Risky Biz News: CitrixBleed vulnerability goes from bad to disastrous
In other news: iOS privacy feature didn't work for three years; CISA re-releases Logging Made Easy; and Israel recruits NSO and Candiru for Hamas war.
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A Citrix vulnerability has entered the dangerous stage of mass exploitation as multiple threat actors are compromising unpatched devices all over the internet in a race with each other to steal their session tokens.
Known as CitrixBleed and tracked as CVE-2023-4966, the vulnerability impacts Citrix ADC and Citrix NetScaler, which are extremely complex networking devices used in large enterprise and government networks in multiple roles, such as gateways, proxies, caching, VPN servers, and a bunch of other stuff.
The vulnerability allows threat actors to send junk data to the Citrix OpenID component that will crash and leak a part of the device's memory. The bad part is that, in some cases, this memory may contain session tokens that attackers can collect and then bypass authentication and access the device. For a more technical explanation, check this write-up from Assetnote researchers.
Citrix released patches to fix the CitrixBleed memory leak earlier this month, on October 10.
The bug in itself is extremely bad as it is, but things took a turn for the worse a week later when Google Mandiant researchers came out to say they found evidence CitrixBleed had been exploited in the wild since late August—making the vulnerability one of this year's tens of actively exploited zero-days.
Mandiant said a threat actor was using the bug to gain access to Citrix gateways and then pivot to internal systems. The attacks were small in scale and targeted professional services, technology, and government organizations.
Things turned from bad to disastrous last week, around October 23-25, when several proof-of-concept exploits started popping up on GitHub and vulnerability portals.
Within a day, mass-exploitation was in full swing. At the time of writing, GreyNoise is tracking more than 120 IP addresses that are probing the internet and attempting to exploit CitrixBleed.
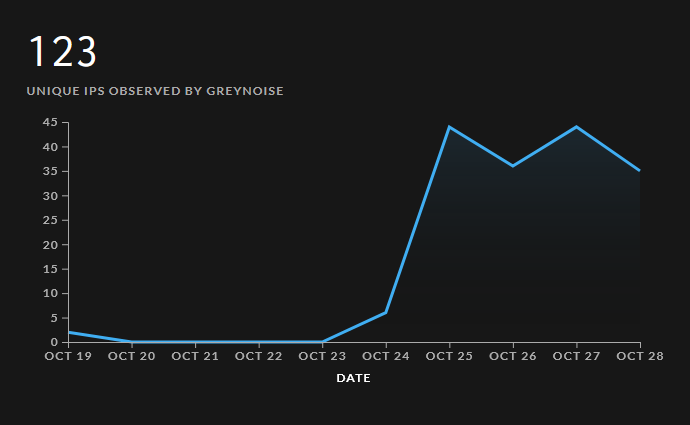
Some of the IPs are associated with initial access brokers, but at least a couple are associated with affiliates for the AlphV and BlackBasta ransomware groups, according to Chris Duggan, the Director of Cyber Threat Intelligence at KryptoKloud.
Security researcher Kevin Beaumont says that—just on Saturday, October 28—more than 20,000 Citrix ADC and NetScaler devices have had session tokens stolen.
Last week, Citrix seemed to have seen the disaster coming and published a blog post about the vulnerability, urging device owners to patch but also invalidate all their past session tokens so that even if they were swiped, they could not be abused in the future. Instructions on how to delete all past sessions are in the blog post.
Beaumont—which also has a write-up on this disaster—has also released a script to test if Citrix systems are vulnerable or still vulnerable after a patch.
The Shadowserver Foundation has also been following the attacks and how companies have been responding. Based on its internal data, the organization is still seeing almost 5,500 unpatched Citrix devices exposed on the internet.
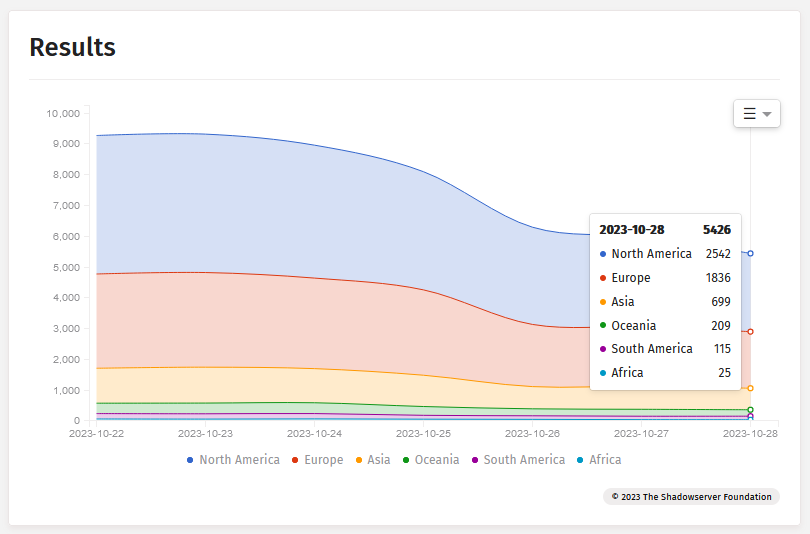
Some numbers here look odd, depending on what each company sees, but we nor you should need extra arguments to be convinced to patch this as soon as possible. We've honestly lost track of all the bad Citrix bugs of the past, but every time this reached the stage of mass exploitation, loads of big orgs and government agencies—especially from the US and Germany—began to appear on ransomware leak sites.
We've all seen this movie before, and there's no happy ending. This is gonna haunt organizations for months, and I will not be surprised if collections of Citrix session tokens start appearing for sale on underground hacking forums in the next weeks or so.
Breaches, hacks, and security incidents
Stanford University breach: The University of Stanford is investigating a security breach at one of its departments. The university confirmed a breach after the Akira ransomware listed the organization on its leak site last week. (h/t DataBreaches.net)
Crimea DDoS attacks: Ukrainian hacktivist groups launched a series of massive DDoS attacks at the end of last week that have disrupted internet services across the occupied peninsula. The attacks targeted MirTelecom, Krymtelecom, and MirandaMedia and impacted both mobile and landline internet connections. Russian officials confirmed the attacks and subsequent downtime in a Telegram post.
Khashoggi lawsuit dismissed: A US judge has dismissed a lawsuit filed by the widow of murdered journalist Jamal Khashoggi against Israeli spyware maker NSO Group. Hanan Elatr sued NSO earlier this year in June after the company's Pegasus spyware was used to hack her and her husband's phones before his murder. The judge dismissed the case because the hacking accusations were not sufficiently connected to the state of Virginia, where the lawsuit was filed. [Additional coverage in the Washington Post/non-paywall]
LastPass hack thefts: The hackers who breached LastPass last year stole another $4.4 million worth of crypto-assets from 25 customers last week. The hackers are cracking stolen LastPass password vaults, recovering crypto-wallet seed phrases, and stealing money from user accounts. With the latest round of thefts, this brings the total to almost $40 million after they previously stole another $35 million from ~150 other users earlier this year.
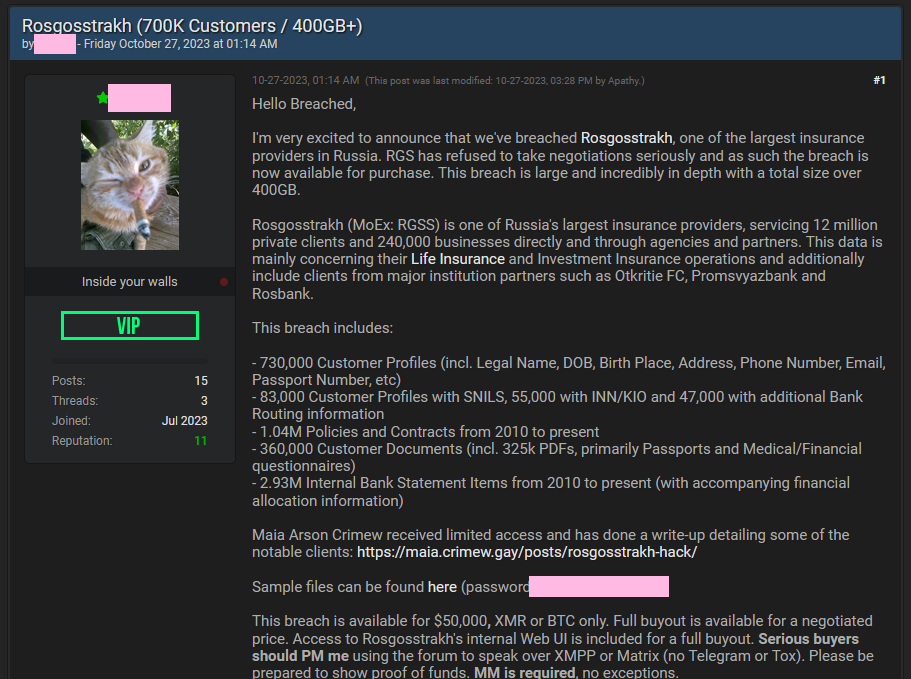
Rosgosstrakh hack: A threat actor is selling the data of 730,000 customers of Rosgosstrakh, Russia's second-largest insurance company. The data contains documents such as bank statements, scanned identification documents, and life insurance contracts. According to a review of the stolen files, the documents go back as far as 2010. The hacked company is one of the first entities put on the US sanctions list after Russia's invasion of Ukraine in February 2022.
General tech and privacy
Plea for longer Win10 support: More than 20,000 members of the Public Interest Research Group have asked Microsoft to extend support for the Windows 10 operating system, which is scheduled to reach End-of-Life status in two years, in October 2025. The organization says that around 40% of the one billion devices that run Windows 10 can't be upgraded to Windows 11, and will create an unnecessary e-waste problem. Also known as PIRG, this is the same industry group that has recently convinced Google to extend the warranty and support for older Chromebooks, citing similar arguments.
Windows 11 DNR: A feature named Discovery of Network-designated Resolvers (DNR) has landed in Windows 11 insider builds. The feature allows Windows 11 systems to automatically discover encrypted DNS servers in their local network, such as DoH or DoT servers.
Mastodon update: Mastodon admins have shipped a new update that adds support for Lists, allowing users better control over their home tabs.
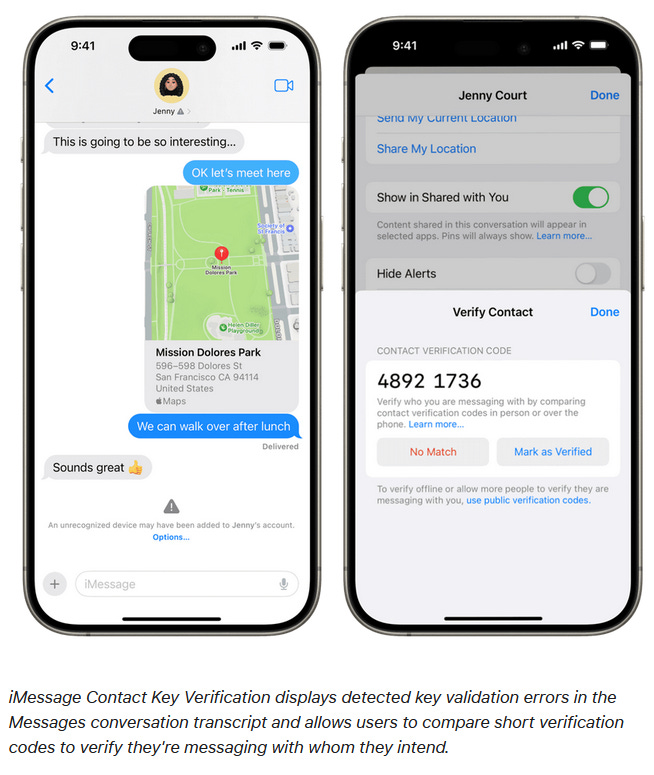
iMessage Contact Key Verification: Apple's security team has published a breakdown of how their new "iMessage Contact Key Verification" feature works. The feature is designed to show alerts inside encrypted iMessage conversations whenever a new device is added to a participant's account. The feature was recently added to dev builds for the company's three major operating systems.
"iMessage Contact Key Verification is available in the developer previews of iOS 17.2, macOS 14.2, and watchOS 10.2."
iOS Private WiFi Address bug: Apple users are advised to update to the latest version of iOS and iPadOS to fix a privacy feature that never worked. Named Private WiFi Address, the feature was added in 2020 and allows users to hide their MAC address on local WiFi networks. Two security researchers say the feature never actually worked, and users who enabled it have been leaking their MAC address for the past three years. [Additional coverage in ArsTechnica]
Government, politics, and policy
NCSC PDNS: The UK's NCSC has launched a secure DNS service named PDNS. The service is currently available for UK central and local government organizations, the NHS, emergency services, the Ministry of Defense, and schools.
UK Economic Crime and Corporate Transparency Bill: The UK Parliament has passed a new law last week that simplifies procedures for seizing crypto and fiat currency linked to money laundering and other fraudulent activities. Named the Economic Crime and Corporate Transparency Act, the law grants law enforcement the power to seize assets linked to criminal operations prior to obtaining a successful court conviction. The new law puts the UK on par with US law enforcement, allowing them to take a more proactive role in disrupting criminal operations.
CISA+HHS Toolkit: The US cybersecurity agency (CISA) and the country's health department (HHS) have released a joint cybersecurity toolkit for organizations in the healthcare sector.
NSA guidance: The NSA has published guidance [PDF] on how to evaluate commercially available embedded Field Programmable Gate Array (eFPGA) devices for security threats.
Defensive cyber exercises: Both the US and Australian militaries have held defensive cyber exercises this month.
Israel recruits spyware vendors in Hamas war: The Israeli government has allegedly hired two spyware companies to help track the location of hostages kidnapped by Hamas forces during the October 7 attack. The country's intelligence agency has asked NSO Group and Candiru to upgrade their spying capabilities in order to target the smartphones of kidnapped victims. According to a New York Times [non-paywall] report from earlier this month, Hamas members have used the smartphones of kidnapped Israelis to hijack online accounts and spread propaganda and threats of violence. More than 200 Israeli hostages are still captive in the Gaza Strip. [Additional coverage in Bloomberg/non-paywall]
Hamas Telegram ban: Instant messaging Telegram has blocked some Telegram accounts and channels that have been identified as belonging to Hamas members. [Additional coverage in CNN]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on the rise and evolution of vulnerability threat intel and how CISA KEV's new ransomware section will be a game changer.
Cybercrime and threat intel
RagnarLocker arrests: The two RagnarLocker suspects that were detained in Spain earlier this month were Alicante residents. Five suspects were detained in total, with the gang leader's being detained in Paris, France, and two other arrests in Latvia.
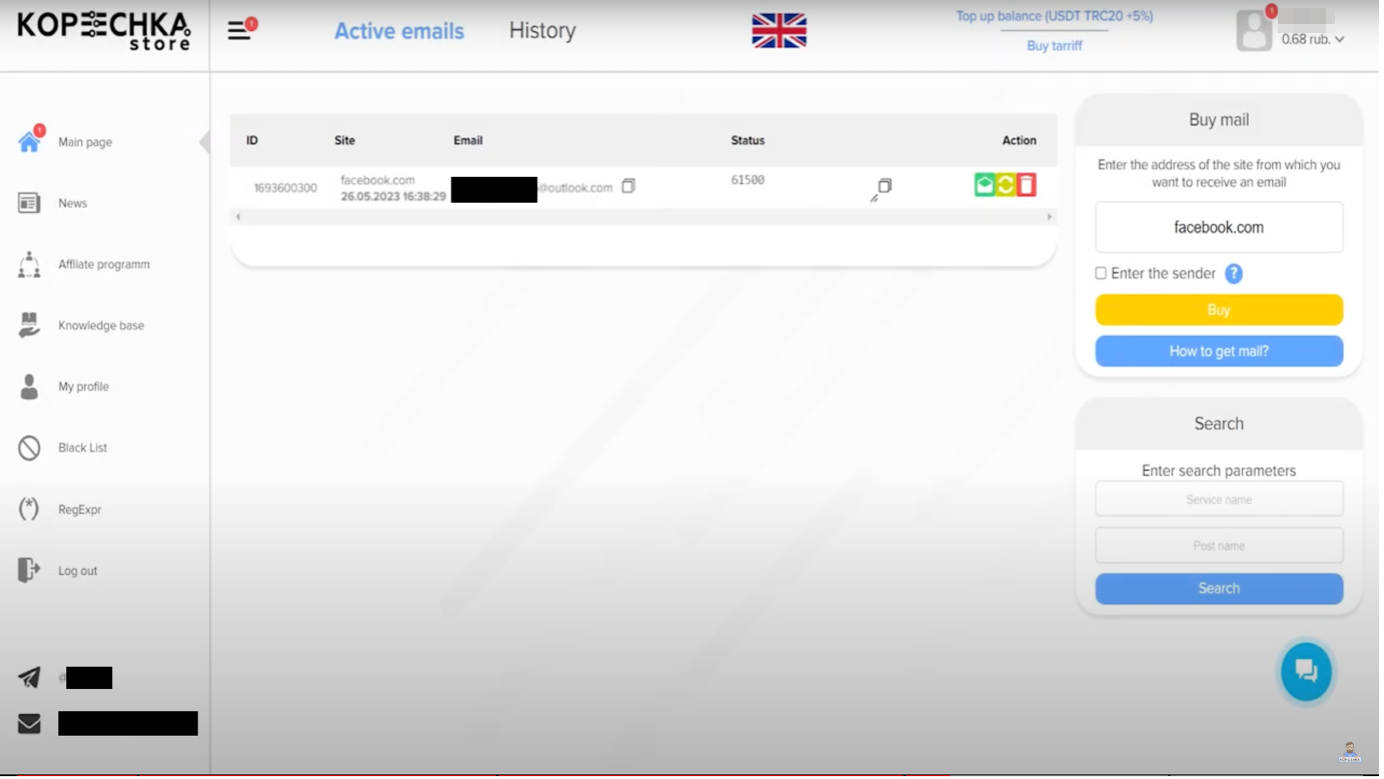
Kopeechka: Cybercrime groups are using a service named Kopeechka ("penny" in Russian) to create accounts in bulk on almost all of the internet's top platforms. Launched in 2019, the service allows threat actors to bypass CAPTCHA, email, and SMS verification systems and create thousands of accounts to be used for spam operations. Kopeechka supports all the main platforms, such as Facebook, Instagram, TikTok, Twitter, LinkedIn, Telegram, Discord, and Reddit. It can also target smaller platforms like Mastodon, Roblox, and Kick. Its API and scripting capabilities also allow threat actors to port its capabilities and target almost any online service.
New npm malware: Four malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Celebrity spam: Ryan Gosling, Emily Blunt, and Jennifer Lopez have been this year's Top 3 most (ab)used celebrity names in phishing and spam campaigns, per McAfee.
Armenian campaign: CyberHUB has published an analysis of a malware campaign targeting Armenian users.
Jarjets ransomware: Broadcom's Symantec has seen two new ransomware strains named Jarjets and CATAKA being used in the wild. Not that many details are available about them so far.
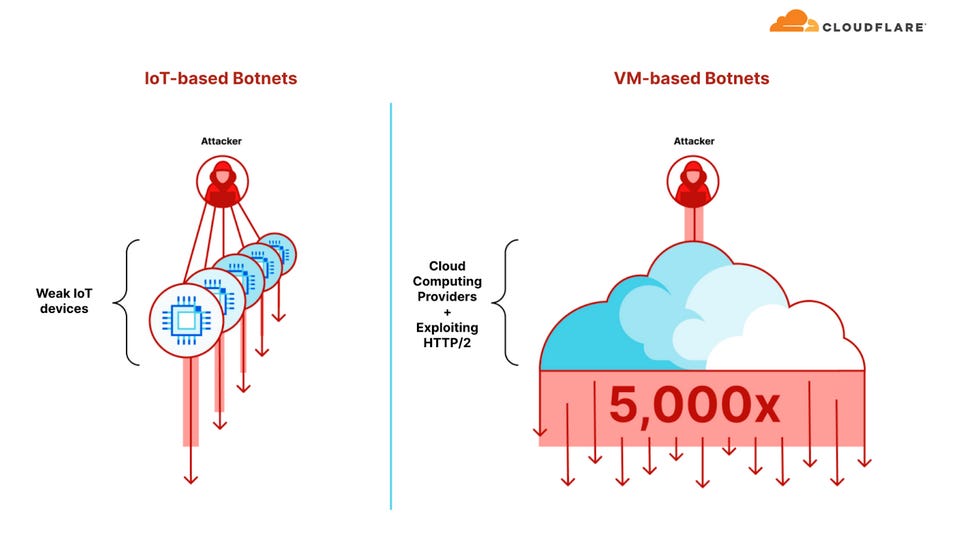
VM-based botnets: In its Q3 threat report, internet infrastructure company Cloudflare says that the new HTTP/2 Rapid Reset technique is allowing DDoS botnets to become more efficient when running from virtual machines hosted on cloud infrastructure rather than using compromised IoT devices. Cloudflare says it is seeing VM cloud botnets generate 5,000 times more DDoS power than classic IoT botnets.
Malware technical reports
AvosLocker: Zscaler researchers have published a retrospective on the AvosLocker ransomware, a RaaS platform that operated between July 2021 and May 2023. The retrospective comes after CISA and the FBI updated their security advisory on the gang. It's unclear if the group returned with new attacks.
GHOSTPULSE: Elastic's security team has discovered a loader named GHOSTPULSE that is currently being used in campaigns leveraging compromised websites, SEO techniques, and malvertising.
Remcos RAT: Embee researchers have looked at the downloader component of the Remcos RAT.
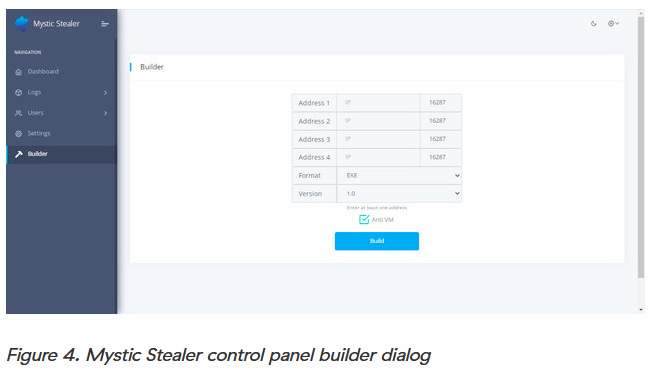
Mystic Stealer: Zscaler researchers have published a new deep dive into Mystic Stealer, an infostealer that launched earlier this year in April. Previous reports on this threat are also available via CyFirma, InQuest, OALABS, and Zscaler (its first analysis).
Sponsor Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
SideCopy: Pakistan-based APT group SideCopy has adopted the recent WinRAR zero-day (CVE-2023-38831) in operations targeting India's Defense Ministry.
DoubleAlienRat: Chinese security firm NSFOCUS has discovered a new APT group named DoubleAlienRat that is currently targeting Chinese organizations. The company says the group possesses a high level of technical skills and comprehensive hacking techniques. The group also focuses on stealth by actively covering its intrusions. NSFOCUS believes the group operates out of an Asian country and specializes in attacking China.
North Korean mobile op: South Korea's National Intelligence Service has put out a warning that North Korean hackers have used a clone of a popular South Korean shopping app to infect South Koreans with malware. [Additional coverage in Newsis]
Lazarus PyPI supply-chain attack: Security firm HAWKEYE says evidence is mounting to suggest that the Lazarus North Korean hacking group is behind the VMConnect campaign that planted malicious packages on the PyPI portal. Per HAWKEYE, the number of malicious packages in this campaign has now reached 24.
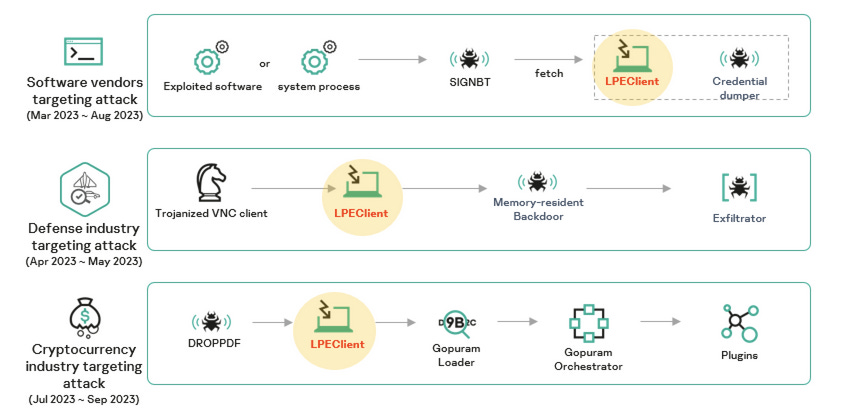
Lazarus 2023 campaigns: The Lazarus North Korean cyber-espionage group has breached a software vendor on multiple occasions throughout 2023. Russian security firm Kaspersky has not named the vendor but said the campaign lasted from March to August 2023. The company says Lazarus operators sought to maintain access to the vendor's network and deploy malware to its customers as part of a software supply chain attack. The campaign is one of three major operations carried out by Lazarus this year where the final payload was the LPEClient malware. The other two targeted defense contractors and the cryptocurrency industry.
Vulnerabilities, security research, and bug bounty
HackerOne milestone: Bug bounty platform says it surpassed a major milestone last week when it went over the $300 million mark in bug bounties paid to security researchers.
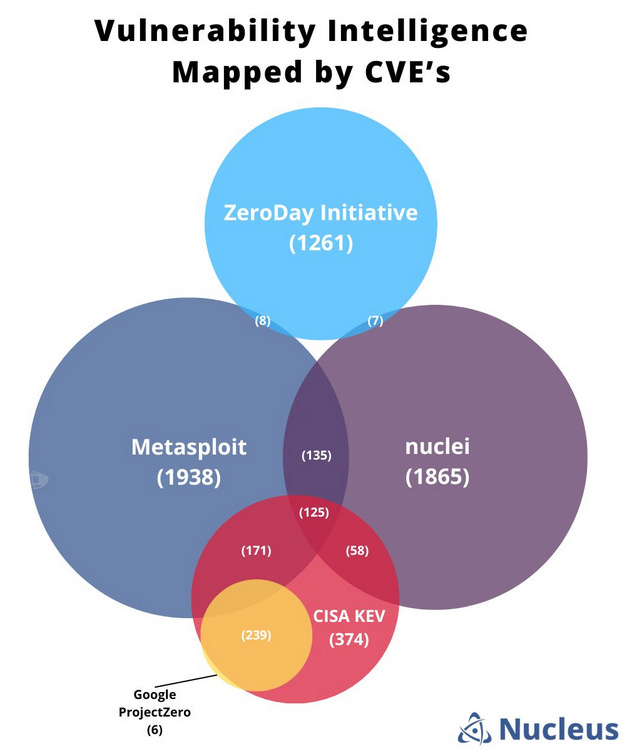
Vulnerability intelligence sources: This week's sponsor, Nucleus Security, has taken a look at the top vulnerability intelligence sources and how they overlap with each other. More in Patrick Garrity's LinkedIn post here.
Mirth Connect vulnerability: Security firm Horizon3 has published a write-up on CVE-2023-43208, a remote code execution bug they found in Mirth Connect, an open-source healthcare data integration platform. The vulnerability is a patch bypass for an older RCE tracked as CVE-2023-37679. The bug was patched two weeks ago in v4.4.1. More than 2,200 such systems are currently connected to the internet.
Unpatched WP plugin bug: NinTechNet researchers warn about a major vulnerability in the Deeper Comments WordPress plugin that has not been patched and allows full website takeover.
XORtigate: BishopFox has published a technical write-up on a Fortinet bug known as XORtigate, or CVE-2023-27997.
Lenovo LPE: SpecterOps has published an analysis of CVE-2023–4632, a local privilege escalation bug in the Lenovo updater. Lenovo patched the bug earlier this month.
VMWare security update: Enterprise software giant VMWare has published two security advisories to fix two sets of issues in its vCenter Server and Tools applications. The worst of the two is the vCenter update, which fixes a 9.8/10-rated memory issue that can lead to remote code execution attacks (CVE-2023-34048). According to LeakIX, more than 1,100 VMWare vCenter servers are exposed online in a vulnerable configuration.
Major Ubiquiti vulnerability: Ubiquiti has released a security update last week to patch a major vulnerability in UniFi, a software backend for controlling the company's gateways, switches, and wireless access points. Tracked as CVE-2023-41721, the vulnerability allows threat actors to access device configuration data and has received a severity rating of 10/10. Ubiquiti devices that have "automatic updates" enabled have already been patched. Those that do not will need to be updated as soon as possible.

Infosec industry
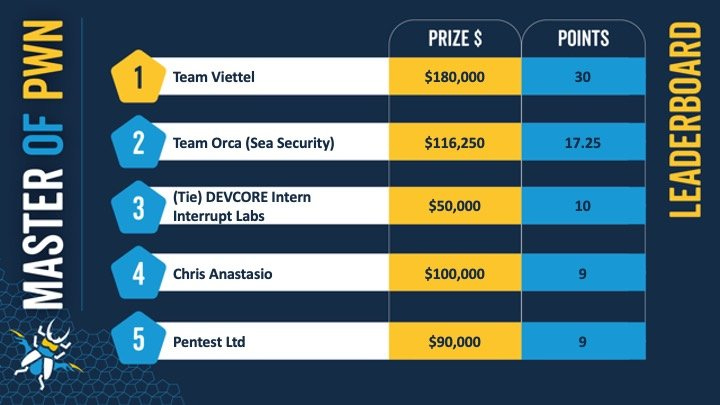
Pwn2Own Toronto 2023: The 2023 edition of the Pwn2Own Toronto hacking contest has come to an end. The contest win went to Team Viettel from Vietnam, with 30 points and $180,000 in prize money. The Toronto (fall) edition of Pwn2Own focuses on hacking smartphones and IoT devices. Participants won more than $1 million in prize money for 58 successful exploits. Devices hacked at this year's edition included the Samsung Galaxy S23 and Xiami 13 phones, HP and Lexmark printers, Wyze cams, TP-Link routers, QNAP and Synology NAS devices, and others.
BSides Canberra videos: Talks from the BSides Canberra 2023 security conference, which took place at the end of September, are available on YouTube.
CISA re-releases LME: CISA has released a new version of Logging Made Easy, a toolkit that enhances log management on Windows devices. The tool was originally developed by the UK's NCSC agency in the late 2010s and retired in March this year. CISA picked up the tool and re-wrote it to cover recent Windows versions and logging capabilities. The tool is available for download via CISA's official GitHub account (here).
Tool update—Nuclei: The Nuclei vulnerability scanner has now reached v3.
New tool—HAR File Sanitizer: Cloudflare has open-sourced a tool named HAR File Sanitizer that can remove authentication cookie files from HTTP Archive (HAR) files produced by browsers and typically used for tech support requests. The company created the tool after its own cookies were stolen from inside a HAR file it sent to identity provider Okta.
New tool—Archive Pwn: Security firm Pentragrid has open-sourced a tool named Archive Pwn that can be used to create boobytrapped archive files, useful for testing vulnerabilities and exploits.
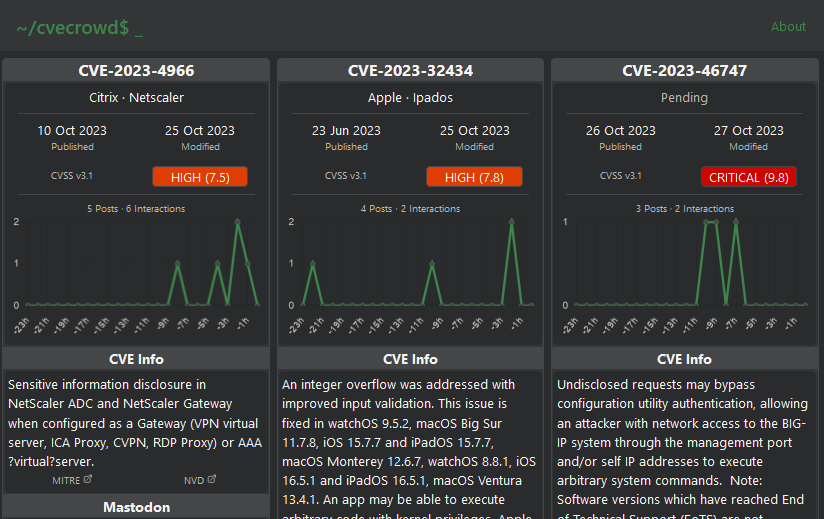
New tool—CVECrowd: A security researcher named Konstantin has launched a website named CVECrowd that shows what CVEs are currently popular and discussed on Mastodon.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss "spooky effects," aka when agencies play silly buggers with target computers.




