Risky Biz News: Cisco IOS XE hackers are hiding their tracks as patches come out
In other news: Okta hacked again; RagnarLocker ransomware boss arrested in Paris; and a new botnet targets C-level execs with slow-and-low brute-force attacks.
This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Over the past three days—since our last newsletter edition—the situation around the latest zero-day attacks targeting Cisco IOS XE devices has drastically changed, and we feel the need to cover it in our featured section and provide a short summary of what has been going on.
Although these attacks have been taking place since at least September 28, news of this campaign came out last Monday, on October 16, when Cisco revealed the existence of a zero-day tracked as CVE-2023-20198 in the web administration panel of its IOS XE operating system.
The zero-day allowed threat actors to create an admin account with the highest level of privileges on devices that had their WebUI panel exposed on the internet.
The investigation that continued throughout last week revealed the presence of a second zero-day that the attackers to use the admin account they created to inject commands into the IOS XE filesystem that would execute with root privileges.
Cisco said the exploit chain was being used to inject a Lua-based backdoor on devices across the world.
The company initially thought the second zero-day was a 2021 fixed bug tracked as CVE-2021-1435, but in a surprising update on late Friday, Cisco said the attackers were actually using a new zero-day altogether, which they are now tracking as CVE-2023-20273.
Nevertheless, Cisco and CISA both confirmed that CVE-2021-1435 was also being exploited in the wild but in a different campaign and by another threat actor.
But that's not the only thing that happened over the past weekend. The most interesting thing is that the Lua backdoor that was placed on all the hacked Cisco IOS XE devices since late September started disappearing.
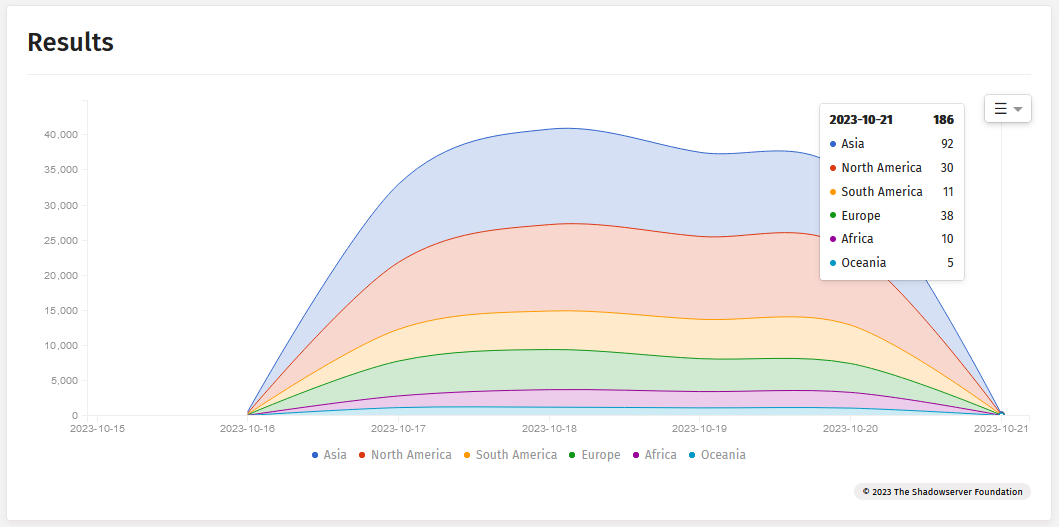
Estimates from Censys and Shadowserver put the number of hacked devices at around 42,000 IOS XE routers and switches. That number remained steady until this weekend when it suddenly dropped to around 500-1,000.
Several theories exist as to what happened, ranging from law enforcement intervention (FBI doing its thing again) to a white-hat cleaning infected systems and even Cisco itself cleaning customer devices.
However, it is very likely that this action was performed by the threat actor itself. The Lua backdoor was not a particularly strong persistence system, since it could be removed with a device reboot, and its public visibility was attracting too much attention to the attacker's operations.
As several security researchers have pointed out, the removal of the Lua backdoor may have also been accompanied by instructions that may have compromised devices in other ways and in the long run—similar to how Chinese hackers evaded Barracuda patches earlier this year and entrenched themselves so deep in the compromised appliances that Barracuda ended up telling customers to replace their gear to be safe.
In the meantime, Cisco delivered on a promise it made on Friday and released patches for both zero-days on Sunday.
Applying the latest patches will not be a one-and-done operation for your IT teams. It will be just the beginning of a sprawling security audit of what happened on that device over the last month.
As for who is behind this campaign, nobody in infosec has yet even tried to make an attribution.
The groups that are interested in Cisco IOS XE gear include almost everyone, from hacktivists to APTs and from initial access brokers to proxy botnet operators.
Attribution would require looking at artifacts from a Cisco IOS XE device, and the people who have looked at that kind of stuff are still staying silent.
If there's one good thing to take away from this, it's that Cisco's own security teams discovered both zero-day while investigating a customer support ticket—unlike similar equipment vendors that either don't look or don't have security teams.
Unfortunately, the bad thing is that they discovered this zero-day exploit chain about the same time they discovered another zero-day—CVE-2023-20109. This suggests there's one or more threat actors specifically looking for bugs in Cisco IOS XE devices, and they appear to have been extremely successful.
Breaches, hacks, and security incidents
Okta breach: A threat actor has compromised the account of an Okta support staffer and accessed the data of some of the company's customers. The attacker had access to Okta's support network for more than two weeks, from October 2 to October 18. Okta says the intruder only stole HTTP archive files that the company requires customers to upload to their customer support portal for debugging purposes. Okta says it notified all customers whose data was accessed in the breach. Public victims known so far include Cloudflare and BeyondTrust, which first detected the breach and was the one that notified Okta.
Philippines security breach: A hacker claims to have gained access to multiple Filipino government websites and downloaded gigabytes of data. Named DiabloX Phantom, the hacker claims to have gained access to the sites due to weak admin passwords, such as "Admin123." He claims to be 19 years old and a former red-teamer who just wants to highlight the government's weak security practices. Known victims of his hacking spree include the websites for the Philippines House of Representatives, the national police's forensics database, the Philippine Statistics Authority, and the country's national health insurance corporation. The hacker released sample data as proof of his intrusions. [Additional coverage in SCMP]
Philadelphia email breach: Officials with the City of Philadelphia are investigating a potential security breach of the city's email server that may have taken place in late May. [Additional coverage in the Philadelphia Inquirer]
BGRS cyberattack: The Lockbit ransomware gang has hit the network of Brookfield Global Relocation Services, a company that helps the Canadian military move troops, materials, and facilities around the world. The company's website has been offline since late September for more than three weeks. The company told the Canadian government that the attackers gained access to the personal data of government personnel. [Additional coverage in CBC]
DCBOE hack: The District of Columbia Board of Elections has updated its data breach disclosure to confirm that hackers gained access to the District's entire voter roll information. The agency confirmed the breach after a hacker started selling the agency's data on an underground hacking forum.
ICC hack: The International Criminal Court says the security breach it suffered at the end of September was "a targeted and sophisticated attack with the objective of espionage." The organization did not reveal which state actor was behind the incident.
Jabber.ru MitM: The administrators of the Jabber.ru instant messaging service have discovered a Man-in-the-Middle attack that was intercepting encrypted TLS traffic going through its German servers. Admins say the active interception lasted for three months between July 18 and October 18 and was discovered when one of the attackers' certificates expired. Because the attack required cooperation from web hosting providers Hetzner and Linode, the Jabber.ru team believes the interception may have been a law enforcement operation.
"All jabber.ru and xmpp.ru communications between these dates should be assumed compromised. Given the nature of the interception, the attacker have been able to execute any action as if it is executed from the authorized account, without knowing the account password. This means that the attacker could download account's roster, lifetime unencrypted server-side message history, send new messages or alter them in real time."
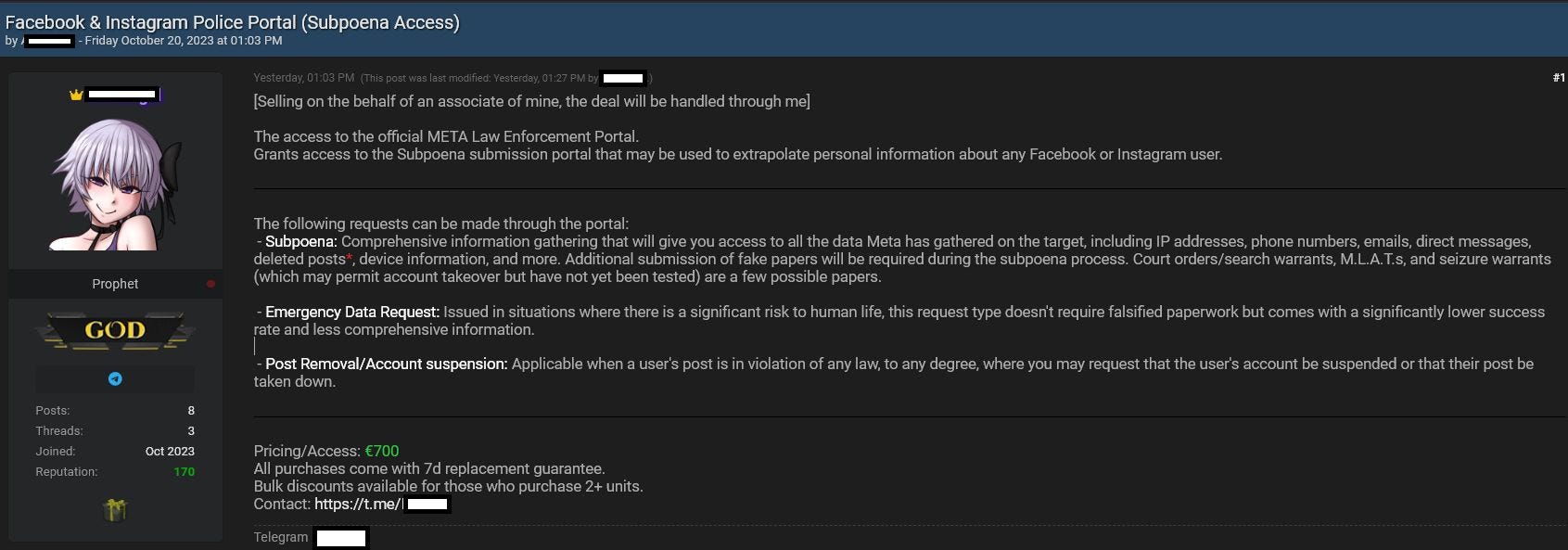
Potential Meta breach: A threat actor is claiming to sell access to Meta's law enforcement portal, where agents file legal requests for the company's services. Unconfirmed for now.
General tech and privacy
Clearview AI overturns ICO fine: American facial recognition company Clearview AI has won a court case against the UK's privacy watchdog and has overturned a £7.5 million fine the ICO imposed on the company in May 2022. Clearview made the case that it only sells its services to foreign governments and their law enforcement agencies. The court sided with the company, which argued the ICO does not have jurisdiction over the affairs of foreign governments. Personal note: This is quite an interesting decision since the original fine was for illegally collecting of UK citizens, not to whom Clearview sold it. The British court system still remains a mystery to us, mere mortals. [Additional coverage in the BBC]
Google Falcon: Google Cloud has announced Falcon, a new low-latency hardware-assisted transport layer designed to speed up Ethernet connections in data centers.
Microsoft Security Copilot: Microsoft Security Copilot is now in early access. This is a GPT4-like assistant to help security professionals with incident response investigations and other security tasks.
Discord moderation: Discord has changed its terms of service and will now give out warnings instead of permanent bans. If users break the rules too often, they'll have access cut off to some core Discord features, such as sending DMs, posting images, and more. [Additional coverage in Forbes]
Twitch opens up: Twitch is finally going to allow streamers to broadcast on multiple platforms at once. The move comes after the company has lost major streamers to new platforms, all of which allow concomitant multi-platform streaming. [Additional coverage in The Verge]
OpenSSL update: The OpenSSL project has added support for the Raw Public Keys protocol.
Twitter disinformation continues: A study has found that Twitter verified blue check users pushed 74% of the most viral dis/misinformation surrounding the Israel-Hamas conflict over the past week. [Additional coverage in AdWeek]
Government, politics, and policy
EU chat control legislation: The EU postponed the vote on its chat control legislation for the second time last week.
AD security guide: France's cybersecurity agency ANSSI has published a guide on securing Active Directory (AD) networks. The guide is only available in French for now.
StopRansomware guide: US cybersecurity agencies have published an update on their StopRansomware guide. The new update comes with new prevention tips for hardening SMB protocols, revised response steps, and added threat-hunting insights.
Crypto-mixers to be desginated money laundering tools: The US Treasury Department's Financial Crimes Enforcement Network (FinCEN) has proposed rules that would designate cryptocurrency-mixing services as money laundering tools. The new rules would allow US authorities to impose sanctions and seize funds more easily. Officials cited the use of such tools by groups like Hamas and North Korea.
US GOP drama: Rep. Andrew Garbarino (R-NY) told Cyberscoop that the lack of an elected House speaker is delaying US lawmakers from advancing crucial cybersecurity legislation.
TSA cybersecurity lagging behind: A DHS OIG report [PDF] has found that high-value asset systems operated by the Transportation Security Administration have serious cybersecurity deficiencies. [Additional coverage in Federal News Network]
Facial recognition coming to Login.gov: The US government is adding facial recognition technology to its Login.gov single sign-on service. The new tech is scheduled to roll out next year. Users who don't want their face scanned to access government services will have a second digital identity verification option available, but the government hasn't decided what it will be yet. [Additional coverage in NextGov]
Philippines Army warns against AI use: Philippine officials have ordered defense and military personnel to refrain from using AI tools due to security risks. The US Space Force imposed a similar ban earlier this month. [Additional coverage in the Associated Press]
Philippines Cyber Command: The Philippine government is recruiting cyber personnel for its own Cyber Command-like structure inside its military forces. [Additional coverage in The Diplomat]
Brazil's New Resistance group: The US State Department has published a report on Nova Resistência, a Brazilian quasi-paramilitary neo-fascist organization formed by a pro-Kremlin disinformation and propaganda network.
"In addition to Nova Resistência's overt propaganda and disinformation in support of Russia's war against Ukraine, the organization has been involved in efforts to mobilize Brazilians to fight on the side of Russia and its proxies in the Donbas region of eastern Ukraine."
Russia formally linked to African online disinformation: A WaPo article describes how an employee at an Israeli online influence company Percepto International infiltrated pro-Russian Facebook groups, became very active, and was invited to a meeting at the Russian embassy in Burkina Faso to establish a partnership and receive further training and help promote anti-West views across the region. It's an eye-opening story on how Russia uses its diplomatic missions as part of its online disinformation efforts. Five countries in Africa's Sahel region were toppled in Russian-supported coups. [Additional coverage in the Washington Post/non-paywall]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely CEO Travis McPeak about the modern DevOps ecosystem, how giving developers tools with security baked in keeps everyone safe and happy, and how that's easier than expecting your software engineers to become cybersecurity experts overnight.
Cybercrime and threat intel
RagnarLocker arrest: Europol officials have arrested a key member of the RagnarLocker ransomware group who was living in Paris, France. The arrest was announced after the gang's dark web leak site went offline last week. Five other suspects were interviewed in Spain and Latvia, and authorities seized servers in the Netherlands, Ukraine, Germany, and Sweden.
Ransomware suspects set free: A French judge has freed two Spanish nationals who have been accused of launching ransomware attacks against 26 French companies. Aged 26 and 28, the two suspects were detained in July of last year. French officials claimed the two used the Babuk ransomware to launch more than 200 attacks against companies all over the world. In a court hearing last week, lawyers for the two suspects argued there was reasonable doubt the two were behind the attacks. [Additional coverage in El Mundo/ h/t PogoWasRight]
Warning for plastic surgery patients: Cybercriminals are targeting plastic surgery offices and hospitals to steal data and extort patients. The FBI says the attacks use phishing and social engineering to gain access to target networks, from where attackers harvest data from electronic health systems. The stolen data is then used to send threats to victims via email, social media, or messaging apps.
Ducktail+DarkGate campaign: WithSecure says it's seeing the Ducktail Vietnamese cybercrime group employ the latest DarkGate Malware-as-a-Service to help its operations.
QNAP takes down brute-forcer: Taiwanese electronics vendor QNAP says it took down a server that was being used by a threat actor to launch brute-force attacks against its NAS devices, looking for accounts protected with weak passwords. The attack took place on October 14, and QNAP says it blocked it within seven hours via its NAS firewall feature. It also worked with Digital Ocean to have the attacker's server shut down.
New npm malware: Ten malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Mastodon abuse: Stanford's Internet Observatory analyzes Mastodon's moderation model and how it could be abused for online propaganda.
New RDGA technique: Infoblox looks at RDGA (Registered Domain Generation Algorithm), an evolution of the classic DGA. So far, Infoblox has seen a Chinese APT using this technique.
"The main difference between this traditional use of a DGA and an RDGA is right there in the name: they're registered. With a standard DGA, the algorithm is incorporated in the malware itself and only a small percentage of the domains created by the algorithm are actually registered. [...] An RDGA, on the other hand, is used by the actor2 to create domains that will all be registered."
ENISA Threat Landscape: The EU's cybersecurity agency has published its yearly threat landscape report. Some main conclusions include the significant rise of social engineering attacks, infostealers became the biggest malware threat, classic mobile malware declined, and law enforcement operations increased.
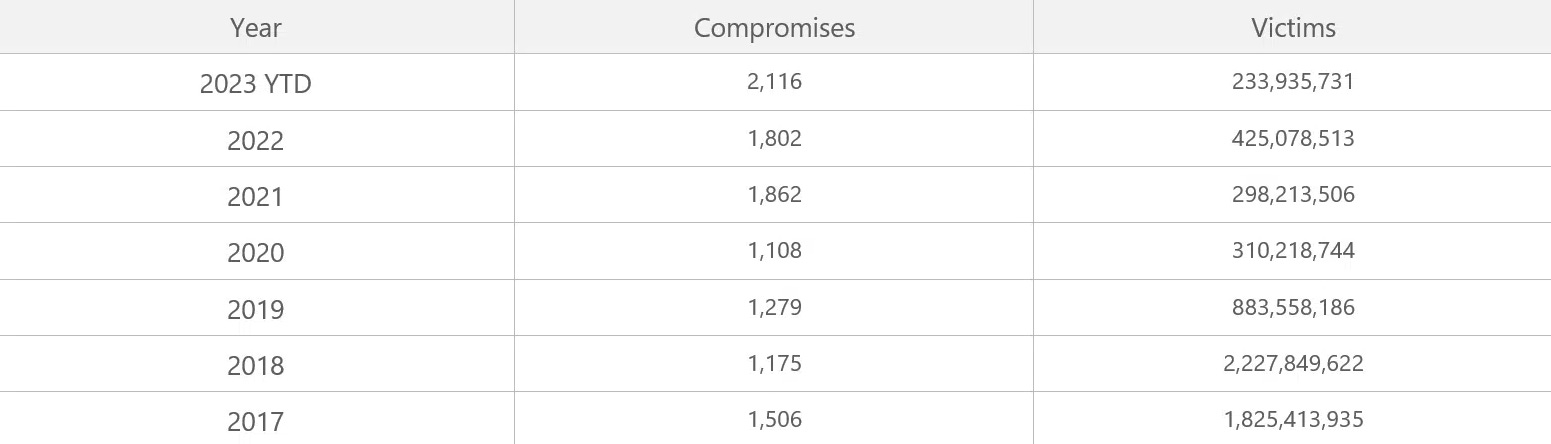
Data breach statistics: The number of publicly disclosed data breaches will reach an all-time high this year, with the numbers for Q3 2022 already passing the previous record. More than 2,100 data breaches have been disclosed this year, way above the 1,862 peak recorded in 2021. According to researchers from the ID Theft Center, the record year can be attributed to the MOVEit hack, with 1,300 data breaches filed this year being related to the incident.
Malware technical reports
Dark Angels ransomware: SentinelOne analyzes the new Dark Angels ransomware, first spotted in September 2023. The security firm says the ransomware uses the leaked Babuk ransomware code for attacks on Windows systems and an ESXi encrypter that resembles the one used by the RagnarLocker group. The group operates a dark web leak site known as Dunghill Leaks.
"ESXi lockers continue to prove successful for the ransomware groups who use them, yet the overall pool of unique Linux ransomware families remains narrow. We assess with high confidence that these two samples are related and that the Linux version of Dark Angels is a very lightly modified, more recent version of the analyzed RagnarLocker binary.
Given the lack of security software on ESXi hypervisors, consider enhanced network monitoring for unusual access to these systems, including internal system traffic. When possible, focus on large or abnormal data transfers off of the ESXi server as well as other file storage services within the network."
7777-Botnet targets C-level execs: A botnet of more than 16,000 infected IoT devices has been launching slow-paced brute-forcing attacks against Microsoft Azure infrastructure. The attacks exclusively target the accounts of C-level executives. Each account is only targeted with two or three brute-force attempts per week and always from a different IP address. Named the 7777-Botnet, security researchers believe the attacker is trying to avoid detection by carrying out attacks at an extremely slow pace. Victims identified so far include two companies from the US energy sector, a UK government contractor, a UK university, and several companies in France.
WatchDog: Anity researchers have published a breakdown of the WatchDog crypto-mining botnet.
IcedID: Walmart's security team looks at a recent IcedID campaign leveraging GitLab.
QuasarRAT: Uptycs researchers have published a report on the QuasarRAT and its DLL side-loading techniques, designed to drop, deploy, and execute malicious payloads without raising suspicions.
LummaStealer: VMware's Carbon Black security team looks at the LummaStealer Malware-as-a-Service (MaaS).
ExelaStealer: Fortinet researchers have analyzed ExelaStealer, a new infostealer that is currently being sold on underground dark web hacking forums.
Sponsor Demo
Listen to Resourcely CEO Travis McPeak talk with Risky Business Snake Oilers host Patrick Gray about the company's automagic Terraform cloud-provisioning technology.

APTs and cyber-espionage
CrimsonRAT: Security researchers have published an analysis of CrimsonRAT, a malware strain used by Pakistani cyber-espionage group APT36.
Vulnerabilities, security research, and bug bounty
ListServ vulnerabilities: Security firm Praetorian has identified several vulnerabilities in mailing list management app ListServ. The vulnerabilities can be used to compromise admin accounts and achieve remote code execution. All bugs remain unpatched after the vendor did not reply to Praetorian's vulnerability disclosure.
SonicWall hardcoded password: Security researchers at watchTowr Labs have found eight vulnerabilities in SonicWall SSL VPNs. All issues have now been fixed.
VMware security updates: VMware has released security updates for its Aria and Fusion products. Horizon3 has a write-up for one of the bugs here.
SolarWinds security updates: SolarWinds has released security updates for its Access Rights Management platform. The patches fix multiple bugs, including three 9.8/10 RCEs [1, 2, 3].
Amazon's passkeys: Identity provider Corbado is not a fan of Amazon's recent passkey implementation.
Three years to fix: The Harvest time-tracking app team took three years to fix a bug in their Azure app that was leaking its customers' OAuth tokens.
Zenbleed PoC: A PoC for the Zenbleed vulnerability that works in the Chrome browser has been released. The bug, disclosed in July, allows an attacker to retrieve secret material from AMD Zen 2 processors. Don't panic, though!
Atlassian zero-day PoC: A PoC for the recent Atlassian Confluence zero-day (CVE-2023-22515) has been added to the Metasploit framework after several exploit developers published PoCs online in the weeks prior. This is the Confluence 10/10 zero-day that was being exploited by a suspected Chinese cyber-espionage group.
HTTP2 Rapid Reset attack: PortSwigger researchers have taken the concept behind the HTTP2 Rapid Reset attack that was being used to launch DDoS attacks and applied it in a manner to perform remote race condition attacks with a single TCP packet. It's actually pretty nifty stuff!
Infosec industry
New tools—GraphRunner: Black Hills Information Security has open-sourced a tool named GraphRunner, a post-exploitation toolset for interacting with the Microsoft Graph API.
"It provides various tools for performing reconnaissance, persistence, and pillaging of data from a Microsoft Entra ID (Azure AD) account."
New tool—FalconHound: Security firm FalconForce has open-sourced FalconHound, a blue team multi-tool.
"It allows you to utilize and enhance the power of BloodHound in a more automated fashion. It is designed to be used in conjunction with a SIEM or other log aggregation tool."
New tool—Delegate: Bell's Clément Cruchet has open-sourced Delegate, a tool to perform GCP domain-wide delegation abuse and access Workspace users' Drive and Gmail data from a compromised GCP service account.
New tool—WolfPack: RoseSecurity Research has open-sourced WolfPack, a tool that uses Terraform and Packer to streamline the deployment of red team redirectors on a large scale.
Chrome extension mapping: Security researcher Hexacorn has published a list that maps Chrome extension IDs with their real names. It is a useful file to have if you're conducting security research on malicious extensions. The file has more than 386,000 rows.
Hack.lu 2023 videos: Some of the talks from the Hack.lu 2023 security conference, which took place last week, are available on this YouTube channel.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss how changing circumstances change the risk/reward balance and change whether effects operations are worthwhile.




