Risky Biz News: Chinese APT hacks subsidiaries, pivots to corporate headquarters
In other news: Google and Mozilla patch another Chrome & Firefox zero-day; Cisco patches its own zero-day; and new DarkRiver APT targets Russian defense sector.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Cybersecurity agencies from Japan and the US have issued a joint security advisory about a Chinese APT group that is hacking the overseas subsidiaries of US and Japanese companies and then pivoting to their corporate headquarters.
Known as BlackTech (Palmerworm, Temp.Overboard, Circuit Panda, and Radio Panda), the group targets internet-facing routers as their entry point into victim networks.
To maintain access, the group hot-patches the router firmware with a modified version that bypasses security features and contains a built-in SSH backdoor to maintain future access.
The backdoor functionality is enabled and disabled using custom TCP or UDP packets.
To hide their presence on the infected routers, the group also manipulates CLI operations to modify output and prevent the running of commands typically used for forensic analysis.
So far, BlackTech has been seen targeting only Cisco IOS-based routers.
In response to the joint advisory, Cisco says BlackTech did not exploit any vulnerabilities in its products but merely abused weak or stolen admin credentials.
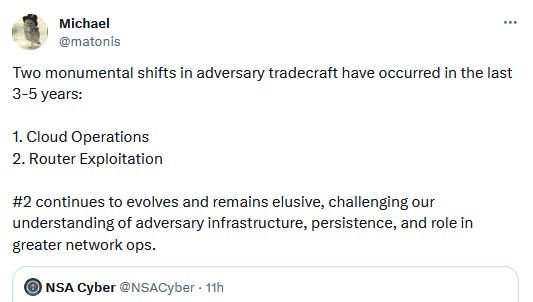
While we've seen APT groups tamper with firmware before, and Cisco has a huge market share across the world, officials were more worried in their joint advisory about the group's penchant for pivoting from subsidiaries to corporate headquarters overseas.
More from Rob Joyce, NSA Cybersecurity Director, and Mandiant researcher Michael Matonis.
"Cyber actors look for the easiest way into their targeted network, like a thief checking vehicles for unlocked doors. [...] Subsidiaries of multinational corporations are attractive targets for threat actors. The security of these subsidiaries' IT environments are sometimes overlooked, posing a significant risk for the critical systems of their international partners."
Breaches, hacks, and security incidents
Leonardo DDoS attack: Rostec says a massive DDoS attack has disrupted the operations of Leonardo, Russia's air booking system. The attack caused several hours-long delays for some flights across the country, as passengers couldn't board planes. [Additional coverage in Reuters]
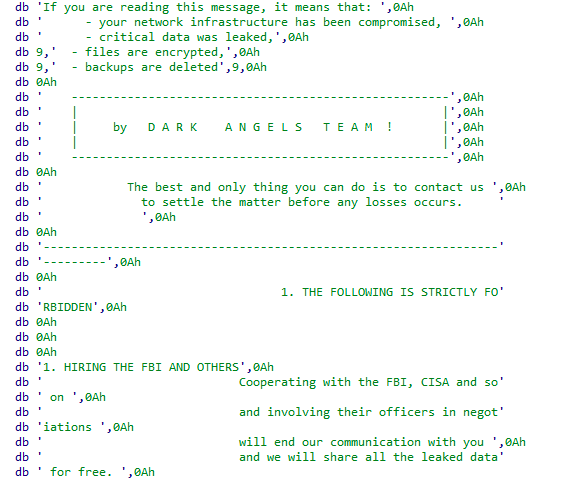
Johnson Controls ransomware incident: Building automation and HVAC systems from Johnson Controls are down after the company suffered a ransomware attack at the hands of the Dark Angels Team. In SEC documents, Johnson Controls says it is working with its insurers to restore systems and customer access to its automation platform. The company is the fourth-largest building automation and HVAC company in the world. [Additional coverage in BleepingComputer]
General tech and privacy
Google urges SMS EoL: Google's security team has encouraged tech companies and governments to end the use of SMS and move to newer texting technologies like RCS.
OpenSSL 1.x EoL: The 1.x branch of OpenSSL has now reached end-of-life with the final release of OpenSSL v1.1.1 earlier this month. The current stable is the 3.x branch.
ECH support on Chrome: Chrome 117, released earlier this month, supports Encrypted ClientHello (ECH) for fully encrypted TLS traffic.
Edge passwords bug: There's a bug in Edge that will convert all your passwords into a GUID. You can fix this by reinstalling and re-syncing your passwords.
Reddit enshitification continues: Reddit has removed the ability for its users to opt out of personalized ads.
Government, politics, and policy
CISA and the government shutdown: CISA expects to furlough almost 82% of its staff in the case of a government shutdown. [Additional coverage in FNN]
Western Hemisphere Cyber Conference: The US DHS is hosting the Western Hemisphere Cyber Conference, a cybersecurity summit with leaders from Latin America. The two-day event is taking place this week with representatives from more than two dozen countries. [Additional coverage in The Record]
ICO warning: The UK's privacy watchdog has warned organizations that handle the data of victims of domestic abuse to take care of how they store the information. The ICO says that since June 2022, it fined seven companies that exposed victim case and location data to alleged perpetrators. The ICO says most of the time, the breaches take place because of a lack of staff training and lack of proper procedures.
Russian censorship: At the direction of the Roskomnadzor, Yandex is now marking the websites of foreign web hosting providers as illegal in its search results.
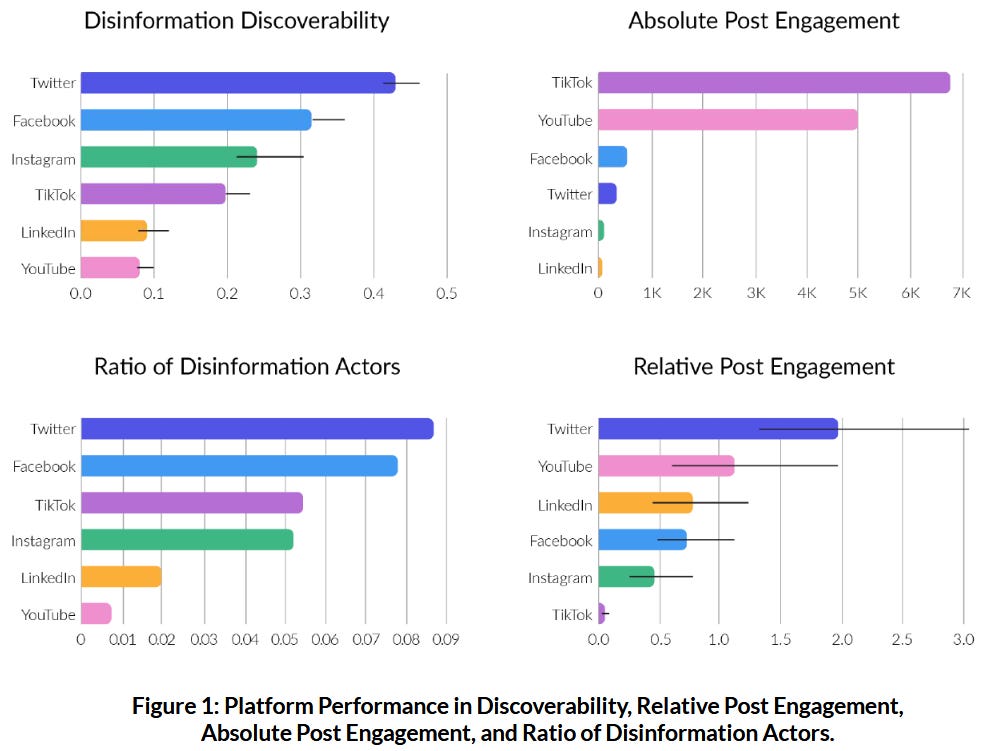
Twitter embraces propaganda: Twitter has disabled a feature that would have allowed users to report election misinformation. The feature was introduced in 2022 and is only present for EU users, where the DSA legislation forces Twitter to keep it up. Ever since Musk's acquisition, the platform has continuously removed or added features that favor bot networks and state propaganda operations. In the meantime, an EU study [PDF] found Twitter as the major hotspot for disinformation among the big six social networks. [Additional coverage in Reuters and the BBC]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Stairwell Principal Reverse Engineer Silas Cutler about Akira's recent server leak and attacker infrastructure.
Cybercrime and threat intel
Russian hacker couple detained: A young couple from Sankt Petersburg was detained in Italy last month under a Europol warrant issued by France. The couple is accused of hacking crimes. They are appealing their extradition to France, where they stand to face charges. [Additional coverage in TASS]
Snatch leak: The leak site of the Snatch ransomware group is leaking data about its backend and real-time users. The leak reveals the website is hosted in Russia, most of its visitors are also from Russia, and that the Snatch group also engages in SERP/SEO poisoning to distribute malware [Additional coverage in KrebsOnSecurity]
ASMCrypt: Kaspersky says a threat actor is advertising on underground forums a new cryptor/loader named ASMCrypt.
RansomedVC: Resecurity looks at the history of the RansomedVC ransomware and data extortion gang, which has made quite a few headlines lately after their alleged intrusions at Sony and NTT Docomo.
ScamClub malvertising group: Security firm Confiant says it has worked with industry partners and has taken down the infrastructure of a threat actor named ScamClub. Active since 2018, the group has abused ad platforms to place malicious ads on reputable websites that redirect users to phishing pages, gift card scams, and giveaway scams. The group has employed multiple browser zero-days and is believed to have made an estimated $8.5 million in the first half of the year alone. Confiant has linked the group's operations to a Hong Kong company named WayTop International Advertising Limited.
USPS smishing campaign: DomainTools has published a report on a smishing campaign that targeted US Postal Service (USPS) customers.
Open directories stats: A Censys scan has found that more than 314,000 internet-connected devices are exposing open directories and their respective data.
Russian exposure: Rostelecom says it found more than 2,200 private source code repositories belonging to Russian companies that appear to have been accidentally exposed online.
Ransomware stats: Reports from NCC Group and Trend Micro have Lockbit as the year's most active ransomware operation.
FBI ransomware trends: The FBI is seeing a trend among threat actors where they deploy two or more ransomware strains to encrypt the same compromised victim. The agency says the majority of dual ransomware attacks occur within 48 hours of each other. The purpose of such attacks is to prevent victims from easily decrypting data using flaws in one of the ransomware strains. According to the FBI, threat actors that use this technique rely on ransomware strains such as AvosLocker, Diamond, Hive, Karakurt, LockBit, Quantum, and Royal. More in the FBI PIN [PDF].
Malicious npm/PyPI packages: DevSecOps company Phylum has discovered 46 malicious JavaScript and Python libraries—41 on npm and 5 on PyPI—designed to steal Kubernetes configuration files and SSH keys from infected systems. The campaign is related to a cluster of activity Sonatype spotted last week.
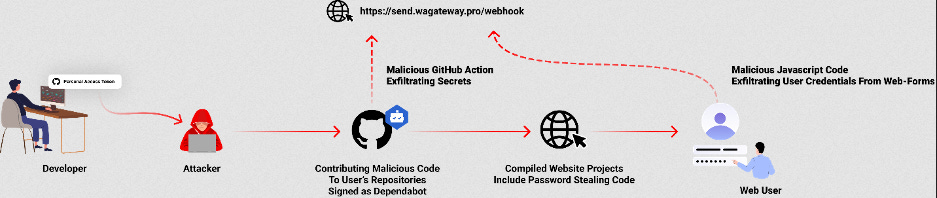
Dependabot attacks: A threat actor is contributing malicious code to GitHub projects and disguising their commits as coming from the platform's Dependabot service. Spotted by Checmarx, the campaign has been taking place since July and has impacted hundreds of repositories. If project owners approve the commits, the malicious code will collect the victim project's secrets and secretly insert an infostealer in the project code.
Malware technical reports
Brute Ratel: CyberGeeks has a two-part deep dive into Brute Ratel C4 payloads.
FantasyMW: Something we missed from July is this analysis of FantasyMW, a new banking trojan popular with Brazilian cybercrime gangs.
Megazord: Chinese security firm Rising analyzes Megazord, the latest version of the Akira ransomware.
Sponsor Demo Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
APT-C-23: Qihoo 360 has a report on the recent operations of APT-C-23, a Palestinian APT also known as Twin-tailed Scorpion, Arid Viper, Micropsia, Frozen Cell, and Desert Falcon. The report focuses on the group's use of the Micropsia backdoor and Arid Gopher trojan in attacks across the Middle East.
DarkRiver: A new APT group named DarkRiver is targeting companies in the Russian defense sector. The group is extremely focused on maintaining stealth, is very selective with its targets, and launches one-off attacks from clean infrastructure. The group's main tool is MataDoor, a highly modular and never-before-seen backdoor. So far, Russian security firm Positive Technologies has linked DarkRiver to intrusions at four Russian defense companies.
Budworm: Chinese APT group Budworm (aka LuckyMouse, Emissary Panda, APT27) has conducted two operations in August this year that have targeted a Middle Eastern telecommunications provider and an Asian government. According to Symantec, the attacks involved a previously unseen variant of its SysUpdate backdoor, a tool exclusively used by the group.
Taiwan disinformation: China is taking a page out of Russia's disinfo book and has flooded Taiwan with rumors that the US is making bioweapons at biolabs across Taiwan. The entire thing is an effort to flood Taiwan with anti-US disinformation ahead of the country's elections. An unrelated WSJ report claims China has invested billions in anti-US and pro-PRC disinformation efforts. [Additional coverage in The Economist/non-paywall and the WSJ/non-paywall]
Vulnerabilities, security research, and bug bounty
Russian exploit broker goes big: Russian exploit broker Operation Zero is offering to pay up to $20 million for zero-day exploit chains in iPhone and Android devices. The company's offer comes two months after it raised payouts for the same exploit chains from $500,000 to $2.5 million. In an interview with TechCrunch, the company says the price increase is a reflection of the current zero-day market. It also said it only sells its exploits to non-NATO countries.
Chrome/Firefox zero-day: Both Google and Mozilla have released security updates to patch another common Chrome and Firefox zero-day. Tracked as CVE-2023-5217, the vulnerability resides in libvpx, a codec for processing VP8, VP9, and AV1 video files in both browsers. Google credited one of its own researchers—Clément Lecigne of Google's Threat Analysis Group—for discovering the zero-day's exploitation. The company says it spotted the attacks on Monday and released a security update two days later, on Wednesday. It didn't provide any details about the attacks.
Cisco zero-day: Cisco has patched a zero-day vulnerability (CVE-2023-20109) in the GET VPN feature of the company's IOS and IOS XE operating systems. Cisco says the vulnerability was exploited in the wild to take over vulnerable routers and switches. The zero-day was discovered by Cisco's own security team and is one of the 14 security updates the company has released this week. The updates also include a patch marked critical for Cisco Catalyst WAN switches that fixes an authentication bypass, a configuration rollback, and other similarly bad bugs.
Apache NiFi exploitation: Threat actors are exploiting a vulnerability in Apache NiFi to hijack unpatched servers. The attacks are exploiting a vulnerability patched in June this year and tracked as CVE-2023-34468. Attacks are most likely exploiting proof-of-concept code posted online.
KEV update: CISA has updated its KEV database with one new vulnerability that is currently being actively exploited. The vulnerability is tracked as CVE-2018-14667, a bug in the Red Hat JBoss RichFaces Framework.
WebP zero-day analysis: HP Wolf Security and Huntress Labs have an analysis of the recent WebP zero-day (CVE-2023-4863) that has been used by the NSO Group to deploy its Pegasus spyware via the Chrome browser.
Windows Server bug analysis: Akamai has a write-up on CVE-2023-24898, a DoS bug in Windows Server's SMB-over-QUIC protocol, patched earlier this year in May.
Friend.tech vulnerabilities: Check Point researchers have found several vulnerabilities in the Friend.tech Web3 platform. If exploited, the vulnerabilities could have allowed attackers control over the platform's database, access to the chat room conversations, modify user ranks and points, and granted access to shared files.
LibreOffice security update: LibreOffice has called on its users to install a security update to fix a zero-day in the Libwebp library tracked as CVE 2023-4863.
TeamCity PoC: A proof-of-concept exploit has been posted for the recent JetBrains TeamCity auth bypass tracked as CVE-2023-42793. [h/t Simon Tsui]
Apple security updates: Apple has released security updates for macOS, iOS, watchOS, and Safari.
Manifest Confusion in PyPI: Manifest confusion attacks also work on PyPI, not just npm. A manifest confusion attack is when threat actors can create clean manifest files but upload malicious versions of their package on PyPI/npm. Because some package management tools only read the manifest file but don't look at the actual library code, threat actors can sneak malicious packages onto official repositories.
Marvin attack: A security researcher with Red Hat's Czechia division has discovered a new variation of the Bleichenbacher 1998 timing attack that can be used to decrypt RSA communications. Named Marvin, the attack works against many modern implementations of the RSA algorithm. Affected projects include OpenSSL, GnuTLS, M2Crypto, and the Mozilla NSS. This is the second time that researchers have found that the old Bleichenbacher attack was not patched properly after they also found the ROBOT attack back in 2018.
"In this paper we show that Bleichenbacher-style attacks on RSA decryption are not only still possible, but also that vulnerable implementations are common. We have successfully attacked multiple implementations using only timing of decryption operation and shown that many others are vulnerable."
GPU.zip attack: A team of academics has discovered a new side-channel attack that can expose visual data that's being processed inside modern GPUs. Named GPU.zip, the attack targets graphical data compression operations that take place inside graphic cards. GPUs from AMD, Apple, Arm, Intel, and Qualcomm are vulnerable. Only one NVIDIA GPU was found to be affected by GPU.zip. Despite disclosing their attack to GPU makers in March this year, vendors have not released any patches.
"For example, using GPU.zip, a malicious webpage can leak pixels from another webpage in the latest version of Google Chrome, violating the browser security model."
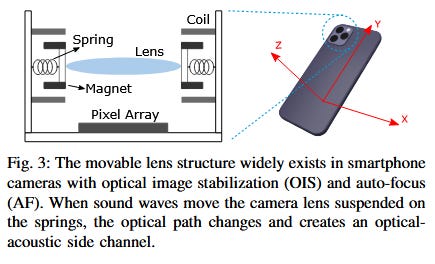
Side Eye: A team of academics from four US universities has developed a technique called Side Eye that can extract audio from static photos or silent videos. The technique targets the image stabilization technology included with cameras on all modern smartphones. It analyzes how camera lenses adjust to movements caused by sound waves and extracts that information from the recorded photo or video to reproduce the original sound. The audio reconstruction accuracy of the Side Eye technique varies from 80% to 99% based on the amount and complexity of the sound that is reconstructed. Researchers say Side Eye currently doesn't work with speech from human voices and was only tested with sound from powerful speakers. More in the paper, here.
Infosec industry
New tool—Chalk: DevSecOps company Crash Override has open-sourced a tool named Chalk that tracks metadata of various resources in order to track items from dev to prod environments.
DEFCON 31 videos: Talks from the DEFCON 31 security conference, which took place this August, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine how US and UK strategies to use cyber power differ but are in some ways mirror images of each other.




