Bringing Humanitarian Law to Cyber War
PLUS: EU Needs to Grow a Spine on Spyware
Your weekly dose of Seriously Risky Business news is written by Tom Uren and edited by Patrick Gray. It's supported by the Cyber Initiative at the Hewlett Foundation and this week's edition is brought to you by Netwrix.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this edition here and on Spotify:

It is hard to care about hacktivism when the news from Israel and Gaza is so bleak, but there has been a flurry of activity from both camps since the conflict erupted.
Cyber attacks reported so far include the DDoSing of both Israeli and Palestinian websites and the leaking of stolen documents and credentials from Israeli-related sites. While these actions generally made little difference to events on the ground, some attacks attempted to disrupt Israel's response to Hamas rocket attacks.
Per Wednesday's edition of Risky Business News:
Pro-Palestine hacktivist groups have launched several cyberattacks that targeted Israel's rocket alert system. DDoS attacks hit endpoints responsible for alerting citizens of incoming missile raids, even as early as one hour after the Hamas operation began. Several groups participated in the attacks, such as Anonymous Sudan, Killnet, and AnonGhost. The latter also exploited vulnerabilities in the API system of Red Alert, an Android app that sends rocket alerts to Israeli citizens. The group abused the API to send fake rocket and nuclear bomb alerts meant to sow panic among the Israeli population.
Threat intelligence analyst CyberKnow is tracking 83 groups so far that have announced involvement in the Israel-Hamas hostilities — 69 pro-Palestine groups and 14 pro-Israel groups.
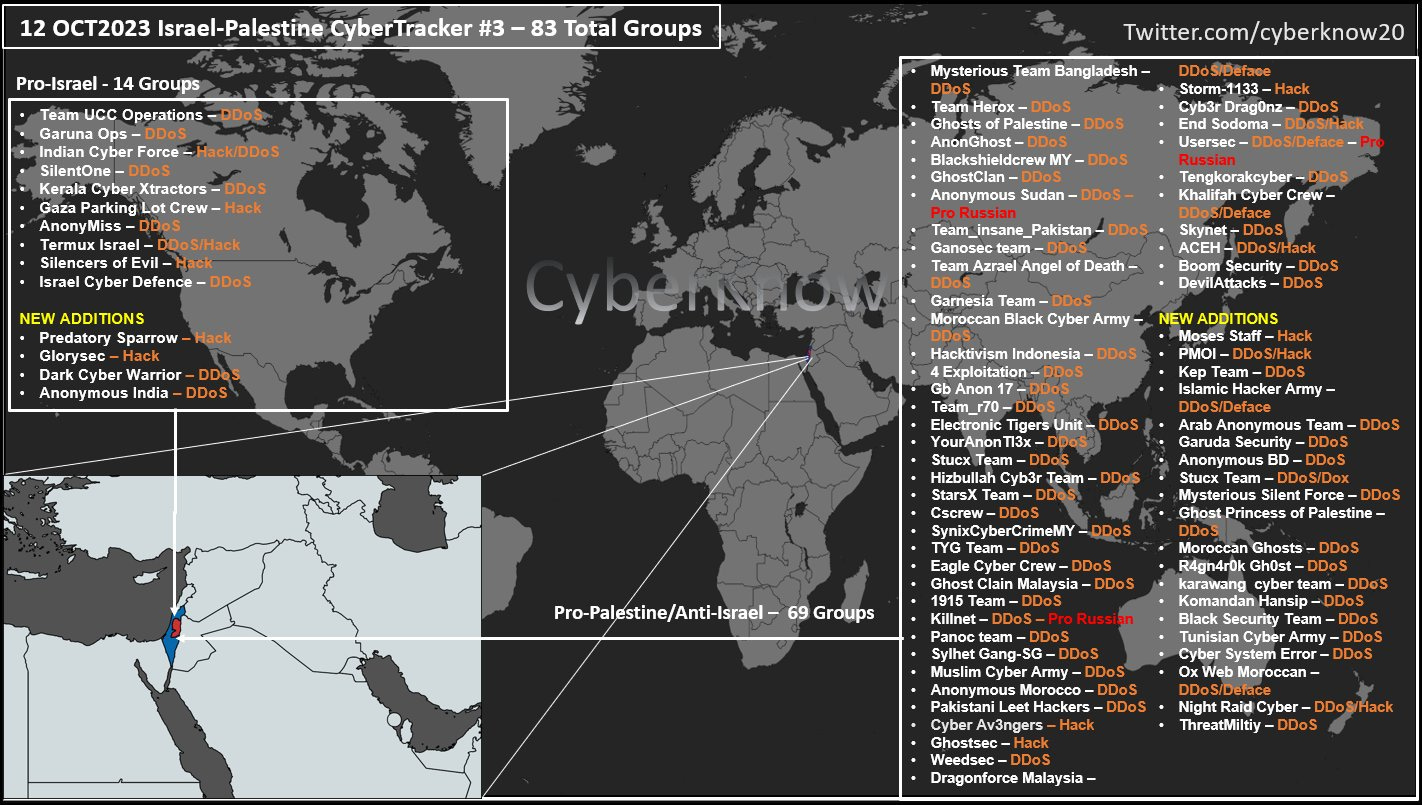
The current scenario is similar to the Russian invasion of Ukraine, where hacktivist groups support both sides. Of course, state-linked groups posing as hacktivists are also involved.
A likely Iran-linked threat actor, Moses Staff, has reappeared on Twitter/X, posting in support of Hamas’s actions. While purporting to be a ransomware actor, the group has previously launched a number of destructive attacks against Israeli organisations.
On the Israel-supporting side, Predatory Sparrow has posted on Twitter/X "we are back". This group is responsible for some spectacularly successful attacks in Iran, including one that dropped molten steel all over a factory floor. Other attacks have affected Iran’s train services and its fuel subsidy system.
These operations were professionally executed and Predatory Sparrow also takes extensive steps to illustrate that it is conducting 'responsible' destructive cyber operations. In these attacks, for example, they've issued prior warnings to minimise collateral damage and prevent people from being physically hurt. (For more information see this newsletter's previous coverage and my discussion with The Grugq covering Predatory Sparrow).
We are sceptical about the value of genuine (i.e. not linked to a state) hacktivist operations, mostly because they could interfere with intelligence collection operations established to inform state actions that have far greater impact on events. Governments need to think about managing or shaping civilian hacktivist actions during conflict to minimise interference with their own cyber operations.
The role of cyber operations during conflict and the obligations on states to restrain hacktivism has drawn the attention of high profile legal specialists. Writing in a blog associated with the European Journal of International Law, two lawyers recently published eight rules for civilian hackers, and four obligations on states to restrain them. The eight rules for hackers are:
- Do not direct cyber attacks against civilian objects.
- Do not use malware or other tools or techniques that spread automatically and damage military objectives and civilian objects indiscriminately.
- When planning a cyber attack against a military objective, do everything feasible to avoid or minimise the effects your operation may have on civilians.
- Do not conduct any cyber operation against medical and humanitarian facilities.
- Do not conduct any cyber attack against objects indispensable to the survival of the population or that can release dangerous forces.
- Do not make threats of violence to spread terror among the civilian population.
- Do not incite violations of international humanitarian law.
- Comply with these rules even if the enemy does not.
These rules and the obligations on states are essentially an extension of the fundamental principles of International Humanitarian Law (IHL, or the Rules of War), and try to ensure cyber hacktivism avoids harming civilians as much as possible.
It's easy to be cynical about these rules, especially when participants engaged in real-world conflict are not observing IHL. It is hard to see that civilian hacktivists motivated by righteous fury will restrain themselves when atrocities are being committed.
For now, however, actors with the skills and resources to cause the most damage (such as Predatory Sparrow) are associated with states. International law may make a difference to these groups. After all, the whole point of IHL is to at least try to make war a little bit less horrible, even if it is not always successful.
EU Needs to Grow a Spine on Spyware
A new investigation has found that EU-based spyware firms have sold their products to authoritarian governments and these products have been used to target European, US and UN government officials.
The investigation, reported under the name 'The Predator Files', is a collaboration between the European Investigative Collaborations (EIC) media network and Amnesty International.
Amnesty International's Security Lab provided technical assistance to the investigation and produced a technical report focused on the Intellexa alliance and its Predator spyware. The Intellexa alliance is a collection of spyware and intelligence companies that appear to have corporate links or share common ownership.
Amnesty documents a particular Predator campaign that appears to be Vietnam-linked and conducted targeting over X (formerly Twitter). In this case, malicious Predator infection links were sent in replies to targets from the @Joseph_Gordon16 Twitter/X account.
This public targeting provided Amnesty's Security Lab with insight into the Predator operator's goals. Its report says:
The targets selected by this account included journalists, academic researchers working on security issues in the South China Sea and Vietnam, as well as senior political officials in the EU, US, and elsewhere, involved in work related to international fishing regulation, an issue of interest to the Vietnamese authorities
The accounts targeted include various European Commission officials, the German Ambassador to the US, Taiwanese President Tsai Ing-Wen, the Taiwanese Ministry of Foreign Affairs, and a Berlin-based media website covering news about Vietnam. The @Joseph_Gordon16-associated infection attempts documented by Amnesty International occurred from February through June this year.
Assuming the operators are linked to the Vietnamese government, at a big-picture level this targeting itself seems fair enough, as it is the sort of espionage that Western governments consider legitimate.
The way it was carried out though—replying with malicious links on Twitter—is pretty crude. Presumably this technique works sometimes, but it's not very specific.
Relatedly, Amnesty found that four US congresspeople were targeted, although perhaps not intentionally. Two of the four, US Senator John Hoeven and Representative Michael McCaul were separately tagged in a tweet from President Tsai Ing-Wen and one from the Taiwanese Ministry of Foreign Affairs respectively. The Predator campaign operator replied with malicious links to the original tweet without removing tags to Hoeven and McCaul, so perhaps they weren't the intended targets. The report isn't explicit about whether the other two US congresspersons involved, Senators Chris Murphy and Gary Peters, were directly targeted, although it was in a tweet that also referenced an Albanian parliamentarian.
From a European perspective, however, the use of Predator in this campaign is outrageous and notionally European companies are selling spyware which is then used to target European and allied politicians. Predator was also used in last year's Greek spyware scandal, where it was deployed for political purposes and used on journalists, activists, opposition political figures and even government cabinet members.
Sales of systems like Predator outside the EU are theoretically subject to export controls but Intellexa has been skirting these regulations by selling via an Intellexa entity in the United Arab Emirates. Amnesty International's report describes this as an EU and member state regulatory failure, and they are not wrong.
The US government has already acted against Intellexa. In July this year it put Intellexa and Cytrox, the Intellexa alliance firm that originally developed Predator spyware, on the US entity list. This prohibits US companies from doing business with them.
The Europeans need to grow a spine here. The European Parliament's PEGA Committee investigating the use of spyware has bemoaned the lack of political will to actually do anything about this problem. In its report to the parliament it concluded that:
…neither the Member States, nor the Council, nor the Commission seemed to be at all interested in maximising their efforts to fully investigate the spyware abuse, thus knowingly protecting Union governments which violate human rights within and outside of the Union.
Perhaps the targeting of EU officials and politicians will finally provide the incentive to act. But we can only hope.
The Chinese Spies Are In The Mail
According to The Financial Times, Belgian intelligence is concerned that a Chinese logistics company that has a large presence in Liège could be used for espionage.
Cainiao, the logistics arm of Chinese giant Alibaba, runs a large logistics hub at Belgium's Liège cargo airport. The Belgian State Security Service (VSSE) fears that information from the logistics hub could be provided to the Chinese government to give them insights into supply chains and potential vulnerabilities.
There certainly are reasons to be concerned and we've argued in the past that "Chinese firms are so closely interlinked with the Chinese government that they cannot be trusted in critical infrastructure".
The Financial Times writes that "Cainiao is able to access data about merchants, products, transport details and flows, said a person familiar with its IT systems", which sounds concerning. However, it also states that the logistics centre in Liège "mainly handles goods sold directly to European consumers through the online shopping site AliExpress".
So the magnitude of the risk here really depends upon whether Cianiao has access to data about other logistics shipments, not just its own. If it can only see its own shipments, we don't see that Cianiao's presence in Belgium is really an additional espionage risk, since a Chinese Alibaba group company already knows all about the shipments anyway.
Still, and we've made this point before, it's the PRC's own actions that make it difficult for its companies to be trusted overseas. There are genuine reasons to be concerned.
Three Reasons to Be Cheerful this Week:
- Google makes passkeys default sign-in: Google has made passkeys the default way to sign in to accounts as of Tuesday this week.
- VBScript on the way out: Microsoft has announced it will remove VBscript from future versions of Windows, although it will be available as a "Feature On Demand" if it is needed. VBScript has been part of the Windows operating system since 1998 and has been a popular tool amongst malware developers. Risky Business News has more in-depth coverage.
- Clouds mandate more MFA: AWS announced that accounts with the highest privileges will be required to use Multi Factor Authentication from mid-2024. Google subsequently told Cybersecurity Dive it would impose the same requirement before the end of this year.
Sponsor Section
In this Risky Business News sponsor interview Tom Uren asks Martin Cannard, VP of Product Strategy at Netwrix, how privileged access management can help defend organisations. 'Advanced Persistent Teenagers' regularly use social engineering techniques to compromise highly privileged accounts, but that doesn't mean it's instantly game over.
Shorts
This Robot Will Seduce and Rob You
Researchers at cyber security firm Avast have produced a report looking at how ChatGPT is being used in a dating platform scam.
The tool has been around for at least a decade, but the incorporation of ChatGPT led the researchers to call it LoveGPT. The tool is quite sophisticated and automates the creation of fake profiles and harvests data across 13 dating platforms. ChatGPT functionality is used in creating description text in fake profiles, reading and replying to messages and asking for phone numbers.
The Record has more comprehensive coverage.
Crypto Theft Wrapped in Fraud, Surrounded by Incompetence
Wired has a tremendously entertaining story about the shenanigans at the FTX crypto exchange on the day it declared bankruptcy and a thief stole over USD$400m worth of cryptocurrency.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq look at the potential for a cyber criminal match made in hell between ransomware actors and BEC scammers.
From Risky Biz News:
Tech companies and security firms rally against EU vulnerability disclosure rules: A group of more than 50 tech experts and organizations have signed an open letter asking EU officials to rethink Article 11of the upcoming EU Cyber Resilience Act.
The article introduces a mandatory requirement for all software vendors to disclose vulnerabilities to the ENISA, the EU's cybersecurity agency, within 24 hours of becoming aware of in-the-wild exploitation. ENISA will then relay this information to national CSIRT teams and stock market watchdogs across its member states.
The open letter's signatories argue that the CRA's Article 11—in its current form, at least—greatly expands the number of organisations that will have first-hand and real-time immediate knowledge of actively exploited vulnerabilities, which, in turn, increases the risks to product vendors, their customers, and the general public.
[more on Risky Business News]
Human-operated ransomware attacks double in a year: The number of human-operated ransomware attacks has more than doubled over the past year, Microsoft said in its yearly Digital Defense Report.
The term "human-operated ransomware" refers to certain intrusions where the ransomware is deployed manually rather than using automated scripts.
[much more on Risky Business News, including that the number of ransomware incidents has returned to 'normal' after the initial disruption of the Russian invasion of Ukraine and how in more than half of ransomware incidents file encryption is deployed within a day of initial access.]
DPRK operations: Google's Mandiant division has published an updated guide to understanding North Korea's APT and cyber operations, complete with an updated organisational chart. The report's main findings are that DPRK groups now increasingly share resources and temporarily collaborate on operations, making exact attribution extremely difficult.
Malware infrastructure overlaps indicating resources and attribution muddled by shifting assignments show how DPRK cyber operations are changing. However, operations conducted to fulfil regime requirements remain steadfast and we believe they will continue. While defenders may not be able to easily sort new DPRK activity into a previously identified bucket, the malware reuse and shared resources creates opportunities for detection and country level attribution.




