China's Barracuda Hacks Were Just Plain Rude
PLUS: Albania's MEK Pickle
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and this week's edition is brought to you by Nucleus Security.

The polite thing to do when your APT operation is discovered by your adversaries is to pack up, go home, and ready your next campaign. What you shouldn't do is escalate in response to discovery, dig in, and turn thousands of expensive email gateway appliances into boat anchors.
But this is exactly what a Chinese APT group did in response to one of its recent campaigns being rumbled.
Last week, Mandiant published a report attributing a recent "wide-ranging campaign" exploiting a Barracuda Email Security Gateway (ESG) vulnerability to a PRC cyberespionage actor it tracks as UNC4841.
UNC4841 took advantage of a vulnerability in Barracuda ESG appliances where the group could gain control of the devices by sending emails with specially formatted TAR archive attachments. The emails these files were attached to looked as spammy as hell, most likely to "dissuade security analysts from performing a full investigation". After gaining control of the ESG appliance, the group would install a variety of different payloads for follow-on operations.
Mandiant describes the campaign as wide-ranging and "spanning a multitude of regions and sectors" and it presents different strands of evidence that support its conclusion that it was a PRC-backed effort.
Targeting, for example, is a bit of a giveaway. Mandiant writes:
Almost a third of identified affected organisations were government agencies, supporting the assessment that the campaign had an espionage motivation. Further, in the set of entities selected for focused data exfiltration, shell scripts were uncovered that targeted email domains and users from ASEAN [the Association of Southeast Asian Nations] Ministry of Foreign Affairs, as well as foreign trade offices and academic research organisations in Taiwan and Hong Kong. In addition, the actors searched for email accounts belonging to individuals working for a government with political or strategic interest to the PRC at the same time that this victim government was participating in high-level, diplomatic meetings with other countries.
When it comes to infrastructure, Mandiant found that UNC4841 used some of the same infrastructure as other operations that are suspected of being PRC linked. Interestingly, Mandiant thinks "this indicates a shared infrastructure procurement support entity rather than the same group being behind both clusters of activity". For cyberespionage, a shared services model may be more efficient or effective but it comes with operational security downsides — it increases the likelihood that notionally unrelated activities can be associated with each other.
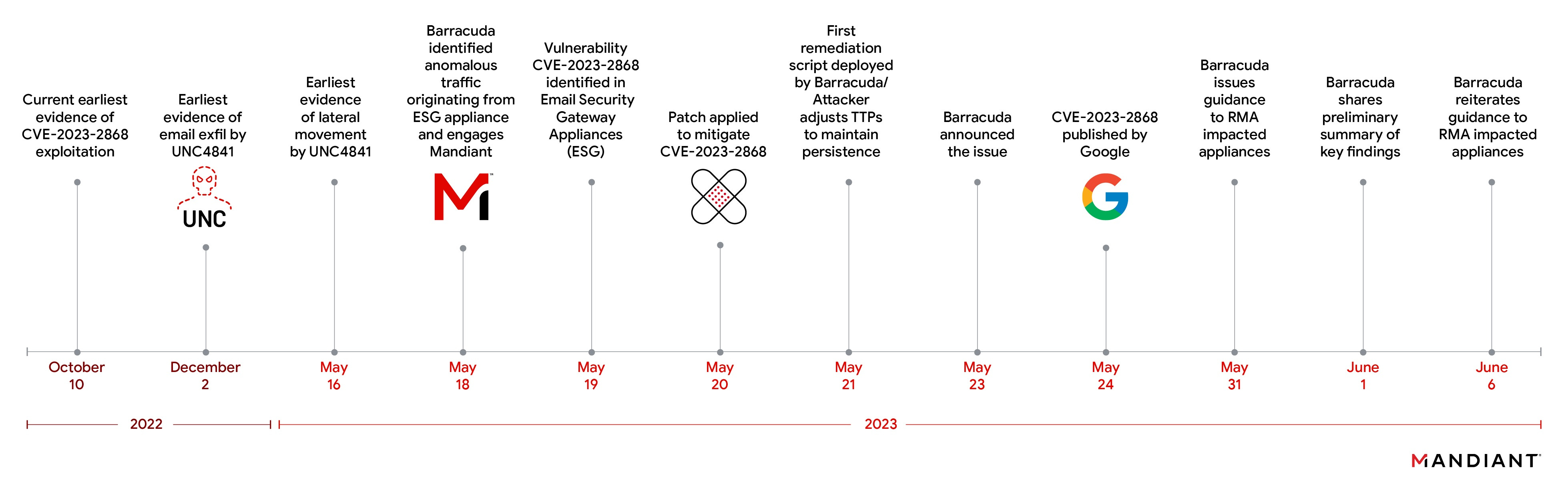
UNC4841's Barracuda campaign started in October 2022, but it wasn't detected until May this year (see timeline). Barracuda moved quickly to roll out patches and kick the group out of its customers' appliances. This triggered a rapid and aggressive response from the group:
On May 19, 2023, UNC4841’s actions were first discovered by the Barracuda team and on May 21, 2023, Barracuda began releasing containment and remediation patches with the goal of eradicating UNC4841 from impacted appliances. In response to these efforts, UNC4841 quickly altered their malware and employed additional persistence mechanisms in an attempt to maintain their access.
Between May 22, 2023 and May 24, 2023, UNC4841 countered with high frequency operations targeting a number of victims located in at least 16 different countries.
We asked Mandiant about these "high frequency operations", which we had assumed were about expanding the number of compromised devices, but apparently they were all about digging in. The group employed a variety of different persistence mechanisms on the Barracuda device including using cron jobs, startup scripts and a kernel rootkit. In some instances they also moved laterally across the network, presumably to set up shop elsewhere in the victim's network.
They dug in so successfully that on June 6 Barracuda warned that customers must replace affected devices, regardless of their patch levels, strengthening its earlier recommendation that they should be replaced.
John Palmisano, a Mandiant Incident Response Manager, told Bleeping Computer that Barracuda was just being thorough because it couldn't guarantee permanent removal of the malware.
"Due to the sophistication displayed by UNC4841 and lack of full visibility into all compromised appliances, Barracuda has elected to replace and not reimage the appliance from the recovery partition out of an abundance of caution," he said.
Using advanced persistence mechanisms that are difficult to detect and remediate is totally fine. But deploying them at massive scale and forcing private companies to undertake expensive remediation is not so fine.
This incident reminds us of the March 2021 mass exploitation of Microsoft Exchange servers by PRC cyber actors dubbed HAFNIUM. Hundreds of thousands of servers were affected and there was significant collateral damage as unsecured webshells were subsequently exploited by criminals. The whole thing looked like it was pulled off by a bunch of criminals, not professional cyber spies.
This Barracuda campaign also feels less like a professional espionage operation and more like the work of a criminal gang. Just look at how the Cl0p gang has moved to monetise flaws in file transfer appliances by hacking them en masse and holding data stolen from them for ransom.
Data extortion causes much more immediate harm than espionage, but the operational behaviour of the PRC in this case is not all that different — fast, aggressive and unconstrained. But the point here is that state-sponsored groups shouldn't behave like criminals. They should have some standards.
The US government has offered a USD$10m reward for information about Cl0p. But what can the US government and allies do to deter this kind of behaviour by the PRC? In July of 2021 the Exchange HAFNIUM incident was the subject of the largest-by-far joint condemnation by the US and its Five Eyes allies, the European Union, all NATO members and Japan and South Korea.
We suspect that more coordinated statements are on the way in the wake of this campaign, and the PRC will just shrug them off and retort that the US is the "biggest global cyber thief" in history.
We wonder whether more public but less formal signalling could be useful here. In the immediate aftermath of the spy balloon incident, for example, the US government reportedly briefed 40 embassies on the PRC's wider surveillance balloon program. China did not like this.
We don't know what the equivalent briefing would look like in this case, but it's our feeling that once you discover something the Chinese government doesn't like you should probably do more of it when they step out of bounds like this.
Albania's MEK Pickle
Albanian authorities have raided a refugee camp run by Iranian opposition party MEK and seized 150 computers as a part of an investigation into hacks targeting Tehran.
About 3,000 members of the MEK live in the Albanian camp. According to the Albanian Ministry of Internal Affairs, the alleged cyber activity broke a 2014 agreement that the camp be used only for humanitarian purposes.
Iran has been getting hacked quite a lot lately, and it's not clear exactly which attacks are thought to have originated from the camp. Our colleague Catalin Cimpanu at Risky Business News notes, however, that the MEK's website has basically served as an "unofficial newswire for various anti-Tehran hacktivist groups".
The whole thing is a mess. People were injured during the raid and one person died.
Iran really doesn't like Albania hosting the MEK, which it maintains is a terrorist organisation. Tehran launched crippling cyber attacks against Albanian government services last year which resulted in Albania severing diplomatic ties with Iran in September 2022.
Risky Business News has more excellent coverage.
Listen to Patrick Gray and Tom Uren discuss this edition of the newsletter in the Seriously Risky Business podcast:
Three Reasons to be Cheerful this Week:
- LockBit Affiliate Arrested… in Arizona: Russian national Ruslan Magomedovich Astamirov has been charged with being a LockBit affiliate after being apprehended in Arizona. Astamirov is alleged by the Department of Justice to be responsible for five ransomware attacks. We don't know why he was in the US and not Thailand.
- US DoJ unit to focus on countering cyber-enabled national security threats: The Department of Justice has announced the creation of a new National Security Cyber Section ("NatSec Cyber") within its National Security Division (NSD). Assistant Attorney General Matthew Olsen said the "new section will allow NSD to increase the scale and speed of disruption campaigns and prosecutions of nation-state threat actors, state-sponsored cybercriminals, associated money launderers, and other cyber-enabled threats to national security". More prosecutions would be good, more disruption would be even better.
- FCC launches Privacy and Data Protection Task Force: The US Federal Communications Commission will launch a privacy and data protection task force. The task force will coordinate efforts that look at data breaches, data privacy and also security-related issues like SIM-swapping.
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on how the company has been tapping into CISA's KEV database for insights on vulnerability management and prioritisation.
And in this product demo Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
Shorts
European Commission: Ditch Huawei Now
Theirry Breton, the European Commission's Commissioner for Internal Markets has told member states that European efforts to restrict "high-risk suppliers" (Huawei and ZTE) from 5G networks are "too slow" and this "poses a major security risk". The warning accompanies a Commission progress report on the implementation of the EU Toolbox on 5G cybersecurity.
In its press release, the Commission said "decisions adopted by Member States to restrict or exclude Huawei and ZTE from 5G networks are justified and compliant with the 5G Toolbox". It is the first time the Commission has named the two Chinese vendors in formal documents and this kind of forthrightness would have been unthinkable just a few years ago, at least from the Europeans. [more coverage at Politico]
The Evolution of the Exploit Industry
Maor Schwarz has an excellent long read about the history and evolution of the spyware and exploit development industry. One of Schwarz's takeaways is that times are getting so tough for exploit development firms that governments that want to sustain these kinds of operations will have to work even more closely with them.
The Evolution of Cyber War
CyberScoop has examined recent cyber operations in the Russia-Ukraine war, and although there's a lot happening it's not clear how much it is affecting outcomes on the ground. CyberScoop writes:
…it is far from clear that these operations are making a meaningful difference to Russian forces in Ukraine, and some of these operations appear geared toward creating the impression of widespread hacking activity even when they aren’t successful.
The various recent developments that the article describes, such as the use of front groups and using visibly destructive operations to affect morale, for example, feel to us like Russian operators are experimenting with how to get the most impact out of their efforts. But we'll only get a good sense of the real contribution cyber operations have made to the war long after it's over.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq look at three different state operations that have recently been outed and what these operations tell us about how these states are behaving.
From Risky Biz News:
Microsoft embarrassingly admits it got DDoSed into the ground by Anonymous Sudan: Microsoft has quietly confirmed that the recent outages of its Outlook, OneDrive, and SharePoint online services were caused by DDoS attacks carried out by a pro-Kremlin group named Anonymous Sudan (Storm-1359 in Microsoft's internal nomenclature).
That's quite the embarrassing statement from one of the world's top three cloud providers that, apparently, can't protect its own services.
In a blog post published late Friday, Microsoft seems to have been caught off guard by the group's choice of attack methodology.
The company says the group leveraged virtual private servers, rented cloud infrastructure, and open proxies to launch the DDoS attacks.
These attacks were "Layer 7," meaning they abused features inside the Microsoft server infrastructure and the apps themselves rather than using a more classic DDoS attack that work at "Layer 3 or 4," and abuse bugs in networking protocols. [See the OSI Model and DDoS attacks]
[more at Risky Biz News]
DHS International Cyber Partner Act: A bill allowing CISA to provide aid to foreign governments has passed the US Senate. [Additional coverage in SC Magazine]
"Current authorities can delay DHS' ability to quickly respond when foreign countries request cybersecurity assistance from the United States. For example, at the start of the Russian invasion of Ukraine, it took weeks for DHS to provide requested support for cybersecurity defenses. The DHS International Cyber Partner Act would authorize DHS and CISA to assign personnel to foreign locations and provide expertise to foreign governments and international organizations on cybersecurity and other homeland security efforts. The bill also allows CISA to include international partners in existing cybersecurity programs that help protect critical infrastructure systems that could disrupt America's national and economic security if breached."
LockBit gang made $91 million from US attacks: The operators of the LockBit ransomware are believed to have made more than $91 million in ransom payments from more than 1,700 attacks targeting US organizations, according to CISA and the FBI.
This puts LockBit right up there with the best-earning ransomware gangs of all time, trailing the likes of Ryuk, REvil, and Darkside. [obviously, based on limited visibility into the ecosystem]
- Ryuk – $150 million
- REvil – $123 million in 2020
- Darkside – $90 million between October 2020 and May 2021
- Maze/Egregor – $75 million
- Cuba - $43.9 million throughout 2021
- Conti - $25.5 million between July and November 2021
- Netwalker – $25 million between March and July 2020
- Dharma - $24 million between November 2016 and November 2019
[more at Risky Biz News]



