Risky Biz News: CSRB to investigate Microsoft's Chinese hack, and the broader cloud security ecosystem
In other news: UK Foreign Office hacked twice in 2021; Japan to build Indo-Pacific cyberdefense network; and Zyxel routers under attack.
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The DHS Cyber Safety Review Board (CSRB) has picked up the unenviable task of investigating the security practices of US cloud service providers and plans to use the recent breach of Microsoft email systems as the figurehead of an upcoming report.
The CSRB may have couched its press release as a generic investigation of cloud security providers, but it is, without a doubt, an investigation into Microsoft's carelessness when it comes to its cloud infrastructure, which underpins a vast section of the US government's IT systems.
The CSRB investigation was announced two weeks after Sen. Ron Wyden asked the DHS—together with the FTC and DOJ—to investigate Microsoft's "lax cybersecurity practices" that led to the breach in the first place.
Of the three agencies that Wyden asked, the CSRB is the one with fewer teeth and the one whose investigation might give Microsoft a slap on the cheek but then allow the US government to kiss the boo-boo later without having to impose any heavy fines.
Established by the White House in 2021, the CSRB is tasked with reviewing major cybersecurity incidents impacting the US. It has no subpoena powers, and its investigations are completely at the mercy of the cooperation they get from other government agencies and private sector companies—which was painfully obvious in its recent Lapsus$ report. A bill is currently in the works to grant the CSRB subpoena powers, but the bill has not passed yet.
So far, the CSRB has investigated just two incidents and issued two reports—on the Log4Shell vulnerability and the operations of the Lapsus$ APT, where APT stands for advanced persistent teens.
This is the first time the CSRB will be investigating an entity that can fight back in meetings and has more lobbyists than the board has members.
About the only thing the board has going is that Microsoft knows it has egg on its face. Its Exchange servers were widely hacked across the world with the ProxyShell vulnerability in 2021, the company got not one but two public tongue-lashings from the Tenable CEO for basically ignoring major Azure vulnerabilities, and then the Storm-0558 hacks happened in July.
These latter intrusions were particularly bad for Microsoft. Not only did Chinese hackers access the email systems of at least four US government agencies, but the technical details of how they did it squarely point the finger at Microsoft's negligence. My colleague Tom Uren went over all of these technical slip-ups in his newsletter two weeks ago, right after Sen. Wyden asked for a CSRB review.
He pointed out back then that a "CSRB review might not result in many new specific technical recommendations" since Microsoft was clearly breaking many basic rules when it came to the storage of privileged access skeleton keys and the separation of internal services and systems.
As Tom, Tenable CEO Amit Yoran, and many other infosec and gov-tech experts have pointed out is that "Microsoft isn't prioritising security as much as it should."
By couching its report as a general review of cybersecurity practices of cloud service providers, we hope the board will establish an unofficial set of rules and requirements that cloud providers will have to adhere to, if they hope to serve secure government systems going forward.
The CSRB's latest report on the Lapsus$ operations clearly showed that US telcos run on extremely insecure infrastructure and that tech companies, even if they use them, they often fail to properly configure their Identity Access Management (IAM) and Multi-Factor Authentication (MFA) solutions.
Believe it or not, the CSRB Lapsus$ report, which is a bore for incident responders—because they know all of Lapsus$'s shenanigans by now— is a gold mine for defenders and CISOs, who now have a set of recommendations and examples on how to use or not-use your IAM/MFA. There is something to learn from reading all of it.
But if you're using some of today's biggest cybersecurity experts and policymakers to issue recommendations and best practices, then what's the point of NIST and standards bodies?
There's a reason why the DHS is looking for subpoena powers for the CSRB. How Microsoft responds to this investigation will most likely determine if the CSRB project implodes or if Congress sees the issue and grants it the legal power it needs to become the cyber NTSB the DHS wants to make into so much.
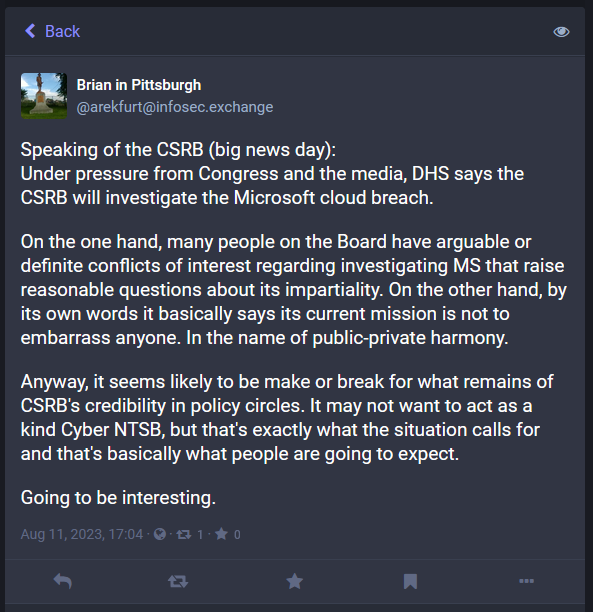
I'll just end this newsletter with a Mastodon post from an infosec commentator whose opinion I always treasure and find extremely to the point.
"Anyway, it seems likely to be make or break for what remains of CSRB's credibility in policy circles. It may not want to act as a kind Cyber NTSB, but that's exactly what the situation calls for and that's basically what people are going to expect."
Breaches, hacks, and security incidents
FCDO hacks: Russian and Chinese hackers have breached the UK Foreign Office in two separate 2021 breaches that were kept secret by British officials. GCHQ sources say the breaches occurred following spear-phishing attacks. Both incidents took place at the same time but impacted different systems. The attackers are believed to have read correspondence from ambassadors and diplomats positioned abroad but did not gain access to classified information. [Additional coverage in iNews]
Rapattoni incident: A mysterious cyberattack has brought down the systems of Rapattoni, a provider of MLS software for real estate companies across the US, including real estate giant Zillow. The outage has left agents unable to edit or add new real estate listings on their sites and mobile apps. Rapattoni says it's still investigating the nature and scope of the cyberattack and has not provided any other details. Thousands of companies and tens of thousands of agents are believed to have been impacted.
General tech and privacy
Atlassian to shut down RU and BY accounts: Australian software company Atlassian plans to disable the accounts of Russian and Belarusian users at the start of September 2023. This includes accounts for services such as Trello, Jira, and Confluence. Russian and Belarusian companies will have 30 days to prepare for the shutdowns once they receive Atlassian's email. Atlassian stopped accepting new accounts from Russia and Belarus shortly after Russia's invasion of Ukraine. Microsoft also notified Russian companies last week that it will no longer be possible to extend their Microsoft 365 licenses after September 30 this year. [Additional coverage in Kommersant]
Xiaomi blocks Telegram on its Chinese phones: Chinese smartphone maker Xiaomi is blocking its Chinese users from installing the Telegram app on their devices. The company is doing this through a so-called "anti-fraud" feature of its MIUI 13 firmware. The company used the same feature last year to block apps that allowed Chinese users to bypass local app stores and install any app directly on their phones. [Additional coverage in Kod]
Quake 2 code: id Software has open-sourced the code for its emblematic Quake 2 FPS game. The company says it released the code "for users who wish to mod the game." The company also quadrupled the server tickrate from 10Hz (100ms) to 40Hz (25ms) for multiplayer gameplay.
Extensions coming to Firefox Android: Mozilla will bring support for browser add-ons to its Android browser later this year.
Chrome post-quantum encryption support: Google says that its latest Chrome 116 release now supports a new cryptographic algorithm that can protect TLS traffic from quantum computer attacks. Known as X25519Kyber768, the algorithm adds a hybrid post-quantum key exchange for TLS 1.3 connections.
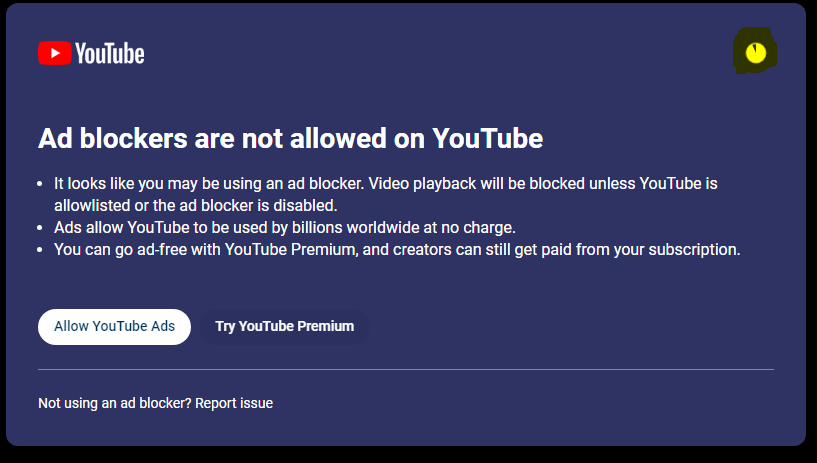
YouTube's ad-blocker block: Google is expanding its annoying anti-ad-blocker popups in a bid to protect its advertising business. The popups are now shown to more users and now come with a 60-second timer during which users HAVE to disable their ad blocker to access YouTube's site.
Government, politics, and policy
Beijing hates hunt-forward missions: China's Foreign Ministry is crying about the US sending hunt-forward missions abroad and Washington's recent "propaganda" that Chinese hackers breached Japanese government networks for years. I swear, reading Chinese government press releases is like watching a toddler's attempts at diplomatic relations.
Beijing's new app dev registration law: China's Ministry of Industry and Information Technology (MIIT) will require all app developers to provide their business details to the government. Companies that want to release new apps through local Chinese app stores must register with the government by September. Existing apps and developers have until March next year to provide their details or have their apps taken down and face punitive measures. The move comes to strengthen the government's control over what apps its citizens can install on their mobile devices in a bid to avoid the spread of unfiltered information such as foreign news, VPNs, games, and others. [Additional coverage in AndroidPolice]
Indo-Pacific cyberdefense network: The Japanese government plans to build an information-sharing network that will span the Indo-Pacific region. The network's main role will be to provide cybersecurity advice and support for countries that lack the technical know-how and resources to defend against cyberattacks, such as the many Pacific island nations. Officials hope the network will serve as a bridge between Japan and the information-sharing networks of Australia and the US. The network will specifically focus on detecting cyberattacks from Russia, China, and North Korea, the most active military and cyber threats in the region. [Additional coverage in Nikkei/non-paywall]
NZSIS report: New Zealand's intelligence service has published its assessment of the country's threat environment. The report highlights China as the main threat to New Zealand's stability, with the Chinese government involved in societal and political influence operations, but also classic and cyber-enabled espionage activities.
Sponsor section
In this Risky Business News sponsor interview Tom Uren talks to Jacob Torrey, Thinkst's Head of Labs. Jacob produces ThinkstScapes, a brilliant quarterly summary of the most interesting security research from around the world. Jacob talks about his favourite research in this edition, why Thinkst invests the time and effort in producing ThinkstScapes and also talks about Thinkst Citation, a companion product that contains information about nearly 70,000 security talks going all the way back to 1993.
Cybercrime and threat intel
Lolek admin charged: US authorities have unsealed charges against a 36-year-old Polish national named Artur Karol Grabowski for running a bulletproof hosting company named Lolek. Officials say Lolek hosted servers for cybercrime groups involved in DDoS attacks, email spam, infostealers, scam sites, and the NetWalker ransomware. The service was seized last week by US and Polish authorities. Five of the site's admins were detained in Poland, but US officials say Grabowski is still at large.

Crypto-recovery schemes: The FBI is seeing an increase in scams involving crypto-recovery companies that target victims of cryptocurrency hacks with false promises of recovering stolen assets. These companies often charge an up-front fee for their services but usually cease all communications with the victim or produce bogus investigation reports. The agency is urging users not to engage with such companies because private sector companies don't have the legal power to either seize or recover funds, a power that's reserved for law enforcement agencies only. Furthermore, the FBI says it is not affiliated or partnered with any such company, and any such claims should help users identify scams.
FBI interview on DDoS disruptions: TechCrunch's Lorenzo Franceschi-Bicchierai has an interview with FBI agent Elliott Peterson about the bureau's recent disruptions of DDoS-for-hire services.
New npm malware: Forty malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Malware technical reports
Shell collection: Indonesian haxor Beruangsalju has put together a collection of the most widely known web shell scripts. Friendly warning to beware of backdoored scripts.
MSI Loader: Cyfirma has found a malware strain named MSI Loader that appears to have connections to the BatLoader malware.
INC Ransom: Huntress researchers have published some basic IOCs for intrusions carried out with the new INC ransomware.
Sponsor Section
This is a section where we typically feature one of our sponsor's products. This time, we're gonna feature a tip on how to use Thinkst's canaries to spot "canary text files" being opened from the terminal, a typical giveaway of threat actor activity.
APTs and cyber-espionage
UAC-0170: Ukraine's CERT team says a threat actor tracked as UAC-0170 is posing as the Ukraine State Cyber Protection Centre to trick organizations into handing over their RoundCube email server passwords in a classic "change our password" phishing campaign.
APT29 spear-phishing: EclecticIQ has discovered a spear-phishing campaign targeting the Ministries of Foreign Affairs of NATO-aligned countries. EclecticIQ has linked the campaign to APT29, an advanced persistent threat actor attributed to Russia's Foreign Intelligence Service (SVR). The company says the threat actor used Zulip—an open-source chat application—for C&C communications to evade and hide its activities behind legitimate web traffic.
Vulnerabilities, security research, and bug bounty
Ford says cars are safe from WiFi bug: American carmaker Ford says that a vulnerability discovered in the infotainment system used on Ford and Lincoln vehicles does not impact the safety of its cars and drivers. The vulnerability resides in the WiFi driver of its SYNC 3 infotainment system and allows a threat actor to execute remote code using malicious WiFi packets. Ford says the issue requires significant expertise to exploit and that successful attacks would only compromise the infotainment system and not impact the car's driving features. The company has told customers to disable the WiFi feature if they fear their cars could be hacked until it prepares and releases a firmware update.
MBTA hack: Two Boston high-school students replicated the research of two MIT students who found a way to hack Boston subway MBTA cards. The MIT students wanted to present their findings at DEFCON 2008 but got sued by the city of Boston and had to back out. This time around, the high-school students got to present their research without any issues. [Additional coverage in Wired]
Apple BTM vulnerabilities: Apple security researcher Patrick Wardle has found a suite of vulnerabilities in Background Task Management (BTM), a macOS utility designed to detect malware persistence techniques. Wardle says macOS malware can leverage these vulnerabilities to bypass the BTM service and silence the app's security alerts, allowing it to persist on a device. Wardle says he reported the issues to Apple and that the company patched them. Nevertheless, the researcher described the fixes as "putting some tape on an airplane as it's crashing," suggesting that the BTM utility still needs a lot of work. [Additional coverage in Wired]
CODESYS vulnerabilities: Microsoft researchers have discovered 15 vulnerabilities in CODESYS V3, a software development kit (SDK) used to program PLCs. Twelve of the 15 vulnerabilities could be used for remote code execution attacks. All issues were patched by CODESYS. Microsoft has also released the tool it used to find the bugs.
Iagona vulnerabilities: Security firm Synack has found four vulnerabilities in Iagona ScrutisWeb, a web-based utility for managing ATM fleets. The vulnerabilities can allow threat actors to silently access ScrutisWeb panels, collect information on connected ATMs, install malicious software, and reboot or power-off devices. Synack says it didn't test to see if they could actually compromise and steal money from the ATMs since that was out of the scope of their research. All vulnerabilities were patched in July, and Synack says Iagona was prompt to respond to the bug reports.
Python lib vulnerability: A major vulnerability has been discovered in urllib.parse, a Python library for parsing URLs that is also included with many versions of the core Python programming language. The vulnerability (CVE-2023-24329) can allow attackers to bypass blocklists by supplying URLs that start with blank characters.
Data-center software vulns: Trellix researchers have identified nine vulnerabilities in two software utilities used across data centers—namely, Dataprobe iBoot PDU and CyberPower PowerPanel Enterprise. If exploited, the vulnerabilities can be used to shut down data center equipment, deploy malware at scale, or conduct silent espionage. All vulnerabilities have received fixes, but it's unclear how many of the hundreds of such systems available on the internet have been patched.
Zoom and AudioCodes vulnerabilities: SySS researchers have found an exploit chain involving AudioCodes desk phones and Zoom's Zero Touch Provisioning feature. The exploit can be used to hijack AudioCodes desk phones to decrypt communications and eavesdrop on communications. In addition, the vulnerabilities can also be used to deploy malware on the phones and even pivot to a company's internal network.
2017 Zyxel vulnerability: US networking equipment vendor Zyxel has sent a security alert to customers warning that a threat actor is exploiting an old 2017 vulnerability to install a version of the Gafgyt malware on customer systems. For now, the attacks seem limited to the company's P660HN-T1A routers. The vulnerability is tracked as CVE-2017-18368. Fortinet says it's detecting roughly 7,000 exploitation attempts per day for this vulnerability.
Citrix exploitation: Stairwell has observed new exploitation patterns for attacks targeting Citrix NetScaler ADC gateways using the CVE-2023-3519 vulnerability. Initial attacks were linked to suspected Chinese state-sponsored hackers. The new attacks suggest new threat actors are exploiting the same bug.
SugarCRM exploitation: Palo Alto Networks says it has seen threat actors use a recently-patched SugarCRM zero-day (CVE-2023-22952) as an entry point into corporate environments, where they scanned for access keys and pivoted to AWS infrastructure.
Lexmark PoC: Security firm Horizon3 has released a PoC for a Lexmark printer exploit they used at a hacking contest last year. The vulnerability, CVE-2023-34362, is a command injection bug that can be used to dump local or AD credentials, install shells, or just use the printer's beeping function to play music.
WPS Office RCE: Security researcher BaoGuo has published a PoC for a remote code execution bug in WPS Office, a Chinese office software suite.
Infosec industry
Black Hat 2023: Presentation slides from the recently-concluded Black Hat USA 2023 security conference are available on its official site or in this GitHub folder.
New tool—VED-eBPF: Security firm Hardened Vault has open-sourced a tool named VED-eBPF, a proof-of-concept kernel exploit and rootkit detection system using eBPF.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq ask whether Chinese operations are becoming stealthier and why. Is it a top-down directive to be careful, or do the operations themselves require more stealth?




