Risky Biz News: Chinese APT hacks 30% of Cisco RV320/325 routers
In other news: Russia purges 600,000 gray SIM cards; HelloFresh fined for spamming; and cybercriminals detained in Belarus, Russia, and Ukraine.
This newsletter is brought to you by Panther, the scalable detection-as-code based SIEM. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
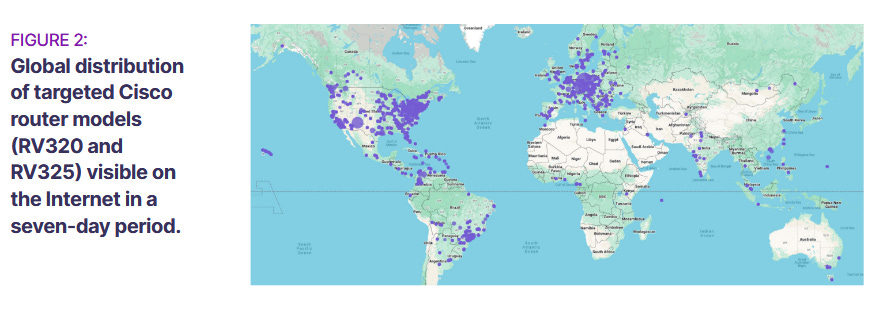
A Chinese state-sponsored espionage group has compromised and is currently controlling roughly 30% of all Cisco RV320 and Cisco RV325 WAN routers across the internet.
Active infections were spotted by SecurityScorecard's STRIKE Team over the past 37 days, between December 1, 2023, and January 7, 2024.
The routers are infected with and are part of KV, a botnet first spotted by internet infrastructure company Lumen last month. According to Lumen, the same botnet also consists of a large number of DrayTek Vigor routers, NETGEAR ProSAFE firewalls, and Axis security cameras.
The botnet is operated by Chinese APT Volt Typhoon. The group is the infosec industry's current Chinese cyber-threat-du-jour. First exposed in May of 2023, the group has been linked to a covert Chinese effort to breach US critical communications infrastructure.
Reporting citing government sources claimed the group was doing the equivalent of "war pre-position" by planting its seeds in critical US infrastructure that could be exploited in the case of a possible military conflict in the Pacific to hinder the US' response in the region.
The initial Microsoft report that exposed Volt Typhoon operations noted that the group was using compromised SOHO devices to proxy and hide its command and control infrastructure from infected hosts and network defenders. The subsequent Lumen report confirmed this particular detail, and Lumen provided both more details and IOCs about Volt Typhoon proxy network—aka the KV botnet.
SecurityScorecard says it used the Lumen findings and internet netflow data to determine targets of Volt Typhoon attacks by looking at which networks the infected Cisco devices communicated once they got infected.
The company says it identified 27 IP addresses hosting a total of 69 US, UK, Australian, and Indian government sites.
While the report basically confirms for the first time that Volt Typhoon has targeted other countries besides the US, it is, honestly, not that surprising.
Breaches, hacks, and security incidents
Framework data breach: Laptop maker Framework says the data of an unknown number of customers was stolen after a security breach at its external accounting provider.
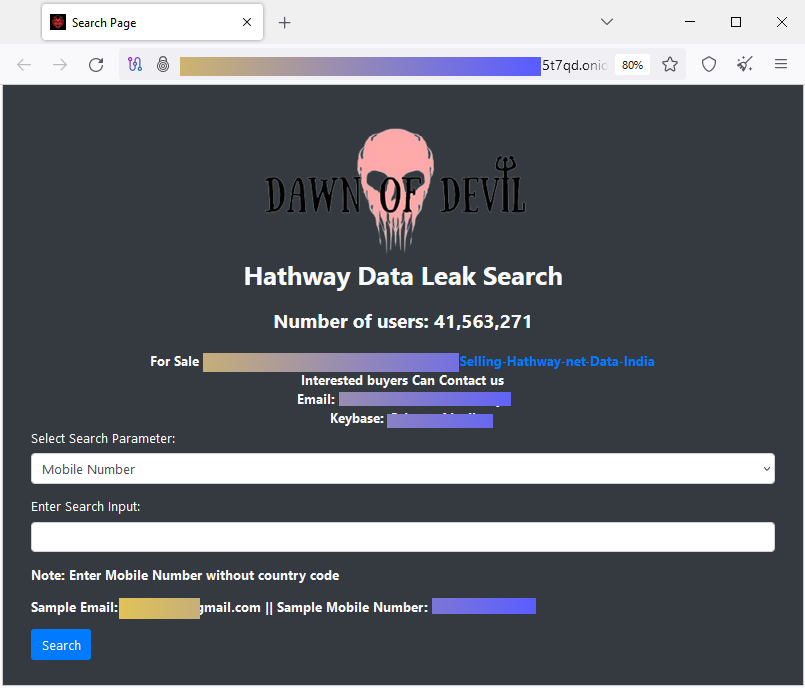
Hathway data leak: A hacker claims to have stolen the data of more than 41.5 million customers of Indian internet service provider Hathway. The hacker has leaked the data of 4.6 million users as proof of their claim. They have also set up a dark web portal where Hathway customers can check if they are affected by the breach. The ISP has yet to acknowledge the incident. [Additional coverage in RestorePrivacy]
General tech and privacy
HelloFresh fined for spamming: The UK's privacy watchdog has fined grocery delivery service HelloFresh £140,000 for sending marketing spam to UK customers. The ICO says HelloFresh sent more than 79 million spam emails and one million spam texts, even to customers who canceled their subscriptions.
eBay fined in 2019 harassment case: eBay has agreed to pay a $3 million fine to settle a DOJ lawsuit accusing the company of orchestrating a harassment and intimidation campaign. The company admitted that its security team harassed a US couple who ran a newsletter that negatively reviewed eBay products. eBay's former Senior Director of Safety and Security and six members of the company's security team posted negative comments on the newsletter's articles and a bunch of way way waaaaaaay more creepy stuff—see below.
"The campaign included sending anonymous and disturbing deliveries to the victims' home, including a book on surviving the death of a spouse, a bloody pig mask, a fetal pig and a funeral wreath and live insects; sending private Twitter messages and public tweets criticizing the newsletter’s content and threatening to visit the victims in Natick; and traveling to Natick to surveil the victims and install a GPS tracking device on their car. The harassment also featured Craigslist posts inviting the public for sexual encounters at the victims' home."
Users are less worth: A Raptive study estimates that the general value of a user's data is now worth 30% less after Google's migration from cookie-based tracking technology to its Privacy Sandbox system. [Additional coverage in Gizmodo]
YouTube sabotages ad block users (again): Instead of cleaning its scummy and scammy ad platform, YouTube is now slowing video buffers for users with an ad-blocker installed.
VMWare license drama: VMWare customers are reporting issues with renewing their licenses. [Additional coverage in BornCity]
"After the Broadcom takeover, absolute chaos reigns. Dealers have been terminated, orders via OEMs are sometimes impossible, and the end customer portal for license activation has been shut down."
Bitwarden adds passkeys: Password manager Bitwarden has added support for passkeys.
OpenSSH removes DSA: The OpenSSH project has announced plans to remove support for DSA keys. OpenSSH has disabled DSA keys by default since 2015 but has retained optional support. A full DSA removal is planned for January 2025.
ModSecurity moves to OWASP: Security firm Trustwave has transferred the stewardship of the ModSecurity open-source web application firewall (WAF) engine to the OWASP Foundation. The company is relinquishing control of the project after it was sold by SingTel to the MC2 Security Fund earlier this month. Trustwave has managed ModSecurity since 2010. The OWASP Foundation is a community-led project that manages several cybersecurity-focused initiatives and open-source projects.
Government, politics, and policy
FCC addresses domestic abuse: FCC Chairwoman Jessica Rosenworcel has sent letters to nine automakers and three mobile operators to seek their help in protecting victims of domestic abuse. The FCC Chair is reacting to multiple incidents of abusers tracking their victims using data from connected cars and mobile devices. The letter has asked companies to reveal what kind of data they collect from users and how domestic abuse survivors can be protected.
US federal cybersecurity education requirements: The Biden administration is working to remove the requirement for four-year degrees for some federal cybersecurity jobs. The upcoming change comes as part of the White House's efforts to boost hiring of cybersecurity professionals in federal agencies. Efforts to improve diversity in cybersecurity hiring are also underway, officials said. [Additional coverage in CyberScoop]
CDP analysis: The US Government and Accountability Office has looked at the activity of the Bureau of Cyberspace and Digital Policy (CDP), a bureau established by the State Department in April 2022 to tackle and promote cybersecurity policies at the foreign affairs and diplomacy level. The GAO gave the bureau a generally positive review. [Additional coverage in NextGov]
NFT scammer charged: US prosecutors have charged an active duty US Air Force cyber analyst for running an NFT scam named UndeadApes. [Additional coverage in Forbes]
Canada hires SecurityScorecard: The Canadian government has signed a partnership with security firm SecurityScorecard to provide security ratings for government and critical infrastructure resources as a way to assess their cybersecurity posture. [Additional coverage in the Vancouver Sun]
Swiss bulk collection scandal: Reporters from Swiss digital magazine Republik have published part one of a three-part series that covers how the Swiss intelligence services are abusing their powers for bulk data collection of all Swiss internet traffic, and not just cross-border communications. The report covers how Swiss intelligence services have ignored safeguards and protections and are now seeking to legalize their current practices and even expand their surveillance powers.
The Great Russian SIM Purge: Russian telecommunications watchdog Roskomnadzor has disabled more than 600,000 gray SIM cards. The agency says it sent notifications to more than 43 million SIM cards that did not have ownership details with mobile operators. SIM card owners had until the end of December to register their information with their operator. There are more than 351 million phone numbers registered in Russia. [Additional coverage in Vedomosti]
Sponsor section
In this Risky Business News sponsor interview Tom Uren talks to Ken Westin, Field CISO at Panther about how the rise of cloud and hybrid IT architectures requires a new type of SIEM.
Cybercrime and threat intel
Cryptominer arrested in Ukraine: Europol and Ukraine's Cyber Police detained a man from the city of Mykolaiv for running a crypto-mining botnet. The 29-year-old suspect used brute-force attacks to break into cloud providers and install crypto-mining malware. Officials say the suspect made over $2 million from the scheme.
Malware author detained in Belarus: Belarusian authorities have arrested a 35-year-old man from Voronovo on charges of developing malware. Authorities say the suspect sold the malware for $100 to customers in China and former Soviet states. The malware was described as a program designed to bypass protections and access account data on online sites.
Phisher sentenced in Russia: A Russian man from the city of Bryansk has been sentenced to one year in prison for launching phishing attacks against Russian government agencies. Officials say the suspect tried to collect login credentials for future attacks. He allegedly launched the attacks from his workplace. [Additional coverage in TASS]
Hacker detained in the Philippines: Philippine authorities have arrested a 47-year-old man on charges of allegedly targeting foreigners with illegal online activities. Named Edgar Silvano, the man previously served a prison sentence for hacking-related charges in the early 2000s, when he was also described as "Asia's best hacker." [Additional coverage in PhilStar, via DataBreaches.net]
Russian independent journalists targeted: A mysterious threat actor is targeting Russian independent journalists with spear-phishing attacks designed to collect their email login credentials. The attackers pose as fellow journalists from other Russian outlets and claim the target has stolen their article. Russian journalists working for Baza and the OCCRP confirmed to have been targeted. They warn fellow reporters to be extremely careful after several Kremlin critics lost their lives since Russia's invasion of Ukraine.
MSIX malware campaigns: Red Canary researchers have taken a look at all the recent malspam campaigns that are using MSIX files for the initial infection, a rising trend that has forced Microsoft to disable the ms-appinstaller (MSIX) protocol handler in Windows. However, as Red Canary points out, we're not out of the woods just yet.
"Microsoft chose to leave the protocol disabled by default, requiring a configuration change to enable it. As with previous encounters with MSIX files, this disabling solution does not fully eliminate the threat of MSIX files, it merely requires the malicious MSIX files to be intentionally downloaded to disk before execution."
Phishing attacks: Spotify and View Card users are currently being targeted with phishing emails.
New npm malware: Thirty-six malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Solana wallet drainers: ScamSniffer researchers have tracked a group that has stolen nearly $4.17 million in crypto assets from about 4,000 Solana users. The campaign used Twitter replies that lured users to phishing sites that drained their Solana funds and NFTs. The campaign is the latest in a recent trend where cybercrime groups are using phishing kits specialized in automatically draining compromised crypto-wallets. These kits are known as "wallet drainers."
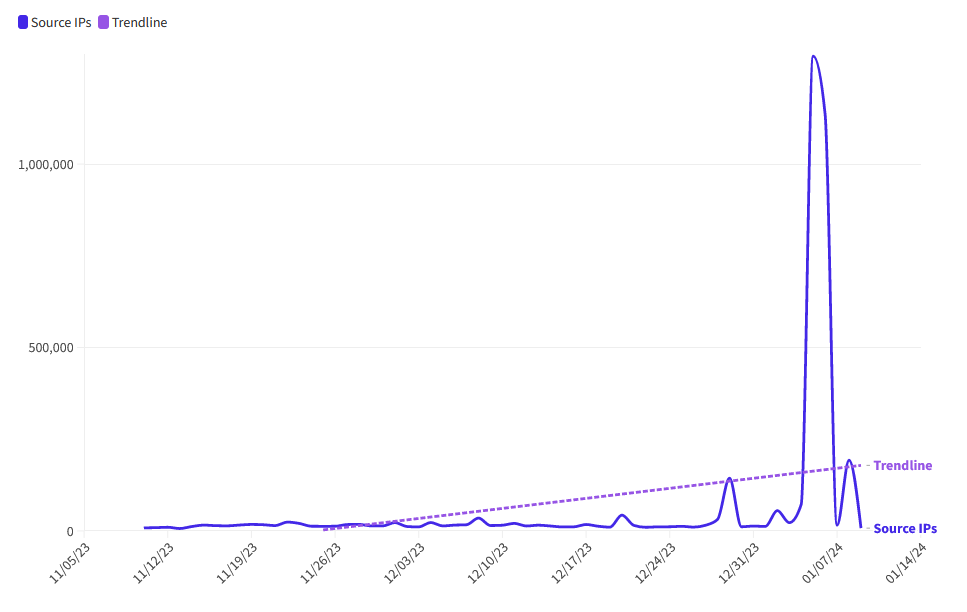
Growth in malicious botnets: Network security company Netscout has seen a spike in malicious botnets performing reconnaissance scanning operations. The company says it observed tens of thousands of devices performing malicious scans in December 2023. Peaks varied from 35,000 to 143,000 daily distinct scanning devices. The number is well above the 10,000 daily average the company saw last year.
Malware technical reports
Phemedrone Stealer: Trend Micro looks at Phemedrone Stealer, a new infostealer currently distributed in the wild with the help of a Windows SmartScreen bypass (CVE-2023-36025).
Shiz: Chinese security firm Tinder Security has published a report on Shiz, an infostealer and browser hijacker.
WorkersDevBackdoor: eSentire has analyzed a malvertising campaign from November 2023 that deployed the WorkersDevBackdoor on infected hosts.
Rimasuta: QiAnXin researchers have analyzed recent changes in Rimasuta, one of the many Mirai malware variants out there in the wild. This particular strain has been in the wild since June 2021 and is also known as Mirai_ptea.
Hunters International: Broadcom has published a summary analysis of Hunters International, a dual-extortion ransomware operation.
Sponsor Section
A short demo on how to use Panther's Detections-as-Code (DaC) platform for cryptominer investigations.
APTs, cyber-espionage, and info-ops
Volexity attacks: Mandiant has published its own report on the recently disclosed Ivanti zero-days. See Volexity's report here. Mandiant says it tracks the attacking group as UNC5221. Volexity's name for the group is UTA0178.
APT28's OceanMap: Malware researcher Niraj S. has published an analysis of OceanMap, a backdoor strain operated by the APT28 Russian cyber-espionage group.
Vulnerabilities, security research, and bug bounty
Juniper security updates: American networking equipment vendor Juniper has released three security updates for its switchers and firewall devices. The worst of the three is a pre-auth RCE (CVE-2024-21591) in the devices' web panel. Juniper has released firmware patches and has recommended that customers disable the J-Web interface until patches are applied. The vulnerability is very likely to be exploited in the wild. According to Censys, there are more than 11,500 Juniper devices with J-Web enabled on the internet.
GitLab security updates: Code management platform GitLab has released a security update to address five vulnerabilities. The most critical issue is a bug tracked as CVE-2023-7028 that can allow threat actors to take over accounts using the platform's password reset feature. User accounts with 2FA enabled are not vulnerable to this attack. The proof-of-concept is apparently ridiculously simple.
Apple keyboard fixes: Apple has fixed a hijack vulnerability in its Bluetooth keyboards discovered by Skysafe security researcher Marc Newlin last year. Android fixes were released in December.
PaperCut WebDAV RCE: Horizon3 has published a technical deep-dive into a PaperCut WebDAV vulnerability (CVE-2023-39143) it found last year and can be used for RCE scenarios. The vulnerability was patched last July.
NextGen Mirth Connect RCE: The same Horizon3 also published a technical deep-dive into a pre-auth RCE (CVE-2023-43208) it found in NextGen Mirth Connect, an open-source healthcare data integration platform. This one was patched last October.
XAML Diagnostics bug: Island's Michael Maltsev has published more details on CVE-2023-36003, an EoP vulnerability in XAML Diagnostics, a library used by several Microsoft system utilities.
Ivanti zero-days: watchTowr Labs researchers claim they were able to create PoCs for the two recently disclosed Ivanti Pulse Secure zero-days in less than 48 hours after their disclosure. It's not the first of such claims, and several PoCs appear to have already been created, although none were publicly released at the time of writing.
LATAM app vulnerabilities: CitizenLab and the Open Technology Fund have published a joint report containing details about vulnerabilities in several mobile apps used across Latin America.
Infosec industry
BSides Berlin 2023 videos: Talks from the BSides Berlin 2023 security conference, which took place in November 2023, are now available on YouTube.
Last Shmoocon: The organizers of the Shmoocon security conference have announced that next year's edition (2025) will be the conference's last one.
Industry moves: Brad Arkin has joined Salesforce as the company's new Chief Trust Officer. Arkin served as Cisco's Chief Security and Trust Officer from March 2020 to December 2023. He previously served as Adobe's Chief Security Officer for seven years. [Additional coverage in SecurityWeek]
Free security help for NGOs: The CyberPeace Institute has published a rundown of all the cyberattacks that targeted its staff and operations over the past two years. The organization says it will offer free cybersecurity assistance and expertise to any other NGO that needs such help.
Ghost jobs: Something we missed from last August was this study from StandoutCV that found that almost half of the job listings for cybersecurity analysts in the UK were "ghost jobs."
"They’re used by employers to build a candidate pool, make the company look like it’s actively hiring (therefore growing), or are left by recruiters who simply forget to take them down."
New tool—Canary Token Scanner: The NeroTeam Security Labs (or NSLabs) has released Canary Token Scanner, a script designed to proactively identify Canary Tokens within Microsoft Office documents (docx, xlsx, pptx).
New tool—Talkback: Security firm Elttam has published a technical explanation (I guess it's a formal launch) of how its Talkback infosec aggregator works.
New tool—Exploit Observer: Security firm A.R.P. Syndicate has launched Exploit Observer, a free API that returns information about exploits available for a certain technology or vulnerability.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk with infosec and anti-virus veteran Martijn Grooten about how the infosec industry has changed over the years.




