Risky Biz News: Tor Project plays down deanon attacks in Germany
In other news: US links Chinese APT botnet to Chinese tech firm; law enforcement takes down Ghost secure platform; Russian disinfo group spams newsrooms and fact-checkers.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The Tor Project says that regular Tor browser users are not affected by a deanonymization attack used by German law enforcement to catch the administrator of a dark web CSAM forum named Boystown.
German TV network NDR reported on Wednesday that German police had been secretly recording traffic entering the Tor network via nodes located in Germany over the past years.
According to technical documents obtained by NDR reporters and reviewed by security experts from Germany's infamous Chaos Computer Club (CCC), authorities used a "timing attack" to analyze traffic entering and leaving Tor nodes and correlate users visiting certain Tor sites to their real-life IP addresses.
German police then took this IP address, went to ISPs, and obtained the suspect's real name, which led to an arrest.
Per NDR, the Boystown administrator was just one of the several users who have been deanonymized this way.
But in a blog post on Wednesday, the Tor Project says the German police's attack exploited an OpSec mistake in that user's setup. Specifically, the suspect had used a very old version of the Ricochet Tor-based instant messaging service that had been end-of-life for several years and did not feature any protections against timing attacks.
The Project says that Onion routing software—at the base of the Tor network—comes with protections against timing attacks and that the users of its Tor Browser need not panic.
"To the best of our knowledge, the attacks happened between 2019-2021. [...] The attacks occurred on an old version of the long-retired application Ricochet that lacked new features The Tor Project has released since to mitigate against the kind of 'timing' analysis described in the articles. The most current versions of Ricochet-Refresh have such protections in place."
"Another important thing to mention is the longevity of the user connection for such 'timing' analysis to be successful. A Tor Browser user that does not maintain its connection for a long time, is less vulnerable to such analyses."
The Project also adds that since this deanonymization attack took place back in 2021, it has since expanded its network of nodes and improved the detection of bad relays—used for the active probing of Tor nodes in a timing attack.
The Project's explanation was backed by a similar response from Donncha Ó Cearbhaill, the Head of Security Lab at Amnesty.
The Tor Project's sudden response in a case that involved the deanonymization of a suspected pedophile rubbed some people the wrong way, but the Tor team and others have pointed out that its network is also used by innocent people in oppressive regimes and they need to be reassured they can still trust Tor to protect their identity and keep them safe.
The deanonymization news comes less than two weeks after German police allegedly raided a Tor node operator at the start of the month.
Breaches, hacks, and security incidents
Trump campaign hack: US officials say Iranian hackers tried to pass files stolen from the Trump campaign to individuals linked to the former Biden campaign. Officials say there is no evidence to suggest the individuals or the Biden campaign responded to the hackers. According to NBC News, the recipients are believed to not have even responded, thinking it was phishing.
UK victims sue Pegasus: Four people who had devices infected with the Pegasus spyware have filed a lawsuit in the UK against the NSO Group. The four victims include activists and journalists from Middle East countries. They claim NSO broke the UK's Computer Misuse Act by aiding malign actors into hacking their devices. The new lawsuit comes days after Apple filed paperwork in the US to dismiss its own NSO lawsuit.
Cencora mega-ransom: Bloomberg says pharma giant Cencora is the company that paid a massive $75 million ransom to the Dark Angels group at the start of the year. The payment represents the largest ransom ever paid to a ransomware gang. According to Bloomberg, the group initially requested $150 million to provide a decryption key and delete data stolen from the company's network. Cencora has not commented on the report.
MyPertamina leak: Indonesian authorities are investigating a breach of the MyPertamina digital financial service. A threat actor leaked the company's data online on a hacking forum in January this year. Officials have started an investigation nine months after the leak, only after the personal data of the country's president and his family was shared online. More than 6 million Indonesians are believed to have had their personal and tax ID numbers stolen in the MyPertamina hack. [Additional coverage in The Star]
General tech and privacy
FTC exposes social media surveillance: An FTC investigation has found that nine of the largest social media and video streaming services engage in "vast surveillance" of their users in order to monetize their data. The agency says the companies stored user data for long periods of time, ignored privacy protections for children and teens, and even collected data from non-users of their platforms. The companies allegedly made billions from selling data to online advertisers or through their own advertising business units. The FTC recommended that US lawmakers pass legislation to limit some of these privacy-intrusive tactics. The study investigated Twitch, Facebook, YouTube, Twitter, Snapchat, TikTok, Discord, Reddit, and WhatsApp.
LinkedIn AI shenanigans: Microsoft has secretly turned on a feature for all LinkedIn users granting itself the right to use their data to train its AI models. [Additional coverage in 404 Media/Instructions on how to turn it off in Mashable]
Cloudflare bug: Cloudflare is apparently misidentifying IPs from Hetzner as coming from Iran, leading to situations where customer firewalls are blocking legitimate traffic.
Chrome 129: Google has released version 129 of its Chrome browser. See here for security patches and webdev-related changes. The biggest changes in this release include a new useless AI feature named "Tab Compare," another useless AI feature to chat with the Gemini AI from the address bar, a new certificate manager, Chrome now blocks 0.0.0.0 to access private networks, and a new Chrome Enterprise feature named Chrome Security Insights to monitor insider risk and data loss prevention.
E2EE RCS: The GSMA says that with the release of iOS 18, which now includes support for the RCS system, it can now move on with its plans to add support for RCS end-to-end encryption.
Apple pulls iPadOS 18: Apple has pulled iPadOS 18, released this week after the update was bricking iPads running on the company's M4 chips. [Additional coverage in MacRumors]
macOS 15: Apple has released this week new versions of its mobile and desktop operating systems. The biggest haul of security-related features was included in macOS 15, also known as macOS Sequoia. The new desktop OS includes support for rotating your MAC address on WiFi networks and changes to the Gatekeeper and XProtect security systems. macOS 15 will also now prompt users every month to reauthorize apps that can record your screen. [Additional coverage in SentinelOne]
Government, politics, and policy
California AI bills: California Gov. Gavin Newsom signed three bills on the use of artificial intelligence technologies. The first of the new laws forces online platforms to remove deepfake videos for political ads. The second requires companies to obtain the consent of performers to use their digital likeness. And the third law protects deceased performers from having digital recreations of their likenesses. [Additional coverage in AP and CBS]
Pennsylvania data breach portal: The Pennsylvania OAG has launched a dedicated portal where companies can report breaches. [h/t DataBreaches.net]
Sponsor section
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Cybercrime and threat intel
Ghost takedown: Law enforcement agencies from nine countries have dismantled an encrypted messaging platform used by criminal organizations. Authorities have arrested an Australian man named Jay Je Yoon Jung for creating and running the Ghost platform. They also seized servers in France and Iceland and seized financial assets in the US. According to Europol, law enforcement also detained 51 suspects who used the app and were linked to large transnational criminal networks. Officials had been investigating the platform for three years before Australian police managed to decrypt Ghost devices. The AFP says it intercepted and modified a Ghost app update in March this year, which allowed it to track down the owner and its users in Australia.
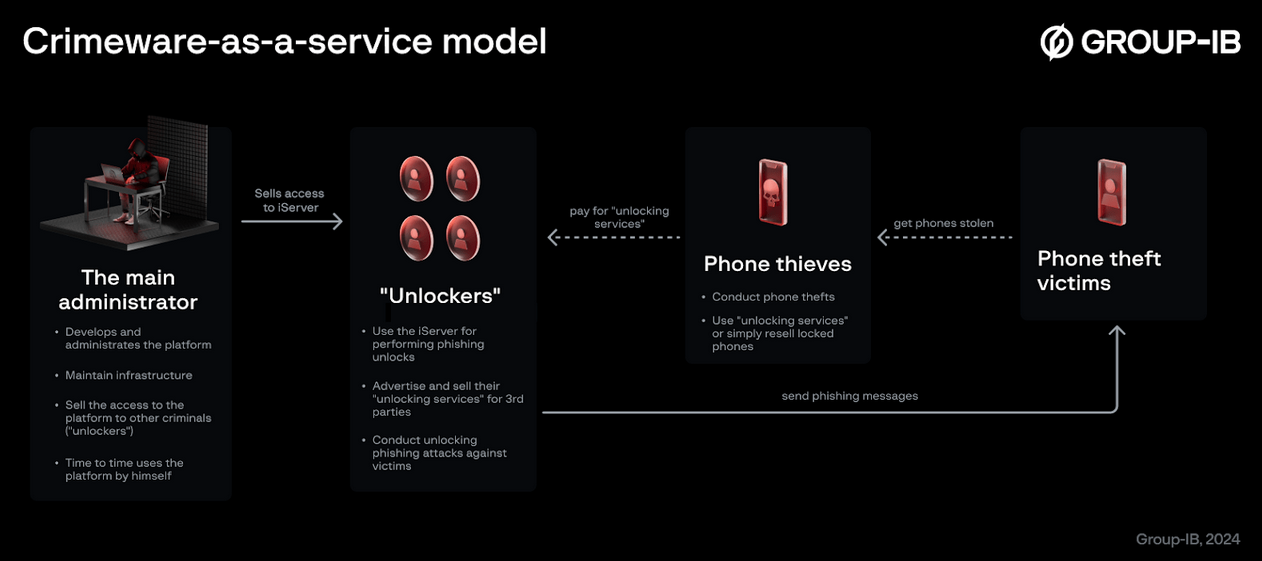
iServer takedown: Law enforcement agencies from Europe and Latin America have dismantled an online phishing platform named iServer. An Argentinian national was detained for allegedly creating the platform back in 2018. Officials say iServer primarily operated as a phone unlocking service. It allowed phone thieves to send phishing messages to a phone's former owner and trick them into unlocking the device. Europol says iServer was used to send phishing messages to over 483,000 Spanish-speaking users across Europe and North and South America.
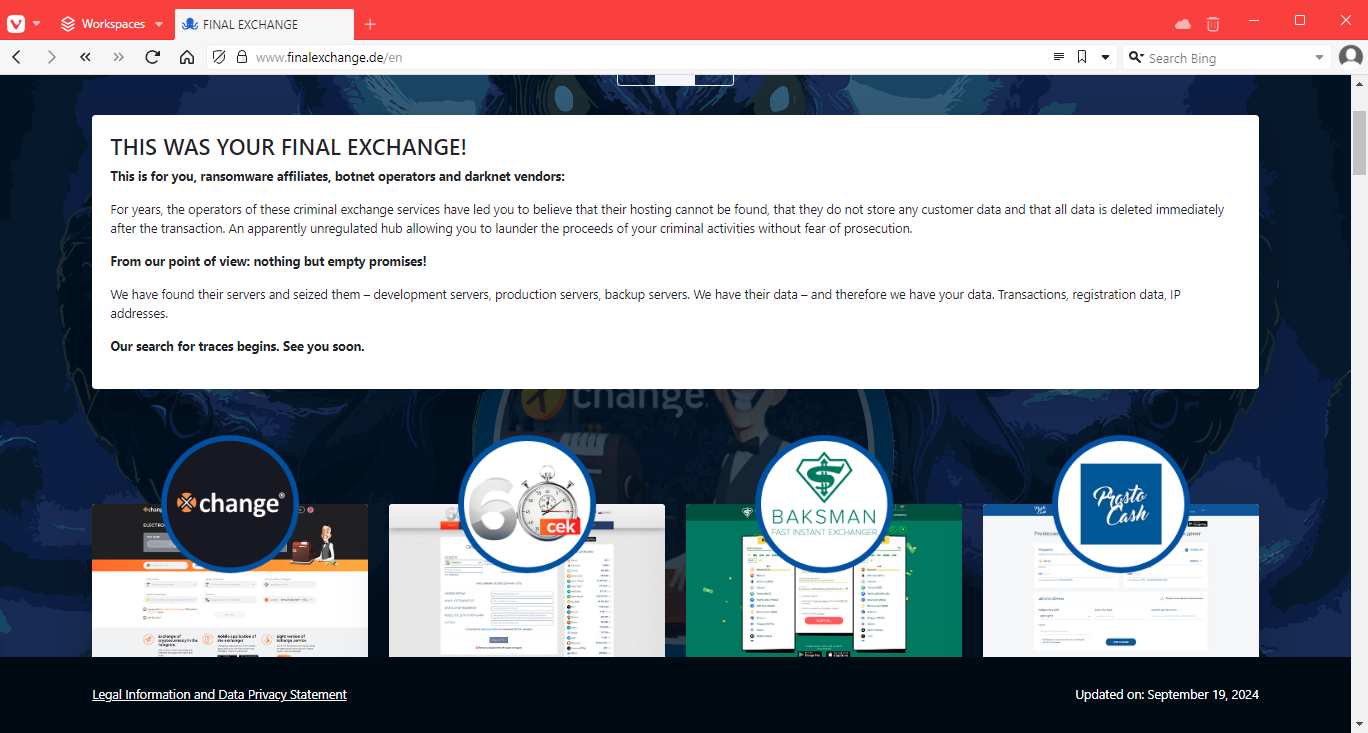
Operation Final Exchange: German law enforcement has shut down 47 cryptocurrency exchanges involved in laundering cybercrime proceeds. Officials say the services knowingly failed to implement anti-money laundering provisions, such as Know Your Customer requirements. German authorities say users of the seized services included ransomware groups, darknet traders, and botnet operators. The largest of the seized sites is Xchange.cash, which had more than 410,000 users before it was shut down.
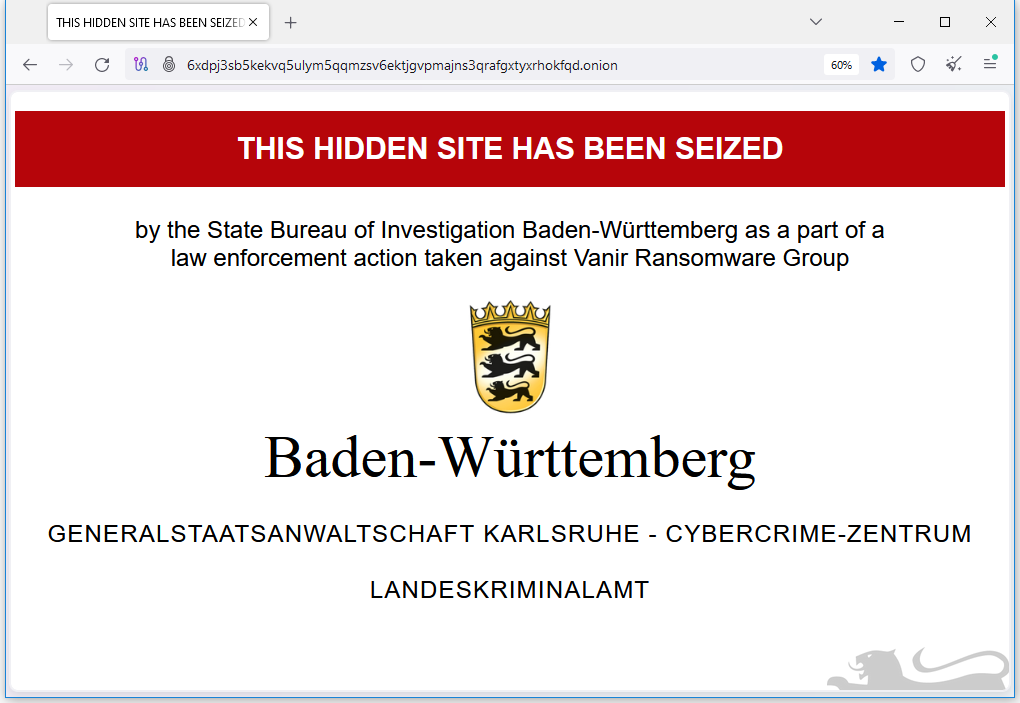
Vanir leak site seized: German authorities have seized the Tor leak site of the Vanir Locker ransomware gang. The group launched operations in July this year and only listed three victims on its site, including a German company. German police say an investigation into the gang's members is still ongoing.
Ukrainian hacker detained: Ukrainian officials have detained a 25-year-old male on charges of hacking into more than 10,000 email inboxes and stealing sensitive data. Officials say the hacker sold the victim's personal and financial data on at least 10 underground hacking forums.
QR phishing in the UK: Netcraft has more details on the QR phishing campaign spotted in the UK over the summer that we featured in our Monday edition. These are malicious QR codes that are placed on top of legitimate QR codes across parking lots.
Auto-reply campaign: Russian security firm FACCT has spotted a threat actor that is compromising email accounts in order to set a malicious auto-reply that responds with links to a crypto-miner.
Walmart-themed malvertising: Malwarebytes has discovered a malvertising campaign targeting Walmart customers with malicious wishlists that feature a rogue customer support service number.
"The scam ends in accusations of money laundering, threats of arrest warrant, and pressure to transfer money into a Bitcoin wallet."
Debate crypto-scam: Infoblox looks at a cryptocurrency scam using a lure of Musk moderating a new Trump-Harris debate.
TeamTNT possible return: Group-IB looks at the possibility that one of the largest crypto-mining groups, TeamTNT, might have returned after going dormant in 2022.
Vanilla Tempest: Cybercrime group Vanilla Tempest has been spotted deploying the INC ransomware in recent operations. The group is a known threat actor that has been an affiliate of many ransomware gangs, such as BlackCat, Quantum Locker, Zeppelin, and Rhysida. Microsoft says recent Vanilla Tempest attacks have leveraged systems infected with the Gootloader malware for initial access.
Traffic noise storms: Cybersecurity firm GreyNoise has been tracking mysterious spikes in spoofed internet traffic since the start of 2020. The company calls this activity Noise Storms and has yet to identify its origin and purpose. The Noise Storms are mainly made up of ICMP packets and TCP packets to port 443 (HTTPS) that originate from spoofed IP addresses. Most of the spoofed traffic is designed to appear as originating from Brazil, but GreyNoise says it found some connections to some Chinese social platforms. The company has different theories for what's happening, such as misconfigured routers, elaborate command-and-control servers, and attempts to carry out sophisticated DDoS attacks.
Malware technical reports
Black Basta ransomware: Qualys has published a report with IOCs from the Black Basta ransomware.
Emmenhtal loader (aka PEAKLIGHT): Sekoia has published a report on a relatively new malware loader service named Emmenhtal. The report's main finding is the malware's use of compromised WebDAV servers to host their customers' payloads. [Other reports on the same malware from Orange, OALABS, and Google Cloud]
AsyncRAT: McAfee looks over a new campaign leveraging cracked software to distribute the AsyncRAT malware.
RECORDSTEALER (RacoonStealer v2): Google's security team has published a technical analysis of the RacoonStealer v2 infostealer, which they call internally as RECORDSTEALER (because why not rename every damn piece of malware 810 times).
SambaSpy: Kaspersky has published a report on SambaSpy, a new RAT that appears to have been developed by a Brazilian or Portuguese developer that targets to infect only Italian-speaking users.
Unicorn: The same Kaspersky team has also discovered Unicorn, a new Windows trojan used in attacks against Russian organizations.
Splinter: Palo Alto Networks says it discovered a new post-exploitation red team tool called Splinter used in the wild. Splinter is written in Rust and extremely difficult to reverse-engineer. The company says it was unable to determine who developed the new tool.
Supershell: AhnLab researchers have discovered Supershell, a new backdoor that's being used to backdoor Linux servers.
"Created by a Chinese-speaking developer, Supershell is developed in the Go language and supports various platforms including Windows, Linux, and Android. Its primary function is a reverse shell, which allows a threat actor to remotely control an infected system."
macOS infostealers: Security researcher g0njxa has a top-down look at macOS infostealers, a scene that continues to grow and grow.
Sponsor Section
In this podcast, Tom Uren and Patrick Gray talk about the structure of the spyware ecosystem. It's concentrated, with lots of vendors in India, Israel, and Italy. And its a small pool of talent, with many companies being founded by just a few individuals.
APTs, cyber-espionage, and info-ops
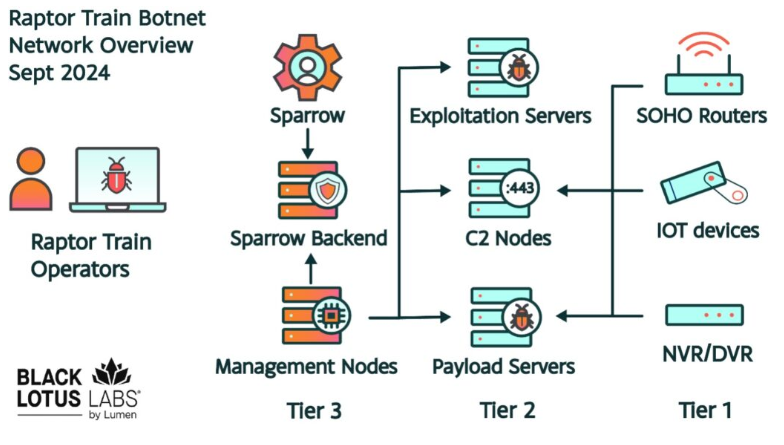
US takes down Flax Typhoon's IoT botnet: US authorities have disrupted an IoT botnet used by Chinese state-sponsored hackers to hide cyberattacks against American and Taiwanese targets. The Raptor Train botnet was set up in 2020 and went under the radar until July of last year—when it was first discovered by Lumen Technologies. Lumen says Raptor Train infected more than 200,000 devices using both zero-day and n-day vulnerabilities. Infected devices included routers, modems, security cameras, NDRs, and NAS devices. The US Justice Department says the botnet was set up and managed by a Chinese company named the Integrity Technology Group. The infosec industry says attacks coming from the botnet were typically tracked under an APT name of Flax Typhoon. The FBI says that when it was taking down the botnet, Flax Typhoon tried to DDoS its infrastructure and prevent the takedown. [Additional technical analysis from the FBI and ACSC]
The suspicious Chinese CTF: Two researchers believe that a Capture The Flag (CTF) competition organized at a Chinese university last year targeted the network of a real company instead of being held on a cyber range. [Additional coverage in Wired]
Chinese APT hack: Binary Defense has published an analysis of a suspected Chinese APT that gained access to a network via an IBM AIX server.
Earth Baxia: Trend Micro says that a Chinese APT group known as Earth Baxia is one of the threat actors exploiting a recent RCE in GeoServer installations. Servers were infected with a new backdoor named EAGLEDOOR. The APT's victims were located in the APAC region.
UNC1860: An Iranian APT group named UNC1860 appears to be responsible for providing initial access services to other Iranian cyber-espionage groups. Google says the group manages an arsenal of backdoors designed to gain strong footholds inside victim networks and establish persistent, long-term access. Some of the backdoors have been found on government and telecom networks across the Middle East. Evidence suggests UNC1860 is likely affiliated with Iran's Ministry of Intelligence and Security (MOIS). The group is also known as Shrouded Snooper, Scarred Manticore, and Storm-0861.
Kimsuky malware: Security researcher somedieyoungZZ has published a report on a relatively new Kimsuky malware payload.
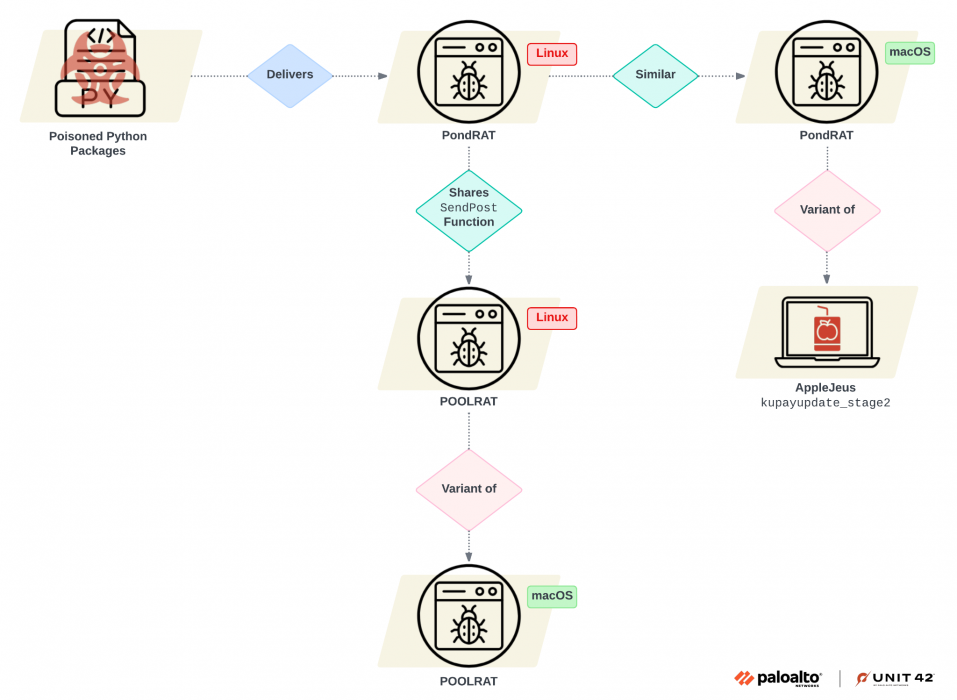
Gleaming Pisces (Citrine Sleet): Palo Alto Networks has published a report on the activities of a North Korean APT tracked as Gleaming Pisces that has spread Linux and macOS backdoors via malicious PyPI libraries.
Operation Overload: A Russian disinformation group has been emailing newsrooms and fact-checkers the whole year in an attempt to spread pro-Kremlin propaganda and narratives. Codenamed Operation Overload, the campaign has sent more than 71,000 emails to almost 250 organizations throughout the year. The group spread disinformation about the war in Ukraine and the Paris Olympics in the first half of the year but has now switched to targeting the Harris Presidential campaign.
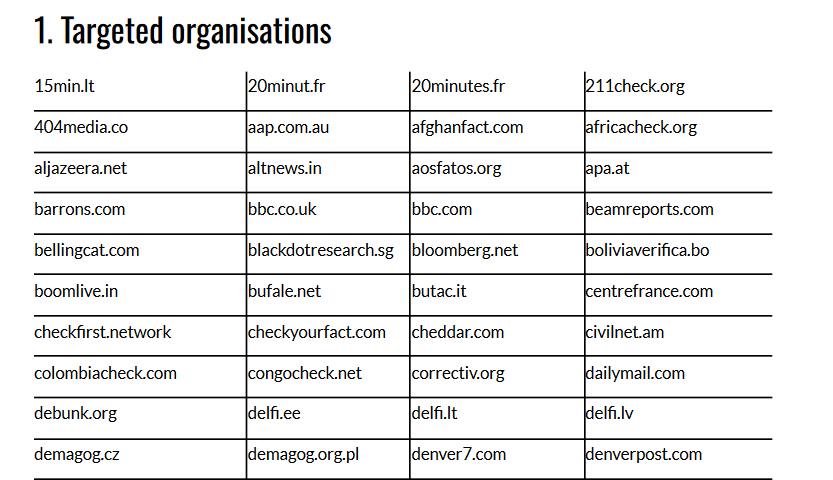
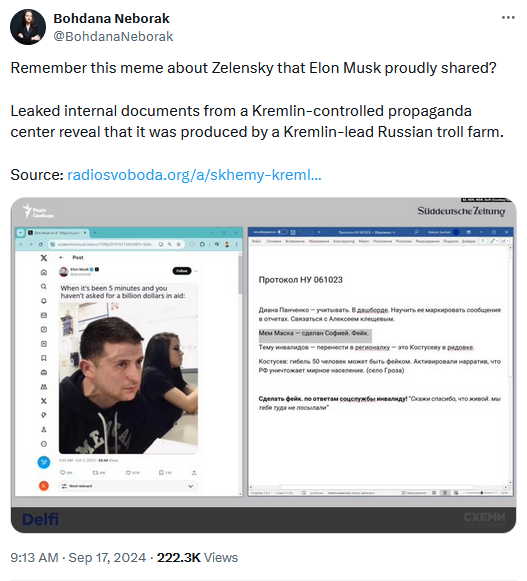
Russian disinfo leak: OCCRP reporter Martin Laine analyzes a leaked database of past fake comments posted by Russian trolls online. The comments come from the Social Design Agency, or SDA, which was recently exposed and sanctioned by US authorities. In one of the leaked SDA internal documents, SDA employees rejoiced when Elon Musk retweeted one of their memes.
Vulnerabilities, security research, and bug bounty
KEV update: CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. This includes a 2024 bug in Apache HugeGraph-Server, a 2020 bug in MSSQL, a 2019 Windows bug, a 2020 Oracle WebLogic server bug, and a 2022 Oracle JDeveloper RCE.
New Ivanti zero-day: Threat actors are exploiting a new zero-day vulnerability in the Ivanti Cloud Service Appliance (CSA). Tracked as CVE-2024-8963, the vulnerability is a path traversal that can allow a remote unauthenticated attacker to access restricted functions. Ivanti says attackers are exploiting the zero-day together with another CSA zero-day it patched last week, tracked as CVE-2024-8190.
GitLab security updates: GitLab has released a security update to fix a SAML authentication bypass (CVE-2024-45409) in its open-source source code management server.
Atlassian security updates: Atlassian has released its monthly security updates. This month, the company has patched six vulnerabilities. All are denial of service issues, and none are exploited in the wild.
vCenter RCE: VMware has released a security update for EoP and RCE vulnerabilities in its vCenter product. [h/t Dietrich D.]
MediaTek PoC: A proof-of-concept has been published for CVE-2024-20017, a remote code execution bug in MediaTek WiFi chipsets. The bug was first patched in March and impacts IoT devices using MediaTek chips, such as Ubiquiti, Xiaomi, and Netgear.
Veeam PoC: watchTowr Labs has released a PoC for CVE-2024-40711, an RCE bug they discovered in Veeam backup solutions.
AJCloud vulnerabilities: Elastic's security team has reverse-engineered AJCloud security cameras and found several vulnerabilities. More in their report.
gqlparser vulnerability: Cato Networks has discovered a denial of service vulnerability in gqlparser, a library used in the development of GraphQL applications.
"This oversight allows an attacker to craft a query with an excessive number of non-existing directives, causing the system to exhaust its resources and lead to a Denial of Service (DoS) of the server."
Infosec industry
Craig Newmark donation: Craigslist founder Craig Newmark has made a pledge to donate $100 million to shore up the cybersecurity of the United States. Half the funds will focus on protecting power grids and other critical infrastructure from cyberattacks, while the other half will be dedicated to cybersecurity educational programs. [Additional coverage in TechCrunch]
New tool—Binsider: Software developer Orhun Parmaksız has released Binsider, a tool for analyzing ELF binaries. The code is available on GitHub as well.
New tool—Bear C2: Red-team specialist S3N4T0R-0X0 has released Bear C2, a compilation of C2 scripts, payloads, and stagers used in simulated attacks by Russian APT groups.
New tool—DGPOEdit: Security researcher Ceri Coburn has released DGPOEdit, a Group Policy Manager launcher, to allow editing of domain GPOs from non-domain joined machines.
New tool—CloudKicker: Security researcher Nyxgeek has released CloudKicker, an Azure OSINT toolkit.
Threat/trend reports: AquaSec, Positive Technologies, ProtectAI, Red Canary, and Red Alert have recently published reports covering infosec industry threats and trends.
SEC-T 2024 videos: Videos from the SEC-T 2024 security conference, which took place last week, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect an FBI advisory about North Korean groups targeting cryptocurrency firms with social engineering.





