Risky Biz News: Interpol plugs Red Notices leak
In other news: Kaspersky says Apple didn't pay bounty for Triangulation report; Medibank faces monumental fine; CISA named as first-ever CVE ADP.

This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Moldavian authorities have arrested four individuals suspected of sharing information about Interpol Red Notices with wanted fugitives, including cybercrime suspects.
The scheme was uncovered earlier this year by the UK NCA during a separate cybercrime investigation. Authorities say a criminal group paid bribes of several millions of US dollars to Moldavian public servants to provide early warning of Interpol Red Notice arrest warrants.
The early warning allowed wanted individuals to seek asylum or refugee status in Moldova or other countries, a process that triggers the deletion of Red Notices from the Interpol database.
Officials say the group behind the scheme is made up of individuals of different nationalities, and the beneficiaries of the scheme were mostly wanted fugitives in countries such as Russia, Ukraine, and Belarus.
Some of the individuals who paid bribes to avoid Red Notices were being investigated for committing cybercrimes that caused millions of US dollars in damages.
According to a report in Radio Free Europe Moldova, the detained suspects are Moldavian public servants. It is unclear if any of the group's members were also detained.
Moldavian authorities are now working with American, British, and French authorities to analyze devices seized from the suspects.
Interpol says it also implemented additional measures "to ensure the suspected misuse is stopped and to prevent future occurrences."
Breaches, hacks, and security incidents
GUR DDoS attack: Ukraine's GUR military intelligence agency took credit for a series of DDoS attacks that targeted the websites and systems of multiple Russian government agencies. [Additional coverage in Pravda]
MediSecure enters administration after hack: Australian electronic prescription provider MediSecure has entered into administration three weeks after falling victim to a ransomware attack. The company previously requested and was denied a bailout by the Australian government. MediSecure was the first-ever company to file for financial support from the Australian government because of a cyber attack. Two FTI Consulting executives have been appointed as administrators and liquidators of the company's assets. [Additional coverage in ABC]
Medibank hack fine: Australia's Information Commissioner has filed a lawsuit against insurance provider Medibank in connection to its October 2022 ransomware attack. The agency says Medibank failed to take reasonable steps to protect its customers' personal information and intends to seek a maximum penalty in the case. According to Australian law, Medibank may be on the hook for AUS$21.5 trillion, AUS$2.22 million for each of the 9.7 million users who had data stolen in the hack. [Additional coverage in AFR]
Patties Foods leak: Security researcher Jeremiah Fowler has found a non-protected database that exposed documents from Australian food service provider Patties Foods.
ClubPenguin hack: A threat actor has breached Disney's Confluence server and stolen data on the company's now-defunct ClubPenguin game. The hacker described themselves as a ClubPenguin fan and leaked some of the stolen data on 4Chan. BleepingComputer claims the ClubPenguin data is part of a larger set of files the hacker stole from Disney, some of which are now being shared in private Discord servers.
Advance Auto Parts: A threat actor is selling 3TB of data from US car parts giant Advance Auto Parts. The hacker claims to have obtained the data by hacking the company's Snowflake account. BleepingComputer claims it was able to confirm that a large number of Advance Auto Parts customer records are legitimate. The company has not formally confirmed the incident.
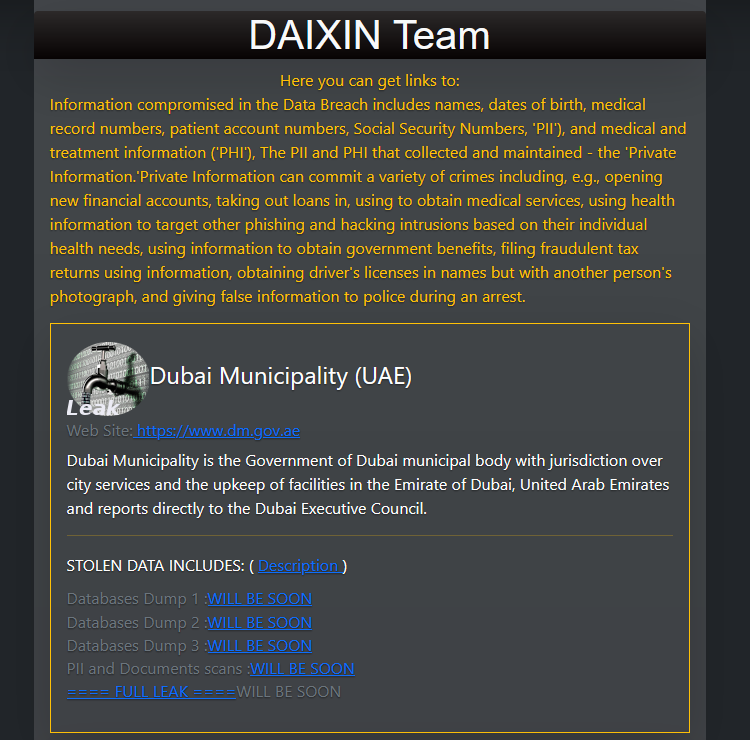
Dubai ransomware attack: The Daixin ransomware group claims to have breached the network of Dubai's municipal government. The hack allegedly took place last week on May 27. The group told DataBreaches.net that it encrypted thousands of internal servers and deleted some of the city's backups. City officials have not confirmed the incident.
General tech and privacy
Twitter opens to pr0n: After putting up a good fight against the relentless and heroic pr0n bots, Twitter (X) has admitted defeat and modified its ToS to allow pornographic content on the platform. [Additional coverage in USA Today]
Australia backs down from Twitter: Australia's eSafety commissioner has dropped a legal case against Twitter. The agency previously sued Twitter to remove videos of the graphic stabbing of Bishop Mar Mari Emmanuel. Australia tried to remove the video from all countries, not just its territory, a request Twitter resisted. [Additional coverage in CyberDaily]
Twitch pricing change: For infosec practitioners who follow or run Twitch cybersecurity channels, Twitch is changing Tier 1 monthly subscription prices from $4.99 to $5.99 per month on July 11.
Google CPO leaves: Google's Chief Privacy Officer Keith Enright is leaving his role at Google after 13 years.
Meta AI complaint: Privacy organization noyb has asked data protection agencies in 11 EU countries to investigate Meta for its plan to use Facebook user data to train its AI.
"Instead of asking users for their consent (opt-in), Meta argues that it has a legitimate interest that overrides the fundamental right to data protection and privacy of European users. Once their data in the system, users seem to have no option of ever having it removed ("right to be forgotten")."
iPhone 15 security updates: Apple says its latest iPhone 15 smartphone model will receive only five years of security updates [PDF]. The model launched in September of last year and will officially reach end-of-support in September 2028. Both Google and Samsung guarantee seven years of security updates for their flagship models. [Additional coverage in Android Authority]
Adobe's Photoshop TOS change: Adobe is blocking access to its Photoshop app unless users agree to new terms of service that grants the company full access to their content, use it freely, and even sublicence it to others. There is no way this ToS change won't get the company sued into the ground, especially since several high-profile creators, such as movie directors, gaming companies, and music artists, have claimed Adobe just gave itself the right to access and "steal" files under some pretty strict NDAs and licensing deals. [Additional coverage in 9to5Mac]
Government, politics, and policy
Malaysia to require data breach notifications: The Malaysian government plans to amend the 2010 Personal Data Protection Act to require organizations that suffered a security breach to notify the government. [Additional coverage in The Sun, h/t DataBreaches.net]
Polish cyberdefense investment: The Polish government will invest $760 million to boost its cybersecurity defenses. [Additional coverage in The Record]
FCC passes BGP rules: The FCC has proposed new rules that will require the US' nine largest broadband providers to file confidential reports on the state of their BGP defenses. The reports must contain information on the steps companies have taken or plan to take to mitigate BGP internet routing vulnerabilities. Smaller providers don't have to file reports with the FCC but must have the data available on request. The FCC started working on the new reporting requirement in February 2022 in the aftermath of reports of Chinese and Russian telcos hijacking US internet traffic. The DOD and DOJ backed the FCC's effort to improve BGP security, seeing it as a national security threat.
FCC school cyber funding: The FCC has allocated $200 million to fund the acquisition of cybersecurity services and products at K-12 schools and libraries. The funds will be made available in the next three years through the FCC E-Rate program. Prior to this year, E-Rate funds could previously only be used to purchase internet subscriptions and networking devices.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Nucleus Security co-founder and COO Scott Kuffer about recent trends the company has observed among customers when it came to patch management and how service level agreements (SLAs) became a sign of an organization's security health.

Cybercrime and threat intel
Conti member detained: Dutch and Ukrainian authorities have arrested a 28-year-old from Kyiv for launching attacks with the Conti ransomware. He is suspected of having ransomed a Dutch multinational in 2021. The suspect was detained in April, and the arrest was part of Europol's Operation Endgame. The operation took place last week and took down six of the world's largest botnets.
Epsilon member detained: French authorities have detained a 16-year-old teen for running a malware rental business. The teen used nicknames such as ChatNoir and Cap and was part of the Epsilon hacker group that breached the Altice French multinational earlier this year. According to posts on the group's Telegram channel, the teenager appears to be behind the WaveStealer malware. [Additional coverage in LeMonde]
Chinese fraudsters plead guilty: Twenty-two Chinese nationals pleaded guilty to running an internet fraud syndicate. The 22 were detained in April as part of a law enforcement crackdown that targeted the offices of a Chinese company named Golden Top Support Services.
npm malware: DevSecOps company Phylum has found a malicious npm library that steals data from cryptocurrency-related browser extensions.
PyPI malware: And we could have a report about npm malware without some PyPI malware too. Sonatype says it spotted PyPI libraries laced with the Lumma Stealer.
GitHub wiping attacks: A threat actor named GitLocker is wiping GitHub repositories and asking for ransom demands. The attacks were spotted this week but have been happening for a while. According to BleepingComputer, almost 50 GitHub repositories currently have GitHub ransomware demands in their README files.
WatchGuard brute-force attacks: SANS ISC has detected a wave of brute-force attacks against WatchGuard VPN nodes.
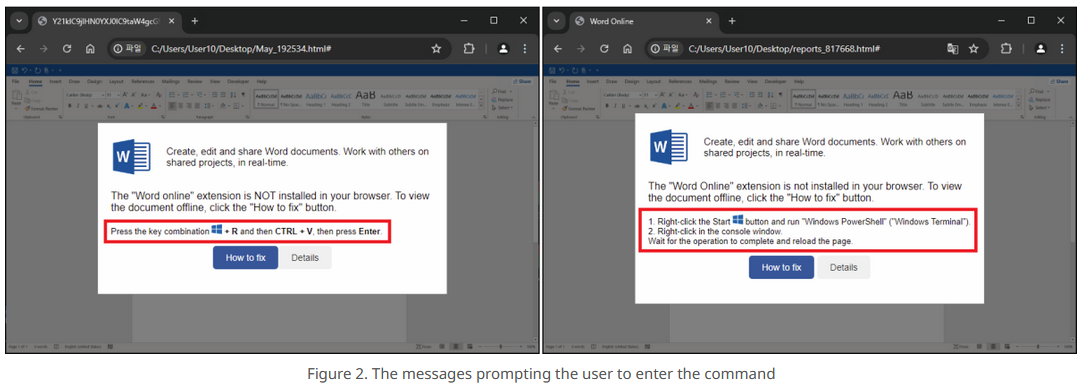
Copy-paste campaign: South Korean security firm AhnLab has spotted a spear-phishing campaign that tries to bypass security defenses by asking users to copy-paste malicious PowerShell commands in their Windows Run prompt.
AirTags abuse: CourtWatch and 404 Media have published a joint report on a Russian human trafficker who has been using Apple AirTags to track women he brought to the US.
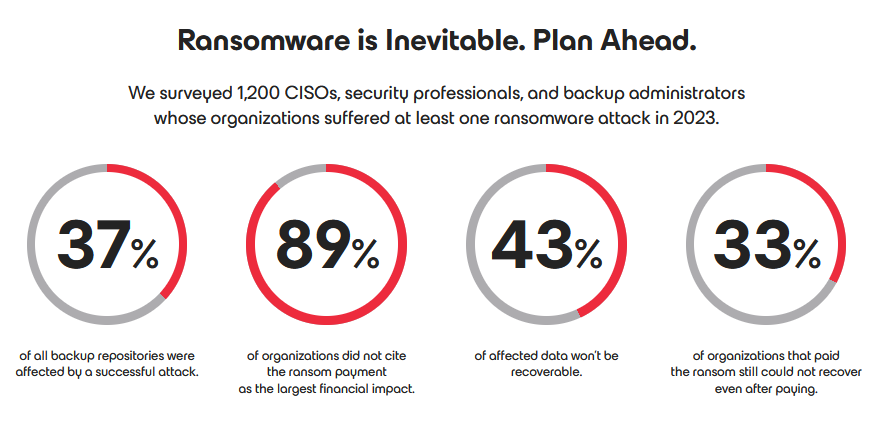
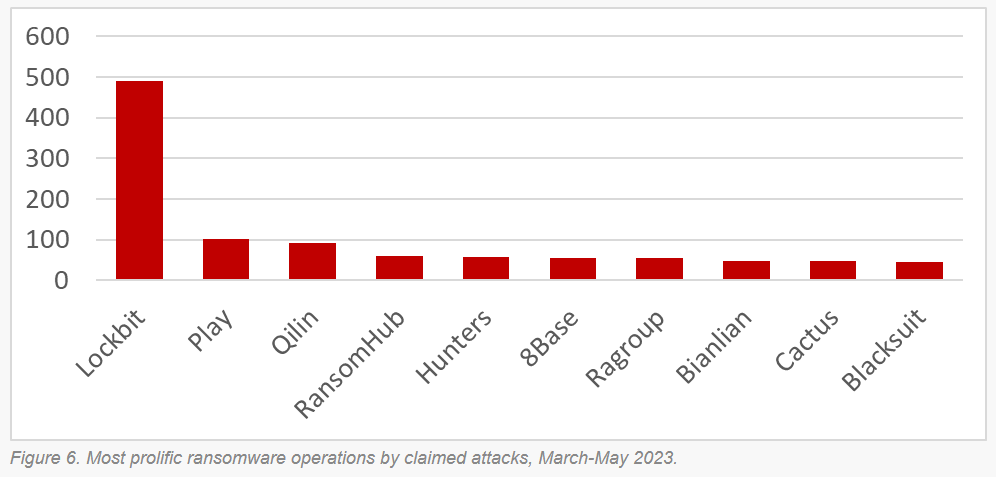
Threat/trend reports: CyCognito, Google TAG, Positive Technologies, Top10VPN, and Veeam have recently published reports covering infosec industry threats and trends.
Malware technical reports
Dama web shell: A Chinese cybercrime group is targeting websites built using the ThinkPHP framework in attacks designed to install a new web shell named Dama. The attacks exploit two old 2018 and 2019 vulnerabilities in the framework, mostly used by Chinese-speaking developers. Akamai says the attacks started last October and are ongoing. The company couldn't say what the final payload was (i.e., cryptomining, proxy bot, DDoS, etc.).
Muhstik: The Muhstik cryptomining botnet is now targeting Apache RocketMQ servers, per a new AquaSec report.
Commando Cat: The Commando Cat cryptomining botnet is now targeting Docker instances with their API exposed online, per Trend Micro.
PlugX: Security firm Hunt.io says it found an exposed server that contained an outdated PlugX builder and controller.
DarkGate: After Trellix's report on the new DarkGate v6 malware version, Cisco Talos has also published its own take on the malware.
Seidr: Flashpoint has published an analysis of the new Seider infostealer, currently advertised in underground cybercrime forums. The infostealer specifically targets cryptocurrency desktop wallets and browser extensions.
TargetCompany: The TargetCompany ransomware group has rolled out v2.0 of its Linux ESXi encryptor.
Fog: Security firm ArcticWolf has spotted a new ransomware strain named Fog that was used in attacks against organizations in the US education sector.
RansomHub: According to new research from Broadcom's Symantec division, the RansomHub RaaS has quickly become one of the largest ransomware groups currently operating today. The ransomware is a rebrand of the older Knight gang, itself a rebrand of the old Cyclops group.
Sponsor Section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information and then allows vulnerability management teams to do things like assigning responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
Mustang Panda: CyFirma has published a profile on Chinese APT group Mustang Panda and its most recent campaigns.
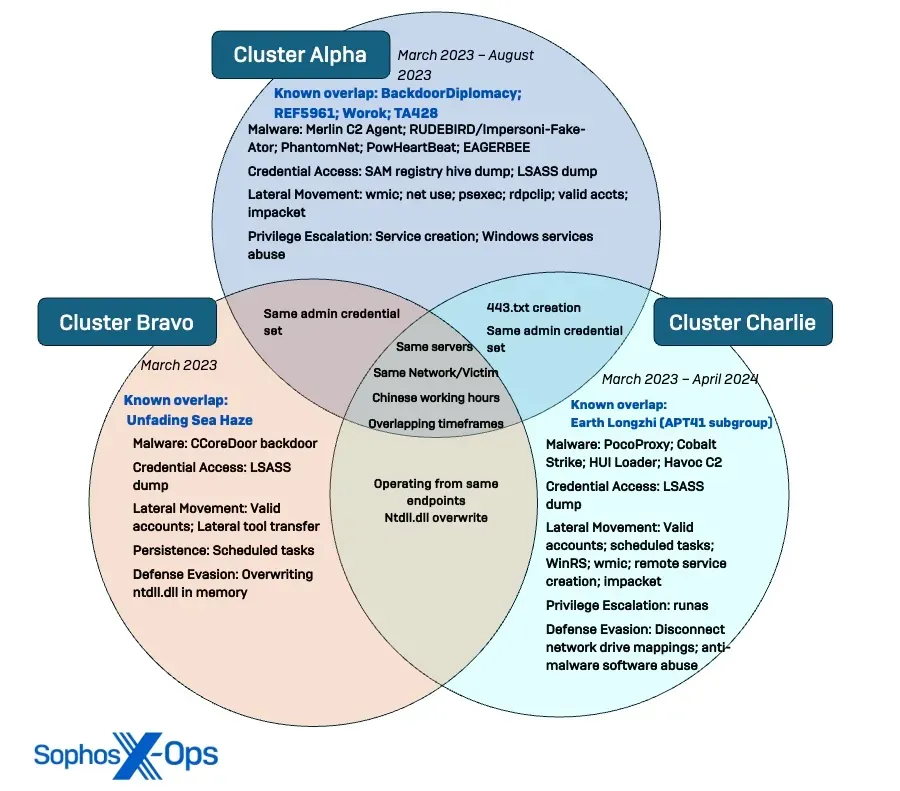
Crimson Palace: Sophos has published two reports on Crimson Palace, a Chinese cyber-espionage campaign that suggests that multiple Chinese APTs groups have targeted the same high-profile Southeast Asian government.
"The clusters were observed using tools and infrastructure that overlap with other researchers’ public reporting on Chinese threat actors BackdoorDiplomacy, REF5961, Worok, TA428, the recently-designated Unfading Sea Haze and the APT41 subgroup Earth Longzhi."
UAC-0020 (Vermin): Ukraine's CERT team says a threat actor it tracks as UAC-0020 (Vermin) is targeting its military with spear-phishing attacks designed to deliver the SPECTR infostealer. The group has returned with new attacks after first being spotted in March 2022, shortly after Russia's invasion of Ukraine. Officials claim the Vermin group receives orders from law enforcement agencies in the Luhansk occupied territory.
Sapphire Werewolf: Russian security firm BI.ZONE has published a report on Sapphire Werewolf, a threat actor that has hit more than 300 Russian organizations since March this year. The group has often used Russian government documents as lures, and the final payload has been a version of the Amethyst stealer. [We featured this in the May 29 edition, but the original report was only available in Russian.]
ExCobalt: Positive Technologies has published a report on ExCobalt, a former cybercrime group that is now conducting cyber-espionage operations against Russian targets. The group's latest attacks involved the use of a Go-based backdoor named GoRed. ExCobalt appears to be related to an APT that Rostelecom tracks as Shedding Zmiy.
Pro-Israeli info-op targets US lawmakers: According to reports from the New York Times and Haaretz, the Israel Ministry of Diaspora Affairs paid a private company named STOIC $2 million for a social media influence campaign that targeted US politicians. The campaign launched a month after the Hamas October 7 attack and targeted at least 128 members of the US Congress. According to disinformation experts [PDF], social media accounts controlled by STOIC targeted US lawmakers with pro-Israeli propaganda and anti-Arab views. STOIC's campaign was spotted and disrupted by Meta [PDF] and OpenAI earlier this month.
Kremlin disinfo: Russian independent news outlet Meduza is warning that Russian propagandists are pushing disinformation using misleading cutouts of its (and others) content.
Doppelganger campaign: DFRLab covers a pro-Kremlin disinformation campaign linked to the Doppelganger gang that attempted to discredit Georgian pro-democracy protests in the eyes of US audiences. Just like they did with Ukraine's pro-democracy protests, the bot farms tried to claim the US was behind the protests.
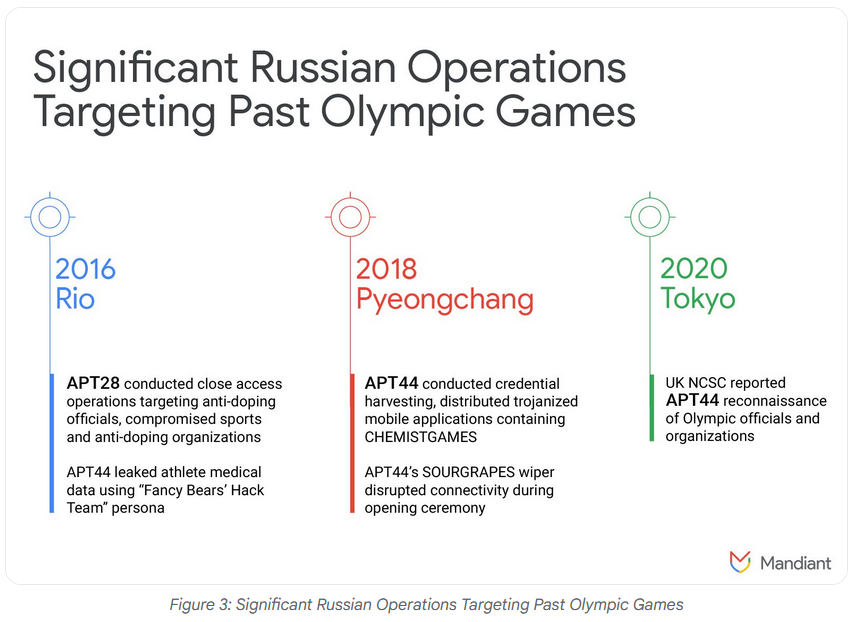
Olympic cyber threats: Google's Mandiant has published a report on the possible cyber threats facing this year's Paris Olympic Games. The report comes after similar ones from Microsoft and Recorded Future. TL;DR: The likelihood of cyberattacks is high, and it's probably gonna be Russian APTs, as usual.
Vulnerabilities, security research, and bug bounty
Cisco Webex security research incident: Cisco has rolled out patches for a Webex bug used by German journalists to identify and access data on past Webex government meetings. The bug was found by German newspaper Zeit and used to find more than 10,000 past Webex meetings for the Dutch and German governments. Zeit reporter Eva Wolfangel says Cisco never acknowledged the issue and rolled out patches behind their backs. Cisco says it's now notifying customers who had their data collected during the research.
Elastic security updates: Elastic has published three security updates for several of its products. [h/t ScreamingGoat]
Fortra security updates: Fortra has released a security update to fix an authentication bypass vulnerability in the REST and SOAP API of its Tripwire Enterprise SCM solution. [h/t ScreamingGoat]
RoR security updates: The Ruby on Rails framework has released two security updates.
SolarWinds security updates: SolarWinds has released security updates to fix four vulnerabilities.
RISC-V vulnerabilities: A team of Chinese academics has discovered a security flaw in the design of RISC-V SonicBOOM processors. Technical details are available here. [Additional coverage in SCMP]
TPM attack: Security researcher Máté Kukri has published details about a software attack on Intel chips that can expose TPM secrets. There's no CVE or patch coming from Intel.
Ariane kiosks: Swiss security firm Pentagrid has discovered a vulnerability in Ariane hotel check-in kiosks that could exit the kiosk mode and access the underlying OS.
Apache HugeGraph RCE: Security firm SecureLayer7 has published a write-up on CVE-2024-27348, a remote code execution on Apache HugeGraph database servers. The vulnerability received a 9.8/10 severity rating and was patched in April. A PoC and scan script are also available.
PHP-CGI vulnerability: Security firm DEVCORE has discovered a vulnerability (CVE-2024-4577) that allows for remote code execution attacks against web servers using PHP-CGI. The vulnerability impacts all PHP versions running on Windows systems. The new vulnerability is a bypass for an older 2012 security patch (CVE-2012-1823) that allowed attacks when PHP-CGI parsed certain query string parameters.
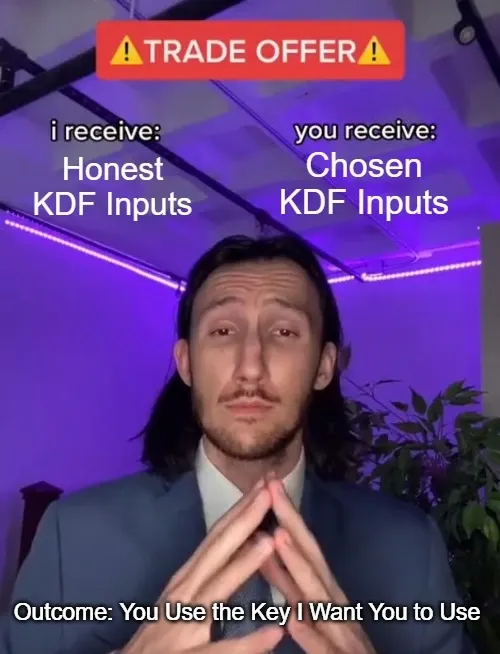
NIST SP 800-108 attack: Cryptography expert Scott Arciszewski has published a blog post on attacking algorithms that follow the NIST SP 800-108 specification.
"This post examines the attack against the initial SP 800-108 design when AES-CMAC is used as the PRF in KDF Counter mode."
Telerik exploitation: Threat actors are now scanning and attempting to exploit Telerik Report Servers using an authentication bypass vulnerability (CVE-2024-4358) that was patched at the end of May. The attacks began this week after security firm the Summoning Team published a proof-of-concept for the vulnerability. According to the Shadowserver Foundation, there are currently around 100 Telerik Report Servers exposed on the internet. Telerik Report Servers are used to provide analytics and reporting capabilities to developers and enterprise customers.
Kaspersky wants an Apple bug bounty: Kaspersky claims Apple refused to pay a bug bounty reward to its researchers after they provided information about the Operation Triangulation attacks and zero-days. The Russian security firm says Apple also refused to donate the $1 million reward to charity, as it is often its custom. Kaspersky disclosed details about Operation Triangulation in June of last year. The operation used several iOS zero-days to target and spy on Russian government officials, foreign diplomats working in Russia, and Kaspersky employees. Russia's FSB intelligence service linked the attack to the NSA and claimed Apple cooperated with the American spy agency. Apple has denied the accusations and released patches for the Triangulation bugs throughout 2023. [Additional coverage in RTVI, h/t Oleg Shakirov]
CISA becomes a CVE ADP: The MITRE Corporation has designated CISA as the first-ever CVE Authorized Data Publisher (ADP). As an ADP, CISA will now be allowed to enrich and add metadata to vulnerabilities added to MITRE's CVE database. MITRE has launched the ADP program after NIST slowed down enriching new CVEs due to staff shortages.
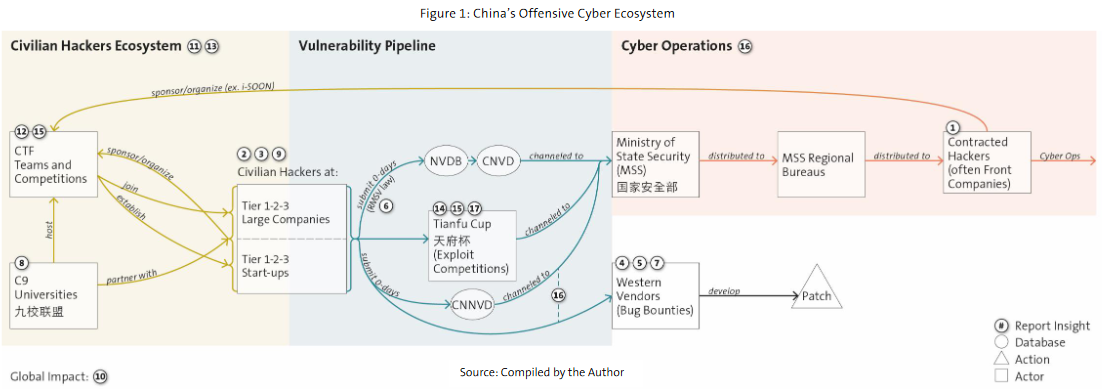
China's hacking and bug bounty ecosystem: Eugenio Benincasa, a Cyber Defense Researcher at the Technical University of Zurich (ETH Zurich), has published a 74-page paper [PDF] on the connections between China's hacking contests and bug bounty platforms and the country's offensive cyber capabilities. I didn't get to read it before this newsletter came out—because the research was so long—but Benincasa has summarized some of the findings in this thread.
Infosec industry
New tool—Scalpel: Security firm Ambionics open-sourced Scalpel, a Burp Suite extension for intercepting and rewriting HTTP traffic.
New tool—nowafpls: Security firm Assetnote has released nowafpls, a Burp Suite extension to bypass web application firewalls using junk data injections.
Acquisition news: Tenable is acquiring Eureka Security, a data security posture management (DSPM) provider for cloud environments.
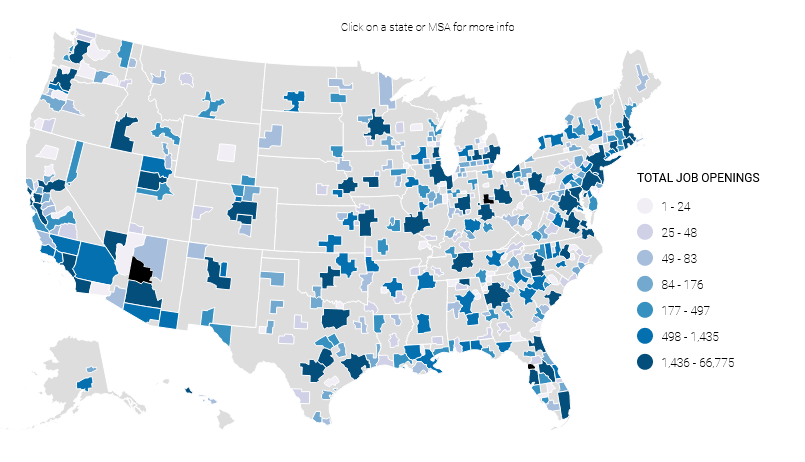
Cybersecurity shortage: NIST's CyberSeek project says the US still needs over 225,000 professionals to close its cybersecurity workforce shortage. The agency says that only 85% of the 1.2 million cybersecurity jobs in the US are occupied. The vast majority of open jobs are in large metropolitan areas in Texas, California, Illinois, and across the East Coast. [Additional coverage in SecurityWeek]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about law enforcement agencies trolling cyber criminals when they carry out disruption operations, and why it might be counterproductive.




