Risky Biz News: Stealer devs bypass Chrome's new cookie protection
In other news: Sandvine to exit dozens of autocratic countries; Ukraine FINALLY bans Telegram on state devices; BingX hack is the 4th largest crypto-heist of the year.

This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The developers of several of today's top infostealers have found several ways to bypass Chrome's new App-Bound Encryption security feature.
Infostealers such as Lumar, Lumma, Meduza, Vidar, and WhiteSnake have told their "customers" they can now bypass the feature and retrieve authentication cookies that were recently coming back encrypted.
Added in Chrome v127, released in mid-July, the App-Bound Encryption feature works by encrypting data related to the Chrome browser process. This data can be decrypted only from an admin-level account.
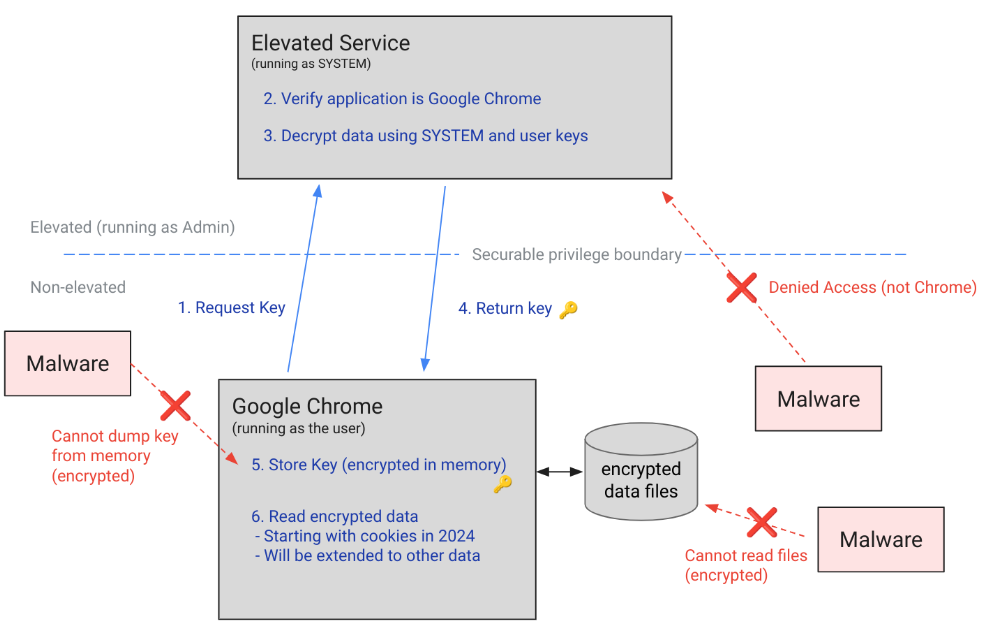
Since infostealer malware typically runs from an infected user's normal account, since the release of Chrome 127, the new feature has prevented infostealers from stealing authentication cookies from infected hosts.
For the past two months, infostealer devs have been working on ways to bypass this feature by either injecting code into the Chrome process itself or by using Elevation-of-Privilege exploits to gain access to admin privileges.
When Google added App-Bound Encryption to Chrome, it knew the feature wasn't bulletproof and that malware devs would eventually find ways around it, but Google implemented it regardless because it knew the bypass techniques would make infostealers easier to spot. (see quote below)
"Because the App-Bound service is running with system privileges, attackers need to do more than just coax a user into running a malicious app. Now, the malware has to gain system privileges, or inject code into Chrome, something that legitimate software shouldn't be doing. This makes their actions more suspicious to antivirus software – and more likely to be detected. Our other recent initiatives such as providing event logs for cookie decryption work in tandem with this protection, with the goal of further increasing the cost and risk of detection to attackers attempting to steal user data."
Something like this happened before, in February 2020, when Google released Chrome v80, which featured a new password hashing algorithm. The update broke several infostealers for weeks until they rolled out updates.
Even if it was a short-lived disruption to the infostealer market, Google counted it as a win, although it did not try other sudden changes in Chrome's password and cookie storage mechanisms until this year.
With the infostealer market—which steals and then sells access to passwords and authentication cookies on specialized underground marketplaces—fueling more and more ransomware intrusions and large breaches over the past month, Google's security team is now taking a closer look at the way they handle sensitive data in the browser.
The App-Bound Encryption feature is currently live only for browser cookies, but Google plans to extend this to passwords, payment data, and other persistent authentication tokens stored in Chrome.
Google is also working on another new security feature named Device Bound Session Credentials that the company is hoping to have ready for some trials by the end of the year. This new tech will use cryptographic keys that are tied to every user's machine to encrypt passwords and cookie-related data. It is a much stronger protection than App-Bound Encryption since it lets websites have some control over these keys, which is why it's taking a little bit longer to develop.
[h/t @g0njxa]
Breaches, hacks, and security incidents
Star Health leak: Telegram has taken down a bot account that was used to sell user data from Indian medical insurance provider Star Health. A threat actor using the alias xenZen created the bot in early August. They claimed to have hacked Star Health and stolen the personal and medical records of 31 million users. Star Health confirmed the breach in a filing with the Indian stock exchange. [Additional coverage in Reuters]
Hertz leak: Car rental service Hertz leaked claims reports via its website, according to cyber risk company Adversis.
HuntStand leak: A threat actor has scrapped public profiles from hunting and land management service HuntStand and later leaked the data on hacking forums.
Ethena Labs domain hijack: The Ethena Labs cryptocurrency project says it was the victim of a domain hijack last week. The company has now regained control of its site and no funds were stolen in the hack.
Remitano hacked funds seized: The FBI seized some of the $2.7 million stolen by hackers from the Remitano cryptocurrency exchange last September.
BingX crypto-heist: Hackers have stolen $44 million worth of assets from Singaporean cryptocurrency exchange BingX. The company says the funds were stolen from its hot wallets. BingX suspended operations at the end of last week to investigate the incident. The incident is the fourth-largest cryptocurrency heist of the year.
Shezmu crypto-heist: The Shezmu crypto-lending platform was hacked for $4.9 million after it misconfigured a part of its infrastructure. An attacker used funds from the company's vault as collateral to mint and steal new Shezmu tokens. Shezmu recovered the stolen funds in less than 24 hours after it agreed to let the attacker keep 10%.
Banana Gun crypto-heist: The Banana Gun automatic trading bot platform says that hackers have exploited a vulnerability in its frontend to steal funds from user wallets. Attackers are believed to have stolen almost $2 million worth of Ether from at least 36 victims. The company claims it fixed the issue and restored the platform with a temporary 6-hour delay on all transactions.
General tech and privacy
Sandvine exits autocratic countries: Surveillance gear maker Sandvine is leaving 56 countries as part of an overhaul of its business model. The company has stopped operating in 32 countries and plans to exit another 24 by April next year. CEO Lyndon Cantor is also stepping down and will be replaced by new management with a focus on human rights. Sandvine's new business model comes seven months after the US Commerce Department sanctioned the company for providing internet mass surveillance technology to the Egyptian government. Other Sandvine customers also included autocratic countries such as Belarus, Eritrea, the UAE, and Uzbekistan. [Additional coverage in TechCrunch]
Kazakhstan internet surveillance: The Open Observatory of Network Interference (OONI) has published research on the Kazakh government's years worth of internet censorship efforts, most of which target news websites and the websites of human rights organizations—you know, the number one enemy of all legit democracies and governments (/s).
Call to deprecate WHOIS verifications for TLS certs: Google has made a proposal to the CA/B Forum to sunset the use of WHOIS for verifying the ownership of a domain before issuing a TLS certificate. [Additional coverage in ArsTechnica]
OpenSearch update: AWS has moved OpenSearch—its internal clone of the ElasticSearch database—under the management of the Linux Foundation. [Additional coverage in TechCrunch]
LinkedIn stops AI scraping in UK: The UK ICO says it reached an agreement with LinkedIn to stop scraping UK user data to train its AI algorithms.
Musk backs down in Brazil: Elon Musk has lost his fReE sPeEcH crusade in Brazil and has agreed to take down right-wing accounts that encouraged a violent attack on the country's Congress in January 2023. Twitter/X will also pay fines and comply with the country's request to appoint a legal representative in the country. Musk bowed after Brazil's Supreme Court imposed a nationwide ban on the social network last month. [Additional coverage in The Guardian]
Microsoft Entra Internet Access now GA: Microsoft says its Entra Internet Access secure web gateway (SWG) solution is now ready for general availability.
Edge to warn of performance hogs: Microsoft Edge will warn users when one of their extensions is using too many resources and impacting browsing performance.
Ads coming to paused YT videos: Google has confirmed that it will start showing ads when users pause YouTube videos. [Additional coverage in The Verge]
Passkeys syncing: Google is now letting Chrome users sync passkeys across devices—just like it already does with passwords, tabs, and browsing history.
macOS Sequoia breaks security tools: Apple's new macOS Sequoia operating system is disrupting security tools made by CrowdStrike, ESET, Microsoft, SentinelOne, and others. Users are also reporting internet issues and connection failures with third-party VPNs. Apple has not commented on the matter, and it's currently unclear what the issue is. [Additional coverage in TechCrunch]
Government, politics, and policy
Ukraine bans Telegram on state devices: Ukraine has banned the use of Telegram on state-issued devices, citing national security and fears of Russian espionage. The ban applies to state and security officials, military personnel, and critical infrastructure facilities. The head of Ukraine's military intelligence agency says Ukraine has "substantiated data" that Russian authorities have access to Telegram personal messages, including deleted posts.
Reversal in BSI chief Russian connection allegations: A Munich court has ruled that Germany's former cybersecurity chief was falsely accused of having secret connections with Russian intelligence agencies. Former BSI head Arne Schoenbohm was dismissed in late 2022 after a ZDF report found alleged ties to Russia's intelligence services in one of his past private-sector endeavors. In a temporary ruling last week, a judge ruled that ZDF was wrong and its report did not not meet journalistic standards. A final ruling in the case is expected at the end of November. Schoenbohm is also seeking over €200,000 from ZDF in a separate case as compensation for his wrongful dismissal. [Additional coverage in Heise Online]
New spyware visa restrictions: The US State Department has imposed new visa restrictions on individuals involved in the development or sale of commercial spyware. The agency did not share the names or the number of targeted individuals. The new visa restrictions come after the US Treasury sanctioned five individuals and a company associated with the Intellexa Consortium last Monday. This is the second wave of visa restrictions imposed by the US on individuals linked to the spyware and surveillance market. The State Department imposed its first visa bans on 13 individuals back in April.
New US car hardware and software bans: The US Commerce Department is expected to ban the use of Chinese and Russian hardware and software in American smart cars. According to Bloomberg and Reuters, the upcoming ban is the result of an investigation of cybersecurity risks associated with smart cars. The US government fears foreign adversaries may use technology embedded in US cars to hack vehicles, intercept communications, or track targets.
DOJ ransomware action audit: An audit from the DOJ Inspector General has found that the DOJ and FBI need better metrics to track their efficiency and successes in fighting ransomware gangs. Despite several seizures and disruptions of ransomware infrastructure between 2022 and 2023, US agencies need new metrics to track how fast they react to ongoing ransomware attacks. The audit also found that many ransomware investigations have been mired in infighting between different law enforcement agencies that often decline to share information with each other. [Additional coverage in The Record]
New warrant officers for cyber: The US is reintroducing warrant officers in its military after more than 65 years, and they are slated to play a big role in US CyberCommand and its cyber forces. [Additional coverage in DefenseScoop]
CSC yearly report: The US Cyberspace Solarium Commission (CSC) has issued its yearly report with 10 recommendations the US government can implement to improve the country's cybersecurity posture.
- Designate Benefits and Burdens for Systemically Important Entities
- Conduct Robust Continuity of the Economy Planning
- Codify Joint Collaborative Environment for Threat Information Sharing
- Strengthen an Integrated Cyber Center Within CISA
- Develop Cloud Security Certification
- Establish a Bureau of Cyber Statistics
- Establish Liability for Final Goods Assemblers
- Develop Cybersecurity Insurance Certifications
- Establish National Guard Cybersecurity Roles
- Build Societal Resilience Against Cyber-Enabled Information Operations
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely co-founder and CEO Travis McPeak about some of the hard and uncomfortable truths about the role of security teams inside a company.

Cybercrime and threat intel
Crypto-whale phishers detained: US authorities have arrested and charged two men with stealing $243 million from a cryptocurrency investor. The incident took place on August 19 and targeted a creditor of the Gemini cryptocurrency exchange. Malone Lam and Jeandiel Serrano allegedly posed as Google Support to trick the victim into resetting their 2FA, sharing their screen, and leaking wallet private keys. The suspects stole the funds and proceeded to launder the assets via multiple blockchains. The two also spent some of the stolen funds on international travel, nightclubs, luxury cars, watches, jewelry, designer handbags, and rental homes in Los Angeles and Miami.
AI in cyber assessment: German's cybersecurity agency, the BSI, has published an assessment on the use of artificial intelligence in cyber operations. The agency says it has not spotted any new TTPs, but AI has made some operations faster and more efficient. NATO's StratCom also published an AI assessment last month, but it looked at AI's role in digital advertising and its potential role for conducting "precision persuasion campaigns."
New npm malware: Forty-one malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Copy-pasta campaign: McAfee has published a write-up on a recent copy-pasta attack leveraging fake CAPTCHA widgets. The campaign was first spotted last week.
Crypto scam campaign: Silent Push looks at a Russian-based threat actor using US politics-themed domains to push crypto giveaway scams.
ICICI phishing: Security researcher Rakesh Krishnan has published a breakdown of a malicious Android app targeting users of Indian bank ICICI.
Snowflake hacker still active: The individual who hacked cloud storage platform Snowflake earlier this year is still active and is still targeting SaaS platforms, Google security researcher Austin Larsen told audiences at the LabsCon security conference last week. The hacker goes by aliases such as Judische and Waifu, is a member of an underground community known as The Com, and has been identified by cybersecurity journalist Brian Krebs as a 26-year-old software engineer living in Ontario, Canada. Larsen says that Google's Mandiant division also believes Judische is based in Canada. [Additional coverage in CyberScoop]
TWELVE returns: Kaspersky researchers say that a pro-Ukrainian hacking group known as TWELVE has returned with new destructive and ransomware attacks against Russian organizations. The group launched in April of last year but ceased activity after its Telegram channel was suspended at the start of 2024. Kaspersky says it has now detected the group's attack patterns in recent intrusions that took place in June. New evidence also suggests the group is sharing infrastructure with another threat actor known as DARKSTAR. Also known as Shadow or Comet, this group is also known for attacking Russian companies with ransomware. [We first featured this in our newsletter in early August but with a link to Kaspersky's Russian language blog]
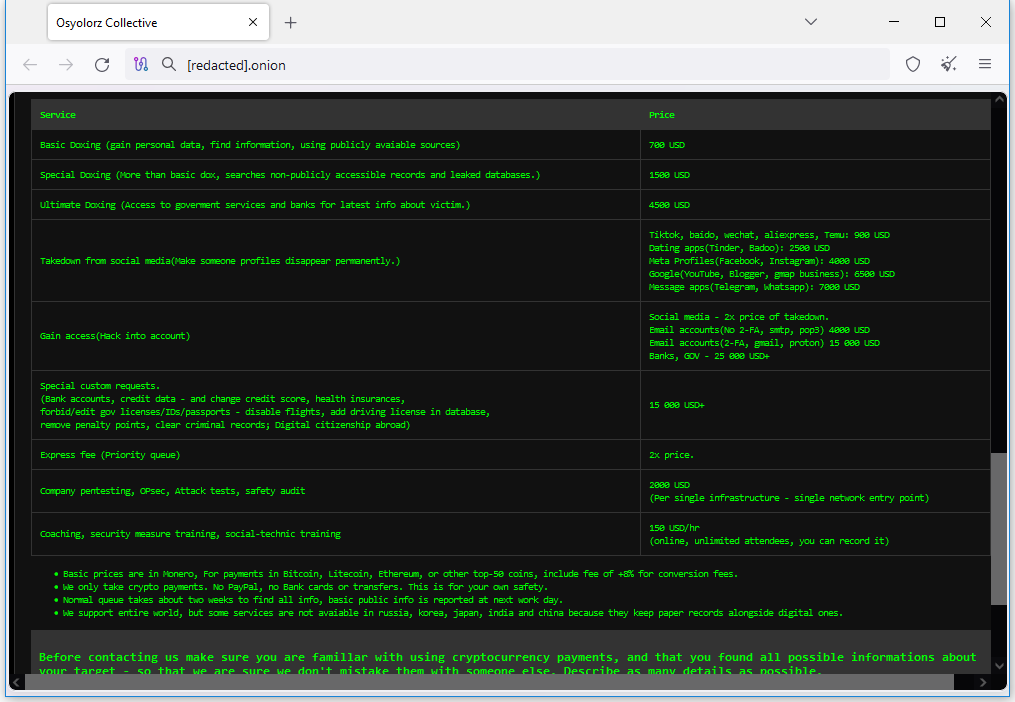
New Osyolorz Collective: Threat intel analyst Dominic Alvieri has spotted a new threat actor named the Osyolorz Collective. The group claimed a collection of past breaches and is offering to conduct on-demand paid offensive cyber operations. [h/t Dominic Alvieri]
Malware technical reports
ReadText34 ransomware: Huntress Labs has published a report on the new ReadText34 ransomware.
Akira ransomware: The same Huntress team has also published IOCs from a recent Akira ransomware attack.
RansomHub adopts EDRKillerShifter: Trend Micro says that the RansomHub ransomware group is now using a tool named EDRKillerShifter to shut down security products on systems before stealing and encrypting data.
Revolver Rabbit: Palo Alto Networks has shared IOCs used by the Revolver Rabbit threat actor as RDGA domains for its cybercrime infrastructure, typically employed by malware groups to host C&C servers or for scams.
Sponsor Section
Resourcely co-founder and CEO Travis McPeak held an off-the-record conversation at this year's Blackhat Campfire Stories, talking about some of the hard truths CISOs don't usually talk about.

APTs, cyber-espionage, and info-ops
COLDWASTREL: PwC's security team looks at COLDWASTREL, a Russian APT group involved in spear-phishing NGOs. PwC says the group is also tracked as UAC-0102 and White Dev 185.
Patchwork (White Elephant): Alibaba Cloud has published a report on PGoshell, a backdoor used by the Patchwork APT.
Iranian APT overview: Trellix has an overview of the most common techniques used by Iranian APT and adjacent groups.
Vulnerabilities, security research, and bug bounty
Android research: The Android offensive security team has published a technical deep dive into Binder, a client-server communications framework included in the Android OS.
AndroCon technique: A team of researchers from the Indian Institute of Technology in Delhi has developed a new technique named AndroCon that can use semi-processed GPS data to map indoor spaces near an Android device.
Tokens in Entra ID: Xintra's Lina Lau has published a guide on all the tokens in the Microsoft Entra ID server.
Cisco SLU write-up: Aruba threat researcher Nicholas Starke has published an analysis of CVE-2024-20439, a hidden admin account with a static password (aka backdoor account) in the Cisco Smart Licensing Utility.
Arc Browser RCE: The Arc Browser has fixed a vulnerability (CVE-2024-45489) that could have allowed threat actors to run malicious code on Arc user browsers via the browser maker's Firebase database. [h/t ScreamingGoat]
Exchange RCE: ZDI researcher Piotr Bazydło has published an article about the three-bug exploit chain he developed for RCE attacks on Microsoft Exchange servers. Bazydło presented the exploit chain at OffensiveCon this year, and the chain was also nominated for a PwnieAward.
Infosec industry
Kaspersky story: Security researcher Artem Baranov looks at how Russian security firm tried and failed to conquer the Western cybersecurity market, being doomed by its suspected ties to Russian intelligence and Russia's invasion of Ukraine.
Junkyard EOL Pwnathon: A DC-area security conference plans to hold a hacking contest against End-of-Life products. Participants will be required to disclose the bug to the vendor, although there are no reasonable expectations for a patch. The Districtcon security conference will hold its inaugural edition in Washington, DC, in February next year.
New tool—MSSprinkler: Security researcher TheresAFewConors has released MSSprinkler, a password-spraying utility for organizations to test their M365 accounts for low-and-slow brute-force attacks.
New tool—Undocumented AWS API Hunter: DataDog has released Undocumented AWS API Hunter, a tool to uncover, extract, and monitor undocumented AWS APIs from the AWS console.
New tool—Metasploit module: Security researcher Alexander Hagenah has contributed a Metasploit module that can extract saved user data from various Chromium-based and Gecko-based browsers.
New tool—BrowserSnatch: Cytomate's Shayan Ahmed Khan has released BrowserSnatch, a tool designed to "snatch" sensitive data from a variety of web browsers.
New tool—ZipSlipper: Security researcher Jan Harrie has released ZipSlipper, a new tool for creating malicious ZIP and TAR archives that can exploit the ZipSlip vulnerability.
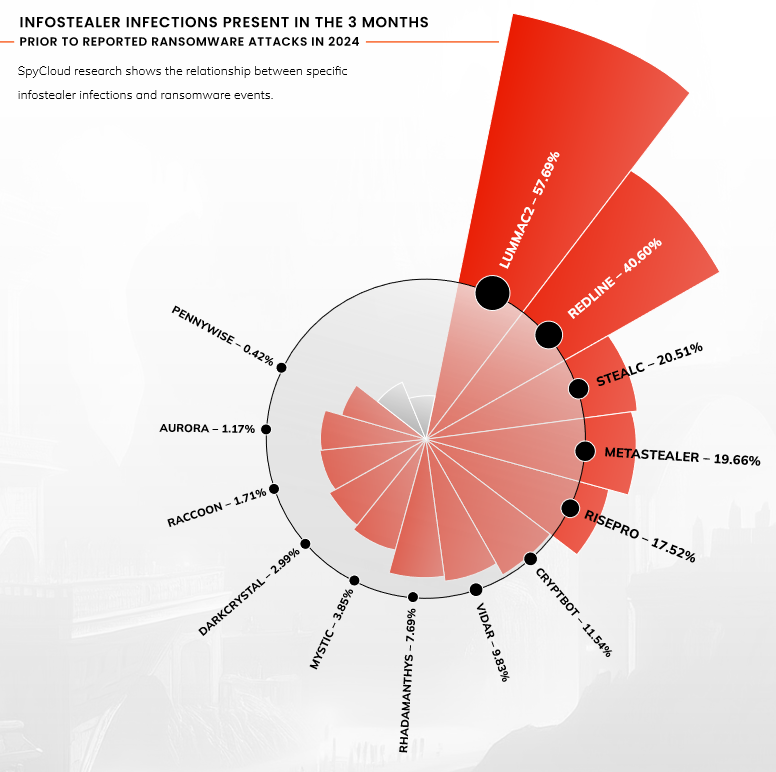
Threat/trend reports: ENISA, Orca Security, and SpyCloud have recently published reports covering infosec industry threats and trends.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect an FBI advisory about North Korean groups targeting cryptocurrency firms with social engineering.
In this podcast, Tom Uren and Patrick Gray talk about the structure of the spyware ecosystem. It's concentrated, with lots of vendors in India, Israel, and Italy. And its a small pool of talent, with many companies being founded by just a few individuals.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





