the Exim bugs—doesn't respond for 11 months or doesn't provide the needed information, it is hardly ZDI's fault.
Second, as the mailing list discussion shows, it's also hard to blame the Exim team either. It's impossible to patch a no-auth RCE without the proper details needed to identify the vulnerable component.
Playing the blame game also diverts our focus from the real problem—the fact that more than 3.5 million Exim servers are now waiting for a patch that's unclear if it will work.
With Exim accounting for 56% of email servers, this leaves more than half of the internet's email infrastructure exposed to dangerous attacks if threat actors manage to identify the root cause of the bug.
Obviously, the chances of active exploitation are pretty slim. If neither ZDI nor Exim are sure the current (private) patch works, an attacker won't figure out an exploit either.
Once a patch is out, server owners will need to hurry and apply it as soon as possible, regardless of whether it works or not. Threat actors will most likely rush to bin-diff the Exim code, identify the patched component, and attempt to exploit the bug.
Exim servers have been a target for hackers every time a major vulnerability has been available. What makes them attractive is the sheer number of systems available for exploitation, which makes it easy to always keep a botnet fed with new bots every few days.
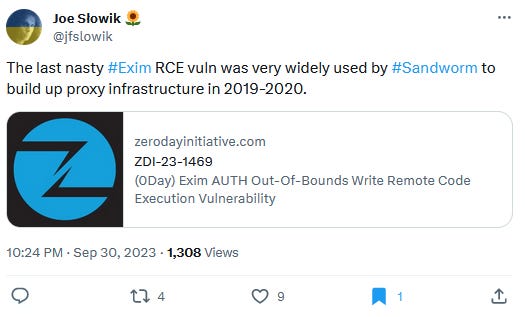
One of the most dangerous groups that has exploited Exim servers in the past includes Sandworm, a cyber-espionage unit inside Russia's military intelligence service. In May 2020, the NSA spotted Sandworm hacking Exim servers in order to build up its proxy infrastructure, which they'll likely attempt again if this new bug makes it possible.
Breaches, hacks, and security incidents
DarkBeam leak: Cyber risk management company DarkBeam has leaked more than 3.8 billion records after it left an Elasticsearch server unprotected on the internet. The database contained information from older breaches that DarkBeam was using to send alerts to customers. While the leaked data had already been public via separate smaller breaches, the DarkBeam leak has made it easier to download everything in one go. The company fixed the leaky servers as soon as it was notified. [Additional coverage in CyberNews]
General tech and privacy
Twitter fires election disinformation team: After disabling an election disinformation reporting tool, it appears that Elon Musk fired half of the election integrity team, even if he told EU officials he'd expand the team a month before. [Additional coverage in TechDirt]
BharOS leak: India's native operating system BharOS is just a badly disguised fork of GrapheneOS. The government research lab in charge of developing the operating system leaked its source code last week, which led to some interesting discussions among Indian experts.
Photoshop web versions: Adobe has released a web version of its Photoshop image editing software. Access is available to paid customers only.
Block Google's AI scrapers: Google now lets you use the robots.txt file to block its garbage and annoying AI scraping technology.
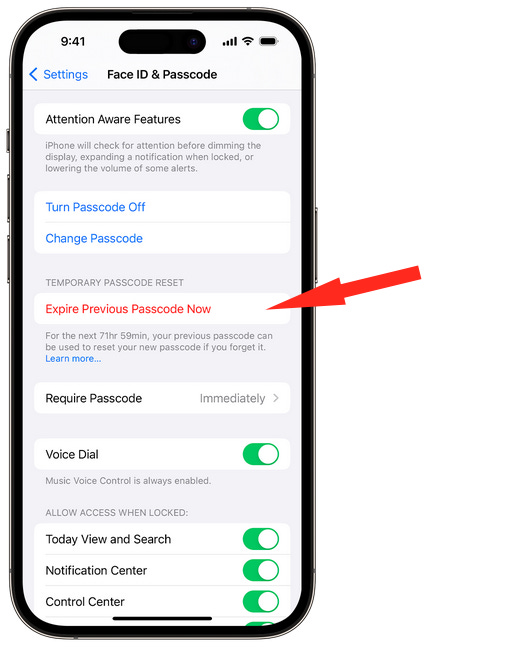
Stupid Apple iOS feature: The recently released iOS 17 operating system contains a new feature that will keep old passcodes alive for 72 hours after they've been changed. Apple says the feature is meant to allow users to re-access their iPhones in case they forget their new screen code. Security experts say the feature could allow threat actors to regain access to a device even if the account owner has changed an older passcode. Users can force older passcodes to expire immediately in the phone's "Face ID & Passcode" section—although this is not widely known by most iOS 17 users.
Government, politics, and policy
US AI Security Center: The US National Security Agency has announced the creation of an AI Security Center under the US DOD that will study and adopt AI technologies for national security and the defense industrial base. The new center will work with the intelligence community, the DOD, national research labs, and the US private sector, but also select foreign partners. The move comes after reports that China is exploring the use of AI for military weapons.
SBU infiltrated ransomware gangs: In an interview with NPR, Illia Vitiuk, Head of the Department of Cyber and Information Security of the Security Service of Ukraine (SBU), says the agency has had an influx of convicted cybercriminals who joined its ranks to help protect the country. Some of these volunteers have allegedly penetrated ransomware gangs, including "Russian ransomware groups working for special services."
Pegasus in Israel: Israeli officials have allowed local police to deploy the Pegasus spyware in a one-time case to investigate the murder of a Palestinian family. Officials have allowed police to use the spyware for surveillance but not to extract data from infected devices. [Additional coverage in the Times of Israel]
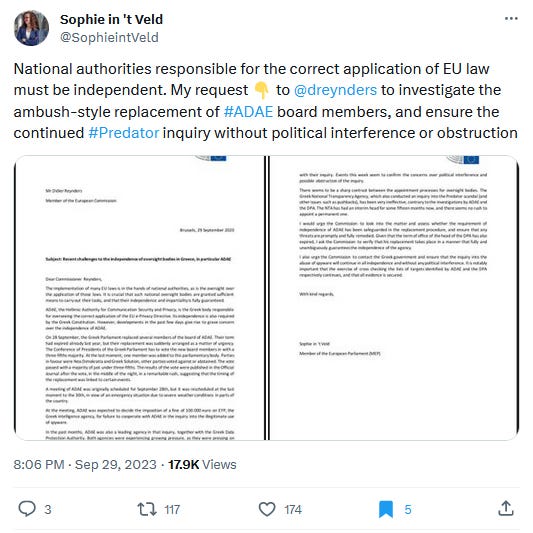
Greece spyware investigation: The Greek ruling government has sabotaged an independent commission meant to investigate the country's use of the Predator spyware. The Mitsotakis government replaced all members of the ADAE commission hours before they were set to meet and fine the EYP intelligence service for using spyware against civilian and political targets. The EYP was in line to receive a €100,000 fine. The move didn't go unnoticed and was criticized by the EU's PEGA commission, established to investigate spyware abuses across Europe. [Additional coverage in Reporter]
Sponsor section
In this sponsored podcast Proofpoint’s Selena Larson talks with Tom Uren about recent changes in the e-crime ecosystem.
Cybercrime and threat intel
French hacker pleads guilty: A member of the infamous ShinyHunters hacking group has pleaded guilty in a US court to hacking-related charges. Sebastien Raoult was one of three ShinyHunters hackers who breached companies all over the world and sold their data on underground forums. The 22-year-old Frenchman created phishing pages to compromise employee accounts, gain access to cloud resources, and then steal their data. US officials charged the trio in June 2021. Raoult was arrested in Morrocco last year and extradited to the US in January. Raoult used the hacker name of "Sezyo Kaizen." His two accomplices, Gabriel Bildstein (Gnostic Players, Kuroi) and Abdel-Hakim El-Ahmadi (Zac, Jordan Keso), are still at large.
Scammers detained in India: Indian authorities have dismantled a network of eight call centers in the city of Guwahati that conducted tech support scams. Authorities detained 250 workers, including three suspects believed to be the call centers' administrators. Officials say the three were part of an international gang with a presence all over India. Guwahati police say the call centers operated at night and used pop-up ads to trick people into calling for tech support. Callers were misled into installing malware on their systems and then tricked into making payments via bitcoin or gift vouchers. [Additional coverage in India Today]
New hacking forum: CyFirma security researcher Kaushík Pał has discovered a new hacking forum named SeekShell that launched earlier this year.
RaaS drama alert: The Donut Leaks ransomware gang is asking the INC Ransom group to not accept and publish any data from one of their past affiliates, who they describe as a scammer. Drama! We love it!
Malicious ads in Bing AI chat: Malwarebytes researchers have found malicious ads being injected and delivered via Bing Chat AI responses. AI is smart but not smart enough to spot malware, apparently.
Malware adopts smart contracts: A malware gang is storing parts of malicious JavaScript code inside smart contracts hosted on the Binance blockchain. The malicious code is used inside websites peddling fake browser updates that infect users with infostealers. According to FINSIN, the technique prevents security researchers from taking down the malicious code since it's not hosted on a web page but on an immutable blockchain.
New npm malware: Twenty-six malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Reddit malware incident: A threat actor tried to bait users of the r/cybersecurity subreddit to download malware on their systems. The lure was a collection of leaked credentials, and the final payload was the WarZone RAT.
AWS honeypots: AWS's threat intel team says that it takes roughly three minutes for threat actors to discover new honeypots and attempt to compromise them.
"This is an astonishingly short amount of time, considering that these workloads aren't advertised or part of other visible systems that would be obvious to threat actors. This clearly demonstrates the voracity of scanning taking place and the high degree of automation that threat actors employ to find their next target."
Clop torrents investigation: Back in June, the Clop gang began releasing some of the data from the MOVEit hacks as torrent files after it began having problems with its hosting infrastructure. Researchers from Palo Alto Networks have analyzed the seeds of the Clop torrent files and found that most of the stolen MOVEit files have been released through three IP addresses belonging to Moscow-based web hosting provider FlyServers.
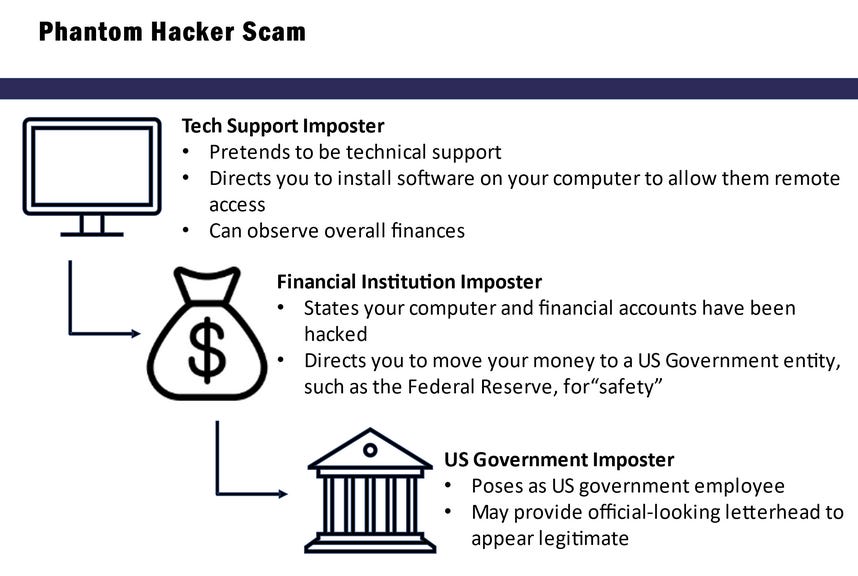
Phantom Hacker scams: The FBI is seeing an increase in a new scam targeting the elderly named Phantom Hacker. The scam relies on calling victims as bank representatives, telling users they've been hacked, and convincing them to move funds to a new account, typically under the scammer's control. The FBI says a recent variation of this scam involves three different scammers calling the victim, posing as representatives for banks, tech firms, and the government, in order to reinforce the need to move funds.
Malware technical reports
RustDeck malware: Dr.Web has identified several desktop remote-control Android apps that contain malware and are ranking high in search results on the Play Store. The apps are named AweSun Remote Desktop, RustDesk Remote Desktop, and AnyDesk Remote Desktop. Dr.Web says the apps are being used by threat actors to take control of Android devices and steal money from any installed e-payment apps.
BunnyLoader: A new MaaS service named BunnyLoader launched last month in underground malware forums.
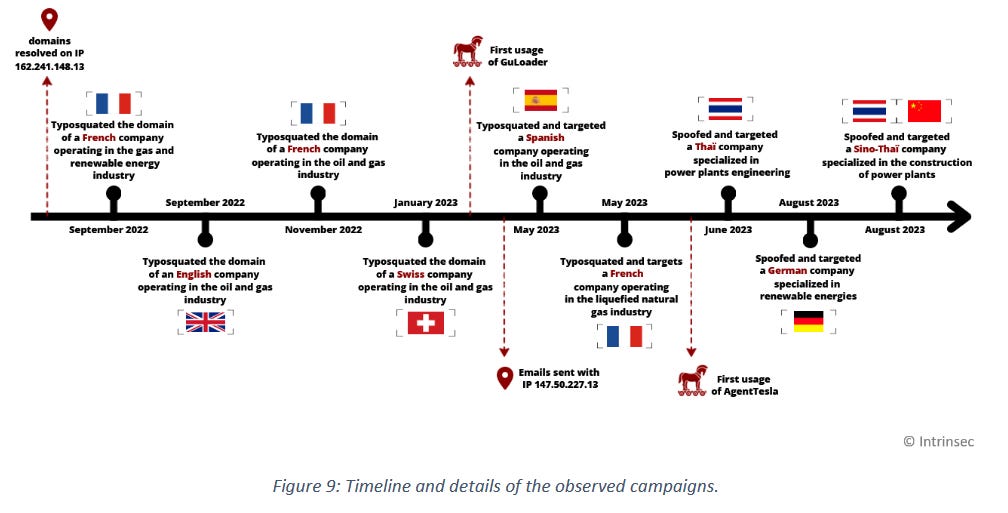
GuLoader: French cybersecurity firm Intrinsec has a 31-page report on the GuLoader malware, the Italian company behind it, and its recent campaigns.
Sponsor Demo Section
Ryan Kalember shows Risky Business host Patrick Gray Proofpoint's Sigma platform. Sigma is a data loss prevention and insider threat detection tool that crunches data from different sources and presents a unified view of it.
APTs and cyber-espionage
Lazarus poses as Meta recruiter: North Korean cyberespionage group Lazarus has compromised the network of a Spanish aerospace company by tricking an employee into running malware on a work computer. Security firm ESET says the attack was successful after Lazarus members posed as recruiters for Facebook's parent company Meta and asked the victim to solve two trojanized coding challenges. The hack took place earlier this year and infected the company with a stealthy new backdoor named LightlessCan. ESET says the attack was part of a long-running Lazarus operation named DreamJob, where Lazarus members pose as recruiters on LinkedIn.
Oilrig: The Oilrig (APT34) Iranian cyber-espionage group has launched attacks against Saudi targets with malicious documents that delivered a new variant of the SideTwist backdoor named Menorah.
Chinese disinformation efforts: The US State Department has published a report detailing China's disinformation efforts, its techniques, and goals.
"The PRC promotes digital authoritarianism, which involves the use of digital infrastructure to repress freedom of expression, censor independent news, promote disinformation, and deny other human rights. Through disseminating technologies for surveillance and censorship, often through capabilities bundled under the umbrella of "smart" or "safe cities," the PRC has exported aspects of its domestic information environment globally. Beijing has also propagated information control tactics, with a particular focus on Africa, Asia, and Latin America. In parallel, the PRC has promoted authoritarian digital norms that other countries have adopted at a rapid pace. As other countries emulate the PRC, their information ecosystems have become more receptive to Beijing's propaganda, disinformation, and censorship requests."
Vulnerabilities, security research, and bug bounty
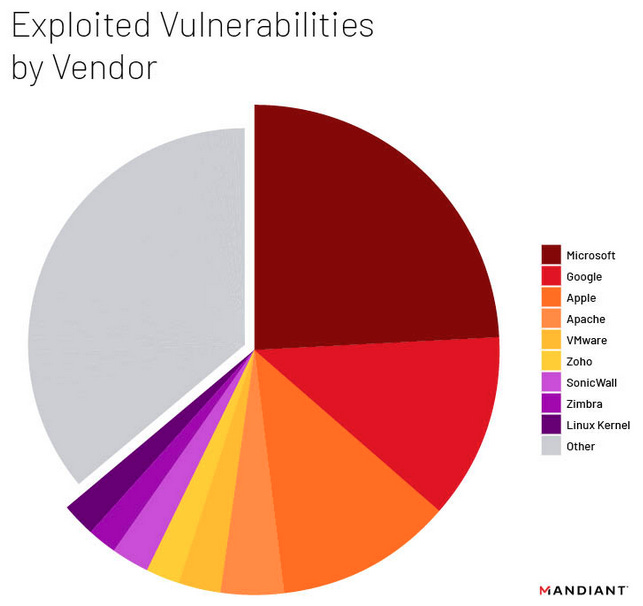
Vulnerability exploitation trends: Google's Mandiant division is seeing threat actors targeting a more diverse set of vendors and products than they did before. Mandiant says that over the past two years, Microsoft, Google, and Apple accounted for less than 50% of targeted vulnerabilities. This marked the first time products from the Big Three were targeted less than products from other vendors since Mandiant began tracking exploit attempts. The top other vendors included Apache, VMWare, Zoho, and SonicWall.
Progress WS_FTP security updates: The company behind the MOVEit file-sharing server has patched another set of critical vulnerabilities in another file-transfer application named the WS_FTP server. Eight bugs have received patches, including two with severity ratings of 10 (CVE-2023-40044) and 9.9 (CVE-2023-42657). Exploitation is trivial and requires one single HTTPS POST request. There are currently more than 550 WS_FTP servers connected to the internet, according to Shodan.
TeamCity exploitation: After a PoC was released last week, threat actors are now exploiting a vulnerability (CVE-2023-42793) in the JetBrains TeamCity CI/CD server to gain access to corporate repositories.
SharePoint PoC: A PoC was posted online for an RCE vulnerability in Microsoft SharePoint servers (CVE-2023-29357). The PoC comes after StarLabs researchers posted a detailed write-up of the bug last week.
"The exploit script facilitates the impersonation of authenticated users, allowing attackers to execute arbitrary code in the context of the SharePoint application pool and the SharePoint server farm account, potentially causing a denial of service (DoS)."
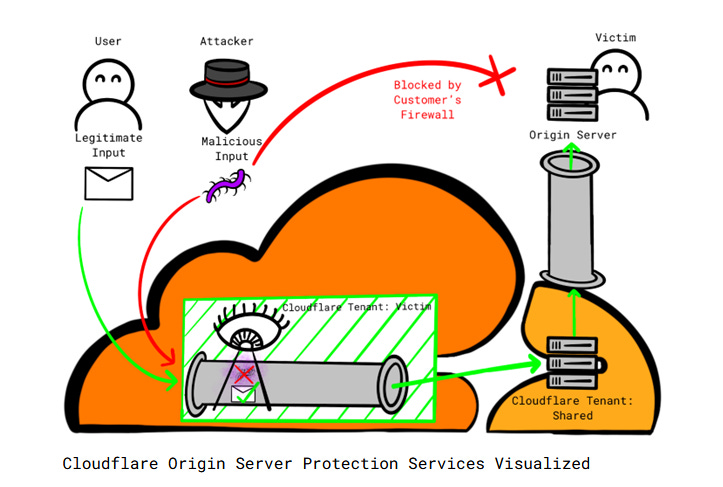
Cloudflare bypass: Security firm Certitude has identified a weakness in Cloudflare's platform that allows threat actors to bypass security features. The weakness is that Cloudflare automatically trusts any traffic originating from its own platform. Certitude says threat actors can host attack infrastructure on the platform and successfully target other customers, bypassing firewalls, bot protections, and other security protections. The company reported the issues to Cloudflare, but the report was closed without a fix.
Infosec industry
IronNet shuts down: Cybersecurity firm IronNet has ceased all operations across all subsidiaries after the company ran out of funds. In an SEC filing, the company says it plans to file for Chapter 11 bankruptcy proceedings. The news comes after the company furloughed the vast majority of its workers at the start of September. [Additional coverage in SecurityWeek]
New tool—DavRelayUp: ShorSec has open-sourced a tool named DavRelayUp to perform NTLM+LDAP relay attacks.
Malware code: The source code of the Sub7 trojan (from the late 90s) has been released on GitHub.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine how US and UK strategies to use cyber power differ but are in some ways mirror images of each other.




