Risky Biz News: Cyber insurance catches on across the EU
In other news: Chinese APT hacked Dutch chipmaker NXP; EU holds election cybersecurity exercise; and three cryptocurrency exchanges lose a total of $161 million.
This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
An ENISA report on NIS compliance spending has found that roughly 42% of the EU's critical infrastructure and digital service provider operators have signed up for cyber insurance in 2022.
The report notes that while cyber insurance coverage was at 43% in 2020 and just 30% in 2021, the cyber insurance market now appears to be active and developed all over the EU.
Last year, organizations in all member states signed up for cyber insurance compared to previous years, where most of the coverage was clustered in just a handful of member states.
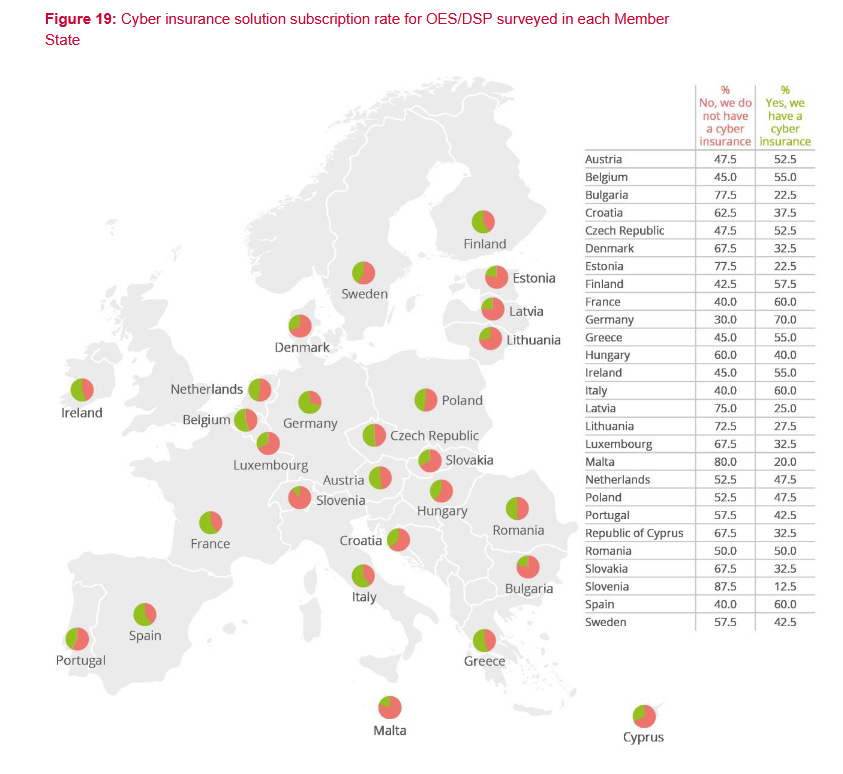
The report is based on data from 1,080 OES or DSP organizations across all 27 member states. OES stands for Operators of Essential Services and is the EU's term for critical infrastructure operators, like healthcare, water, energy, transport, and the sort. DSP stands for Digital Service Providers and includes all the large service providers that have more than 50 staff and an annual balance sheet of over €10 million.
Put together by ENISA—the EU's cybersecurity agency—the report looks at how major companies and critical infrastructure operators are investing in complying with the EU's NIS directive. The directive mandates that larger organizations reasonably secure their networks against cyberattacks and report larger cybersecurity incidents to national regulators.
Ever since it passed in 2016, NIS compliance has revolved around companies setting up robust cybersecurity defenses and having the proper tools and systems for dealing with and reporting incidents efficiently.
Even if companies started from scratch or had in-house security teams, NIS compliance has typically come with its own budgeting load.
Since budgets are easier to quantify than other NIS compliance work, ENISA has been surveying the market every year to see how EU organizations have approached the problem.
In 2022, ENISA says that organizations allocated €83.6 million to IT spending on average, of which €5.1 million went to information security spending.
Cybersecurity spending increased by 0.4% from the previous year, suggesting companies have found their sweet spot.
The same trend was also seen in employment figures, with organizations allocating 11.9% of their IT staff to cybersecurity operations, a number down 0.1% from the 12% recorded in 2021.
Around 47% of companies also said they don't have any plans to hire new cybersecurity staff in the next two years, again confirming the market has found its sweet spot in terms of budgeting and staffing.
However, with NIS2 set to replace the old NIS throughout the next two years, cybersecurity is now again a top spending target for EU organizations, and by a very large margin.
Breaches, hacks, and security incidents
Credit union hacks: A hacking group named N4ughtySecTU has hacked and is extorting TransUnion and Experian, two of South Africa's largest consumer credit reporting agencies. The group is asking for $30 million from each, threatening to release its customers' data online. This is the second time the N4ughtysecTU group hacked TransUnion after it deployed ransomware on its network in March 2022. The group is believed to operate out of Brazil. [Additional coverage in TimesLIVE]
CTS cyber-attack: A cyberattack on a shared IT service provider is impacting the activities of more than 80 UK law firms involved with the real estate market. The attack has hit CTS, a Chesire-based company that provides cloud hosting and IT solutions for law firms in the UK and Ireland. The Telegraph reports the company fell victim to the recent wave of CitrixBleed attacks carried out by the LockBit ransomware group. Ever since the attack last Wednesday, some UK law firms have been unable to complete real estate conveyance transactions. [Additional coverage in The Telegraph/non-paywall]
HSE cyber-attack: A cyberattack has hit the IT network of HSE, Slovenia's largest power utility. The company says the incident was the result of a "crypto-virus" that encrypted files and locked staff out of its systems. HSE says it has not received any ransom request and that the incident did not impact activity at any of its power plants. [Additional coverage in STA and 24ur] [h/t Amadej Papež]
Gulf Air data breach: Bahrain-based airline Gulf Air says it suffered a security breach during which an unidentified threat actor might have gained access to customer data. Gulf Air says critical systems and flight operations were not affected by the incident. [Additional coverage in BNA]
New Relic incident: Web tracking and analytics company New Relic is investigating a security breach of its infrastructure. The company did not share any details on the exact nature of the incident. New Relic says it will directly contact each affected customer if their data was impacted by the breach. [h/t Scrantic]
Justin Sun crypto-heists: Two cryptocurrency exchanges linked to blockchain entrepreneur Justin Sun suffered security incidents last week, resulting in an estimated loss of $115 million worth of assets. Hackers stole $85 million from Heco Chain and another $30 million from HTX. This marks the second time HTX got hacked in two months after the platform also lost $8 million in a hack at the end of September. Sun promised to compensate all affected users. [Additional coverage in CNBC]
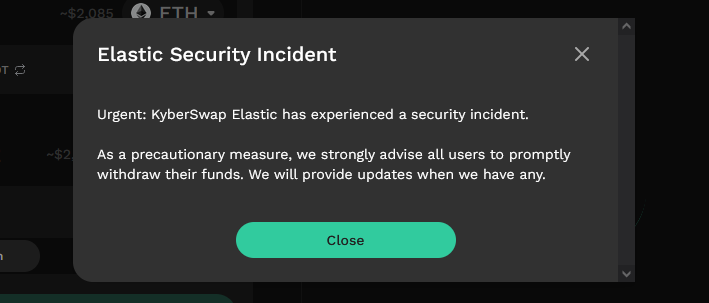
KyberSwap crypto-heist: A hacker has breached the network of cryptocurrency trading platform KyberSwap and stole $46 million worth of assets. The company confirmed the hack and urged users to withdraw funds from their platform. KyberSwap has offered the hacker the possibility of keeping 10% of the stolen funds as a "bug bounty reward," but five days later, the funds have yet to be returned. This is the company's second hack after it lost $265,000 in September 2022. [Additional coverage in CoinTelegraph]
Government, politics, and policy
EU election cybersecurity exercise: EU agencies held a cybersecurity exercise to test the resilience of election systems. The exercise was meant to prepare EU agencies and officials ahead of EU MP elections that are scheduled to take place in June next year. Participating organizations included the European Parliament's services, ENISA, CERT-EU, and national electoral and cybersecurity authorities.
EU CSA bogged down: Progress on the EU Cyber Solidarity Act has slowed down, and the EU's new cyber legislative effort seems to have gotten bogged down in various commissions. More on the EU CSA is here. [Additional coverage in Euractiv]
IRS getting better at logging: The US IRS is now doing a better job at logging its network, the agency's director of cybersecurity operations, Rick Therrien, said in a webinar earlier this month. [Additional coverage in FederalNewsNetwork]
Russia adds Meta spokesperson to most-wanted list: The Russian government has added Meta spokesperson Andy Stone to the country's most-wanted list. Officials have not revealed why, but an order for his arrest was issued way back in February 2023. The Russian government labeled Meta as a terrorist organization shortly after its invasion of Ukraine after the company refused to censor its content according to the whims of Russian officials. [Additional coverage in the Associated Press]
Sponsor section
In this Risky Business News sponsor interview Tom Uren talks to Brian Dye, CEO of Corelight about the value of data from NDR tools when it comes to longer term incident response.
Cybercrime and threat intel
Nigerian politician connected to Patricia hack: Nigerian police detained a local politician in connection to the May 2023 hack of local cryptocurrency exchange Patricia. Investigators say $750,000 of the stolen funds were sent to the bank account of Wilfred Bonse, a member of Nigeria's Peoples Democratic Party. Patricia says the funds represent a small part of the funds it lost in May. The company has yet to disclose the size of the hack. [Additional coverage in TechPoint Africa]
Apple spyware notifications: Apple has sent a team of security experts to India to help the local authorities investigate recent cases of spyware being found on the iPhones of opposition members. At least eight opposition figures spoke out about security alerts they received from Apple at the end of October. Among them was Rahul Gandhi, leader of the National Congress Party and Modi's main rival for the upcoming elections.
New npm malware: Fifty-eight malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Telekopye: ESET has published its second part on Telekopye, a Telegram bot for building phishing pages for various Russian online marketplaces. This part focuses on Neanderthals, the Telekopye admin. See part one for an overview of the service itself here.
PrivateLoader servers: Embee researchers have identified 12 command and control servers for the PrivateLoader malware operation.
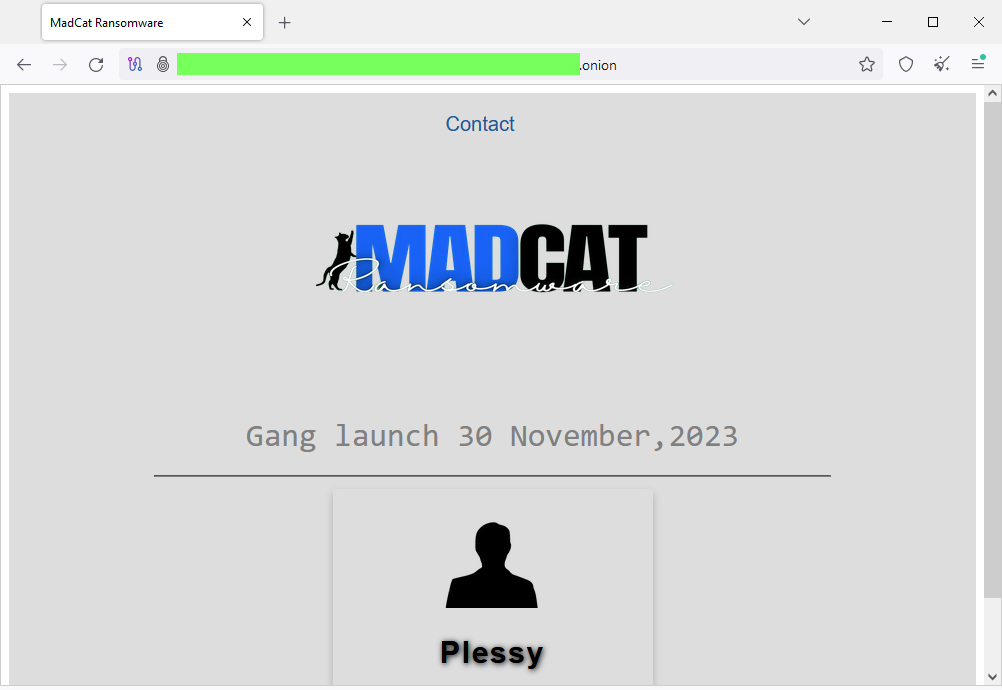
MadCat ransomware: A threat actor known as Plessy and WhiteVendor has been linked to a new ransomware strain named MadCat—per the CERT team for Poland's financial sector [PDF].
MEOW: Sticking with the cat-themed extortion groups, we also have MEOW Leaks, a group that's been operating since September this year. It's unclear if they engage in ransomware attacks or classic data extortion. Their latest victim is the Vanderbilt University Medical Center.

Malware technical reports
Parallax RAT: eSentire looks at Parallax RAT, a remote access trojan launched in 2019 and still used in attacks today, primarily via SERP-poisoned pages.
Tellyouthepass ransomware: Chinese security firm Sangfor has published an analysis on the Tellyouthepass ransomware after several Chinese companies got hit over the past weeks.
Sponsor Section
This week's Risky Business newsletters are brought to you by Corelight. They maintain the open source Zeek network security sensor/monitor. They also make very good commercial products in the network security space. Check them out at Corelight.com, or watch this video about why you need NDR as well as EDR.
APTs, cyber-espionage, and info-ops
Chimera's NXP hack: Chinese state-sponsored hackers have breached the network of Dutch chipmaker NXP in an attempt to steal chip designs. The intrusion lasted from October 2017 to the start of 2020 and was carried out by a group known as Chimera. NXP told Dutch newspaper NRC the group managed to steal some intellectual property but did not elaborate. NRC says the group also breached Dutch airline Transavia and seven Taiwanese chipmakers in subsequent operations. [Additional coverage in NRC/non-paywalled]
XDSpy: Russian security firm FACCT says the XDSpy APT group has targeted Russian companies in the metallurgy and military-industrial sectors. XDSpy is an APT discovered in 2020 that has historically targeted Russian organizations only. A past campaign targeted Russian private companies and a well-known research institute.
APT37: South Korean security researcher Sakai has published an analysis of a recent APT37 (Reaper) spear-phishing campaign targeting South Korean organizations.
DoNoT Team: Qihoo 360 looks at a recent campaign carried out by the DoNoT APT group, also known as APT-C-35. The final payload was a mundane, run-of-the-mill Remcos RAT.
Hamas APT op: Check Point analyzes recent versions of the SysJocker multi-platform backdoor, which the company has spotted in some Hamas APT operations linked to the Gaza Cybergang.
"Among the most prominent changes is the shift to Rust language, which indicates the malware code was entirely rewritten while still maintaining similar functionalities. In addition, the threat actor moved to using OneDrive instead of Google Drive to store dynamic C2 (command and control server) URLs."
Syrian Army targeted: Chinese security firm QiAnXin has published a report on a spear-phishing campaign targeting Syrian Army soldiers. The final payload is the SpyMax Android RAT.
Vulnerabilities, security research, and bug bounty
Synology security updates: NAS vendor Synology has patched the bugs used during the Pwn2Own Toronto 2023 hacking contest that took place last month.
ownCloud security updates: File sharing and synchronization solution ownCloud has released three security updates for its on-premise solution. All vulnerabilities are rated critical with severity scores of 9, 9.8, and 10. The most dangerous of these bugs is a vulnerability that can be used to leak ownCloud admin passwords and mail server credentials via the OwnCloud Graph API.
strongSwan RCE: A remote code execution vulnerability (CVE-2023-41913) has been patched in the strongSwan VPN solution.
Windows micro-patch: Acros Security has released a micro-patch for a new NTLM relay technique disclosed by Check Point earlier this month.
C2PA forgeries: Dr. Neal Krawetz looks at various ways of creating authenticated forgeries for multimedia files secured with C2PA, a multimedia signing and authentication standard developed by Adobe, Arm, Intel, Microsoft, and Truepic.
Infosec industry
New tool—AD Canaries: The Airbus security team has open-sourced AD Canaries, a canary solution for Windows AD environments.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how being more open about cybersecurity threats is great for marketing and has also forced cybersecurity companies to pick sides and make value judgements.




