Risky Biz News: 1Password joins the list of Okta victims
In other news: Australia and Microsoft partner to build country's cyber shield; September was a record month for ransomware gangs; and major breach at the University of Michigan.
This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Password management service 1Password has joined the list of companies that have been impacted by a recent security breach at identity provider Okta.
1Password becomes the third company known to be affected by the Okta breach—after BeyondTrust and Cloudflare.
The Okta incident is the second major hack the company disclosed after a January 2022 incident when 366 companies had their Okta environments accessed.
This time around, we don't have a headcount for the hack just yet, but the incident is starting to look just as bad.
From public statements made by Okta, BeyondTrust, Cloudflare, and 1Password, the hack seems to have taken place somewhere at the end of September.
Okta says a threat actor used "stolen credentials" to access the account of one of its tech support engineers.
The hacker then used this account to look at tech support requests filed by Okta customers, most of which are major companies that use Okta's identity services to manage user logins into sensitive environments.
These tech support requests typically don't contain that much sensitive information, except when Okta asks customers to capture their browser traffic in the form of an HTTP Archive (HAR) file and upload it to their support case.
Okta says that some of these files contained copies of a company's Okta admin account session cookie, which the attacker extracted from the HAR and used to access customers' Okta management instance.
Luckily for Okta, some companies like BeyondTrust and 1Password spotted the attackers trying to log into their environments with the stolen session cookies. It's unclear how BeyondTrust spotted the intrusion, but 1Password said they spotted the attacker when it generated a report that compiled a list of all 1Password Okta admins, something that none of their staff requested.
So far, the three companies say they spotted the intruder in their Okta instance in early phases of reconnaissance, and none have seen the attacker pivot to internal systems.
Despite the happy ending for the three companies, all have put out statements that were extremely annoyed with Okta's slow response to the breach.
BeyondTrust says it notified Okta on October 2, but it took the company 16 days to investigate and publicly acknowledge the breach; time that several security experts claim could have helped other Okta customers carry out their own investigations at the time of the breach rather than two weeks later.
Breaches, hacks, and security incidents
AlfaBank hack: The Ukrainian Security Service has collaborated with two pro-Ukrainian hacking groups to breach Alfa Bank, one of Russia's largest banks. The hack took place last week and involved members of the KibOrg and NLB hacking groups. The two groups claim to have stolen data for 30 million Alfa Bank customers and have leaked some of the stolen files. The bank denied getting breached in a statement released to Russian media. Ukrainian security officials did not elaborate on the role they played in the hack. [Additional coverage in The Record]
University of Michigan breach: The University of Michigan has disclosed a security breach after hackers broke into its internal servers at the end of August. The organization says it detected the incident but not before the intruder accessed information on employees, students, alumni, donors, and contractors. The University of Michigan is one of the oldest and largest universities in the US, ranked 11th by 2022's enrollment numbers.
Gardai leak: Thousands of Irish drivers have had their driver's license information leaked online after the Irish Gardai left a server exposed on the internet. The server leaked PII data, but also leaked details of insurance investigations, vehicle registration certificates, notices of car seizures, and payment card details. The leak was traced at one of the agency's IT suppliers. [Additional coverage in the Irish Independent]
DDoS attacks on Israel: Cloudflare says it spotted DDoS attacks against Israel's rocket warning alerting system as fast as 12 minutes after Hamas launched missiles at Israeli cities on October 7, the day of their attack.
Hope Lend crypto-heist: A threat actor has stolen more than $825,000 worth of crypto-assets from the Hope Lend DeFi platform. The incident is surrounded by controversy because several security firms claim that a white hat managed to beat the attacker to the exploit and is actually now in control of the funds. On the other hand, the Hope Lend developer claims the attacker paid half of the stolen funds as a bribe to a transaction validator to process the malicious transaction and that the money is now gone. [Additional coverage in Cointelegraph]
General tech and privacy
Map apps in Israel: Apple and Google have disabled their live traffic data in their map apps in Israel at the request of the Tel Aviv government. [Additional coverage in Engadget]
Chrome to get IP protection feature: Google is working on adding a feature to its Chrome browser that will hide a user's IP address behind a network of proxies. Named IP Protection, the feature is currently being tested in Chrome Canary builds. In its initial phase, the feature will use a one-hop proxy, but Google says it is aiming for a two-hop proxy system that will be harder to deanonymize. [Additional coverage in BleepingComputer]
Firefox 119: Mozilla has released Firefox 119. New features and security fixes are included. The biggest change in this release is the ability to edit PDFs.
Government, politics, and policy
Global Encryption Coalition: A global coalition of tech companies, academics, and privacy and cybersecurity experts have published an open letter asking governments across the world to stop trying to backdoor end-to-end encryption.
Security cameras across the Netherlands: Dutch officials are worried about the large number of wrongly adjusted security cameras across the country. More than 315,000 security cameras are installed across the Netherlands, and more than 55,000 belong to private individuals. The cameras are only allowed to film the owner's property, but officials say they often record public roads and other citizens' private property, in violation of GDPR. [Additional coverage in Security.nl]
Australia to get a cyber shield: Microsoft has signed an agreement with the Australian government to build a cyber shield and help the country fend off cyber-attacks. The project's official name will be the Microsoft-Australian Signals Directorate Cyber Shield, or MACS. It is a classic threat-exchange program aimed at improving the detection of threats targeting Australia. Besides MACS, Microsoft will also invest AUS$5 billion to build nine more data centers in the country, raising the total to 29.
FTC ransomware report: The US FTC has published a report on cybercrime and ransomware-related reports the agency has received over the past years. Nothing particularly interesting in this one. The FBI IC3 report provides a far better view—in our opinion—of the cyber threat landscape.
TSA security updates: The US Transportation Security Administration (TSA) announced updates to three directives regulating cybersecurity for passenger and freight railroad carriers.
CYBER.ORG donation: CISA has donated $6.8 million in funding to CYBER.ORG, a non-profit that promotes cybersecurity education in K-12 schools.
"The funding will be used to empower educators and caregivers with resources and training needed to deliver cybersecurity content to students. CYBER.ORG currently has more than 30,000 teachers across all 50 states and four US territories enrolled in its content platform, reaching millions of students nationwide."
Spamouflage in Canada: The Canadian government says that a Chinese disinformation campaign named Spamouflage is targeting lawmakers and public institutions. The operation began in early August 2023 and continued through September and rellied on Facebook and Twitter bot networks. The accounts posted content accusing Canadian politicians of criminal and ethical violations and tried to silence CCP critics. Some of the posts also used deepfaked videos.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely CEO Travis McPeak about the modern DevOps ecosystem, how giving developers tools with security baked in keeps everyone safe and happy, and how that's easier than expecting your software engineers to become cybersecurity experts overnight.
Cybercrime and threat intel
Spain arrests: Spain's National Police has dismantled a cybercrime group that made more than €3 million from online scams conducted via smishing, phishing, and vishing. Officials say the group impersonated delivery firms and electricity suppliers but also engaged in a scam known as the "son in distress." The group also stole and sold the personal data of four million people. Thirty-four suspects were detained last week across five Spanish cities.
Sachkov appeal: A Moscow court has rejected an appeal filed by former Group-IB CEO Ilya Sachkov to have his prison sentence repealed. Sachkov was sentenced in July to 14 years in a maximum security prison for high treason. Russian officials said Sachkov shared information of Russian citizens with foreign law enforcement agencies. It is believed information shared by Sachkov helped US authorities identify several Russian hackers and APT members. [Additional coverage in Interfax]
Hunters International: DataBreaches.net has an analysis of recent attacks carried out by an extortion group named Hunters International, which the site believes might be a rebrand of the Hive ransomware group.
Facebook malvertising: G Data analyzes a malvertising campaign that used Facebook ads to target users with malware.
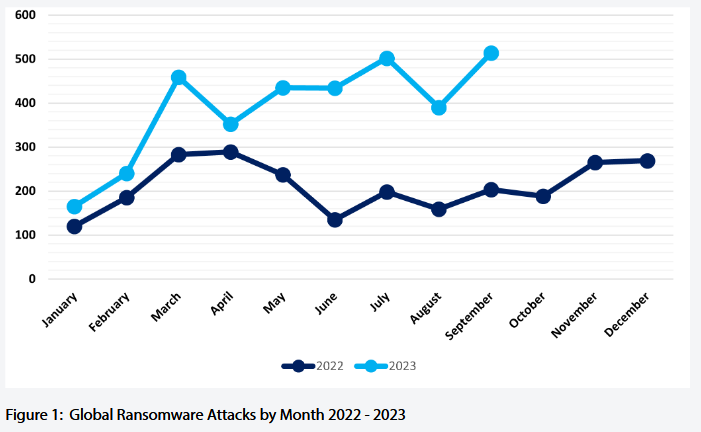
Record ransomware numbers: The month of September 2023 has been the most active month for ransomware gangs on record, with 514 disclosed attacks. September 2023 beats the previous record of 459 ransomware attacks disclosed earlier this year in March. Two groups that launched last month, LostTrust and RansomedVC, ranked in the top five of most active groups. The numbers were compiled by NCC Group using data published on ransomware leak sites.
Scammers pounce on Israel-Hamas conflict: The FBI, the IRS, the FTC, and the UK government are warning citizens to be on the lookout when donating money to Israeli or Palestinian charity organizations. The agencies warn that scammers have already set up fake organizations to collect funds from individuals looking to donate to either cause. The FBI has seen fake charity schemes advertised on social media and via encrypted messaging apps. The agency says it also received complaints of legitimate Israeli email accounts being hacked and used to solicit donations.
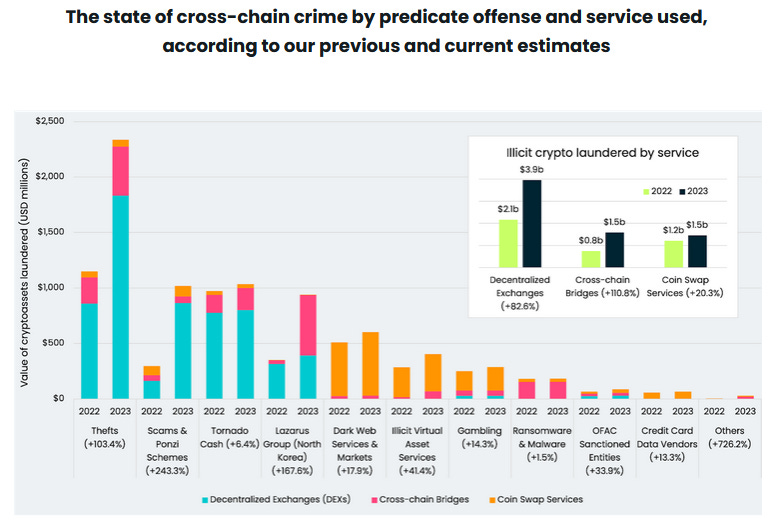
Crypto money laundering: More than $7 billion worth of crypto-assets have been laundered through cross-chain services, with $2.7 billion laundered over the past year alone. Blockchain security firm Elliptic says cross-chain crime is rising at a faster rate than predicted. The company previously estimated that cross-chain crime would reach $6.5 billion by the end of the year and $10.5 billion by 2025. More than $2 billion worth of crypto was stolen from cross-chain services this year alone, according to rival blockchain tracking service Chainalysis.
Malware technical reports
Play ransomware: Antiy researchers have published an analysis of the Play ransomware.
Mallox ransomware: Chinese security firm Tinder Security Labs has looked at attacks against MS-SQL databases with the Mallox ransomware.
Cactus ransomware: SecurityScorecard's Vlad Pasca has a technical breakdown of the Cactus ransomware, first spotted back in March 2023.
Crypto-mining botnet: Kaspersky has a breakdown of a crypto-mining botnet targeting Windows systems. Besides the crypto-mining feature, the malware used in this attack also comes with backdoor and keylogging functionality. The botnet has been active since May this year and has infected around 200 users.
Cobalt Strike: Embee has three blog posts on analyzing Cobalt Strike payloads.
GoPIX: Russian security firm Kaspersky has spotted a new banking trojan that targets the Brazilian financial sector. Named GoPIX, the malware has been active since December 2022 and targets users of the PIX money transfer system.
Grandoreiro: Proofpoint has discovered new versions of the Grandoreiro banking trojan that targets financial institutions outside Brazil. The new version has been seen targeting the users of Mexican and Spanish banks. This marks a rare instance where malware designed for Brazil's unique financial sector targets banks in the EU.
XWorm: Poland's CERT team has reverse-engineered XWorm, a popular remote access trojan.
Origin Logger: OALABS analyzes Origin Logger, a new .NET stealer and a possible clone/successor for the old and extremely popular Agent Tesla malware.
Riddle: ThreatMon looks at Riddle, a new infostealer advertised on the hacking underground, with possible ties to a Russian developer.
Sponsor Demo
Listen to Resourcely CEO Travis McPeak talk with Risky Business Snake Oilers host Patrick Gray about the company's automagic Terraform cloud-provisioning technology.

APTs and cyber-espionage
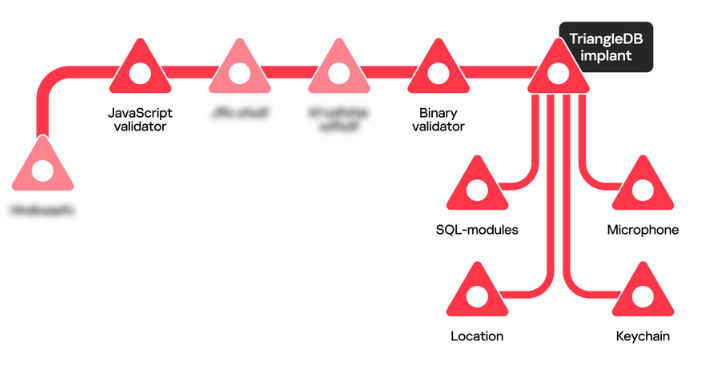
Operation Triangulation: Kaspersky researchers have published a second analysis of TriangleDB, the iOS spyware implant that was deployed part of Operation Triangulation. The operation targeted Russian government officials, foreign diplomats working in Russia, and Kaspersky employees. Russia's FSB intelligence service linked the attack to the NSA and claimed Apple cooperated with the American spy agency. The first report focused on the implant itself. The second focuses on two pre-infection components that attackers used to triage victims and four TriangleDB modules. These modules allow attackers to track the victim via GPS location data, record through the microphone as long as the battery has more than a 10% charge, and steal the device's keychain and SQLite files that store a phone's passwords and configuration data.
Vulnerabilities, security research, and bug bounty
Zcash security audit: NCC Group has conducted a security audit of the Zcash FROST protocol.
Single App Mode escape: WithSecure researchers have published details about an escape of Single App Mode, a feature that locks an iOS device to run a single application. This has no fix from Apple since the company does not consider it a vulnerability.
Orthanc vulnerability: Shielder researchers have published an analysis of CVE-2023-33466, a vulnerability in Orthanc, an open-source software to manage, exchange, and visualize medical imaging data.
"A quick lookup on Shodan (by searching for the authentication realm "Orthanc Secure Area") returned ~1700 exposed instances. We have developed a quick script to check for (probable) presence of the vulnerability here.
At the time of writing, ~20 hosts are publicly exposed with default credentials and with the arbitrary overwrite endpoint unrestricted. We urge every administrator that is using Orthanc in their systems to change the default/weak credentials and upgrade the software."
CitrixBleed: Assetnote researchers have published an analysis of CVE-2023-4966, a vulnerability in Citrix ADC and NetScaler devices that was patched on October 10. According to Mandiant, the vulnerability was exploited in the wild since the end of August. Assetnote named the vulnerability CitrixBleed because it can leak session tokens from Citrix devices and bypass authentication.
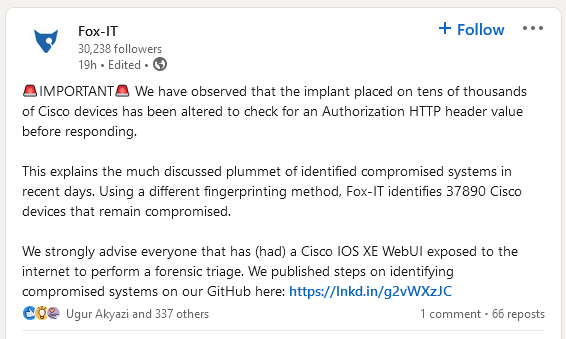
Cisco IOS XE update: The threat actor behind the attacks on Cisco IOS XE devices has added a protection mechanism (an HTTP authorization header) to the malware it planted on hacked devices. The protection mechanism has prevented some security firms from tracking the number of infected devices, but after tweaks to their scanners, it appears that ~38,000 devices are still infected. A tool to detect the new implant configuration is available here.
Infosec industry
HITB2023HKT videos: Talks from the Hack In The Box 2023 Phuket security conference, which took place back in late August, are available on YouTube.
Truesec layoffs: Cybersecurity firm Truesec has laid off some of its cybersecurity experts. Numbers are unclear so far. Still in the early reporting phase [1, 2].
Patch Tuesday anniversary: Microsoft's monthly Patch Tuesday security updates turned 20 this month, with the program having launched in October 2003.
Pwn2Own Toronto: The mobile and IoT edition of the Pwn2Own hacking contest is taking place in Toronto, Canada. See the schedule and live results.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss "spooky effects," aka when agencies play silly buggers with target computers.




