Risky Biz News: Clop is coming after your SysAid servers
In other news: OCCRP's India reporters targeted with Pegasus; China hacks 24 Cambodian government agencies; and Nokoyawa ransomware gang retires.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The infamous Clop ransomware gang is exploiting a zero-day vulnerability in on-prem SysAid IT automation servers.
The attacks were discovered last week by SysAid's security team, and the company released a software update to patch the exploited bug.
Tracked as CVE-2023-47246, SysAid's team described the zero-day as a "path traversal vulnerability leading to code execution."
The company says it worked with security firm Profero to investigate the attacks and found similar exploitation. Attacks involved exploiting the zero-day to gain control over the server, downloading and installing a Java webshell, and then running a series of PowerShell commands that installed the GraceWire trojan.
The attackers then used a second set of PowerShell scripts to remove traces of their intrusion and then moved to hands-on-keyboard activity on the compromised systems.
According to Microsoft's threat intel team, this involved the same Clop shenanigans of moving laterally across local networks, stealing any data they can get their hands on, and encrypting with its ransomware.
The recent attacks would make SysAid the fourth different enterprise software the gang has exploited this year after it previously targeted GoAnywhere and MOVEit file transfer servers and PaperCut print management servers.
All of these attacks are now part of Clop's regular mode of operation, which involves targeting popular enterprise software, stealing corporate data, encrypting systems, and then asking for ransoms for the decryption key or not publishing the victim's data.
The group has been doing this since late 2021 and rose to infamy after its successful mass exploitation of Accellion file transfer appliances.
On its website, SysAid says it has more than 5,000 customers, but IoT search engines like Shodan appear to see only 500 of these systems exposed on the internet.
Breaches, hacks, and security incidents
OCCRP journalists targeted with Pegasus: Two Indian reporters from the Organized Crime and Corruption Reporting Project have had their phones targeted with the Pegasus spyware. The attacks took place hours after the two reporters reached out for comment to the Adani Group, one of India's largest companies. The reporters were investigating the Adani Group's owners for possible market manipulation by secretly buying their own stocks. OCCRP reporters Ravi Nair and Anand Mangnale are two of the 20 Indians that Apple notified in October that their phones were targeted by state-sponsored malware.
ICBC ransomware attack: The Industrial and Commercial Bank of China has suffered a ransomware attack. The incident impacted the bank's ability to connect to US markets and settle trades for Chinese entities. ICBC is China's largest commercial lender by assets. [Additional coverage in the Financial Times/non-paywall]
Nordex BEC scam: Wind turbine giant Nordex lost $800,000 to a BEC scam after one of the company's employees paid a fake invoice to a scammer's account. The incident could have been worse since the invoice total was $1.75 million, which Nordex couldn't pay at the time. Nordex discovered the scam a month after making the initial payment. The FBI says that $50,000 of the stolen funds were sent to the bank account of Dr. Kelechi Ofoegbu, a Nigerian government official and regulator of the oil and gas industry. [Additional coverage in Forbes/non-paywall]
Sumo Logic breach: Cloud security company Sumo Logic has disclosed a security breach after a threat actor used a set of compromised credentials to gain access to its AWS servers. The company has rotated all its infrastructure and is now asking customers to reset and rotate their API keys. The keys are typically used to sync SIEM logs and backups from customer systems to Sumo Logic's servers.
OpenAI DDoS attacks: ChatGPT maker OpenAI says the recent technical outages appear to have been caused by a series of DDoS attacks that hit its servers.
CoinSpot crypto-heist: Cryptocurrency exchange CoinSpot has lost $2.4 million worth of crypto-assets after a threat actor used an unknown exploit to siphon the funds. The attack targeted two of the company's hot wallets. The Aussie company has yet to publicly confirm the hack.
MEV crypto-heist: A threat actor stole $2 million worth of cryptocurrency from an automated MEV (maximal extractable value) bot after its owner failed to set up the proper permissions.
General tech and privacy
Smart cars privacy lawsuit: A Washington state federal judge has ruled in favor of car manufacturers in a lawsuit that challenged their right to intercept and store a car owner's text and call logs. The judge ruled that carmakers didn't break state privacy laws when car infotainment systems secretly collected user data from drivers' phones when they were connected to the car. [Additional coverage in The Record]
NY data breach fine: The state of New York has fined healthcare provider US Radiology $450,000 for not securing its networking gear, which eventually led to the company getting ransomed and crooks stealing the data of 92,000 New Yorkers.
Omegle shuts down: Live video chat website Omegle has shut down 14 years after it first launched and after countless claims of child abuse. In a statement on its website, Omegle founder Leif Brooks said the site was no longer sustainable financially and psychologically. The site was known for matching random people in video chats and grew in popularity during the COVID-19 pandemic. It became widely known after it became a hunting ground for pedophiles, with more than 50 criminal cases citing Omegle in court documents. [Additional coverage in the BBC]
Zuckerberg ignored child safety: Court documents reveal that while executives called on Mark Zuckerberg to devote more staff to improve child safety on the company's apps, Meta's CEO ignored the requests for months while his company was doing the PR rounds about how safe the site was for kids. [Additional coverage in CNN]
2FA at DNA testing companies: DNA testing and genealogy companies Ancestry, MyHeritage, and 23andMe are enabling 2FA for all their customer accounts in an attempt to protect their users from brute-force attacks and account hijacking. [Additional coverage in TechCrunch]
ADA update: Google is relinquishing its control over the App Defense Alliance, and the organization will migrate under the Linux Foundation umbrella. As part of the move and restructuring, Microsoft and Meta are joining Google in the organization's founding steering committee to help ADA move forward with broader app security standards. Google founded the App Defense Alliance in 2019 with a focus on Google Play Store and Android app security. The organization expanded its scope in 2022 to cover cloud apps and security assessments.
GitHub Advanced Security: GitHub has announced the addition of AI-powered tools to its Advanced Security package.
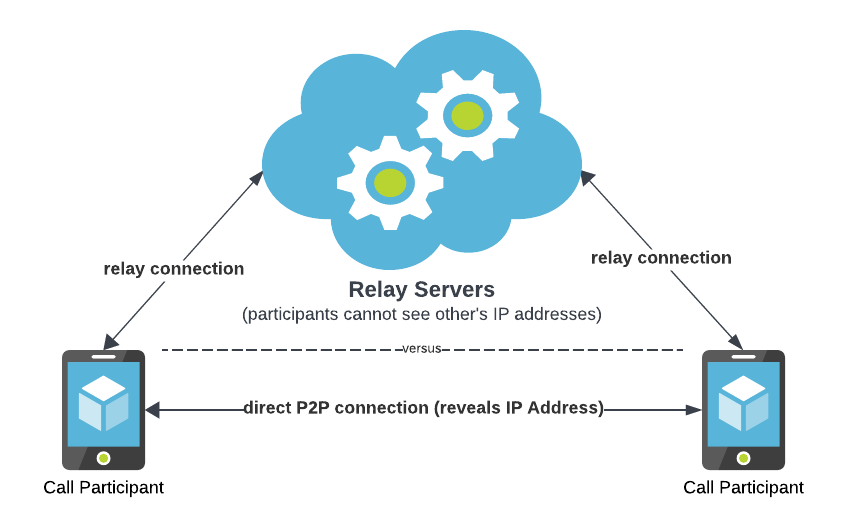
WhatsApp Protect IP Address in Calls: Meta has announced two new security features for its WhatsApp instant messaging application. The first is named "Protect IP Address in Calls" and works by relaying all calls through WhatsApp servers in order to hide each participant's IP address from one another. The second is named "Silence Unknown Callers" and works by silencing calls from numbers that are not in a user's address book. Meta's engineering team says this second feature has a secondary side-effect of blocking zero-click exploits delivered via calling and network protocols. Meta did this by building a special protocol for delivering stripped-down, silenced call notifications and letting recipients choose to upgrade the alert to a fully-featured call.
Signal tests usernames: The Signal encrypted instant messaging service is testing support for usernames as a replacement for its current system, where real-world phone numbers serve as user identities. The new feature is currently available for the app's testers. Once finalized and released to the stable channel, users can select their usernames by going to the Settings/Profile and Settings/Privacy/Phone Number section. Signal devs did not say when they expect the new feature to launch.
Government, politics, and policy
Microsoft provides new election security tools: Microsoft is offering US politicians and campaign groups new tools to counter the rise of deepfakes and AI in the current election landscape. Named Content Credentials as a Service, the tool will help campaigns cryptographically watermark multimedia content. Microsoft says the tool will help campaigns spot when their content was modified using AI without authorization. In addition, Microsoft has also set up new teams to help candidates deal with cyber-influence campaigns.
Shields Ready: The DHS, CISA, and FEMA have launched a new project named Shields Ready, a campaign aimed at critical infrastructure operators and meant to get them to improve their cyber and physical security resilience.
Online Safety Act recommendations: UK telecommunications watchdog Ofcom has published draft guidance on how tech companies can comply with the UK's recently passed Online Safety Act, a new law aimed at making the internet safer for kids. The primary recommendations are below.
- Children should not see lists of suggested friends;
- Children should not appear in other users' lists of suggested friends;
- Children should not be visible in other users' connection lists;
- Children's connection lists should not be visible to other users;
- Accounts outside a child's connection list should not be able to send them direct messages;
- Children's location information should not be visible to any other users.
Russian media police: You can now get a "media police" bachelor's degree from Russian universities to police the internet and flag extremism, terrorist propaganda, piracy, and cyberbullying to Russian authorities. [Additional coverage in Izvestia]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Huxley Barbee, Security Evangelist at runZero, about finding the unknown unknowns and what is a security evangelist.
Cybercrime and threat intel
Artemis Refund Group: The US government has arrested members of the Artemis Refund Group, a criminal gang that specializes in large-scale refund fraud. The group works with insiders at retailers and helps customers place large orders and then recover their money but keep the products. The group operates via Telegram, and their most common tactic revolves around filing Did-Not-Arrive complaints. [Additional coverage in 404 Media]
Monopoly Market admin pleads guilty: A Serbian national has pleaded guilty in a US court to running Monopoly Market, a dark web drug market. Milomir Desnica, 33, was arrested in Austria in November 2022 and extradited to the US earlier this year. The Monopoly Market was taken down by German authorities in December 2021. Intelligence collected during the takedown was used to detain 288 drug traders in May this year, part of Operation SpecTor. Europol called it its most successful operation against dark web marketplaces so far.
Qakbot takedown aftermath: A KELA report found that the law enforcement takedown of the Qakbot botnet has had a minimal impact on the cybercrime underground, with many former Qakbot members and customers continuing to collaborate on operations.
Hunters International: Bitdefender has an analysis of recent attacks carried out by an extortion group named Hunters International, a rebrand of the Hive ransomware group.
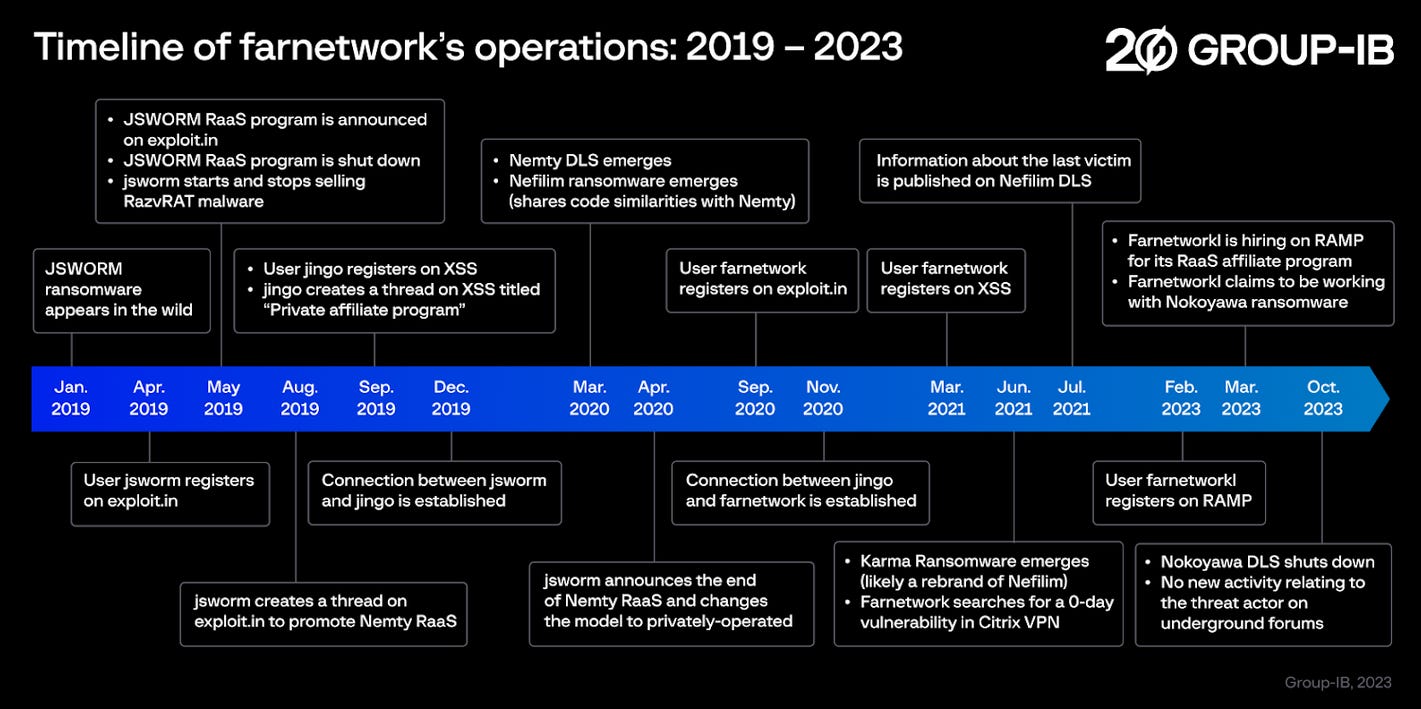
Nokoyawa RaaS shuts down: The Nokoyawa ransomware operation has shut down in October 2023 after a decision by its creator, a threat actor named Farnetwork. Prior to Nokoyawa, the same individual helped create and run other ransomware strains, such as JSWORM, Nemty, Nefilim, and Karma. Security firm Group-IB believes Farnetwork will most likely launch another RaaS platform under a new name.
New ransomware trends: The FBI says that since 2022, ransomware gangs have breached third-party gaming vendors as a way to gain access and encrypt the networks of US casinos. The attacks have targeted small and tribal casinos and are separate from the MGM and Caesars hacks that took place this August. The FBI says it is also seeing ransomware gangs use callback-phishing and remote access tools to gain access to corporate employee systems. One of the groups that has used this technique is the Silent Ransom Group, also known as Luna Moth. [Additional information in the FBI's PIN]
Ransomware campaigns: AhnLab is seeing phishing campaigns distribute the Phobos and LockBit ransomware.
WindowsReport/CPU-Z malvertising campaign: Malwarebytes has spotted a malvertising campaign activating on Google Search. The campaign used a clone of the WindowsReport tech news site to lure users to a malicious installer for the popular processor tool CPU-Z.
Google Forms abuse: Cisco Talos has discovered spam groups abusing the "Release scores" of Google Forms quizzes to deliver malicious mail to victims. Because the emails originate from Google servers, the campaigns bypass email security solutions. Talos says it saw abuse of this feature as far back as 2021, but volumes spiked this year.
SLP protocol enters abuse: CISA says threat actors are exploiting a vulnerability in the Service Location Protocol (SLP) to launch DDoS attacks in the wild. News of active exploitation comes six months after security firms said the protocol could be abused for the largest DDoS attacks known to date. Companies like Bitsight and Curesec said SLP had a DDoS amplification factor of 2,200, the third largest factor known to date. DDoS attacks abusing SLP come two weeks after a researcher posted a proof-of-concept tool on GitHub. The vulnerability that enables these attacks is tracked as CVE-2023-29552.
Sordeal releases free version: Per CyFirma security researcher Kaushík Pał, Nova Sentinel, the author of the Sordeal infostealer, has released a free version of their malware.
Malware technical reports
BlazeStealer: Checkmarx has discovered a malicious campaign on PyPI distributing a new malware strain, BlazeStealer. Controlled via a Discord bot, the malware can be used to steal credentials from infected hosts, take screenshots via the webcam, and even deploy additional malware.
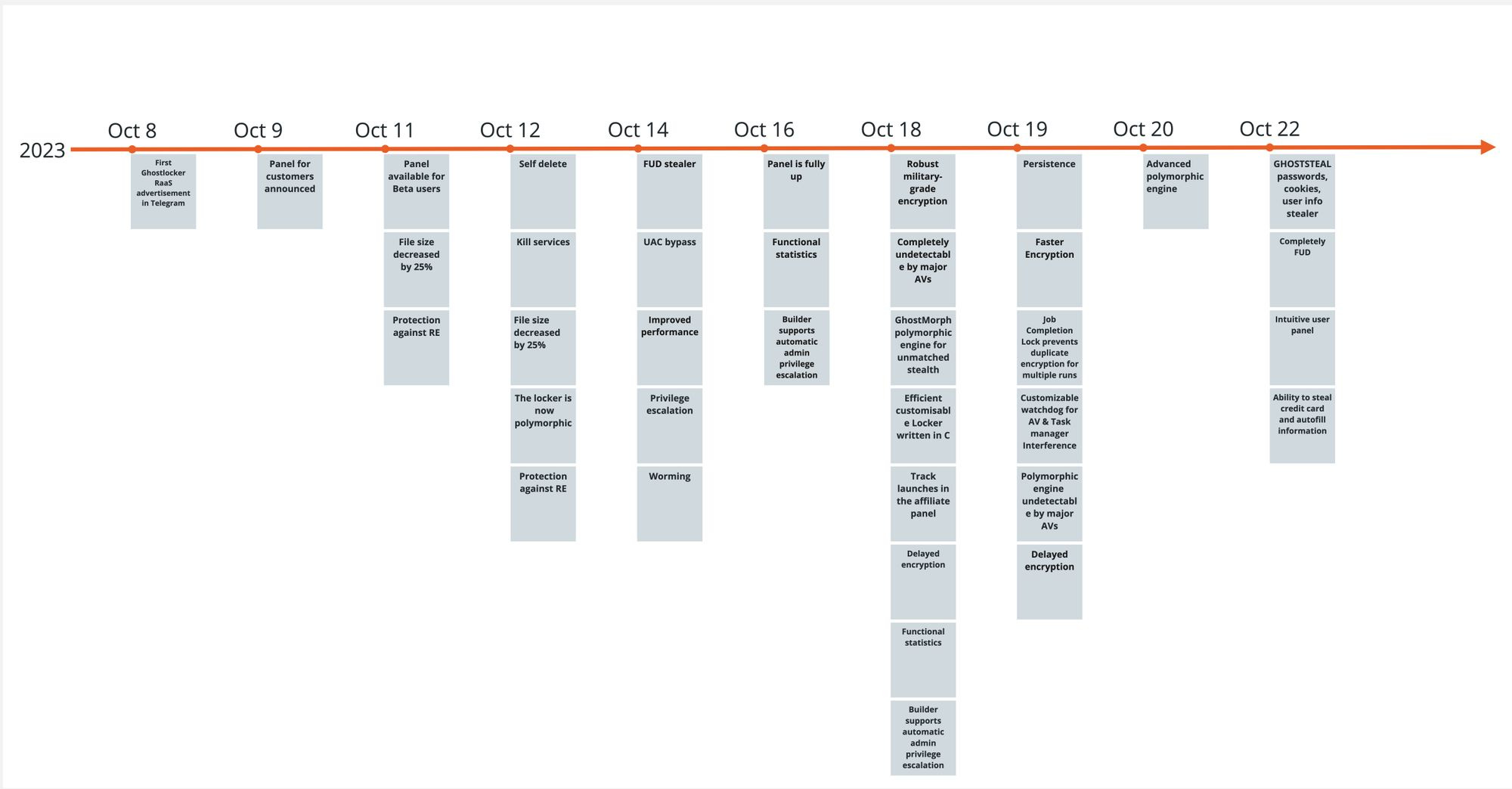
GhostLocker: Rapid7 looks at GhostLocker, a RaaS created by the GhostSec "hacktivist" group.
Sponsor Demo
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
NSA's SecondDate: Chinese security researchers have published a technical analysis of SecondDate, a malware strain first detailed in the Snowden leaks (2013). In September, the Chinese MSS claimed the NSA used the malware as recently as June 2022 to hack the network of the Xi'an Northwestern Polytechnical University.
Black Cube campaign: Microsoft's security team says that Israeli private intelligence agency Black Cube (tracked as Blue Tsunami) is conducting LinkedIn phishing campaigns. The company honeypot profiles, fake jobs, and fake companies to engage in reconnaissance or human intelligence (HUMINT) operations on behalf of its customers.
Caracal Kitten: Chinese security researchers have a breakdown of a new mobile RAT used by the Caracal Kitten APT.
MuddyWater's MuddyC2Go: Deep Instinct researchers have analyzed MuddyC2Go, a new command and control (C2) framework used by Iranian cyber-espionage group MuddyWater. The framework is written in Go and has been used in attacks since 2020.
No Iran-Hamas cyber cooperation so far: Microsoft says it has not seen any signs of cyber cooperation between Iran and Hamas hackers, either prior to or after the start of the recent Hamas-Israeli conflict last month.
Sapphire Sleet: Microsoft says it is seeing the Sapphire Sleep APT setting up new infrastructure for its LinkedIn social engineering campaigns. The group, also known as BlueNoroff, has a history of targeting individuals working in the cryptocurrency space.
Asian APTs: Kaspersky has a top-down look at the recent tactics employed by "modern" Asian APTs in their intrusions across the globe. The report is 370 pages long and mainly covers attacks from Chinese APTs, such as Stone Panda, Emissary Panda, Mustang Panda, APT41, and others.
Chinese APT in Cambodia: Chinese state-sponsored hackers have breached at least 24 Cambodian government agencies in one of the largest compromises of the year. The intrusions were spotted by security firm Palo Alto Networks, who detected traffic going from the compromised agencies to the infrastructure of a Chinese APT group. The infrastructure had been disguised to look like cloud backup services. According to Palo Alto, hackers seem to have gained access to government agencies responsible for national defense, elections, finances, telecommunications, and natural resources.
Kremlin "influence-for-hire" firms: The US State Department says the Kremlin is using three "influence-for-hire" companies to spread its propaganda across Latin America. Officials say companies such as the Social Design Agency, the Institute for Internet Development, and Structura have helped plant pro-Russian stories with local news outlets and social media influencers. The State Department says the articles are written in Russia, translated to Spanish or Portuguese, and then sent to the three companies for promotion across local news outlets. Officials have named Ilya Gambashidze as the lead in Russia's disinformation effort in Latin America.
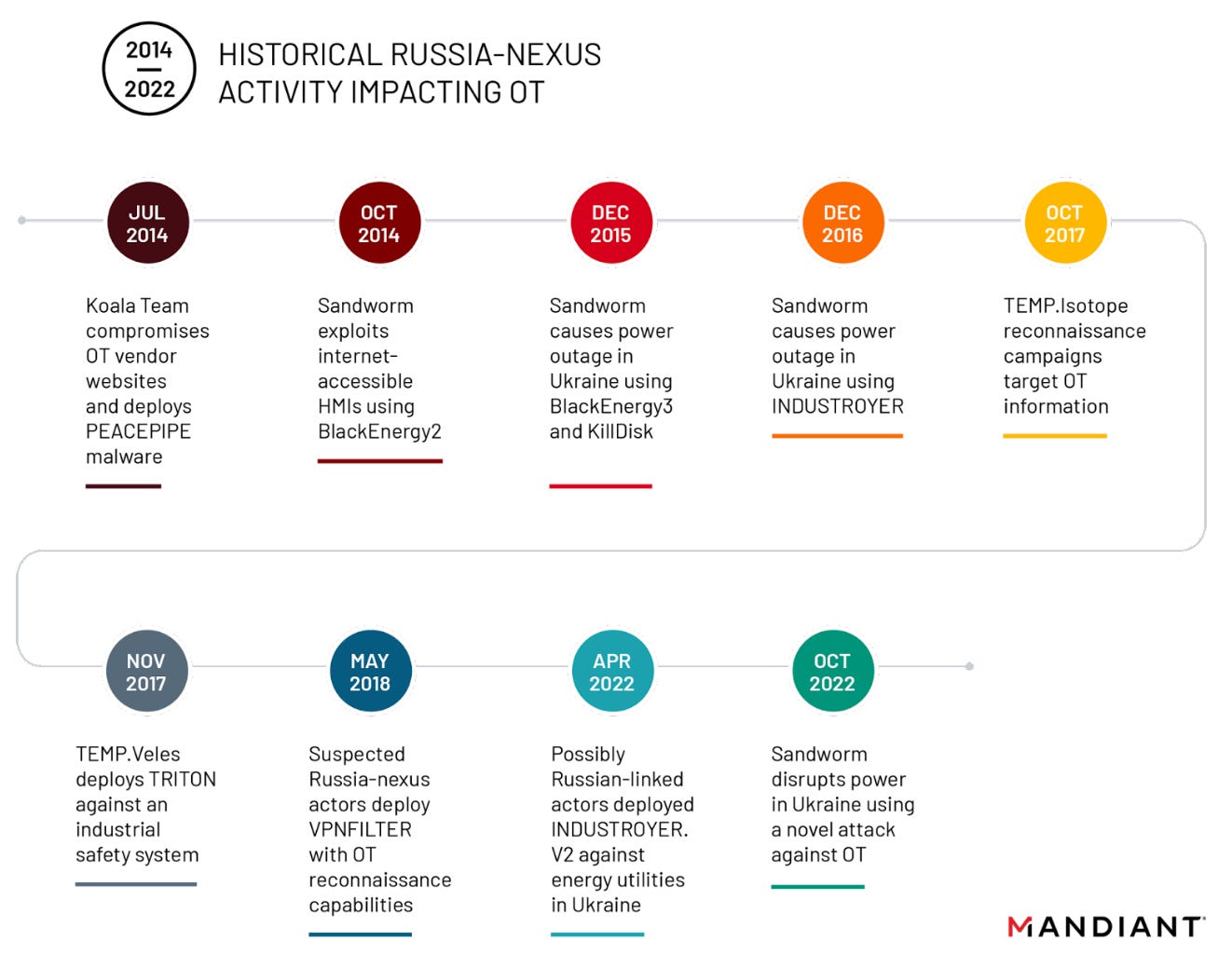
New Sandworm power grid attack: Russian military hackers breached the network of a Ukrainian power grid operator in June 2022 and launched a cyber-attack that crashed its OT environment to trigger a power outage in October 2022. This marks the third time since 2014 that Russian hacking group Sandworm has triggered a power outage in Ukraine using solely cyber tools. Mandiant says the cyber-attack coincided with missile strikes on critical infrastructure across Ukraine. The security firm told Wired reporter Andy Greenberg that they don't have evidence to support the theory that Russia intended the blackout and bombings to be simultaneous, but Mandiant pointed out that Sandworm held on to access to the hacked power grid for weeks prior to deploying their attack just before the kinetic missile strikes.
Vulnerabilities, security research, and bug bounty
Defiant bug bounty program: Security firm Defiant, the maker of the Wordfence firewall plugin for WordPress sites, has launched a private bounty program. The program will work like ZDI and will pay researchers to find vulnerabilities and disclose them privately to its program. Defiant will then handle disclosing and getting a fix pushed out for the bugs.
Azure Automation Service: Security firm SafeBreach has developed several ways to abuse the Azure Automation Service and execute code without getting charged—a useful feature for crypto-mining gangs. The company released a tool named CloudMiner that exploits these loopholes, some of which have been patched by Microsoft.
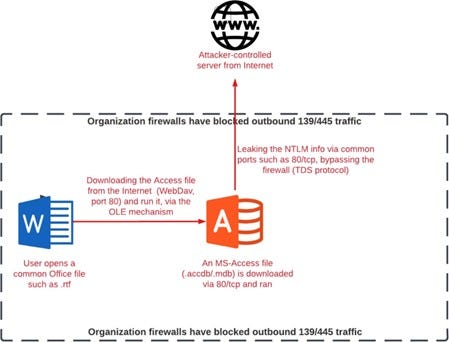
NTLM leak: Check Point researchers have identified a vulnerability in Microsoft Access databases that can be used to bypass firewalls and leak a Windows user's NTLM password hash. The technique abuses a Microsoft Access feature named Linked Table that allows Access databases to link to each other's tables. Check Point says the feature is exempt from local firewall rules, allowing attackers to piggyback on it and send NTLM hashes out of a network.
Netgear vulnerability: QuarksLab has published a write-up on CVE-2023-27368, a vulnerability in the soap_serverd daemon of Netgear routers. The company used the vulnerability in the 2022 edition of the Pwn2Own Toronto hacking contest.
PRTG RCE: Bladur Security has found an RCE (CVE-2023-32782) in the PRTG Network Monitor utility, often used in data centers and corporate networks.
Visual Studio Code vulnerabilities: SonarSource researchers have published part one of its three-part series on vulnerabilities they found in Microsoft's Visual Studio Code app. The team's DEFCON talk is below.
Infosec industry
Virus Bulletin 2023 videos: Talks from the Virus Bulletin 2023 security conference, which took place last month, are available on YouTube.
No Hat 2023 videos: Talks from the No Hat 2023 security conference, which took place last month, are available on YouTube.
New tool—ConscryptTrustUserCerts: NCC Group has open-sourced a tool named ConscryptTrustUserCerts that can be used for intercepting (some) HTTPS traffic on Android 14.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the internet-melting 1988 Morris Worm and how cyber security has changed since then.




