Australia's Equifax Moment
PLUS: Russian hacktivists are being directed by the GRU
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray and supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.
Australia's Equifax Moment
Optus, Australia's second largest telecommunications provider, suffered a significant breach last week that resulted in the loss of 11.2 million customer records which were then offered for sale on a cybercrime forum. Although the attacker now claims to have deleted the data, this incident will have a big impact on the Australian regulatory and cyber security landscape.
As best we can tell, the attack was far from sophisticated. The attacker, known as "Optusdata" on the Breached cybercrime forum, reportedly used an unauthenticated API call to api.www[dot]optus.com.au to scrape customer information. They were eventually detected after the high traffic volume on the API endpoint triggered a security alert inside the telco’s IT systems.
Optus described what data the attacker collected in a breach notification last week:
Information which may have been exposed includes customers’ names, dates of birth, phone numbers, email addresses, and, for a subset of customers, addresses, ID document numbers such as driver's licence or passport numbers. Payment detail and account passwords have not been compromised.
Excellent reporting from Jeremy Kirk covered Optusdata's efforts to extort Optus for a million dollars (currency not specified) in Monero cryptocurrency, and subsequent threats to release data in parcels as a way to ratchet up the pressure. The strategy was effective: Australians were constantly reminded about the threat over the last week via rolling media coverage.
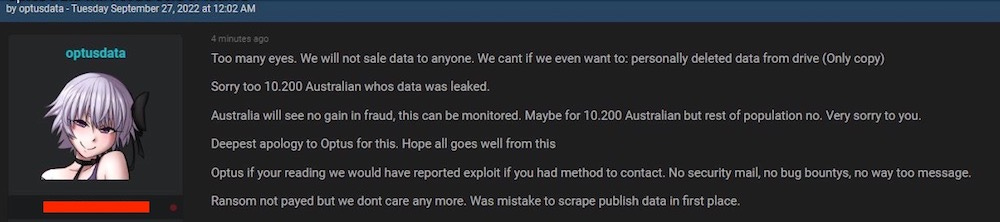
On Tuesday this week, however, the Optusdata user had a sudden change of heart, writing:
Too many eyes. [Ed: is that a FVEY reference?] We will not sale data to anyone. We cant even if want to: personally deleted data from drive (Only copy)
Sorry to the 10.200 Australian whose data was leaked.
Australia will see no gain in fraud, this can be monitored. Maybe for 10.200 Australian but for the rest of the population no. Very sorry to you.
Deepest apology to Optus for this. Hope all goes well from this.
Optus if you're reading we would have reported exploit if you had method to contact. No security mail, no bug bounties, no way too message.
Ransom not payed but we dont care any more. Was mistake to scrape publish data in first place.
Hopefully, the stolen data has been destroyed, but Optusdata's statement isn't evidence that it actually has been. Optus confirmed that it had not paid a ransom.
So. Where to from here?
It is common in Australia to prove your identity when creating new accounts by providing "100 points" of identification, where various identity documents are assigned particular point values. A driver's licence might be worth 50-70 points and a credit card 30, for example. This was originally an anti-financial crime measure, but the practice has since spread broadly in Australia across all sorts of sectors.
Optus itself requires 100 points of ID to create a new account or order a device.
In an interview with Australia's ABC, the Minister for Cyber Security Clare O'Neill explicitly highlighted risk of identify theft. O'Neill said that for 2.8 million Australians "quite extensive personal data which includes things like licence numbers and passport numbers have been taken".
Now, this doesn't mean that it's always possible to immediately use just ID numbers alone to conduct fraud, but people should be aware of the elevated risk of identity theft.
The Australian government has responded on several fronts.
The Australian Federal Police launched Operation Hurricane "to identify the criminals behind the alleged breach and to help shield Australians from identity fraud". The last couple of years the government has been building towards a more active response to cybercrime. The AFP received additional funding in the 2020 Cyber Security Strategy to build capacity to investigate and prosecute cyber criminals and it stood up a new Cyber Command at the beginning of this year.
Speaking of the Optus breach, Justine Gough, the AFP's Assistant Commissioner Cyber Crime said "criminals who use anonymising technology can’t see us but I can tell you that we can see them".
"We've had a lot of success in the past in identifying those criminals".
With assistance from ASD, which has a mandate to disrupt offshore cyber criminals, we think there are lots of opportunities for the AFP here. A low sophistication criminal could well be encouraged to stop their activities with the internet equivalent of a knock on the door: "we know who you are, so cut it out". This type of intervention is well-worth trying for a high-impact breach carried out by what looks to be a relatively unsophisticated and opportunistic individual or group. Of the various potential explanations for Optusdata's sudden change of heart, this is our favourite.
Having their OPSEC punctured would certainly be a wake-up call and could well make a cybercriminal reevaluate the risk/reward benefit. (Our second favourite hypothesis is that Optusdata's mother walked into their bedroom, found 11.2 million Optus records lying around and told them to knock it off).
As for what the impact of this whole thing will be if the data does eventually leak, Australia as a whole is already in a relatively good place when it comes to identity verification. Federal and state governments collaborate on an identity matching service that is used to confirm people's identities. The service already implements a Document Verification Service (DVS), which confirms that identity information as presented matches official records. To some extent this service will be undermined by the release of the Optus breach data — if criminals have enough of your personal details they can probably satisfy DVS checks.
In response to the breach, however, a number of state governments have said that they will issue new driver's licences. This is a change in policy and previously occurred only when an individual could prove that identity theft had already occurred.
A September 1 change to driver's licence verification procedures also mitigates the breach to some extent. For online identity matching services, all states except Queensland and Victoria now require not only the driver's licence number but also the card number, a number that changes each time a licence is reissued. (We should consider outlawing the retention of card numbers, treating them like credit card CVV values.)
These mitigations mean that — barring more large breaches — documents alone are probably going to be good enough to establish a person's identity for the time being. Waiting in the wings, however, is the Face Verification Service (FVS). The FVS goes the next step and compares a person's face to a photo on identity documents such as a passport or driver's licence. Currently, FVS use is limited to government services, but if knowledge of document numbers becomes less useful as proof of identity (because they've been leaked), faces become increasingly important.
In 2019 legislation on increasing the use of facial recognition technology for these services was knocked back by the Parliamentary Joint Committee on Intelligence and Security (PJCIS). The Committee's assessment of the legislation was withering:
The lack of detail in the IMS [Identity Matching Services] Bill has made the Committee’s review challenging…
… a citizen should be able to read a piece of legislation and know what that legislation authorises and what rights and responsibilities the citizen has in relation to that legislation. This is especially important in the case of the IMS Bill which has the potential to affect the majority of the Australian population. It is clear that the IMS Bill does not inform the citizen reader in this way.
It was a good decision by the PJCIS, and its recommendations for redrafting the IMS Bill are bang on: build a scheme around privacy and transparency, make it subject to Parliamentary oversight and require reporting on its use. Mind-boggling, really, that those features weren't there to begin with.
One proposal to emerge in direct response to this breach is to alter data breach notification rules so that companies are required to inform banks when customer details are lost. The Australian Prudential Regulation Authority has also issued a note saying "As a matter of priority, all APRA-regulated entities should harden controls on high-risk processes and transactions where possible, e.g. digital customer on-boarding, setting up first time payees etc."
The government is also signalling that it will push for larger fines after major data breaches. The Minister for Cyber Security, Clare O'Neill told the ABC that "we are probably a decade behind in privacy protections where we ought to be [and] I would say we are five years behind in cyber protections".
Federal and state governments are also rightly trying to push remediation costs onto Optus. Optus has already agreed with some state governments to reimburse costs for new licences, will pay for credit monitoring services for the most seriously affected customers and both the Prime Minister and Minister for Foreign Affairs are pushing for Optus to pay for the costs of passport renewals.
We are fans of these efforts. Part of the problem with cyber security is that companies systemically underinvest in security because many of the costs of breaches are borne by third parties. The damage to Optus's reputation here is huge, but it's only a fraction of the total damage caused. Customers and other stakeholders are left carrying the remainder of the damages bill, but why would a company pay to avoid costs that don't affect it? This is the right place for the government to align incentives with regulations to prevent screw ups, and fines when breaches result from demonstrably negligent security practices.
Greetings, Fellow Activists
Two reports this week shed light on how both Ukraine and Russia are making use of their respective hacktivist armies.
Mandiant found evidence that three Russian hacktivist groups in particular, Xaknet, Infoccentr, and the CyberArmyofRussia_Reborn are "coordinating their operations with Russian Main Intelligence Directorate (GRU)-sponsored cyber threat actors". Mandiant says:
Our assessment is based in part on the deployment of GRU-sponsored APT28 tools on the networks of Ukrainian victims, whose data was subsequently leaked on Telegram within 24 hours of wiping activity by APT28, as well as other indicators of inauthentic activity by the moderators and similarities to previous GRU information operations.
In one particular Xaknet data leak Mandiant found a APT28 artifact indicating "APT28 had access to the same parts of the network the leak was sourced from". (Risky Business News has more coverage)
On the Ukrainian side, Dutch publication de Volkskrant has an in-depth profile of "Hactic" a former Dutch commando who has been operating in the Ukraine IT Army. It makes for interesting reading, although this kind of one-person account has to be taken with a huge grain of salt.
Part of the account covers the IT Army's DDoS attacks:
With its hacking campaigns, the IT Army wants to make the war tangible for Russian citizens. Just before the weekend, cinema systems are shut down, making it impossible to buy tickets, or UberEats is shut down. Putin's speech is delayed by an hour and a half when the IT Army blocks the access system to the location. The metro in Saint Petersburg and Moscow does not function for a day. An IT Army-affiliated group invades RuTube, YouTube's Russian counterpart and a much-loved video platform. The hackers shut down the service and destroy the infrastructure. For some organizations, the damage is so great that they do not function for weeks or months.
Because the Russian war machine runs on diesel and vodka – diesel for equipment, vodka for morale – the hackers are also targeting that. A days-long attack on EGAIS, responsible for certifying and registering vodka in Russia, brought the production and distribution of alcoholic beverages to a complete standstill in early May. The transportation of Russian equipment is frustrated by the shutdown of electricity companies and the railways.
Attacks on civilian targets are problematic, although Ukraine cannot reasonably be expected to adhere to "cyber norms" when it's in an existential fight for its survival. (This recent, tone deaf Lawfare article reminds us of Amnesty's disastrous report into Ukrainian military tactics.)
Tasking volunteers is difficult. The Grugq and yours truly discussed this in the latest Between Two Nerds podcast — it is hard to find valuable targets that the IT Army has the capacity to usefully attack. Hence, attacks on vodka.
Hactic also describes an attack on Aeroflot:
Ultimately, according to Hactic, they loot passenger lists, an entire internal database and overviews of radar positions. They leave that data, which may be of interest to the Ukrainian security service, in an online portal of the SBU.
This kind of information kinda seems like it might be useful, but Aeroflot is certainly not a priority Ukrainian target in the war. Again the IT Army seems to have been told to do, well, not exactly busywork, but definitely lower priority work.
Another section describes some of the IT Army searching for harvesting credentials much like an initial access broker:
The groups search for vulnerabilities in Russian government networks, mount phishing campaigns, attempt to penetrate military and civilian organizations, copy databases, and loot usernames and passwords. They then give this to the Ukrainian security service SBU using so-called dead drops: they leave the information in a designated online portal.
This could make sense, providing an initial head start but leaving more sensitive work to real intelligence agencies. But overall the entire account reinforces our view that perhaps the major value in collaborating with the IT Army is to direct it away from priority targets so that Ukraine's intelligence services have a clear shot.
Any Way You Slice It, the Viasat Hack Is a Big Deal
Kim Zetter has an interesting article exploring the impact of Russia's invasion-day hack of Ukrainian satellite communications and theorises that, contrary to previous reporting, the hack had minimal impact on Ukrainian military communications. We are sceptical, but even if this is true it doesn't diminish the significance of the operation.
The hack disrupted Viasat's KA-SAT communications by bricking ground terminals in the hours leading up to the Russian invasion of Ukraine. Victor Zhora, a senior Ukrainian cyber security official said it caused a "really huge loss in communications in the very beginning of war". Zetter, however, sought clarification from Zhora who now claims that although satellite communications were disrupted the impact was limited because satcom was only a backup communication method.
Zetter notes there is conflicting information here. A Washington Post exploration of the early days of the war reports Ukrainian Colonel Leonel Khoda saying "military communications were completely paralyzed" after:
…the Russians completely jammed the Ukrainians’ communications and satellite networks, leaving Khoda and others without a link to front-line soldiers. Ukrainian commanders moved around to their troops’ positions to communicate and issue orders.
Zhora now claims that landlines were the primary military communication method, which is somewhat perplexing because landlines certainly aren't useful for forces in the field, like frontline soldiers fighting a Russian invasion. Broadly speaking, forces in the field have just three practical communications options: radios, mobile phones or satellite comms. For the Russians, removing one leg of this triad is certainly a win and left the Ukrainian military with fewer communication options and less redundancy. In areas without mobile phone coverage, for example, the Ukrainians were entirely reliant on radio communications that could be (and were!) jammed by Russian electronic warfare units. And it strikes us that we'd never describe an attack that disarmed one leg of the nuclear triad [Ed: This is the most American website we've ever seen] as 'low impact', even if, say, ICBMs and submarines were still available for redundancy.
Regardless of the precise battlefield impact of the Viasat hack, it is still the best example of a wartime cyber operation. It was coordinated with other conventional military action and it is easy to see how it contributed to Russia's strategic goals. It just needed to be combined with a telecommunications attack at the same time. Even if other teams weren't effective at accomplishing those goals — disruption of radio comms via EW, taking out cell towers or related infrastructure — the Viasat operation still achieved its aims and is a massively significant event.
Three Reasons to be Cheerful this Week:
- Enhanced phishing protection comes to Windows 11: the latest version of Windows 11 contains phishing protection features for enterprise users. Windows looks for passwords being entered and can detect password reuse, corporate passwords being entered into reported phishing sites, and even the storage of passwords in unencrypted files. Seems like a feature worth turning on.
- UK Police round up the usual suspect: The 17-year old allegedly responsible for recent hacks of Rockstar Games and Uber has been arrested by City of London Police. This is the teen's second arrest and Eurogamer reports he was previously arrested in March last year.
- Quad ransomware steps: The foreign ministers of the Quad (Australia, India, Japan and the US) issued a joint statement on tackling ransomware. It's easy to be cynical about these statements because in the short term they achieve absolutely nothing. Ransomware is a transnational problem, however, and getting more high-level focus from more governments will make a difference in the longer term.
Sponsor Section
A recent Proofpoint report examines an Iran-aligned threat actor TA453's use of a technique that it calls "Multi-Persona Impersonation" or MPI. Rather than trying to socially engineer a victim with a single persona, TA453 introduces a second attacker-controlled persona, often by cc'ing them into an ongoing email conversation in the cases that Proofpoint has seen. MPI leverages "the psychology principle of social proof to prey upon its targets and increase the authenticity of the threat actor's spear phishing".
Analysing Files to identify threats with Stairwell's Inception platform
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In our latest demo, Mike Wiacek shows Patrick Gray how to hunt down and triage suspicious files within your enterprise using Stairwell's file analysis and threat detection platform.
Shorts
China is building Cyber Ranges
The Center for Security and Emerging Technology has a report on Chinese cyber ranges, which it says are being built at a rapid clip. From the executive summary:
China is rapidly building cyber ranges that allow cybersecurity teams to test new tools, practice attack and defense, and evaluate the cybersecurity of a particular product or service. Nineteen of China’s 34 provinces are building, or have built, such facilities. Their purposes span from academic to national defense. In short, the presence of these facilities suggests a concerted effort on the part of the government, in partnership with industry and academia, to advance technological research and upskill its cybersecurity workforce—more evidence that China has entered near-peer status in the cyber domain.
The ranges are evidence that China is keen on investing even more into cyber capabilities, but this newsletter isn't convinced that it provides any indication at all of relative strength compared to the US. Is it a near-peer of the US? US OPSEC makes it very hard to get any idea of relative strength.
Chinese cyber operations have often been effective but noisy. Our fear is that these ranges will educate cyber forces so that they become effective and quiet.
German BSI Late to the Kaspersky Party
The German Federal Office for Information Security (BSI) has issued a statement warning about the use of Kaspersky antivirus software:
The actions of military and/or intelligence forces in Russia and the threats made by Russia against the EU, NATO and the Federal Republic of Germany in the course of the current military conflict are associated with a considerable risk of a successful IT attack. A Russian IT manufacturer can carry out offensive operations itself, be forced to attack target systems against its will, or be spied on without its knowledge as a victim of a cyber operation, or be misused as a tool for attacks against its own customers.
This is entirely correct, but of course the trick is to mitigate this kind of risk well before war breaks out. Keeping this in mind we have a short quiz for the German readers of this newsletter:
- Kaspersky is to Russia as Huawei is to _____
- Ukraine is to Russia as Taiwan is to _____
But so far it looks like Germany is quite happy to assume that kind of critical infrastructure risk. Understandable really, since German reliance on Russian gas via NordStream is really paying off.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss how Ukraine could actually make use of the IT Army.
From Risky Biz News:
Signal asks users to help Iranians: Secure messaging app Signal has asked its users to set up and run proxy servers and help Iranians connect to the Signal service, currently blocked inside the country following massive public protests. A ready-made server setup is also available on GitHub.
Kaspersky faces possible ban across the EU: Bloomberg reported on Friday that five countries (Latvia, Lithuania, Estonia, Ireland, and Poland) are pushing for a new set of sanctions against Russia, including a possible ban on Russian cybersecurity firm Kaspersky.
Exchange servers compromised for spam operations: Microsoft has a report out on a clever campaign where attackers compromise Azure tenant accounts through stolen credentials, install an OAuth app on the account, grant the app permission to interact with the server's underlying Exchange email server module, and then use this server as a proxy to relay spam campaigns via "clean servers." Pretty clever stuff, tbh.



