Risky Biz News: Chinese APT exploits two Pulse Secure zero-days
In other news: FTC issues first US data broker ban; White House prepares cybersecurity requirements for hospitals; ShinyHunters member sentenced to 3 years.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A Chinese state-sponsored hacking group has exploited two zero-days in Ivanti Connect Secure VPN appliances (formerly known as Pulse Secure) to gain access to corporate networks.
The zero-days were discovered by American cybersecurity firm Volexity, which attributed the attacks to a group it tracks as UTA0178.
Ivanti has published mitigations and workarounds that customers can apply until firmware patches are released on January 22.
The two zero-days are an authentication bypass (CVE-2023-46805) and a command injection vulnerability (CVE-2024-21887) that can be chained together to run malicious code on remote Pulse Secure devices.
UTA0178 abused the zero-days primarily as an initial entry vector. After gaining access to Pulse Secure appliances, the attackers installed JavaScript keyloggers that collected user credentials, which they later used to move inside internal networks.
Once inside, UTA0178 installed a new web shell named GLASSTOKEN on internal servers and externally facing devices.
Operators then used a network of hacked Sophos Cyberoam firewalls as proxies and connected to the web shells in order to disguise their real location and collect data from compromised victims.
Volexity says it traced UTA0178 attacks as early as December 3, 2023.
Ivanti says it is "aware of less than 10 customers impacted by the vulnerabilities."
The security firm has published a list of IOCs from the incidents it investigated. It urged Pulse Secure customers to use the IOCs to scan for possible compromises of their internal networks.
Both Volexity and Ivanti warn that applying firmware patches will only prevent future exploitation with the two zero-days but will not remove UAT0178 from already compromised networks. Organizations with Pulse Secure devices will have to scan networks and remove the attacker's web shells on their own.
"The anticipated wait time for a patch is several weeks – some product users will have to wait until February for a patch," Satnam Narang, senior staff research engineer at Tenable, told Risky Business.
"As soon as a proof of concept is available for this exploit chain, we expect malicious activity to spike, especially based on historical activity targeting these products."
More than 16,000 Ivanti Pulse Secure appliances will need patches in the coming weeks. Scans to identify Pulse Secure devices have already begun, according to Rapid7.
Apparently, the two zero-days have been collectively nicknamed "ConnectAround."
Breaches, hacks, and security incidents
Chattr.ai leak: AI hiring tool Chattr left its Firebase database exposed on the internet and leaked its customers' information, two security researchers have found. The company's AI hiring tool is primarily used in the US fast food industry. Its customers include some of the world's largest companies, such as McDonalds, KFC, Taco Bell, Target, Applebees, Arby's, and Subway. The database exposed information on job applicants, franchise managers, and Chattr employees alike.
Maldives attacks: An Indian hacktivist group named TeaM NETWORK9 has defaced multiple Maldives government websites in a series of attacks this week. The attacks came after three local politicians made inappropriate public remarks about Indian Prime Minister Narendra Modi after he urged Indians to vacation in India's own Lakshadweep Islands instead of the Maldives. The Maldives government has since apologized for the statements. [Additional coverage in The Week]
Taiwan cyberattacks: Taiwanese organizations are seeing a flood of cyberattacks and espionage operations ahead of the country's election this weekend. [Additional coverage in Politico]
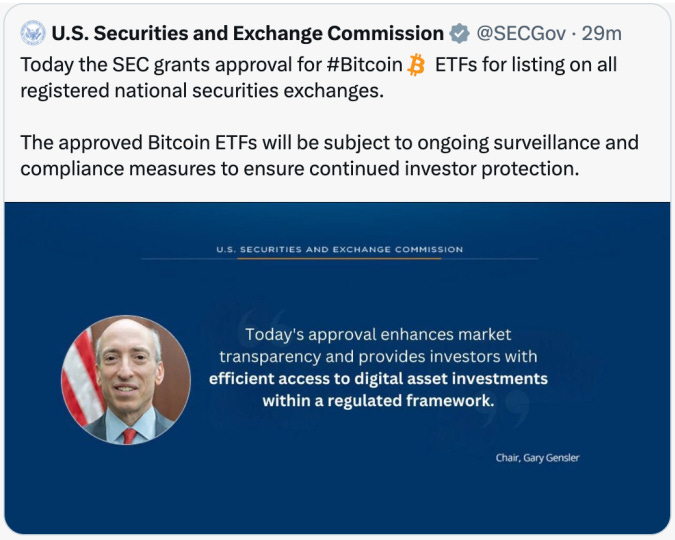
SEC Twitter account hack: A threat actor has hijacked the Twitter account of the US Securities and Exchange Commission and published a tweet claiming the agency had approved the trade of exchange-traded funds (EFTs). The incident is the latest in a long list of similar hacks of official Twitter accounts. Previous hacks have also hit companies like Mandiant, Hyundai, Netgear, CertiK, CoinGecko, and Bloomberg Crypto. Security firm CloudSEK previously reported about the rise of a new marketplace advertising access to compromised Twitter "gold" business accounts. [Additional coverage in TechCrunch]
General tech and privacy
Fortnite refunds deadline extended: The FTC has extended the deadline for parents to submit claims and receive compensation from Epic Games. The game maker agreed last year to pay $245 million to parents whose kids were tricked into making unwanted purchases in the company's Fortnite game. The FTC notified parents via email in September 2023, and parents could have filed claims until January 17 this year. The new deadline is February 29.
FTC bans data broker: The FTC has banned data broker Outlogic (formerly X-Mode Social) from selling precise location data of American citizens. The agency says the sale of such data violates consumers' rights to privacy. The FTC says past X-Mode/Outlogic location data was used to expose visits to sensitive locations such as medical clinics, places of religious worship, and domestic abuse shelters. The agency argued that such data could be used to expose consumers to potential discrimination, physical violence, emotional distress, and other harms. Outlogic becomes the first US data broker to receive this type of ban.
Twitter bans: The "fReE sPeEcH" absolutists at Twitter have banned a large number of accounts for prominent journalists and left-wing political commentators. [Additional coverage in Vice]
Twitter slashes trust and safety team: Twitter has fired a third of its trust and safety team since Musk's acquisition, according to Australia’s online safety watchdog.
Meta GDPR complaint: EU privacy-focused foundation Noyb has filed a GDPR complaint against American social media company Meta. The complaint claims Meta ignores EU users' right to withdraw their consent to be tracked online. Noyb says users of Meta services can't withdraw their consent unless they become paid Meta users, which costs €250/year. The complaint was filed in Austria.
Microsoft EU Data Boundary: Microsoft has announced the EU Data Boundary, a new feature that will let EU organizations store customer data on EU servers only. The new feature will be available for the company's Azure, Microsoft 365, Power Platform, and Dynamics 365 services. Microsoft says some data may be transferred to its US infrastructure for crucial cybersecurity functions, but such transfers will be documented.
Iran's Wikipedia campaign: Pro-Iranian editors are conducting a campaign to alter or delete Wikipedia pages describing its human rights and other abuses. Massive edits were made to Wikipedia's Persian pages, with recent edits now also being made on the English version. The modifications or page deletions were spotted on articles about mass killings, assassinations, and dissidents. The edits were spotted by a Wikipedia editor who shared his findings with journalists after the site failed to take action. [Additional coverage in The Australian]
Government, politics, and policy
New Russian legislation: The Russian government is working on a law draft that will force any website that allows users to "exchange messages" to register with the Roskomnadzor, the country's internet watchdog. Websites that fail do so may be fined or blocked inside RuNet, Russia's internal internet. [Additional coverage in Kommersant]
US cybersecurity requirements for hospitals: The White House will unveil new cybersecurity requirements for US hospitals in the upcoming months. The new rules will require hospitals to establish basic cybersecurity defenses in order to receive federal funding. The US government is pushing the new requirements in the aftermath of a wave of incidents that has crippled hundreds of hospitals across the US over the past year. The US hospital industry previously vowed to fight any new rulemaking. [Additional coverage in The Messenger]

Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Chris St Myers, Stairwell's head of threat research, about managing the risk from software you absolutely must use.
Cybercrime and threat intel
ShinyHunters member sentenced: A US judge has sentenced a French hacker to three years in prison for hacking, wire fraud, and identity theft charges. Sebastien Raoult was a member of the ShinyHunters group, where he operated under the Sezyo Kaizen nickname. He pleaded guilty to hacking and selling the data of more than 60 companies on underground hacking forums. As part of the sentence, Raoult will also have to pay $5 million in restitution for his crimes. [h/t Gabriel Thierry]
CLINKSINK campaign: Mandiant has published details on CLINKSINK, a campaign that uses scams posted on hacked Twitter accounts to lure users to a crypto-drainer phishing kit and steal user's cryptocurrency funds. This is the same campaign that posted a scam on Mandiant's Twitter account at the start of the year.
OPAU (OpAustralia): On December 22, several Indonesian hacktivist groups launched OPAU (OpAustralia), a campaign of attacks against Australian organizations. The reason for the campaign is just as stupid as you think it is—because most hacktivist campaigns are stupid like this.
"The trigger for this campaign was an article from 25 April 2023 that reported on the KKB, who has conducted attacks on the Indonesian military in West Papua. Within the article, it's reported that the KKB has asked Australia for weapons. (The Australian government has not provided any weapons to the group)."
Akira attacks: Finland's cybersecurity agency has published three security alerts over the past weeks warning local organizations about an increase in attacks from the Akira ransomware group. The agency says the intrusions typically occurred after the gang exploited vulnerabilities in Cisco ASA and FTD devices. NCSC-FI says that in several cases, the attackers also wiped NAS and tape backups before encrypting files.
Jenkins brute-force campaign: Jenkins servers are currently seeing some brute-force attacks, per SANS ISC.
Apache exploitation: A threat actor is exploiting Apache Hadoop and Flink servers to deploy rootkits and cryptominers. The attacks have taken place over the past weeks, and the same threat actor previously also targeted Redis and Spring servers as well.
SharePoint exploitation: CISA says that threat actors are exploiting a vulnerability in Microsoft SharePoint servers. Tracked as CVE-2023-29357, the bug was patched in June of last year. The vulnerability is an elevation of privilege that can be chained with other SharePoint bugs to achieve remote code execution attacks. Technical write-ups and public PoCs on how to perform such attacks have been available online since September of last year [1, 2, 3, 4, 5, 6].
Hacked WordPress sites: More than 6,700 WordPress sites have been hacked and compromised with the Balada Injector backdoor. The sites were hacked using a vulnerability (CVE-2023-6000) in the Popup Builder plugin disclosed at the start of December. Balada Injector is a malware campaign that has been active for years. Its primary role is to redirect visitors of the hacked sites to tech support scams.
Abuse of GitHub services: Recorded Future looks at how malware authors are abusing GitHub's services to host and disguise malicious content.
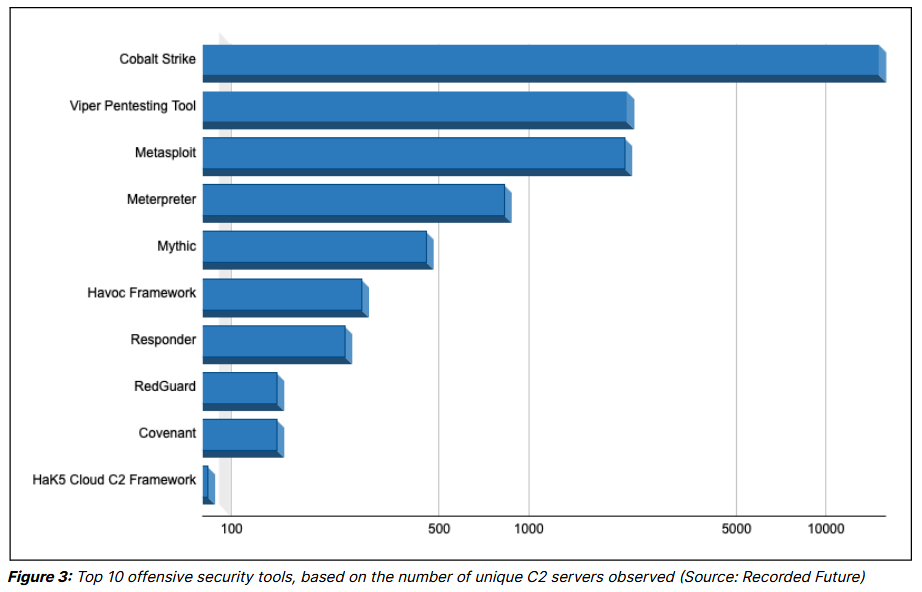
C&C frameworks: Open-source tools like Cobalt Strike, Meterpreter, and Viper have been the most popular command-and-control (C&C) frameworks with malware authors in 2023. The three were by far the most popular frameworks among malware authors, followed at a large distance by tools like Sliver, Havoc, and Brute Ratel. The biggest change is Viper, which is now just as popular as Meterpreter, according to data collected by Recorded Future.
Malware technical reports
Medusa ransomware: Palo Alto Networks has published an analysis of the Medusa ransomware operation, a dual-extortion group that launched in 2023.
Atomic Stealer: Malwarebytes has found a new version of Atomic Stealer, a macOS information stealer that was first spotted last year.
FBot: SentinelOne looks at FBot, a hacking tool used by multiple threat actors to hijack cloud infrastructure, web servers, and SaaS services.
DreamBus: Zscalers researchers look at DreamBus, a Linux-based botnet that has been active since 2019. Researchers say that over the past six months, the botnet has seen a resurgence after launching attacks against Metabase and Apache RocketMQ servers. The final payload is still a Monero miner, as before.
Aquabot: Antiy researchers have published a technical report on Aquabot, another Mirai variant spotted recently in the wild.
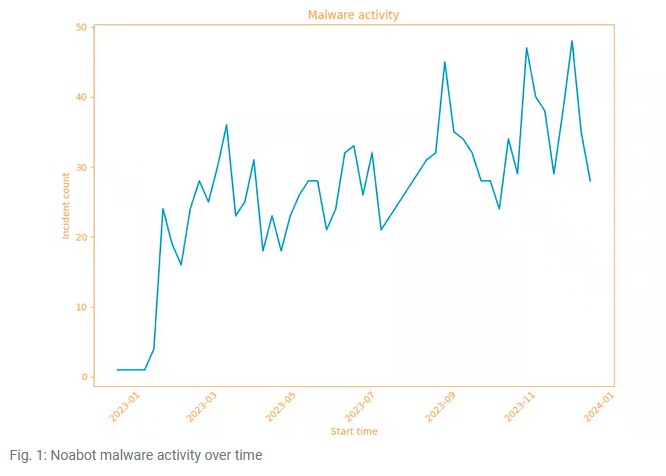
NoaBot: Akamai researchers have uncovered a new malware botnet named NoaBot that has been seen infecting servers across the world. NoaBot is built on top of the Mirai SSH self-spreading worm but drops a cryptocurrency miner on infected systems. Akamai says the botnet has been silently expanding since January of 2023 and appears to be connected to the P2PInfect botnet that targets Redis databases, also for cryptomining.
Sponsor Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs, cyber-espionage, and info-ops
Sticky Werewolf: The Sticky Werewolf APT group launched a spear-phishing operation on January 2 and 3 that targeted Russian telecommunications providers, according to Russian cybersecurity firm FACCT.
UAC-0050: Ukraine's CERT team has new details on the never-ending UAC-0050 spear-phishing campaigns targeting Ukraine.
Sandworm: Forescout has a deep dive [PDF] into the Sandworm attacks against Denmark's critical sector that were spotted last year by local authorities. The surprising main conclusion is below.
"Evidence suggests that the two waves of attacks on Danish infrastructure reported by SektorCERT were unrelated. It also suggests that the second wave was simply part of a mass exploitation campaign against unpatched firewalls, not part of a targeted attack by Sandworm or another state-sponsored actor."
Vulnerabilities, security research, and bug bounty
ColdFusion zero-day write-up: SecureLayer7 has published a technical deep dive of CVE-2023-26360, an Adobe ColdFusion zero-day exploited in the wild that was patched in March 2023.
OFBiz exploitation: Security firm VulnCheck says that of the 10,000 Apache OFBiz servers exposed online, only ~1,000 are vulnerable to a recent zero-day (CVE-2023-51467).
Cisco security updates: Cisco has released or updated seven security advisories for various products.
Unfixed Linux RCE/DOS: A Linux vulnerability tracked as CVE-2023-6270, which can lead to DOS and RCE scenarios, has been sitting unfixed in the Linux kernel for more than 100 days, per Brad Spengler from Grsecurity.
Bosch thermostat firmware rewriting: Bitdefender researchers have found a vulnerability (CVE-2023-49722) in Bosch BCC100 thermostats that can be used to rewrite a device's firmware from the local LAN.
Infosec industry
New tool—ContainerCVE: Software engineer Amir Boroumand has launched a tool named ContainerCVE that scans Docker Hub images for known vulnerabilities.
New tool—Secator: French security firm FreeLabz has released Secator, a task and workflow runner that can be used for cybersecurity assessments.
Tool update—RansomLord: Version 2 of the RansomLord anti-ransomware tool is now out.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk with infosec and anti-virus veteran Martijn Grooten about how the infosec industry has changed over the years.




