Risky Biz News: DHS links pro-PRC info-op to Chinese municipal government
In other news: Russia cracks down on "gray" SIM cards; Sandworm hackers targeted Ukraine's military systems; and Curve Finance hacker returns most of the stolen funds.
This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
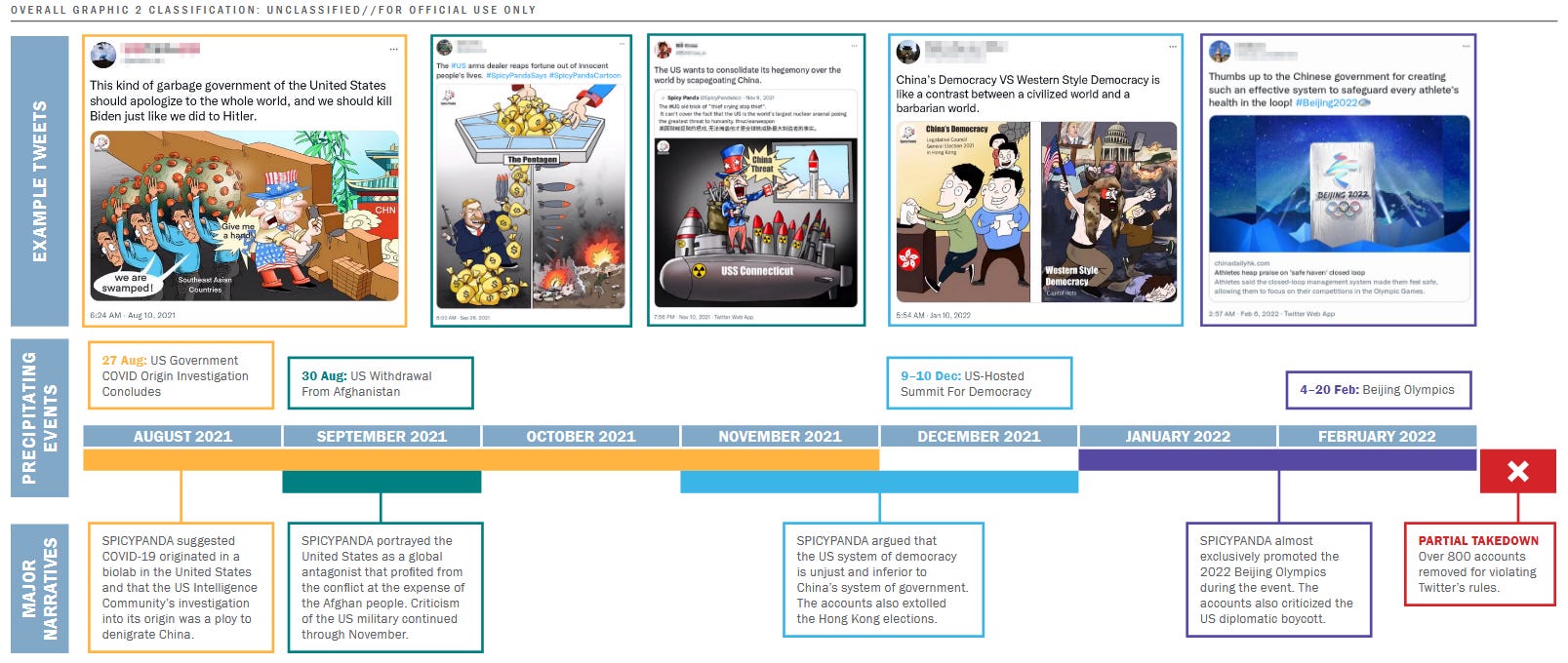
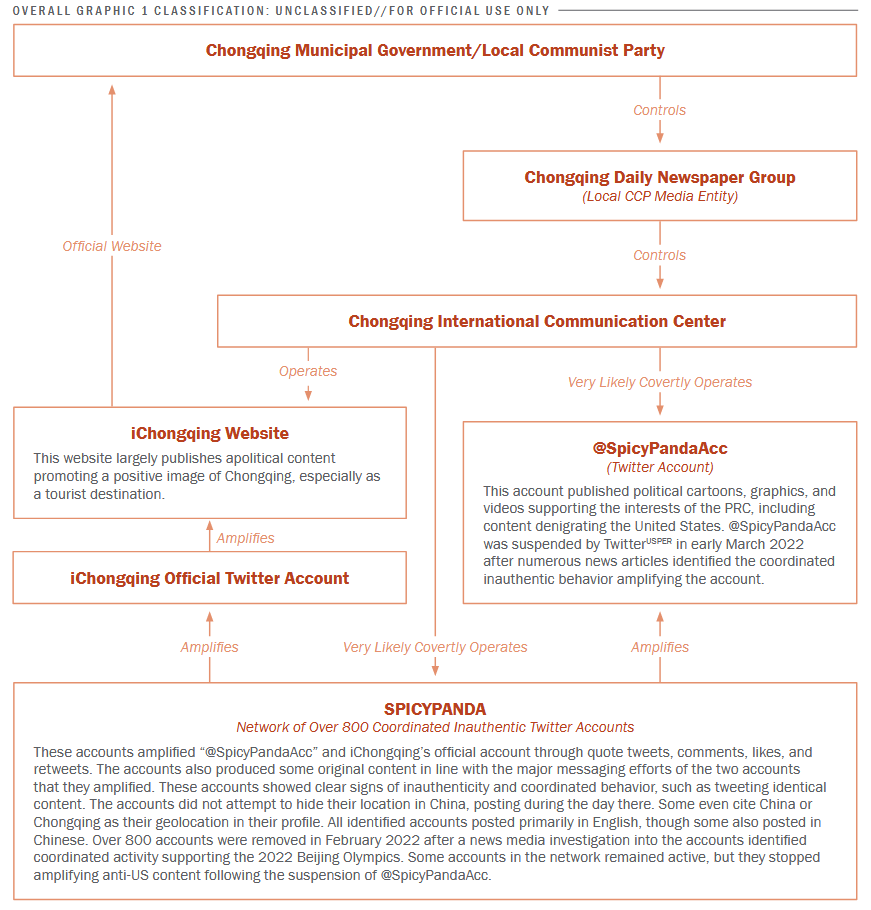
The US Department of Homeland Security has linked a Twitter disinformation campaign to a media organization managed by the municipal government of Chongqing, China's fourth largest city.
The US government says that the Chongqing International Communications Center (CICC) is behind a network of more than 800 Twitter accounts that consistently published anti-US and pro-PRC content.
The DHS says it tracked this network under the name of SPICYPANDA, and it believes it's part of a larger Chinese-backed disinformation effort tracked as DRAGONBRIDGE, or Operation Spamouflage.
According to a private intelligence note compiled by the DHS Office of Intelligence and Analysis and obtained by the Public Intelligence research project, SPICYPANDA was active on Twitter between January 2021 and February 2022, when the cluster was removed from the site.
The group primarily posted tweets portraying the US as a war-profiteering nation after its withdrawal from Afghanistan, tried to pin a US lab as the origin of the COVID-19 pandemic, criticized the US democratic system ahead of the White House-hosted "Summit for Democracy," and promoted PRC political views and the 2022 Beijing Olympics.
The DHS says that even if SPICYPANDA accounts were easy to spot, the operation was one of the most sophisticated and most responsive of all Chinese disinformation clusters.
"Despite using relatively unsophisticated accounts, SPICYPANDA published timely and highly sophisticated content, including dozens of original political cartoons, graphics, memes, and videos, judging from a review of identified accounts. These posts often responded to trending news topics within days and leveraged popular, and sometimes divisive, figures to press their narratives. SPICYPANDA responded more dynamically to emerging events than other pro-PRC inauthentic networks, judging from open-source reporting and a DHS review of the accounts."
The DHS says it compiled the intelligence note to help intelligence analysts gain "greater insight into the command and control structures of PRC social media messaging operations" and the state's involvement.
Breaches, hacks, and security incidents
Curve Finance hacker returns funds: A hacker who stole more than $73.5 million from multiple cryptocurrency platforms is now returning the stolen funds. Roughly $52.3 million have been sent back to the hacked platforms over the past few days. The funds were stolen at the end of July after the hacker exploited a vulnerability in a protocol developed by Curve Finance and used by multiple platforms. Curve Finance offered the hacker a chance to return the funds and keep 10% as a "bug bounty reward." The attacker initially ignored this offer but began returning funds after Curve Finance offered a $1.85 million bounty on any information that could unmask the hacker's identity.
UK Electoral Commission breach: An unidentified threat actor stole the electoral registries of the UK Electoral Commission. Officials say the attacker stole the "name and address of anyone in the UK who registered to vote between 2014 and 2022, as well as the names of those registered as overseas voters." The breach took place in August 2021 and lasted until October 2022, when the intruder was discovered by the commission's staff. UK officials say that besides stealing voter records, the attacker also gained access to its email systems.
Russian "hacktivism": After attacks on Spanish and Italian government and private sector organizations, the pro-Kremlin "hacktivist" group NoName057(16) is now targeting the Netherlands. The Dutch NCSC says that while the DDoS attacks are taking down websites, the impact is "often limited and symbolic" and nothing to worry about in the long-run.
General tech and privacy
Intel GPU telemetry collection: The latest version of the Intel Arc GPU driver contains a hidden user telemetry collection feature. As TechPowerUp reports, the new feature is not included in the driver's changelog and can collect information such as visited websites, PC usage patterns, system properties, and information about other peripherals. The hidden telemetry collection was forced on all users who received an update, hidden under a "custom installation" section where no user ever checks during an update.
Firefox update: Mozilla has updated Firefox to fix an issue causing keystrokes to be scrambled for users using ZoneAlarm anti-keylogger. Good ol' antivirus products messing with your apps.
Chrome 116: Google has released version 116 of its Chrome browser. The major change in this release is a shift in how Google delivers security updates and bug fixes. Going forward, Google says it will release Chrome updates every week in an attempt to narrow the patch gap that exists between Chrome and the underlying Chromium open-source browser.
"This should not change how you use or update Chrome, nor is the frequency of milestone releases changing, but it does mean security fixes will get to you faster."
New Android 14 cellular security feature: The upcoming version of the Android mobile operating system will include two new major security features. The first will allow IT administrators to disable 2G support and prevent Android 14 smartphones from connecting to older telco networks. The second feature will allow mobile fleet operators to prevent devices from connecting to unencrypted cellular networks, also known as null-ciphered networks. The new Android 14 is scheduled to be released later this month.
Discord and security keys: Discord says it has now rolled out YubiKeys to all employees in a bid to improve the company's security.
Government, politics, and policy
Russia cracks down on "gray" SIM cards: Russian telecommunications watchdog Roskomnadzor has ordered local mobile operators to block access to their networks to SIM card numbers that don't have data on their owners, also known as "gray numbers." Since the start of the month, operators have been notifying users with incomplete data. Customers will have 15 days to provide their personal information on the provider's website, at one of the operator's branches, or on the Gosuslugi e-government portal. SIM card owners will have to provide an ID or passport to verify their identity. The SIM card verification requirement has been in place since 2018 but has not been enforced until now. [Additional coverage in Vedomosti]
MIA warning on Ukrainian scammers: Russia's Ministry of Internal Affairs says that Ukrainian scammers and hackers are stealing money from Russian citizens and promising to return the funds if they set fire to military, transport, or banking infrastructure. The Ministry says that while the tactic has been used before, it started receiving a larger number of reports last week. The vast majority of victims extorted in this campaign are elderly.
Iraq blocks Telegram over data leaks: The Iraqi government has blocked access to the Telegram service citing a threat to national security. The Ministry of Communications took the decision after Telegram failed to take down channels that leaked government data. Iraq joins countries such as Brazil, Iran, and Russia, which blocked access to the site after the company did not cooperate in investigations.
Senators want more info on DPRK crypto-thefts: A group of US senators has asked the White House and the US Treasury to share more details on North Korea's use of crypto-hacks to amass cryptocurrency and evade US sanctions.
DHS cybersecurity fund: The Department of Homeland Security is providing $374.9 million in grant funding to state and local authorities to boost their cybersecurity postures. The funding is being made available through the State and Local Cybersecurity Grant Program (SLCGP). The sum is more than double what the DHS allocated to state and local cybersecurity funding last year.
K-12 cybersecurity: The Biden administration has announced a series of measures meant to improve the cybersecurity posture of K-12 schools. Multiple government agencies, such as CISA, the FBI, the FCC, and the Department of Education, will establish and run programs to train school staff on cybersecurity and provide funding for cybersecurity investments. Private sector companies like AWS, Cloudflare, Google, D2L, and PowerSchool are also contributing funding or IT resources to the endeavor.
US PRC IoT inquiry: The US House Select Committee on the Chinese Communist Party wants the FCC to become more aggressive in cracking down on the use of Chinese-developed software modules included in modern IoT devices. US officials fear the CCP might use these modules as backdoors into smart devices deployed across the US. The Committee would like the FCC to focus regulatory efforts to address this threat through a certification program or anything else the FCC sees fit. [Additional coverage in Newsweek]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Tines co-founder and CEO Eoin Hinchy about how organizations can maximize the potential of their security teams during an economic downturn, with a concentration on why human error and burnout caused by excessive workloads on security teams can be a risk.
Cybercrime and threat intel
16Shop takedown: Interpol officials have shut down 16Shop, a Phishing-as-a-Service platform that has been active since 2019 [1, 2, 3]. Three suspects were detained, including a 21-year-old Indonesian believed to be the platform's main administrator. The 16Shop platform offered ready-made phishing pages for various online services, such as Apple, PayPal, Microsoft, Amazon, and others. Access to phishing kits varied from $60 to $150, depending on the targeted brand. According to Group-IB, 16Shop has been linked to more than 150,000 phishing domains.
Yashma ransomware: A suspected Vietnamese threat actor has been using a version of the Yashma ransomware strain to conduct attacks since at least June this year.
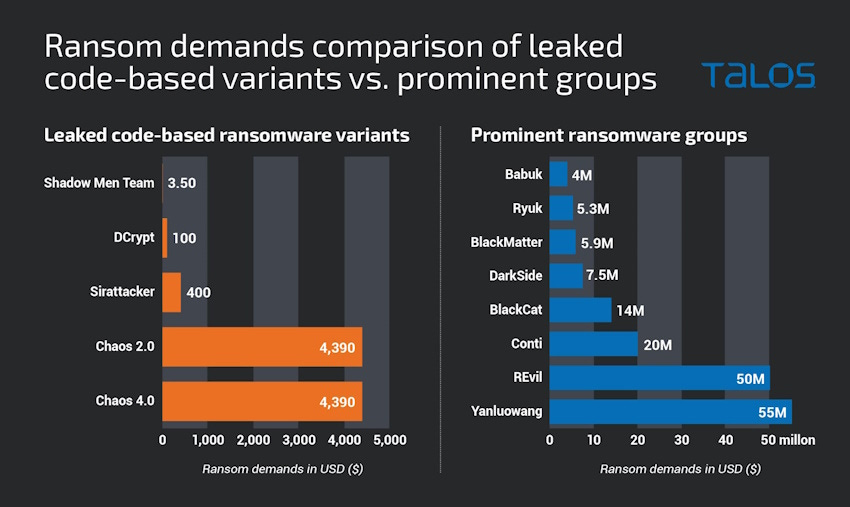
Leaked ransomware code: A Cisco Talos investigation has found that threat actors who use leaked ransomware code are asking for lower ransoms from their victims compared to gangs that write their own code. The difference is enormous, with gangs that use leaked source code asking for around $4,000 while gangs that write their own code asking in the real of millions. Ransomware gangs that had their code leaked and repurposed by lower-tier gangs include Babuk, Conti, Chaos, and LockBit.
Malware technical reports
QakBot: Team Cymru says that after exposing some of QakBot's infrastructure back in May, the group appears to have migrated to new servers as a result, causing a lull in activity from the group.
OpenBullet: Kasada looks at a campaign spreading a RAT-laced version of OpenBullet, a tool used by threat actors to conduct credential-stuffing attacks. Looks like a campaign designed to steal data from other threat actors. Why do the actual work when you can steal other people's work instead?
TargetCompany ransomware: Trend Micro has a report on TargetCompany, a ransomware strain used in targeted enterprise attacks.
Sponsor Demo
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs and cyber-espionage
Russian disinformation in Africa: A Reset investigation looks at a large-scale Russian disinformation effort carried out on Facebook and targeting audiences in Francophone Africa. The campaign centers around Russian state media channels and focuses on portraying Russia as "Africa's true friend and ally, ready to help African countries stand up to French hegemony." The networks published content in French and were artificially inflated using viral content, only to make a sudden shift to Russian propaganda a few months later.
"All pages in the network underwent a drastic shift in their content strategy and a major overhaul in their visual identity (changing their names, logos, cover photos) before beginning to publish pro-Russian content. For most of the pages this happened in March or April 2023."
Ukraine thwarts Sandworm ops targeting military systems: Ukraine's Security Service, the SBU, has blocked attempts by Russian hackers to breach the country's military and data exchange networks. The SBU says it identified ten malware samples designed to extract information from its systems. The malware ranged from Android remote access trojans to backdoors designed to collect data from Ukraine's Starlink satellite connections. The SBU has attributed the campaign to Sandworm, a cyber-espionage unit in Russia's GRU military intelligence service.
ScarCruft: North Korean cyber-espionage group ScarCruft has breached the network of sanctioned Russian missile maker NPO Mashinostroyeniya. Security firm SentinelOne says the group breached the company's email servers and internal IT network, where they planted a backdoor named OpenCarrot. The backdoor is typically used by the Lazarus Group, another DPRK APT, suggesting the two groups are likely collaborating in some sort of fashion.
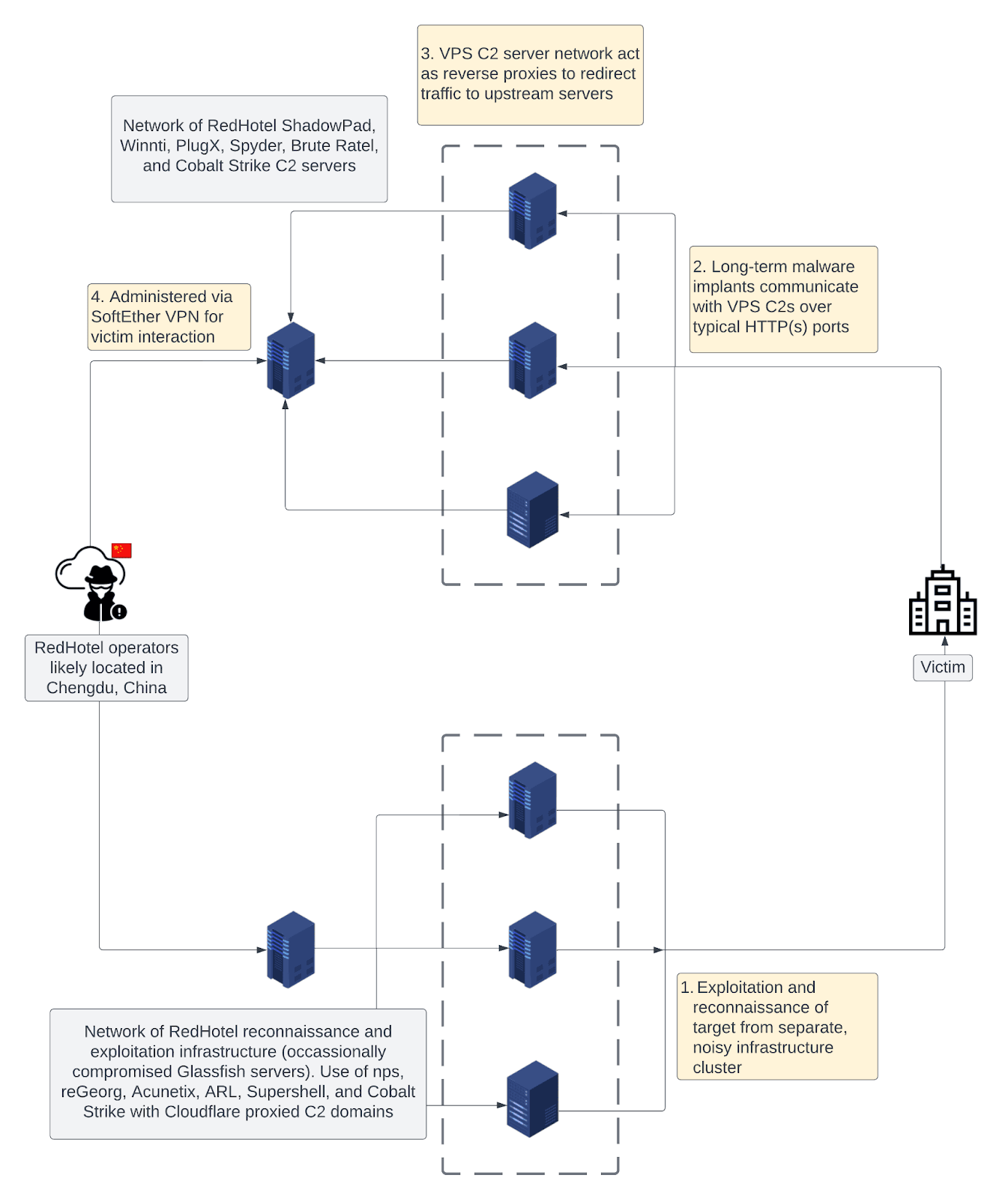
RedHotel: Cybersecurity firm RecordedFuture says that an APT group it tracks as RedHotel is being run from the city of Chengdu, China. RecordedFuture says the group's modus operandi aligns with "other contractor groups linked to China's Ministry of State Security (MSS), indicating a nexus of cyber talent and operations in Chengdu." Also known as Earth Lusca, the group has been active since 2019, and its cyber-espionage operations have focused on both intelligence gathering and economic espionage. Unlike other Chinese APT groups, RedHotel has a distinct focus on reconnaissance and long-term network access. RedHotel's most high-profile intrusion was a breach of a US state legislative body in July 2022.
"RedHotel activity overlaps with publicly reported activity under the aliases Aquatic Panda (CrowdStrike), BRONZE UNIVERSITY (SecureWorks), Charcoal Typhoon (Microsoft), Earth Lusca (Trend Micro), and Red Scylla (PWC), and, as noted above, was previously tracked by Recorded Future under the temporary group designator TAG22."
Vulnerabilities, security research, and bug bounty
Mozilla VPN vulnerability: The OpenSUSE security team has disclosed a vulnerability in the Mozilla VPN client on Linux. The vulnerability resides in the VPN client's high-privileged daemon that can be exploited by any user on multi-user systems to secretly set up their own VPN connection or change existing VPN settings. After a 90-day disclosure window, Mozilla has not patched the reported issues.
Office 2017 vulnerabilities: Kaspersky says that a 2017 Office vulnerability tracked as CVE-2017-11882 is still being abused in the wild, more than five years later.
Patch Tuesday: Yesterday was the August 2023 Patch Tuesday. We had security updates released by Adobe, Microsoft, AMD, Intel, Citrix, Fortinet, SAP, Siemens, Zoom, and Zyxel. The Android project, Chrome, Mozilla Firefox, Drupal, GitLab, VMWare, Schneider Electric [PDF], and Cisco, released security updates last week as well.
Microsoft security updates: This month, Microsoft patched 87 vulnerabilities, including an actively exploited zero-day tracked as CVE-2023-38180, impacting .NET and Microsoft Visual Studio apps. The company also released security updates for CVE-2023-36884, a zero-day in the Windows Search feature the company disclosed last month but did not release software updates at the time.
Inception attack: ETH Zurich academics have discovered a new side-channel attack that can leak data from AMD Zen CPUs. Named Inception (CVE-2023-20596), the attack can bypass all previous software and hardware-based mitigations that AMD has put in place to protect its CPUs from transient execution attacks. The attack is named Inception after Christopher Nolan's eponymous movie, as it plants malicious predictions in an AMD security feature named "Training in Transient Execution (TTE)" that can be exploited at a later date using what researchers call a Phantom speculation (CVE-2022-23825).
"As in the movie of the same name, Inception plants an "idea" in the CPU while it is in a sense "dreaming", to make it take wrong actions based on supposedly self conceived experiences. Using this approach, Inception hijacks the transient control-flow of return instructions on all AMD Zen CPUs."
Downfall attack: Sticking with CPU vulnerabilities, security researcher Daniel Moghimi has published details on Downfall (CVE-2022-40982), another side-channel attack—this one impacting Intel CPUs. Moghimi says the attack can allow a malicious threat actor to steal data from users who share the same computer. The researcher says the root cause of this new vulnerability are memory optimization features in Intel processors that unintentionally reveal internal hardware registers to unprivileged software, allowing local untrusted apps to access sensitive data.
"For instance, a malicious app obtained from an app store could use the Downfall attack to steal sensitive information like passwords, encryption keys, and private data such as banking details, personal emails, and messages. Similarly, in cloud computing environments, a malicious customer could exploit the Downfall vulnerability to steal data and credentials from other customers who share the same cloud computer."
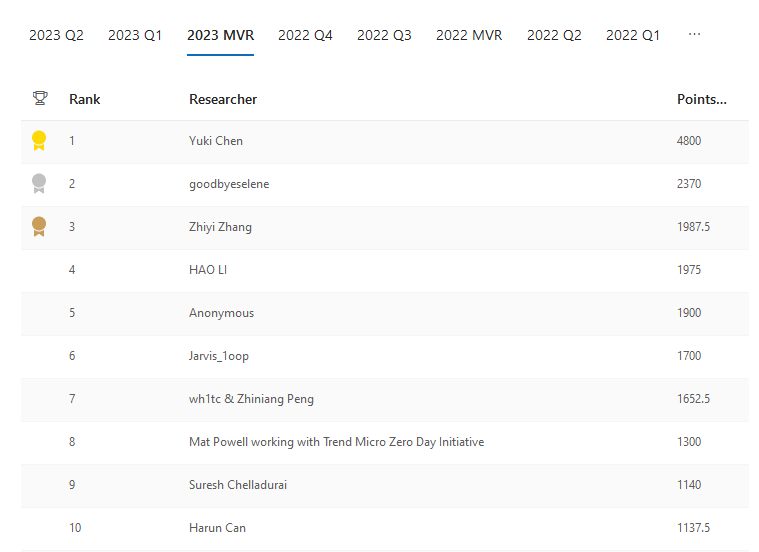
MSRC VRP: Microsoft has published the ranking for the top bug bounty hunters who contributed reports via the company's VRP over the past calendar year (July 2022 to June 2023). Congratulations to Yuki Chen, a member of Qihoo 360's Vulcan Team, who tops the ranking for the second year in a row after being named Microsoft's top bug bounty hunter in 2022 as well.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq ask whether Chinese operations are becoming stealthier and why. Is it a top-down directive to be careful, or do the operations themselves require more stealth?




