Risky Biz News: China admits NSA hacked Huawei
In other news: iOS zero-days used to hack Egyptian presidential candidate; new Sandman APT targets telcos across the world; Russia's largest travel agency breached by pro-Ukraine hackers.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
This newsletter edition covers the bigger news stories from last week (we were off), so it is quite long, at almost 5,000 words. Everything will be back to a shorter, normal version for Wednesday's edition, covering only the most recent stories in infosec of the prior two days.
China's Ministry of State Security (MSS) published an extremely rare official statement on its WeChat account last week formally accusing the US National Security Agency of hacking and maintaining access to servers at Huawei's headquarters since 2009.
The statement is the first time the Chinese government has confirmed the NSA's Huawei hack—first reported by the New York Times and Der Spiegel back in 2014.
Based on documents from the Snowden leaks, the two reports cover Shotgiant, an NSA operation to compromise Huawei's network.
The NSA's intended goals were to find links between Huawei and the Chinese PLA, learn Huawei's internal corporate structure, and identify ways to exploit Huawei equipment—which, at the time, were being widely adopted by both US allies and adversaries.
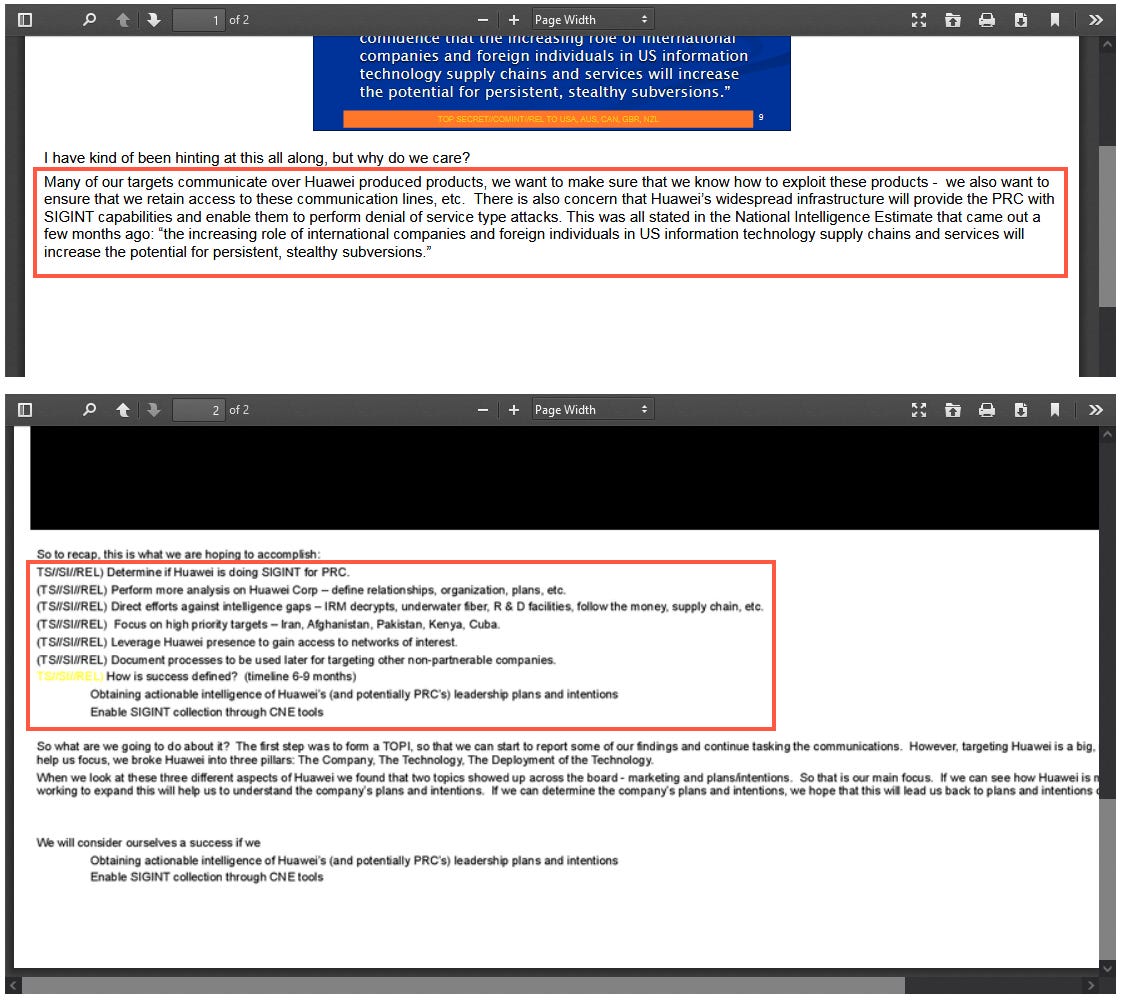
The MSS statement doesn't go into any technical details about the actual hacking but merely recycles information from the NYT and Spiegel reports and the Snowden leaks. It does, instead, spend a lot of time accusing the US of using (and I kid you not) "the despicable tactics of the 'Matrix' to maintain a 'cyber hegemony'."
Chinese officials claim the US is actually doing all the intellectual property stealing and then using its allies and PR machine to hype, exaggerate, and smear innocent little China on the "Chinese cyber secret stealing issue."
None of this is new. We covered both topics in previous editions of your newsletters in April (China using the ancient Snowden and ShadowBrokers leaks to complain about US hacking a decade after the fact) and September 2022 (China's poor attempts at doing US APT attribution with zero discoveries of new tooling).
The MSS press release comes a week after Qihoo 360 published a report that claims to have identified the first known samples of SecondDate, a malware strain first detailed in the Snowden leaks (2013) that the NSA used as recently as June 2022 to hack the network of the Xi'an Northwestern Polytechnical University, a Chinese university known to work on Chinese military projects. If you're having a hard time believing the NSA used malware leaked nine years ago in recent operations, you're not the only one with a raised eyebrow.
The Qihoo report covers the inner workings of an actual malware sample but has yet to be publicly or privately confirmed to this newsletter that it is indeed an analysis of NSA's SecondDate toolkit.
Qihoo also touted that they worked with "industry partners from multiple countries" to identify the NSA operators who conducted the Northwestern hack and 12 other NSA staffers. Chinese state media suggested some sort of NSA dox, but that has yet to happen.
Instead of getting either a dox or an exposé of newer NSA operations, we still get Chinese officials taking ancient NYT reporting and reusing it for the same "US cyber hegemony" propaganda shtick that they've been droning about for two years now.
Che Chang, a cyber threat analyst at the Taiwan-based cybersecurity firm TeamT5, told Wired in a May 2022 piece that all of this is just tit-for-tat propaganda that's not actually based on any new discoveries.
"Considering the close relationship between China's cybersecurity firms and the Chinese government, our team surmises that these reports could be a part of China's strategic distraction when they are accused of massive surveillance systems and espionage operations."
And they are indeed a distraction. For what? For Storm-0558. The recent accusations that the NSA hacked the Xi'an Northwestern University and Huawei come after the US and its allies blamed China for hacking into Microsoft and then pivoting to the email accounts of several US government agencies.
It's indeed tit-for-tat, but as we pointed out last year, this also shows that China's intelligence and cybersecurity sectors are still lagging behind with Western capabilities since it often has to rely on old hacks and leaks to push its "US cyber hegemony" message across.
Breaches, hacks, and security incidents
Air Canada hack: Air Canada officials say a threat actor breached its systems and gained access to employee data. The company says the incident did not impact flight operations or customer systems and that no customer data was compromised.
TransUnion denies hack: US credit reporting company TransUnion has denied getting hacked after some customer data was posted online. The company blamed the leak on a third-party service provider.
Colombia ransomware attack: The operations of multiple Colombian government agencies have been disrupted by a ransomware attack that hit a shared IT provider. The attack took place two weeks ago and impacted IFX Networks. Affected government agencies include the country's health, judiciary, and industry and commerce ministries. The government has also started a legal investigation into IFX Networks for its failure to detect and prevent the attack, which has lead to days-long outages of government services across the country. [Additional coverage in The Record]
Bermuda government cyberattack: Multiple Bermuda government websites and public services are down following a cyberattack that crippled IT systems on Thursday, September 21. The attack has impacted the speed of some government services, such as border crossings, mail delivery, and court proceedings, but most other systems remained unaffected. Officials say the attack originated "most likely from Russia" but did not provide any additional details. The incident is suspected of being a ransomware attack. Other Central American countries that have dealt with similar incidents this past two years include the likes of Costa Rica, Martinique, Trinidad and Tobago, the Dominican Republic, and Guadeloupe. [Additional coverage in Royal Gazette]

Remitano crypto-heist: Crypto exchange Remitano says it lost $2.7 million after a third party was compromised but has already managed to freeze and claw back $1.9 million of the stolen assets.
Balancer crypto-heist: Hackers have stolen $240,000 from users of the Balancer DeFi portal after they compromised its frontend using a DNS attack and redirected users to a phishing page. [Additional coverage in Decrypt]
Microsoft AI leak: A leak in a Microsoft GitHub repo led to the exposure of 38TB of data from Microsoft's AI research team. More in this Wiz blog. This issue has been corrected.
IPI attacks: Two weeks after issuing a report that Hungarian independent media sites are victims of DDoS attacks, the International Press Institute also fell victim to a DDoS attack itself.
ICC hack: The International Criminal Court (ICC) in the Hague fell victim to a cyberattack. The incident took place two weeks ago and was disclosed to reporters from Dutch TV station NOS during a press conference. The hack comes after the ICC charged Russian officials with war crimes earlier this year and after officials announced plans to prosecute hackers for cyber operations that target and damage civilian infrastructure during wars.
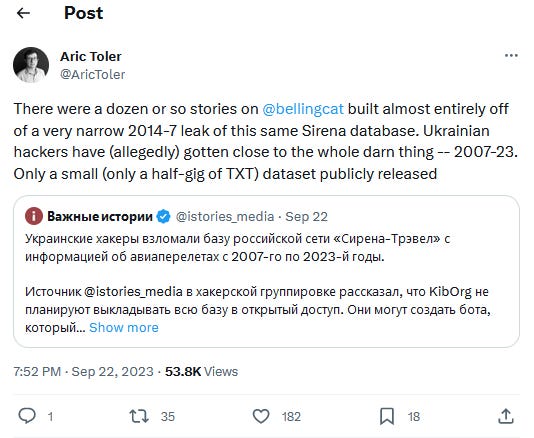
Sirena hack: A pro-Ukrainian hacking group named Muppets has hacked the reservation system of Russian travel agency Sirena. The group claims to have stolen over four billion database entries containing data on airplane and railway reservations made in Russia over the past 16 years between 2007 and 2023. A sample of 3 million entries leaked by the hackers has been verified as authentic by multiple sources. The Muppets group has encouraged journalists to reach out for the data and mine it for information on the travels of Russian politicians and intelligence agents around important events. The hackers say they're also considering transferring the stolen database to the Ukrainian Armed Forces. [h/t Oleg Shakirov; Additional coverage in Important Stories]
General tech and privacy
EU fines Intel: The European Commission has fined US chipmaker Intel €376.36 million for blocking its competitors' access to the x86 CPU market. The fine covers exclusivity contracts between Intel and computer and laptop makers such as HP, Acer, and Lenovo.
Fortnite refunds: Under an FTC lawsuit, Epic Games has now begun refunding parents whose kids were tricked into making unwanted purchases in the company's Fortnite game. The FTC has allegedly notified by email more than 37 million Fortnite players. Epic Games is refunding $245 million in shady Fortnite purchases, and the company will also pay a separate $275 million fine to the FTC for collecting data on kids without their parent's approval.
Twitter is propaganda garbage: Evidence #29,108 that Twitter is now hot propaganda and disinformation garbage.
Disinformation research in the US: WaPo covers the GOP's recent, obsessive, and relentless efforts to intimidate scientists and researchers investigating online disinformation campaigns. We all know why, and it's not about fReE sPeEcH.
Gmail retires HTML view: Google will retire Gmail's Basic HTML View in January 2024.
Chromebook warranty extended: Google has extended the warranty of Chromebook laptops from 5/8 years to 10 years of guaranteed software and security updates. The company's announcement comes after a coalition of K-12 professionals, environmentalists, consumer advocates, and more than 10,000 members of the US Public Interest Research Group have asked Google to support older Chromebooks to avoid e-waste and growing IT costs for US schools.
Mullvad diskless infrastructure: VPN provider Mullvad says it is now running a fully diskless, RAM-based server infrastructure for increased privacy.
Signal update: Signal has hardened its encryption protocol against post-quantum resistant protocols.
Firefox to hide HTTPS protocol: Firefox joins all the other current browsers and will hide the HTTPS protocol marker from the browser's address bar. The change is expected to take place later this year.
Privacy Badger update: The EFF has updated its Privacy Badger browser extension to block the latest techniques used by Google to track users who click on links in Google Search results, Maps, Gmail, Docs, etc.
iOS privacy: It looks like the recently launched iOS 17 has reenabled a couple of privacy settings behind its users' backs. These include Significant Locations and iPhone Analytics. For increased privacy, security experts have always advised to have both options set to OFF.
Android privacy: Ad Topics (Privacy Sandbox) is now being rolled out to Android users. See here for instructions on how to disable it.
Government, politics, and policy
CISA statement on memory safety: CISA has urged software companies and developers to embrace and accelerate their use of memory-safe programming languages.
DOD to rethink cyber role in wars: The Pentagon is reevaluating cyber's role in an active conflict based on the current conflict between Russia and Ukraine. [Additional coverage in DefenseScoop]
Voting machines testing: Three major US voting equipment manufacturers held a first-of-its-kind pilot event where they allowed some of the best cybersecurity experts to test and find vulnerabilities in their voting machines. The event took place between September 18 and 20 last week and involved the testing of digital scanners, ballot marking devices, and electronic poll books manufactured by companies like ES&S, Hart InterCivic, and Unisyn. The three companies say they plan to review reports together with an independent commission and release patches if needed.
Six cyber shields: In a speech last week, Australia's Home Affairs and Cyber Security Minister Clare O'Neil provided the first details on Australia's upcoming National Cyber Security Strategy. The new strategy is built around the concept of building "six cyber shields around [the] nation." The six shields will focus on (1) protecting citizens and local businesses, (2) promoting the use of safe technologies, (3) improving threat sharing and threat blocking, (4) protecting critical infrastructure, (5) creating a sovereign cyber ecosystem, and (6) improving international partnerships. [Additional coverage in itNews]
KYC for Russian web hosts: Russian web hosting providers will be required to verify the identity of all their customers using a real-world document, such as an ID card or a passport. The new know-your-customer requirement will enter into effect on December 1, 2023, according to a document published by the Russian Ministry of Digital Development. Russian communications watchdog Roskomnadzor will also establish a database of all hosting providers and keep track of whether they follow proper KYC requirements. This is part of the Kremlin's crackdown on the Russian Internet space, known as RuNet. Other laws related to this crackdown are covered in one of our August newsletter editions. [Additional coverage in the Moscow Times]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Stairwell Principal Reverse Engineer Silas Cutler about Akira's recent server leak and attacker infrastructure.
Cybercrime and threat intel
More DoppelPaymer raids: German and Ukrainian officials have raided the homes of two suspected members of the DoppelPaymer ransomware gang. The raids targeted a 44-year-old Ukrainian who held a key position within the group and a 45-year-old man from southern Germany who is suspected of having helped the gang launder ransom payments. Officials hope the information they obtained will help track down the whereabouts of the gang's leaders, who were charged earlier this year in March and are still at large.
Online gambling group arrested: Interpol has detained 23 members of a criminal gang that intercepted raw TV signals from sporting events and used the information to place bets before bookmakers could adjust their odds. The scheme worked because the gang relied on raw TV signals while bookmakers used slower satellite TV signals that had a considerable delay. Interpol says the gang collected significant payouts from bets made on Asian and South American football leagues, the UEFA Nations League, the Bundesliga, Qatar 2022 World Cup matches, and ATP and ITF tennis tournaments. Interpol said the gang contained Romanian and Bulgarian members and operated out of Spain, and that besides manipulating online bets, the gang also corrupted athletes to fix games.
Piilopuoti takedown: Finnish authorities have taken down a dark web marketplace operating within its borders. Named Piilopuoti (Finnish for "Hidden Shop"), the site has been live since May 2022 and has been a haven for the sale of drugs and other illegal substances.
WeLeakInfo letters: Dutch police are sending letters to 400 Dutch citizens who purchased stolen data from the WeLeakInfo portal.
Indian cybercrime hot spots: An FCRF report looks at the cybercrime trends and cybercrime centers that are growing inside India's burgeoning IT landscape. The report highlights payment card fraud and SIM swapping as popular forms of cybercrime and several cities as cybercrime hot spots, such as Chennai, Hyderabad, and Bengaluru.

GOLD MELODY group: An initial access broker (IAB) named GOLD MELODY (Prophet Spider) has been hacking companies across the world since 2017 and selling access to other criminal groups, including ransomware operators. The group has been observed exploiting vulnerabilities in products such as Apache Log4j, Apache Struts, Sitecore, Oracle E-business, and Oracle WebLogic. According to Secureworks, the group has worked with ransomware gangs such as Egregor, CryptoDefense, and MountLocker.
LUCR-3: Permiso has a blog on the tactics of LUCR-3, a threat actor also known as Scattered Spider, Oktapus, UNC3944, and STORM-0875—the group behind the recent MGM and Caesars attacks. Okta CSO David Bradbury says that besides MGM and Caesars, the group also hit three other companies operating in the manufacturing, retail, and technology sectors. In the meantime, MGM has restored its systems 10 days after the initial intrusion.
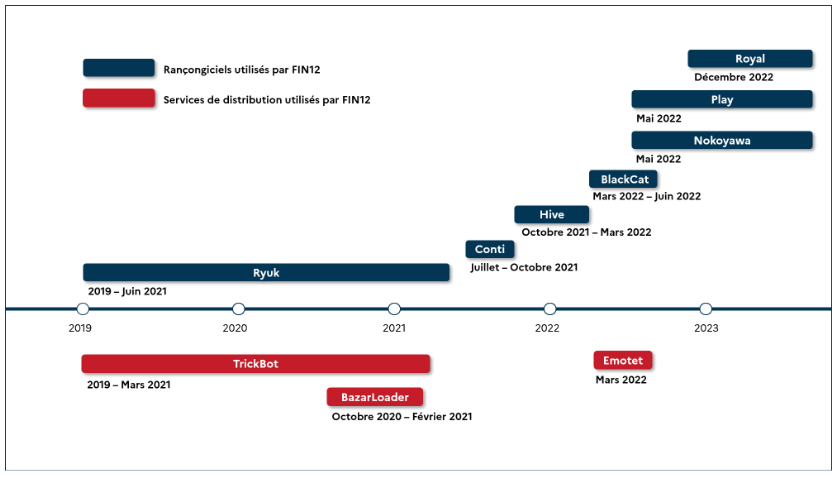
FIN12: CERT-FR has published a detailed report (French language only for now, English version to follow) on the operations of FIN12, a cybercrime group that has rented access to several malware botnets in order to deploy various ransomware payloads. The group has been seen using TrickBot, Emotet, and BazaarLoader in order to deploy ransomware such as Ryuk, Conti, Hive, BlackCat, Royal, and others. Also known as Pistache Tempest, the group is one of today's most active ransomware affiliates.
8Base leak: A leak on the dark web leak site of the 8Base ransomware suggests the website was coded by a 36-year-old Moldavian man named Andrei Kolev [archived]. [Additional coverage on KrebsOnSecurity]
PayPal scams: Netcraft has spotted a series of PayPal scams that are abusing PayPal's official invoicing service to send out authentic-looking invoices that contain malicious contact phone numbers.
Factory resetting malware: Singapore police are warning of a new Android malware strain that is performing factory resets on infected devices after it executed unauthorized e-banking transactions.
New npm malware: Ninty-seven malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details. This includes 14 packages spotted by Sonatype that were caught stealing Kubernetes config files and SSH keys.
Malicious PyPI package: Checkmarx has identified a malicious Python library named Culturestreak that installs a cryptominer on infected systems.
Bot attacks: A Netacea study found that 72% of surveyed companies experienced a bot attack originating from China's IP address space.
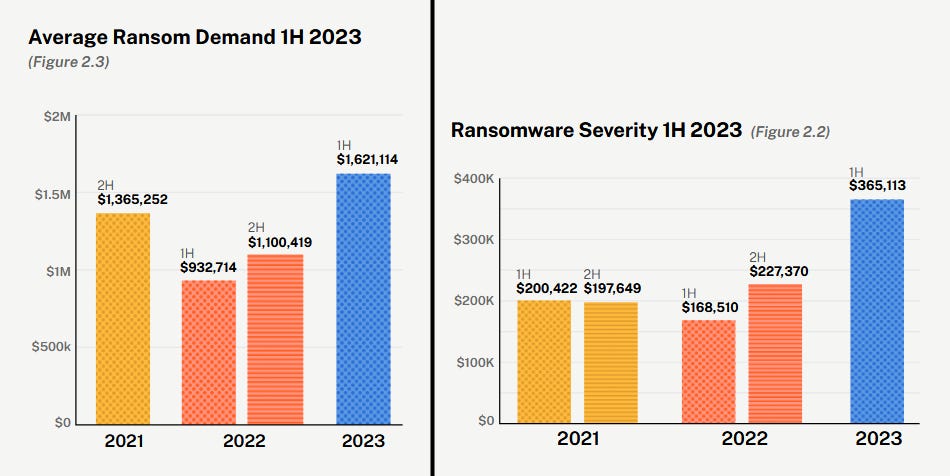
Ransomware in H1 2023: The number of ransomware insurance claims grew by 12% in the first half of the year, according to cyber-insurance provider Coalition [PDF]. The growth in ransomware activity can also be seen in the average loss caused by a ransomware attack (now at $365,000) and the average ransom demand (now at $1.6 million).
Malware technical reports
BBTok: Check Point has a report on BBTok, a new banking trojan targeting Latin America and heavily relying on LOLBins for its post-infection phase. The banker appears to have been active since 2020 and appears to focus on banks in Brazil and Mexico only.
Bumblebee returns: The operators of the Bumblebee malware botnet resumed activity at the end of August after a two-month break. The gang's return came as law enforcement agencies took down the Qakbot botnet. Together with IcedID and DarkGate, Bumblebee is one of the three botnets that are expected to take Qakbot's place in the underground malware distribution ecosystem.
QakBot affiliate moves to DarkGate: And just on cue to prove our point, a former Qakbot affiliate tracked as TA577 is now pushing DarkGate, according to Prodaft, Cryptolaemus, and Deutsche Telekom's CERT. An analysis of a recent DarkGate campaign is also available on the DCSO blog.
CloudEyE returns: The Italian company behind the CloudEyE code obfuscation has re-activated its website and its selling access to its toolkit once more. The company shut down operations in 2020 after Check Point surfaced connections between the company, CloudEyE, and the GuLoader malware. In a recent report, Check Point looks at how CloudEyE is being used in GuLoader campaigns again to help the malware deploy various RATs, such as Remcos.
Chinese campaigns: Proofpoint looks at PurpleFox, ValleyRAT, and Sainbox RAT, three malware strains that are widely used in campaigns targeting Chinese companies and users.
RedLine Stealer: CyFirma has a report on recent RedLine Stealer operations and the malware's proliferation.
Fake WinRAR exploits: Palo Alto Networks says it has seen fake exploits and PoCs for the recent WinRAR zero-day (CVE-2023-40477) being used to infect security researchers with the VenomRAT malware.
Snatch ransomware: CISA and the FBI [PDF] have published a joint advisory with technical details on the Snatch ransomware gang. The group has been active since 2018 and uses file encryptors, data exfiltration, and double extortion tactics. Besides that, the group has also been seen purchasing data stolen by other ransomware groups and extorting victims in their stead.
AMBERSQUID: A new threat actor named AMBERSQUID is compromising AWS cloud infrastructure in order to deploy cryptominers on victim networks. The group has been active since May 2022 and has been seen leveraging AWS services like Amplify, Fargate, and SageMaker, which are not typically covered by cloud security solutions. Sysdig says it saw AMBERSQUID generating cloud computing bills for some of its victims as large as $10,000/day.
P2PInfect explodes: Cado Security says it saw a 600x increase in activity from the P2PInfect botnet since August 28. The malware was first spotted in July this year targeting Redis servers. Most of the infected systems are located in China, on the network of the Hangzhou branch of Alibaba Cloud.
Sponsor Demo Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
Predator spyware in Egypt: The Egyptian government is suspected to have performed a man-in-the-middle (MITM) attack on the network of Vodafone Egypt in order to redirect mobile traffic from a political figure and infect their smartphone with the Predator spyware. The attack targeted Egyptian MP Ahmed Eltantawy days after he announced his intention to run for president. According to CitizenLab, the malicious website used an exploit chain of three iPhone zero-days (CVE-2023-41991, CVE-2023-41992, CVE-2023-41993) to deploy the spyware. Google researchers say they also discovered a similar exploit chain targeting Android devices that relied on a now-patched Chrome zero-day (CVE-2023-4762).
Transparent Tribe: SentinelOne has found three Android apps containing a version of CapraRAT, a remote access trojan used by Transparent Tribe, a Pakistan-based state-sponsored APT group. The three apps mimic the official YouTube app and appear to have been used in romance-based social engineering attacks.
Stealth Falcon's Deadglyph: ESET looks at Deadglyph, a new backdoor used by suspected UAE APT group Stealth Falcon (FruityArmor, Project Raven). ESET says they found the malware used in an attack against the network of a Qatari government agency.
APT campaign in Armenia: Security researchers are seeing a state-sponsored campaign targeting Armenian government agencies posing as the country's intelligence service. The final payload is the AsyncRAT.
APT29: Google's Mandiant division takes a look at the increased pace of espionage activity performed by Russia's APT29 group since the start of Ukraine's counter-offensive earlier this year.
Turla: Trend Micro takes a top-down view of recent Turla APT operations and their most common TTPs. A similar Turla overview is also available from PAN Unit42.
Oilrig: ESET takes a look at Outer Space and Juicy Mix, two Oilrig APT espionage operations that have targeted Israeli organizations in 2021 and 2022, respectively.
Gelsemium: PAN Unit42 has observed a rare campaign from a super stealthy APT group named Gelsemium. The campaign a Southeast Asian government over six months between 2022-2023.
"In addition to an array of web shells, the main backdoors used by the threat actor were OwlProxy and SessionManager. This combination, which was publicly documented once before in 2020, is rare and was previously used to target several entities in Laos."
Stately Taurus: PAN Unit42 has observed the Stately Taurus (Mustang Panda) Chinese APT engaged in a number of cyberespionage intrusions targeting a government in Southeast Asia.
"The intrusions took place from at least the second quarter of 2021 to the third quarter of 2023. Based on our observations and analysis, the attackers gathered and exfiltrated sensitive documents and other types of files from compromised networks."
Alloy Taurus: The same PAN Unit42 team has also seen the Alloy Taurus APT mount attacks against another Southeast Asian government. These attack waves used Exchange vulnerabilities and started in early 2022 and persisted throughout the current year.
Earth Lusca: Trend Micro researchers have discovered a Linux backdoor named SprySOCKS that is currently being used in the wild by Chinese APT group Earth Lusca. Researchers say the backdoor appears to have been developed from the code of an open-source Windows backdoor named Trochilus. SprySOCKS is currently deployed on internet-facing Linux systems compromised via N-day vulnerabilities.
TAG-74: RecordedFuture says the Chinese APT group TAG-74 has conducted a multi-year cyber-espionage campaign that has targeted the government of South Korea.
"TAG-74 primarily focuses on infiltrating South Korean academic, political, and government organizations. This group has been linked to Chinese military intelligence and poses a significant threat to academic, aerospace and defense, government, military, and political entities in South Korea, Japan, and Russia. TAG-74's targeting of South Korean academic institutions aligns with China's broader espionage efforts aimed at intellectual property theft and expanding its influence within higher education worldwide."
EvilBamboo: A Chinese cyber-espionage group known as EvilBamboo (EvilEye, GREF, APT15) has been conducting a years-long operation using malware hidden in Android apps. The campaigns have involved malware named BADBAZAAR, BADSIGNAL, and BADSOLAR, and targets have included Tibetan, Uyghur, and Taiwanese individuals and organizations. Security firm Volexity says the EvilBamboo group relies on third-party websites to distribute the apps, which are usually posing as add-ons or enhancements for popular apps such as Signal and Telegram. Volexity says it found credible evidence that an iOS version of the BADSIGNAL malware was distributed through Apple's official App Store but has yet to discover a sample.
Chinese APTs in Africa: At its LABScon conference, SentinelOne has taken a look at China's recent cyber-espionage efforts that have focused on African countries. The new report covers Tainted Love, a broad spying operation carried out by the BackdoorDiplomacy APT, and which targeted entities in the African telecommunication, finance, and government sectors.
ShroudedSnooper: A new APT group named ShroudedSnooper has compromised telecommunication providers across the Middle East using two malware strains named HTTPSnoop and PipeSnoop. Cisco Talos has not attributed the group to any state actor (yet).
Sandman: A new APT group named Sandman has compromised telecommunication providers in the Middle East, Western Europe, and South Asia. Attacks go back as far as the first half of the year and have relied on a malware framework named LuaDream. SentinelOne says the malware has 36 components and suspects Sandman may be a private contractor or mercenary group.
"Attributing Sandman remains a mystery, placing it in the same enigmatic category as Metador and other elusive threat actors who operate with impunity. LuaDream stands as a compelling illustration of the continuous innovation and advancement efforts that cyber espionage threat actors pour into their ever-evolving malware arsenal."
Vulnerabilities, security research, and bug bounty
Variston Heliconia exploits analysis: Google Project Zero looks at the three bugs used for an in-the-wild exploit chain that was deployed against UAE-based Samsung Android devices earlier this year. The exploit chain was linked to spyware vendor Variston, where it is part of its Heliconia attack framework.
WebP zero-day analysis: Ben Hawkes from Isosceles has an analysis of the recent WebP zero-day (CVE-2023-4863) that has been used by the NSO Group to deploy its Pegasus spyware.
Trend Micro zero-day: Trend Micro has released patches for a zero-day vulnerability (CVE-2023-41179) that was exploited in the wild. The vulnerability resided in a third-party AV uninstaller module included with its Apex One (on-premise and SaaS), Worry-Free Business Security, and Worry-Free Business Security Services (SaaS) products.
GitLab security update: GitLab released a "critical" security update last Monday. The update patches CVE-2023-5009, a bypass for a previous bug tracked as CVE-2023-3932.
Nagios XI vulnerabilities: Outpost24 has discovered four vulnerabilities in the Nagios XI network monitoring solution.
VMWare Aria analysis: Juniper has published a deep dive into CVE-2023-20887, a VMWare Aria remote code execution vulnerability that has been exploited in the wild over the past few months by APT and cybercrime groups alike.
DoubleQlik vulnerability: Security firm Praetorian has discovered a bypass for an RCE vulnerability in Qlik Sense, a business data analytics platform used for data visualization and analysis.
CISA KEV reaches 1K: The CISA KEV database of actively exploited vulnerabilities reached more than 1,000 entries last week. CISA says the KEV database has been a resounding success as federal civilian agencies have reduced their exposure to known exploited bugs by 72%, 45 days after an entry is listed. CISA says vulnerabilities listed in KEV get fixed nine days faster compared to bugs that are not listed in KEV. This stat is even more impressive for internet-facing bugs, which get fixed 36 days faster if they're listed in KEV.
GitHub Security Lab reaches 500 disclosures: GitHub's security team says it has now identified and helped disclose and patch 500 security flaws since starting its effort back in 2017.
Infosec industry
Cisco acquires Splunk: Networking and cybersecurity giant Cisco has acquired SIEM provider Splunk for $157 per share in cash, representing approximately $28 billion in equity value. Cisco plans to merge Splunk's threat detection and response capabilities with its threat prediction and prevention services and boost its cybersecurity offerings.
Chronicle update: Google Cloud has announced that Chronicle has merged its SOAR and SIEM solutions.
Yubico goes public: Hardware security key maker Yubico is now listed on the Stockholm stock exchange.
New tool—Donut Decryptor: Security firm Volexity has published a tool named Donut Decryptor, a tool to decrypt and analyze malware obfuscated with the Donut open-source code obfuscator.
New tool—Capslock: Google has open-sourced a tool named Capslock that can analyze Go libraries and notify users of what privileged operations a package can perform/access.
Risky Business Podcasts
In this edition of Seriously Risky Biz, guest host Adam Boileau talks with Tom Uren about what Microsoft's recent breach by a Chinese-based threat actor tells us about the company's security culture. There were several serious governance failures that allowed this incident to happen.




