Risky Biz News: Black Basta group made $107 million from ransom payments
In other news: HackingTeam founder arrested in Italy for attempted murder; US seizes Sinbad mixer; and Okta breach was larger than initially thought.
This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Black Basta ransomware gang is believed to have made more than $107 million in ransom payments since the group began operations in early 2022.
The number represents payments made by more than 90 victims of the 329 organizations known to have been hit by the gang.
The largest payment was $9 million, while the average ransom payment was $1.2 million, according to joint research published by blockchain tracking company Elliptic and cyber insurance provider Corvus Insurance.
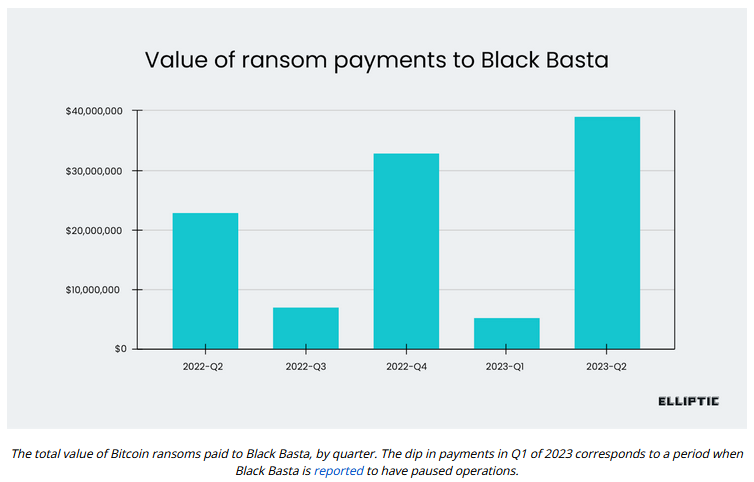
Although all ransomware "earnings" estimates are extremely inaccurate, this would put Black Basta in the upper echelon of the "best-earning" ransomware groups of the past years.
- Ryuk – $150 million
- REvil – $123 million in 2020
- Lockbit - $91 million from January 2020 to June 2023 (US only)
- Darkside – $90 million between October 2020 and May 2021
- Maze/Egregor – $75 million
- Cuba - $43.9 million throughout 2021
- Conti - $25.5 million between July and November 2021
- Netwalker – $25 million between March and July 2020
- Dharma - $24 million between November 2016 and November 2019
The group itself began operations in early 2022. The group appeared shortly after the implosion of the Conti group, itself a Ryuk rebrand.
It is widely believed in the infosec community that former members of the Conti gang splintered off and created multiple ransomware gangs after the gang's demise in early 2022—precipitated by a dox of Conti operations, itself caused by Conti admins proclaiming their allegiance to Russia following its invasion of Ukraine.
Together with Akira, BlackSuit, and Royal, Black Basta is one of the four main post-Conti ransomware gangs (as per independent security experts, RedSense, IBM X-Force, Trend Micro, and NCC Group).
In its dying days, Conti denied any affiliation with the group, which is why some companies still don't track Black Basta as a Conti offshoot. With the Conti source code leaked online, they might be right, or they might have been trying to sabotage an unwanted competitor—we'll never know.
While the gang advertised its Ransomware-as-a-Service portal in underground forums for weeks, the first actual Black Basta attacks were spotted in the wild in April 2022, when the group's ransomware strain was also detected.
Since then, the gang's tactics have revolved around two ways of breaching their victims. The first relies on exploiting recently patched vulnerabilities in networking and enterprise applications (i.e., CitrixBleed, PrintNightmare, ZeroLogon, etc.). The second relies on buying access to corporate networks infected by other malware gangs (i.e., SystemBC, PikaBot, Qakbot).
A SentinelOne report claims Black Basta may have also started working with the FIN7 threat actor or at least recruited former FIN7 developers. With the cybercrime ecosystem being a mess of shady connections and a limited coding talent pool, this isn't that hard to believe.
As for its activities, the gang has been extremely proficient. Its activity can be described as a mix of large pulses of attacks and periods of total quiet. In some months, Black Basta has been one of the Top 5 most active groups, while in others, they have been nowhere to be found, spurring rumors of a possible shutdown.
Some of the gang's biggest victims include UK outsourcing giant Capita, German arms manufacturer Rheinmetall, industrial automation company ABB, food retail giant Sobeys, and, more recently, the Toronto Public Library.
Elliptic and Corvus note that many of the gang's successful extortions were laundered through Garantex, a sanctioned Russian cryptocurrency exchange. The same exchange was previously used by the Conti gang to launder its funds as well.
Putting inaccurate estimates on ransomware gangs might sound like a waste of time, but these numbers often inform law enforcement agencies of the biggest threats they might want to target. So, let's keep them coming.
For technical reports on the Black Basta crew, visit their Malpedia page.
Breaches, hacks, and security incidents
Okta data breach: Okta says that the hackers who breached its customer support system in October stole data on all its customers. The company says that some of its own employee information was also accessed. Initially, Okta said that only 1% of its customers had data stolen. The company is currently notifying all customers via email and asking organizations to enable MFA for their Okta admin accounts.
Staples incident: Office supply retail chain Staples took down some of its IT systems to contain a cybersecurity incident. The company says it is restoring affected systems, but the incident is affecting its ability to process and deliver orders via its official website. Staples did not say if it is facing a ransomware attack and directed customers to its stores for urgent orders. [h/t EoA]
JAXA hack: A threat actor has breached the Japan Aerospace Exploration Agency after exploiting a vulnerability in a network device. According to Japanese media, the hack took place over the summer but JAXA didn't notice the intrusion and only recently learned of the breach from law enforcement. The agency says the hacked systems did not contain information on its rocket and space technology. [Additional coverage in Nippon]
Dollar Tree breach: The personal details of almost 2 million Dollar Tree users were stolen during a security breach at one of the retail chain's subcontractors. Dollar Tree is a Fortune 500 company that operates more than 15,000 discount-price stores across the US and Canada.
Capital Health incidents: A cybersecurity incident that took place during Thanksgiving is impacting the activities at hospitals operated by US provider Capital Health. Hospitals in New Jersey and Pennsylvania are experiencing network outages following the attack. The incident comes as hospitals owned by Ardent Health in six states are seeing similar issues.
KyberSwap hack: The hacker who stole $55 million (updated from $46 million) worth of crypto assets from the KyberSwap exchange posted their conditions for returning the stolen assets. The tl;dr is that they want the current leadership ousted and control over the entire platform, which is unlikely to happen.
General tech and privacy
Plex privacy disaster: Plex media server users are receiving "week in review" reports with what their friends have been watching on their devices. The reports have stirred quite a controversy, as it exposes some users' porn preferences. [Additional coverage in 404 Media]
Rivian snafu: Car software maker Rivian fixed a buggy firmware update that bricked 3% of the company's infotainment systems. The company blamed the bug on a bad certificate. Rivian said it tested the firmware update on more than 1,000 vehicles before it went out, but the bug did not show up in tests. [Additional coverage in Electrek]
New meme TLD: Google has released a new .meme top-level domain. Lets hope they stick with it this time and don't dump it on another company like they did with .zip.
RETVec: Google has developed and provided more details on a system called RETVec that the company has been using inside Gmail to detect spam and malicious emails. The tool was also open-sourced on GitHub.
"RETVec is trained to be resilient against character-level manipulations including insertion, deletion, typos, homoglyphs, LEET substitution, and more. The RETVec model is trained on top of a novel character encoder which can encode all UTF-8 characters and words efficiently. Thus, RETVec works out-of-the-box on over 100 languages without the need for a lookup table or fixed vocabulary size."
WhatsApp Secret Code: Meta has rolled out a new feature named WhatsApp Secret Code that lets users lock and put sensitive conversations behind a password prompt.
"Secret code starts rolling out today, and in the coming months will be available globally."
Government, politics, and policy
CISA issues first SbD alert: CISA has published its first-ever "Secure by Design" alert. The first SbD document urges software vendors to take action and design more secure web management interfaces. CISA recommendations include disabling a product's web management interface by default and configuring products to stop operating when the web management interface is exposed on the internet. Umm... that's bold!
French govt bans foreign E2EE apps: France has banned government officials from using foreign encrypted messaging services like Telegram, Signal, and WhatsApp. The government is notifying ministers and their cabinet staff that they have to uninstall the apps from their devices by December 8. Instead, French officials have been told to use locally-developed alternatives like Tchap and Olvid. Officials cited privacy risks and a need to "advance towards greater French technological sovereignty." [Additional coverage in Le Figaro]
Spyware in Canada: Thirteen Canadian government agencies and federal departments have access to spyware and hacking tools, according to documents obtained by Radio-Canada. The list includes law enforcement agencies but also departments that deal with environmental protection, climate change, and natural resources. The tools have features that can recover and analyze data found on computers, tablets, and mobile phones. Some tools can recover data from cloud services, and some can recover encrypted and password-protected information. Suppliers include companies like Cellebrite, Magnet Forensics, and Grayshift. [Additional coverage in CBC]

Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Corelight CEO Brian Dye about the value of data from NDR tools when it comes to long-term incident response.
Cybercrime and threat intel
HackingTeam founder arrested for attempted murder: The founder of the now-defunct spyware maker HackingTeam was arrested in Italy. David Vincenzetti was detained by authorities over the weekend after allegedly stabbing a family member. After rambling in court, a judge ordered Vincenzetti to be analyzed for mental health issues. [Additional coverage in TechCrunch]
SSNDOB admin sentenced: A US judge has sentenced a Ukrainian national to eight years in prison for running SSNDOB, an online marketplace that sold the personal information of more than 24 million Americans. Vitalii Chychasov was arrested in March 2022 while attempting to enter Hungary and was extradited to the US in July 2022 when the FBI also seized the SSNDOB portals. Officials say Chychasov made $19 million from running SSNDOB, which ran on five different domains.
Money launderer sentenced: A Florida judge has sentenced an Indian national to four years and three months in prison for laundering money for an Indian call center network. The call center network posed as IRS and FBI agents in a scheme that threatened US citizens with arrests unless they paid a fine to one of their accounts. Officials say Jignesh Purshottambhai Vekaria worked throughout 2018 to transfer funds collected in the US to his accomplices in India.
US seizes Sinbad mixer: The US government has sanctioned and seized Sinbad, a cryptocurrency mixing service. The service was used by North Korean hackers to launder funds stolen from cryptocurrency platforms like Horizon Bridge, Axie Infinity, Stake, FTX, BadgerDAO, CoinEx, and Atomic wallet owners. US officials say the service was also used to obfuscate transactions linked to sanctions evasion, drug trafficking, and the purchase of child sexual abuse materials. Sinbad launched in February this year and is believed to be a rebrand of Blender, another cryptocurrency mixing service. Blender was sanctioned by the US Treasury in May 2022, also for helping North Korean hackers launder stolen funds.

CISA warns of Unitronics exploitation: CISA is warning that a threat actor is most likely exploiting weak passwords to take control of Unitronics PLCs used in the US water management sector. The agency is asking organizations to enable MFA and remove the devices from the internet or place them behind a firewall. While CISA did not name the threat actor, they are most likely referring to an Iranian hacktivist group known as Cyber Av3ngers. The group hacked water pumps in the town of Aliquippa, Pennsylvania, last week after exploiting Unitronics PLCs.
Cactus Qlik exploitation: The Cactus ransomware gang is exploiting three vulnerabilities in Qlik Sense business analytics servers for initial access to corporate networks. All three vulnerabilities were discovered by security firm Praetorian and patched in August and September this year. Security firm ArcticWolf spotted the attacks on Qlik servers, which appear to have begun this week.
Rare Wolf: Russian security firm BI.ZONE looks at the tactics of Rare Wolf, a threat actor targeting Russian users and organizations.
Shadow/Comet/Twelve: Russian security firm FACCT analyzes a cybercrime group that has been known to go under different names, such as Shadow, Comet, and Twelve. The group is known for carrying ransomware attacks on Russian companies. FACCT says the group's most recent victim is a factory of one of Russia's semiconductor companies.
ScamClub: Malwarebytes has detected a malvertising campaign orchestrated by the ScamClub threat actor that managed to plant malicious ads on respectable sites like the Associated Press, ESPN, and CBS.
Malware technical reports
Mobile spyware cluster: Symantec looks at an Android spyware cluster. No details on whose malware is this.
FjordPhantom: Promon has discovered a new Android banking trojan named FjordPhantom that uses virtualization apps to create virtual containers and hide its malicious behavior from security tools. The malware is currently being spread through messaging spam and targets users in Southeast Asia.
Qakbot servers: Embee researchers have identified 83 servers that are part of the Qakbot botnet infrastructure. Authorities took down the botnet earlier this year, and it's unclear if the 83 servers are part of the gang's new infrastructure or leftovers from the old one. From the detection timestamps on Qakbot malware samples, they seem to be new infrastructure (but don't take my word on it since I'm an idiot about these things).
ScrubCrypt: Human has published an analysis of a recent RedLine stealer campaign employing the ScrubCrypt obfuscator.
Nova: Since September, a new infostealer named Nova has been advertised on the cybercriminal underground.
Serpent: K7 researchers look at Serpent, a new .NET infostealer currently advertised on underground hacking forums.
GoTitan botnet: Fortinet has discovered a new botnet named GoTitan that is currently exploiting a recently disclosed Apache ActiveMQ vulnerability tracked as CVE-2023-46604.
Lockbit ransomware: Chinese security firm Antiy looks at Lockbit, the ransomware gang that attacked the Industrial and Commercial Bank of China.
Cactus ransomware: Logpoint researchers have published a technical analysis of the Cactus ransomware.
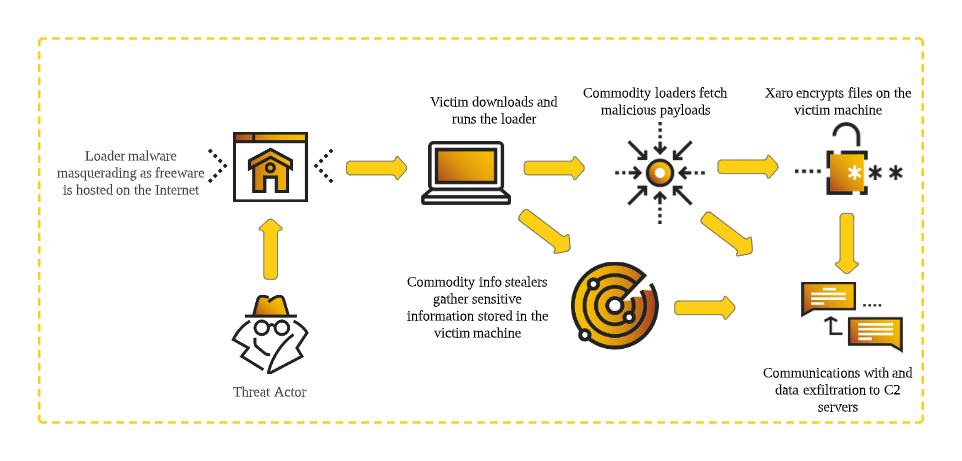
Xaro ransomware: Cybereason researchers have spotted a new version of the DejaVu ransomware that they are tracking under the name of Xaro. The ransomware is currently distributed via boobytrapped freeware apps.
Sponsor Section
This week's Risky Business newsletters are brought to you by Corelight. They maintain the open-source Zeek network security sensor/monitor. They also make very good commercial products in the network security space. Check them out at Corelight.com, or watch this video about why you need NDR as well as EDR.
APTs, cyber-espionage, and info-ops
Kimsuky: AhnLab published a report on a Kimsuky operation targeting South Korean research institutes.
DPRK crypto-heists: Recorded Future published a report on North Korea's cryptocurrency heists. The report does a good job at putting the size of these operations in context.
"North Korean threat actors were accused of stealing an estimated $1.7 billion worth of cryptocurrency in 2022 alone, a sum equivalent to approximately 5% of North Korea’s economy or 45% of its military budget. This amount is also almost 10 times more than the value of North Korea's exports in 2021, which sat at $182 million, according to the Observatory of Economic Complexity (OEC)."
SugarGh0st RAT: A suspected Chinese threat actor is targeting South Korea and Uzbekistan with SugarGh0st RAT, a modification of the open-source Gh0st RAT malware.
Patchwork: QiAnXin has published a report on the Patchwork APT (APT-Q-36) and its recent campaigns involving the Remcos and Spyder malware.
UAC-0050: Ukraine's CERT team is warning about a series of attacks against government agencies trying to install the Remcos RAT. The agency attributed the attacks to UAC-0050, a threat actor it's been tracking since 2020. Similar attacks were spotted in February and November as well.
Hellhounds: Russian security firm Positive Technologies says that a threat actor named Hellhounds has been conducting intrusions against Russian organizations. PT linked the group to at least 20 intrusions and said Hellhounds hacked and destroyed infrastructure at a Russian telecom operator. Described by the Russian telco as the "Thanos Click" [PDF], the incident resulted in the destruction of customer and billing databases and a day-long outage for the company's customers.
Meta blind to new info-ops: Meta says it's having an increasingly harder time spotting foreign inauthentic coordinated campaigns since US judges have barred US government agencies from interacting with the company. Meta head of security Nathaniel Gleicher says the company has not received any new information from US government agencies since July. Meta's statements come as the company published its quarterly threat report for Q3 2023, which includes information on three major influence operations, two of Chinese origin and one from Russia. [Additional coverage in CyberScoop / Meta report PDF]
Vulnerabilities, security research, and bug bounty
ownCloud vulnerability: GreyNoise has published an analysis of CVE-2023-49103, a recently patched ownCloud vulnerability that is being exploited in the wild. The report concludes that some strict conditions exist for vulnerability to be exploitable in the wild.
Splunk vulnerability: Uptycs has published an analysis of CVE-2023-46214, an RCE in Splunk's SIEM for which a PoC was published this week.
Zyxel security updates: Zyxel has published two waves of security updates this week to fix 15 vulnerabilities across its firewall and NAS products.
LogoFAIL: Binarly researchers have discovered a set of security vulnerabilities in image parsing libraries that are included with BIOS firmware. Named LogoFAIL, the vulnerabilities exploit a feature of BIOS firmware that allows companies to add their logo to a PC's boot-up screen. Binarly says many of these libraries are vulnerable and allow threat actors to upload malformed logo images inside the BIOS and execute malicious code to bypass Secure Boot and take over devices. Binarly says the LogoFAIL vulnerabilities can be exploited on x86 or ARM-based devices from companies like Intel, Acer, and Lenovo. It also impacts UEFI firmware produced by AMI, Insyde, and Phoenix.
Apple zero-days: Apple has patched two WebKit zero-days that were exploited in the wild. The two are tracked as CVE-2023-42916 and CVE-2023-42917. Updates are availble for both iOS and macOS.
Infosec industry
Google cybersecurity training: Google announced a $10 million investment in cybersecurity training programs across Europe. The program will provide universities with a cybersecurity training program and curriculum for their students. Eight universities in eight different European countries will receive funding of up to $1 million to get their cybersecurity courses started. Other universities can also apply. Google launched a center in Malaga, Spain, to coordinate the effort and will be working with the European Cyber Conflict Research Incubator CIC, a UK-based non-profit. Earlier this year, Google also committed more than $20 million to the creation of cybersecurity clinics at 20 higher education institutions across the US.
New tool—AWS Kill Switch: Robinhood security engineer Jeffrey Lyon has open-sourced AWS Kill Switch, a tool that can be used during security incidents to delete or contain other AWS accounts.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the latest Russian cyber attacks on the Ukrainian energy grid.




