Risky Biz News: Congress considers making CSRB permanent and more independent and transparent
In other news: GitHub rotates signing keys; new Samsung phones to get 7 years of security updates; DDoS attacks hit Switzerland during Zelenskyy visit.

This newsletter is brought to you by Panther, the scalable detection-as-code based SIEM. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Following a hearing of the Senate Homeland Security and Governmental Affairs Committee, US lawmakers said they're considering legislation that would make the DHS Cyber Safety Review Board (CSRB) a permanent organization in the US cybersecurity space.
Established in May 2021 through a White House executive order, the CSRB was set up as an analog to the TSA's National Transportation Safety Board (NTSB).
It was established in the aftermath of the SolarWinds supply chain attack as an independent board tasked with investigating cybersecurity-related incidents that affect the US government and issuing recommendations to improve security measures across both the US public and private sectors.
Since its inception, the CSRB has published two reports, one covering the Log4Shell vulnerability and another covering the Lapsus$ hacking group.
Three cybersecurity experts invited to testify at the hearing argued that while the CSRB was a step in the right direction, the Board was somewhat ineffective, and its reports were superficial.
Some blamed the Board's current problems on the CSRB's lack of subpoena powers, which meant that the CSRB would often have to put reports together using legally sanitized statements rather than raw incident response data.
No subpoena powers also means the Board can't force companies and individuals to cooperate and (still) needs to lean on its subjects' goodwill and cooperation to get the answers it desires.
"I think that the big challenge that we have with a lack of subpoena power on the current Board is that the real answers are often found about three layers deeper than the information that, as far as I'm aware now, is being provided to the Board," Tarah Wheeler, CEO at Red Queen Dynamics, told the HSGAC.
John Miller, Senior Vice President of Policy, Trust, Data, and Technology and General Counsel at the Information, was the only one among the three to oppose the idea of giving the Board subpoena powers.
"I think that it's premature to say that a board focused on investigating incidents needs subpoena power to get information until we know what those regulations say and what information is already going to be mandatorily required to be provided to CISA and the government. I think that the other factors that I would keep in mind are, one, CISA has long had a partnership mission and collaborative mission with the IT sector and all critical infrastructure sectors in areas such as information sharing and otherwise. We are concerned subpoena authority puts CISA, particularly, if that's where the CSRB continues to live, in a more adversarial position with the private sector."
Miller also brought up the other current major issues with the CSRB, which he says lacks the transparency and independence of the much more successful NTSB, a topic also brought up by Trey Herr, Director Cyber Statecraft Initiative at the Atlantic Council.
The two argued that the procedures around how CISA decides what the CSRB investigates are still unclear. While the Log4j and Lapsus$ topics were important, the CSRB has often skipped on looking at incidents with a broader impact on national security.
It took quite a lot of pressure from US Senators and the private sector to convince CISA to have the CSRB look at the recent Storm-0558 hack of Microsoft infrastructure from June 2023.
"The Board provides the potential for a long range lens. Not just a reactive moment, but potentially picking historical incidents that have far greater consequence for the design and operation of these systems than we understand in the moment," Herr said.
Wheeler also touched on the Board's membership, which she argued should be staffed with dedicated investigators rather than industry figureheads, especially those from the private sector, which may end up investigating competitors.
"Many individuals on the CSRB are beloved and respected, but they do have full-time jobs, and they do not have the time, freedom, and authority to conduct independent, thorough investigations."
Wheeler also asked lawmakers not to introduce classified information and require clearances to sit on the CSRB.
"Lack of transparency around how people are currently nominated to the CSRB and how the Board selects which investigations they pursue may decrease trust in its impartiality. In addition, forcing CSRB members to hold clearances would drastically limit the pool of potential investigators in the already massive deficit of US cyber security talent."
The HSGAC hearing was conducted at the request of the White House, which asked Congress to codify the CSRB as part of the US National Cybersecurity Strategy last year [PDF, page 16].
Breaches, hacks, and security incidents
DDoS attacks on Swiss sites: Switzerland's cybersecurity agency has confirmed that a wave of DDoS attacks has caused temporary outages of several government portals. Swiss officials have blamed the attack on NoName, a Russian-linked hacktivist group. The attacks coincided with Ukrainian President Zelenskyy's attendance at the World Economic Forum's annual meeting.
Kyivstar attack: Dutch telecommunications company Veon expects to lose around $95 million in the aftermath of Russia's cyberattack on Kyivstar, Ukraine's largest mobile operator. Veon says the figure represents lost revenue and loyalty measures Kyivstar had to pay out to customers following its prolonged outage. Hackers part of Russia's military intelligence unit breached Kyivstar on December 12 and wiped thousands of the telco's servers.
Socket crypto-heist: Cryptocurrency platform Socket temporarily halted operations of its Bungee trading platform after a threat actor stole $3.3 million in assets. The company believes the attacker exploited one of its wallets. Socket restarted Bungee after fixing the issue and said it was working on a compensation plan for affected users. [Additional coverage in CoinDesk]
GitHub rotates keys: Code hosting platform GitHub has rotated GPG keys used by its apps and API to sign code commits and submit secrets. The company rotated the keys after receiving a bug report about a vulnerability that could have allowed threat actors to gain access to the signing keys. GitHub says it did not find evidence that the bug was exploited prior to getting patched.
Naz.API leak: A threat actor has leaked more than 104GB of infostealer logs and credential-stuffing lists. According to security researcher Troy Hunt, the data contains more than 71 million unique email addresses and 100 million unique passwords. Named Naz.API, the leaked data was added to Hunt's Have I Been Pwned database.
General tech and privacy
Samsung S24 to get 7 years of updates: Samsung has launched its new line of S24 smartphones, and the company has committed to providing seven years of software and security updates. Previously, the company's smartphones were only supported for five years. Samsung joins Google to be the only vendor to provide seven years of security updates for its Android smartphones.
Chrome Incognito Mode update: Google is changing the text that appears in Chrome's Incognito Mode browser mode. The change comes after the company settled a 2020 lawsuit for tracking users while in Incognito Mode. The new text informs users that their activity will be tracked by the company.
"Others who use this device won't see your activity, so you can browse more privately. This won't change how data is collected by websites you visit and the services they use, including Google. Downloads, bookmarks, and reading list items will be saved. Learn more"
YouTube making millions of climate disinformation: A new study has found that YouTube is making millions of dollars a year from running ads on climate change disinformation videos. The study also found a new trend in climate change disinformation, where instead of negating that climate change happens, videos claim that clean energy solutions don't work and that the world should embrace more fossil fuels. [Additional coverage in CBC]
Yahoo fined in France: French privacy watchdog CNIL has fined Yahoo's EMEA branch €10 million for failing to comply with the EU GDPR regulations. CNIL says Yahoo ignored user choices and continued to use tracking cookies for the users of its Yahoo Mail service. The agency says Yahoo also ignored users who withdrew their consent through the Yahoo Mail interface.
Facebook tracking: A Consumer Reports study found that users generally have their data collected and sent to Facebook's ad platform by roughly 2,230 companies, on average. Some users even had their data collected by more than 7,000 companies.
ACSC phone security guide: The Australian Cyber Security Center has published a guide on how business leaders can keep their devices secure. The guide comes with several recommendations, including the advice to turn devices on and off on a daily basis. A similar advice was shared by the makers of mobile operating system GrapheneOS a week earlier.
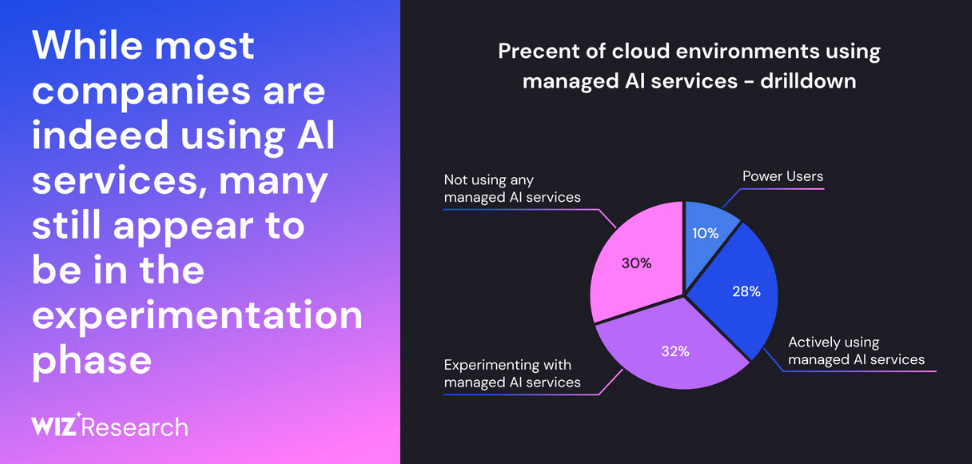
State of AI in the Cloud: Cloud security firm Wiz has published its State of AI in the Cloud 2024. According to Wiz, AI is rapidly gaining ground in cloud environments, with over 70% of organizations now using managed AI services.
Government, politics, and policy
FTC joins CAPE: The US Federal Trade Commission has joined Global Cooperation Arrangement for Privacy Enforcement (Global CAPE), an international organization that facilitates cooperation and assistance in privacy and data security investigations.
US warns of Chinese drones: CISA and the FBI have published a joint security advisory warning US companies and federal agencies against the use of Chinese drones. The two agencies describe Chinese drones as a national security threat and claim they could be used to collect and spy on US critical infrastructure sites. US officials cite recent Chinese laws that grant the government the power to coerce companies into helping its espionage efforts.
Election interference: The Chair of the US Senate Intel Committee has urged CISA to recommit to fighting foreign malign influence ahead of the upcoming 2024 US Presidential Elections. Sen. Mark Warner has cited a recently declassified intelligence report describing an uptick in disinformation efforts from US adversaries. Sen. Warner filed an amicus brief in support of CISA in its Supreme Court case, where several Republican states are trying to limit the agency's role in combating election disinformation.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Ken Westin, Field CISO at Panther, about how the rise of cloud and hybrid IT architectures requires a new type of SIEM.
Cybercrime and threat intel
npm dead repos: A study from Aqua Security estimates that the real number of deprecated packages is around 21.2%, rather than the official 8.4%. The company is basing new figure on the practice of some developers who remove or archive their libraries when confronted with a security flaw, rather than fixing it.
Microsoft IR guide: Microsoft has published incident response guides for its Entra and 365 services.
"These guides contain the artifacts that Microsoft Incident Response hunts for and uses daily to provide our customers with evidence of Threat Actor activity in their tenant."
Water sector IR guide: CISA, the FBI, and the EPA have released an incident response guide for organizations in the water and wastewater management sector.
BEC increase: BEC attacks grew by 137% last year, according to an Abnormal Security report.
AI scams targeting Romania: Cyber Geeks has published a report detailing an online scam using AI-generated content targeting Romanians with investment opportunities in one of the country's main energy providers. The scam is abusing YouTube ads and has been going on since October of last year. Google has refused to take any action against it despite numerous reports from Romanian cybersecurity vendors and experts—including this reporter. The Romanian company whose brand is being abused has also warned customers not to fall victim to the scam.
TA866: Proofpoint has seen the return of TA866, a new financially motivated threat actor the company first saw last year.
Mimo: AhnLab researchers have published a profile on Mimo, a threat actor active since 2022. The group operates by using vulnerabilities to breach servers, where it installs cryptominers and proxyware. AhnLab says the group has recently also started installing ransomware (named Mimus) on hacked servers.
NoName057(16): Netscout researchers have published a profile on NoName057(16), a pro-Kremlin hacktivist group that's been recently involved in a long list of DDoS attacks against what they call "pro-Ukrainian organizations," may them be Western government or just random shoe stores.
Punchmade shop: A rapper named Punchmade Dev, known for singing about the cybercrime lifestyle, has apparently launched a card shop. Yes, I am just as shocked as you are. According to infosec reporter Brian Krebs, Punchmade is a young man named Devon Turner from Lexington, Kentucky. [Additional coverage in KrebsOnSecurity]
Malware technical reports
Monster Stealer: CyFirma researchers have published a report on Monster Stealer, a new infostealer advertised on Telegram by a Russian threat actor that gained popularity last year by releasing free infostealer logs on their channel.
Chae$ 4.1: Morphisec has published an analysis of Chae$ 4.1, the latest version of Chaes, a malware strain designed to infect Chrome browsers and exfiltrate data from users of Latin American online marketplaces since 2020.
macOS malware: SentinelOne looks at how three macOS infostealers (CherryPie, KeySteal, and Atomic InfoStealer) are evading XProtect signatures.
New botnet: Cado Security researchers have discovered a new botnet that infects Docker instances to deploy a cryptominer and 9Hits, an app that allows the attacker to monetize the hacked server's bandwidth.
Kuiper ransomware: Trellix researchers have published a breakdown of the Kuiper ransomware. According to Trellix, the ransomware has evolved quite a lot since its launch in September of last year. There are similar reports on this new ransomware strain from Stairwell and BishopFox as well.
Sponsor Section
A short demo on how to use Panther's Detections-as-Code (DaC) platform for cryptominer investigations.
APTs, cyber-espionage, and info-ops
Mint Sandstorm: Iranian APT group Mint Sandstorm is conducting spear-phishing campaigns aimed at compromising high-profile individuals working on Middle Eastern affairs at universities and research organizations in Europe and the US. Mint Sandstorm attempted to masquerade as known journalists seeking expert input on the Israel-Hamas war. According to Microsoft, the group tried to infect targets with a new, custom backdoor called MediaPl. The Mint Sandstorm overlaps with other Iranian threat actors tracked as APT35 and Charming Kitten and is linked to Iran's Islamic Revolutionary Guard Corps (IRGC) military intelligence service.
ColdRiver: Google's TAG security team has observed the ColdRiver APT group conducting new hacking operations targeting Western officials. The recent wave of attacks employed a new custom backdoor named Spica, a deviation from the group's typical account compromise and disinformation efforts. In early December 2023, the British government publicly linked the group to Center 18, a cybersecurity division inside Russia's FSB intelligence agency.
Vulnerabilities, security research, and bug bounty
Toyota network compromise: Security researcher Eaton Zveare broke into the network of a Toyota insurance broker through the company's premium rate calculator.
HVCI bypass: Software engineer Satoshi Tanda has published a technical write-up on CVE-2024-21305, a bypass of the Hypervisor-Protected Code Integrity (HVCI) security feature in Windows.
Oracle CPU: The quarterly Oracle security updates are out, with patches for 387 vulnerabilities.
Outlook bug: Varonis researchers have published a write-up on CVE-2023-35636, a new way to steal NTLM hashes via Outlook.
TensorFlow bug: Praetorian researchers have identified a series of CI/CD misconfigurations that, when combined, can lead to compromise of TensorFlow releases. Google has fixed all issues.
RBI bypass: Security researchers at SpecterOps have devised a method to break and bypass Remote Browser Isolation (RBI), a security technology that isolates a user's browsing experience inside a remote cloud VM, lowering security risks.
Drupal security updates: The Drupal team has released a security update for the team's CMS that could allow attackers to crash sites via their comment fields.
Hidden Juniper bugs: According to watchTowr Labs, Juniper has secretly patched four vulnerabilities in JunOS without disclosing the bugs or filing for a CVE.
"Given this, it is interesting that Juniper did not find at least the missing authentication vulnerability to be severe enough to justify an out-of-cycle advisory, nor to register CVE or mention them in the release notes (although they did deem them important enough to request we delay our usual and industry-aligned 90-day VDP timeline)."
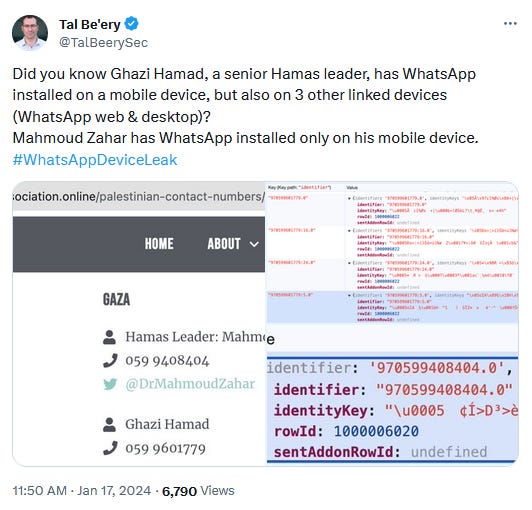
WhatsApp leak: ZenGo co-founder and CTO Tal Be'ery has disclosed a vulnerability that allows threat actors to determine how a user is using the WhatsApp instant messaging service. The bug allows attackers to determine how many devices a user has registered and if they are using the WhatsApp web interface. The attacker only needs a user's phone number, and the technique works even if the victim blocks the attacker's phone number. Be'ery disclosed his findings after Meta declined to patch the issue.
Infosec industry
New tool—Application Block: Malwarebytes has made its Application Block free as part of its ThreadDown offering.
New tool—LVE Repository: A group of academics and software engineers have released LVE Repository, a portal that documents and tracks vulnerabilities and exposures of large language models (LVEs).
New tool—Cybersecurity Incident Tracker: Security researcher Andrew Hoog has put together Cybersecurity Incident Tracker, a portal that tracks cybersecurity incidents reported via SEC 8K forms.
Industry moves: Email security company has appointed Marc van Zadelhoff as its new CEO. Former CEO Peter Bauer will remain a member of the Board.
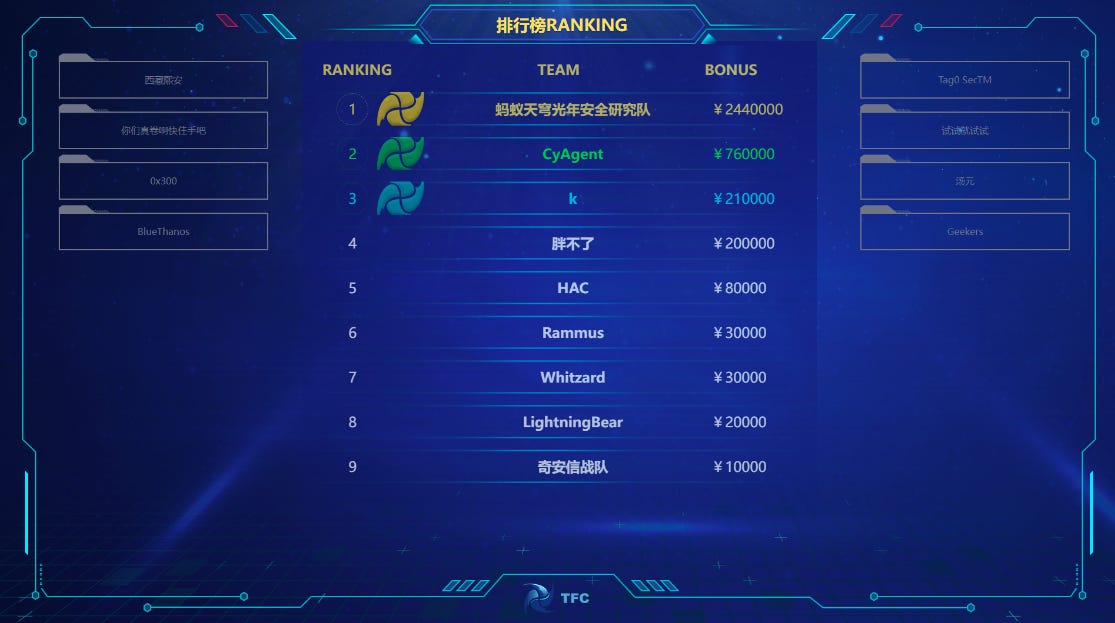
Tianfu Cup 2023: Ant Group's Lightyear Lab has won the 2023 edition of the Tianfu Cup, China's most prestigious hacking contest. The competition took place in November 2023 after organizers canceled the contest's 2022 edition with no explanation. The cancellation came after several reports that bugs found during the 2021 edition were used in the wild by Chinese state-sponsored hackers days after the contest. Sixty-two teams participated in the 2023 edition, which featured new rules and a lot more Chinese products on the target list. Despite the change, the highest prices were still offered for Western products, while contest organizers shared very little information about what products were targeted or successfully hacked. [Additional coverage in Natto Thoughts]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how Stuxnet was an 'inevitability gamechanger,' how much we now know about the operation, and how much the Dutch government should have known at the time.




