After Viasat, Space Systems Get Scrutiny
PLUS: Cyber Disaster Relief Is Going to Be a Thing
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.

The CSC 2.0 project — which aims to continue the work of the US Government's Cyberspace Solarium Commission — has recommended that the US government designate space systems as critical infrastructure.
The project's report argues that the space sector is increasingly important but also increasingly under threat from adversary states:
Space systems serve fundamental roles in national security and economic prosperity and are at risk of disruption. These risks stem from adversarial nations intent on causing harm to the United States and its partners and allies and are amplified by legacy technologies and the unique challenges of space.
On the importance side, the report notes that space underpins a variety of other critical infrastructure sectors. Space services such as positioning, navigation and timing are used across diverse critical infrastructure sectors such as energy, water, telecommunications, transportation, agriculture, and even financial systems.
On the threat side of the equation, both Russia and China have used real-world and cyber operations to target satellite systems. Both have successfully tested anti-satellite missiles and have also penetrated satellite networks with cyber operations — Russia's disruption of Viasat's KA-SAT network is a notable example. The commercial satellite network Starlink has also been critical for Ukrainian defenders and has become a target of Russian disruption efforts.
Despite all this, there's still an argument for maintaining the status quo. Many components of the space sector are already designated as critical infrastructure because they fall within the scope of other sectors:
Commercial communications satellites are considered part of the communications sector, while military reconnaissance satellites and GPS systems are part of the DIB [Defense Industrial Base]. Meanwhile, the critical manufacturing sector includes aerospace parts and manufacturing, while the Federal Aviation Administration governs launch and re-entry from space as part of the transportation sector.
Some experts also told CSC 2.0 that CISA and the Department of Defense are already doing a good job as sector risk management agencies. So if it ain't broke, why fix it?
Leaving aside whether CISA and DoD were doing a good job, important components of the space sector aren't covered as critical infrastructure. CSC 2.0 identified gaps that were not covered in either the communication or DIB sector, particularly in commercial remote sensing enterprises such as "those used for scientific and other research purposes, including weather tracking and forecasting systems". It also notes the potential for growth in other uncovered areas including in "emerging space-based systems for transportation, remote sensing, manufacturing, mining, and cislunar operations".
CSC 2.0 also cites a 2022 MITRE and Aspen Institute report into the space industry which found that although the status quo may work for some parts of the space industry, for the sector as a whole it's not working:
Currently, commercial space operators seeking approval of space operations must adhere to several distinct regulatory policies and procedures and must engage with several different government agencies, including the Federal Communications Commission, the Federal Aviation Administration, and the Department of Commerce. This reduces the speed and flexibility with which U.S. companies can bring innovative technology to bear. It also increases risks to space mission operations and to the space domain.
The report's recommendation that NASA serve as the sector risk management agency is key. Getting CISA or DoD to do more would spread available expertise more thinly. This would match the required expertise — in space-related stuff — to the managing agency. This report says that more funding for NASA will be "imperative", though, "because policy without resources is merely rhetoric".
Designating the space sector as critical infrastructure also has a signalling value. It tells people — both domestically and internationally — that space security and resilience is important. Although it is hard to put a dollar value on that type of signal, we think it worthwhile given that adversary states are one of the main concerns.
Cyber Disaster Relief Is Going to Be a Thing
The US State Department is working with Congress to develop a cyber aid program.
At recent events, the US's Cyberspace and Digital Policy Ambassador, Nathaniel Fick, has talked about the need for an emergency assistance fund, modernising and expanding capacity-building efforts, and also cyber literacy efforts.
The US has already pledged USD$25m each in assistance to both Costa Rica and Albania to help them recover from separate cyber attacks, after Costa Rica was hit by Conti ransomware and Albania by Iranian state-backed groups.
From a US government perspective, it makes sense to fill out the "portfolio" of cyber products it can use to engage other countries.
US Cyber Command already conducts hunt forward operations which find and disrupt adversary activity on partner networks. This addresses a particular Cyber Command interest in imposing costs on adversaries wherever possible, but US government interests as a whole are far broader than that. And there are also sensitivities that may make some countries cautious about inviting the US military onto critical networks.
A funded program of work operating out of the State Department would help to both win friends and influence countries while at the same time improving cyber security. What's not to like?
Have We Tried Just Asking Nicely?
An international coalition of cyber security authorities – including CISA, the FBI, and all Five Eyes cyber security agencies — have released a document advocating a shift to building products with "Security-by-Design and Default".
This reinforces the message in the recent US National Cybersecurity Strategy that manufacturers should be on the hook for developing insecure products, and the interesting thing here is that the document sets a very high bar.
It encourages manufacturers to "build their products in a way that prevents customers from having to constantly perform monitoring, routine updates, and damage control on their systems to mitigate cyber intrusions".
Other suggestions are also heretical. It suggests that rather than issuing hardening guides, which can be "a roadmap for adversaries to pinpoint and exploit insecure features", products should be installed in a highly secure way by default. Manufacturers should release "loosening guides" which would explain the security implications of enabling additional features.
It's a high bar, and it is a very long way from where standard practice is currently. Encouraging documents won't do much to change the status quo by themselves, but the document flags the direction these governments want software makers to move in. Considering the noises they've been making about regulation lately, we suggest tech pays attention.
Three Reasons to be Cheerful this Week:
- WhatsApp Security Upgrades: Meta announced three separate security improvements to WhatsApp that cover account, device and encryption security. Our favourite is "Device Verification", which makes it harder for on-device malware to steal WhatsApp authentication keys and impersonate users on a new device. The technique uses a rolling security token that is updated whenever a WhatsApp client responds to new message notifications.
- Lawyers tackle Cobalt Strike abuse: A coalition or organisations are taking legal action to disrupt the use of Cobalt Strike "adversary emulation" i.e. hacking software, by cybercriminals. Cobalt Strike is legitimate commercial software used by red teams, but legacy and cracked versions are abused by cybercriminals. Similar previous legal actions have focussed narrowly on malware command and control, but this more broadly targets infrastructure used by 16 "John Doe" cybercriminal groups including LockBit, EvilCorp and Conti. The coalition includes Microsoft, Cobalt Strike manufacturer Fortra, and Health-ISAC. According to Microsoft's announcement, cracked copies of Cobalt Strike have been linked to more than 68 healthcare ransomware attacks in more than 19 countries. [more at Risky Biz News]
- Evidence Apple's iOS Lockdown mode worked: Citizen Lab reports NSO Group used three different iOS "zero-click" or no-interaction exploit chains in 2022. The good news is that it was able to confirm that iOS's Lockdown mode prevented one of these exploit chains and even warned users when exploitation of their devices was attempted.
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and corporate sponsor Proofpoint.
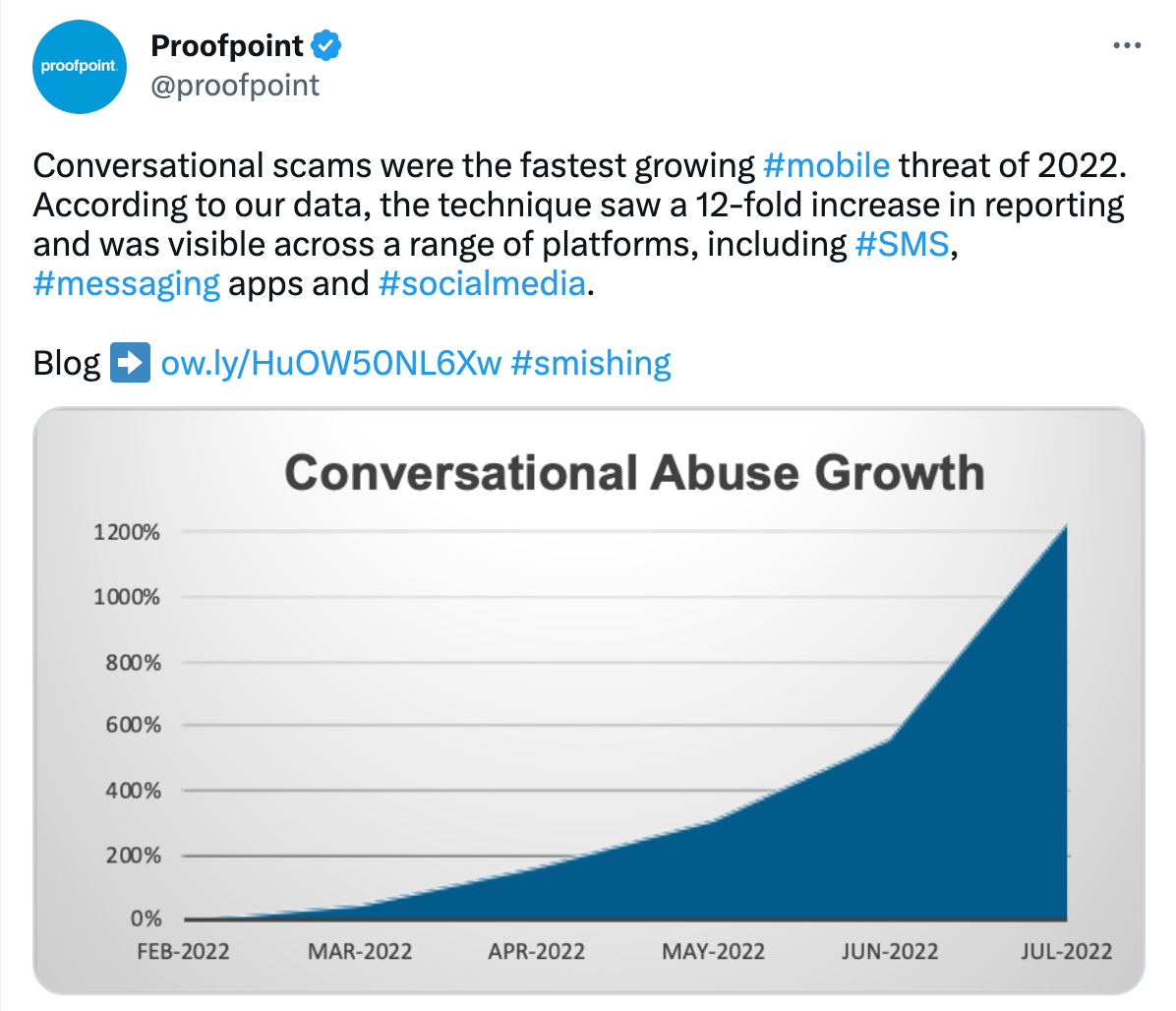
Proofpoint finds that "pig butchering" and conversational attacks are the fastest growing mobile threats of 2022.
Tines No-code Automation For Security Teams
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In this video demo, Tines CEO and co-founder, Eoin Hinchy, demonstrates the Tines automation platform to host Patrick Gray.
Shorts
A Short History of Crime Phones
The New Yorker has a great long read on law enforcement success against encrypted crimephones. It mostly focuses on the busts of Encrochat and Sky ECC, but the FBI-run An0m app also gets a brief mention. There's some good stuff in there and what the busts reveal about official corruption and organised crime is sobering.
No More Fuzzy Capybaras?
Microsoft has announced a new threat actor naming taxonomy. All names are two words, with the first word being a descriptor indicating a specific group and the second word being a weather event that associates groups to "families". Chinese groups are "Typhoon", Russian are "Blizzard", financially motivated are "Tempest" and so on.
So Strontium, aka APT28 or Fancy Bear and attributed to Russian military intelligence, is now known as Forest Blizzard. Microsoft have released a guide that contains a table converting from old to new names.
Sandstorm Wrecks Cloud
Microsoft reports that Iranian threat actor Mango Sandstorm, previously known as Mercury and linked to the Iranian government, conducted destructive attacks on both the on-premise and cloud portion of organisations. Patrick and Adam discuss this on the Risky Business podcast (at 12:40), and Adam thinks these approaches will trickle down to cybercriminal and ransomware groups.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss the UK National Cyber Force's "Responsible Cyber Power in Practice" document. It explains how the NCF uses offensive cyber operations to f*ck with people.
From Risky Biz News:
Israeli spyware vendor QuaDream has allegedly shut down: Joint reports from Microsoft and CitizenLab have blown the lid on another Israeli cyber-surveillance vendor, a company named QuaDream. These reports provide the first technical details about QuaDream's iOS hacking capabilities — a spyware tool named KingsPawn.
According to the two companies, KingsPawn was deployed using "invisible iCloud calendar invitations" sent by QuaDream customers to their targets. The invites used an exploit for iOS 14 named ENDOFDAYS to deploy KingsPawn on the device, and then used KingsPawn to exfiltrate data, track victims, and hack their online accounts. [more at Risky Biz News]
Cyber-attack on irrigation systems: A cyber-attack is suspected of having disrupted the operations of irrigation systems in Israel's Upper Galilee region. Water controllers for irrigating fields in the Jordan Valley and control systems for the Galil Sewage Corporation were down last week during yearly cyberattacks aimed at Israeli targets known as OpsIsrael. While several hacktivist groups announced their participation in OpsIsrael this year, the identity of the attacker remains unknown, the Jerusalem Post reported.
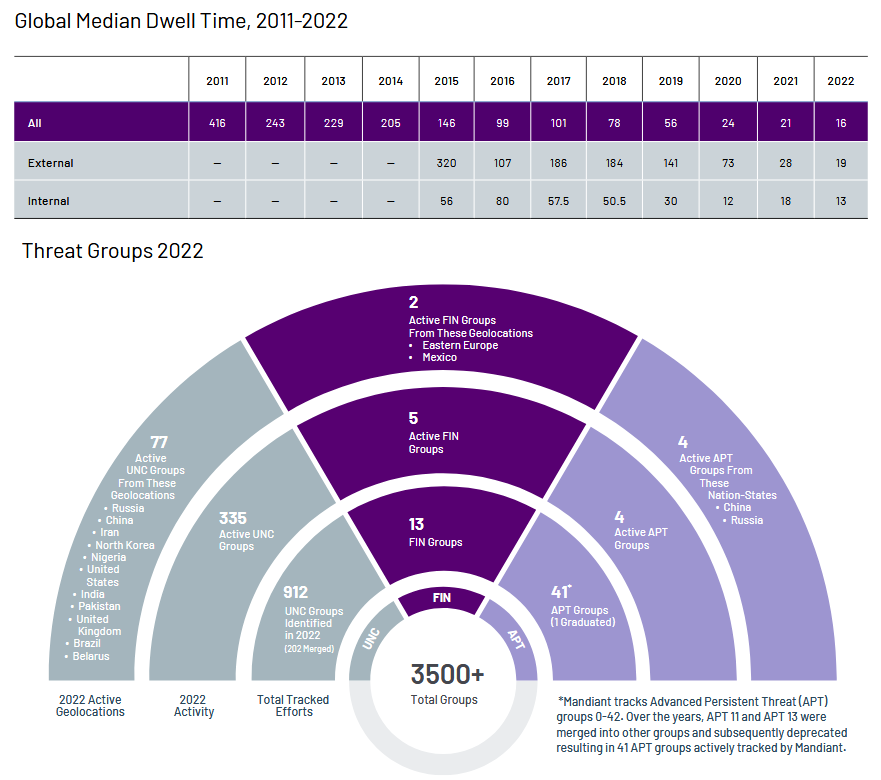
Mandiant M-Trends report: The median dwell time of an attacker inside a compromised network went down to 16 days last year, according to M-Trends 2023, a report compiled by Mandiant from data from its frontline incident response teams. The number has gone down from 21 days in 2021 and down from 416 days in 2011, suggesting companies have gotten better at detecting threat actors inside their networks. Mandiant's dwell time is similar to the 11-day dwell time reported by Secureworks in its own yearly report, published last October. The Mandiant report also covers other topics, such as initial access (with vulnerability exploitation and phishing being top entry points) and top malware families (where Cobalt Strike was king with 15% of all detections).